diff --git a/i18n/be/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/be/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index d10f3e8722a..e8bf65a8bb2 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -21,19 +21,19 @@ The old beta extension will be renamed to [**AdGuard Ad Blocker MV2**](https://c
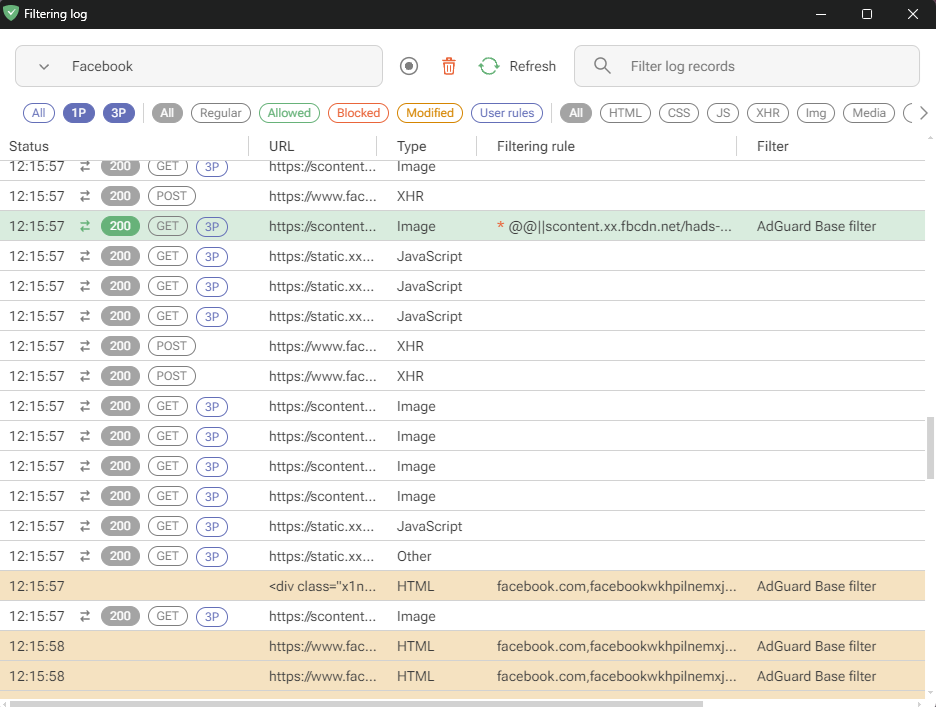
- **Filtering log**
- 
+ 
- Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
+ Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
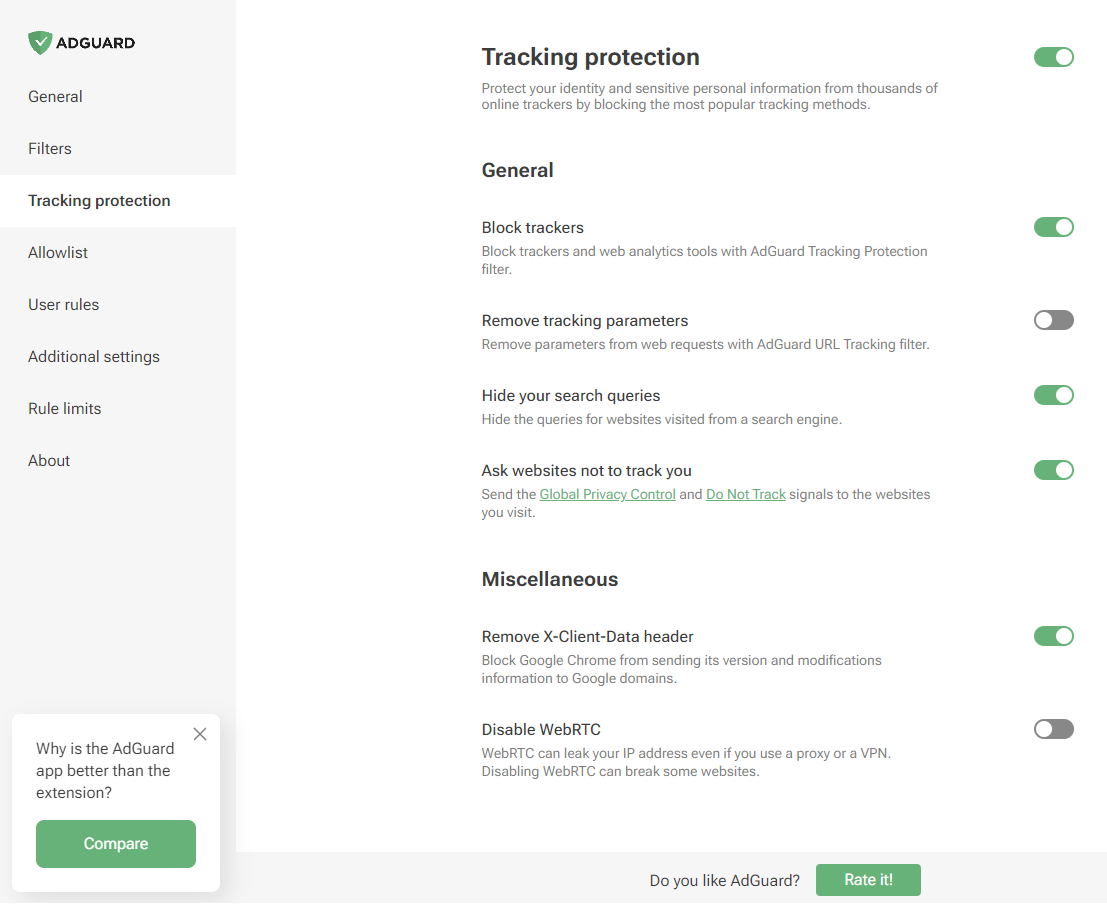
- _Tracking protection_ (formerly known as _Stealth mode_)
- 
+ 
- There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
+ There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
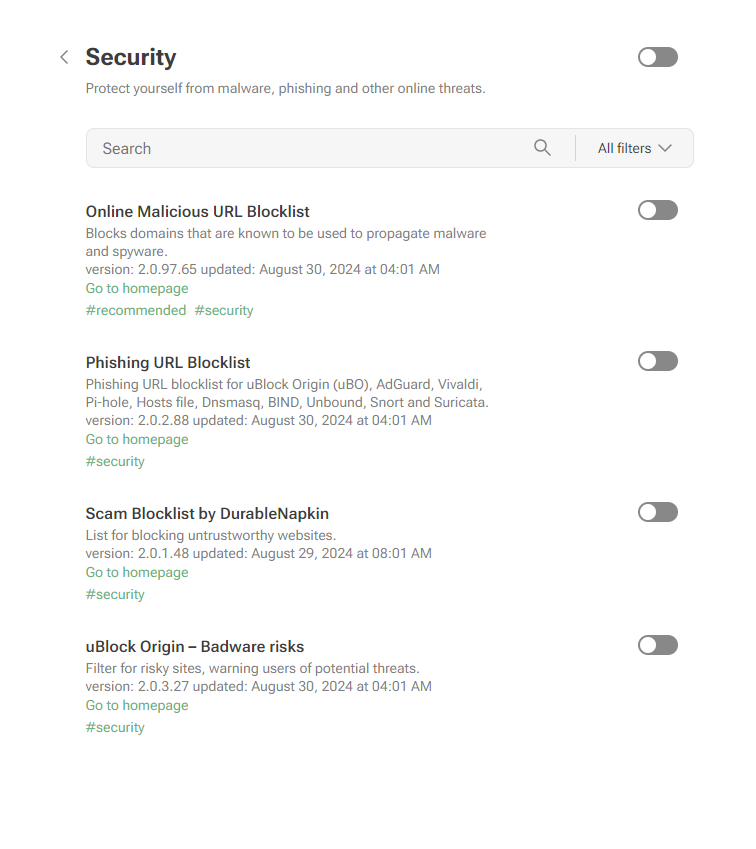
- _Phishing & malware protection_ is no longer available in the general settings. To protect yourself from malicious websites and scams, enable the appropriate _Security_ filters in the _Filters_ tab.
- 
+ 
## Limitations
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index b1adcc3ff6a..ae7977af510 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/be/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 68db37af985..ae7977af510 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/bn/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index 8b7b529ce50..0e51ab28b05 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -137,6 +137,12 @@ Pokud je toto nastavení povoleno, bude AdGuard filtrovat kromě jiných typů p
**O HTTP/3**: Jedná se o nejnovější verzi protokolu HTTP založenou na protokolu QUIC.
+**Limitations**:
+
+- Prohlížeče založené na Chrome nepřijímají uživatelské certifikáty, proto v nich není podporováno filtrování HTTP/3.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari podporuje filtrování HTTP/3 bez další konfigurace.
+
### Odchozí proxy
#### Zobrazit nastavení Filtrovat požadavky DNS
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 0aaff143088..df51df23e3d 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Upozorňujeme, že filtrování DNS bude aktivní i v režimu _Automatického pr
V této sekci najdete informace o své licenci a můžete provádět následující:
- Zakoupit licenci AdGuardu pro aktivaci [funkcí plné verze](/adguard-for-android/features/free-vs-full)
-- Přihlásit se ke svému AdGuard účtu nebo zadat licenční klíč pro aktivaci licence
-- Zaregistrovat se a aktivovat si 7denní zkušební dobu, pokud jste ji ještě nevyužili
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Obnovit stav licence z nabídky se třemi tečkami (⋮)
- Otevřít AdGuard účet a spravovat v něm své licence
- Resetovat licenci — například pokud jste dosáhli limitu zařízení pro tuto licenci a chcete použít jinou
-
+
## Podpora
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 39bceedfd31..38cc45e564e 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ Hotovo, AdGuard pro Android TV je nainstalován.
- V Terminálu zadejte příkaz `adb install Downloads/adguard_tv.apk`. V případě potřeby nahraďte `Downloads/adguard_tv.apk` vlastní cestou.
- Počkejte, až se v Terminálu zobrazí zpráva o úspěšné instalaci aplikace.
+
+## Instalace aplikace AdGuard pro Android TV skrze atvTools
+
+**Důležité:** Vaše chytrá TV a TV s Android TV (TV box) musí být ve stejné místní síti.
+
+1. Nainstalujte [aplikaci atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) do svého telefonu s Androidem
+
+2. Připojte **atvTools** k **Android TV**
+
+ 1. Povolte režim pro vývojáře na zařízení Android TV
+
+ `Nastavení` → `Nastavení zařízení` → `O zařízení` → Klepněte na `Sestavení Android TV` dokud neuvidíte zprávu potvrzující, že jste úspěšně získali stav pro vývojáře
+
+ 2. Povolte USB ladění na zařízení Android TV
+
+ Přejděte do `Nastavení` → `Nastavení zařízení` → `Pro vývojáře` → `Ladění`, povolte a zapněte `USB ladění`
+
+3. Spusťte **atvTools** na svém chytrém telefonu
+
+4. Vyhledejte v seznamu požadované zařízení **Android TV** a klikněte na něj
+
+5. Povolte připojení na TV
+
+6. Stáhněte instalátor [AdGuard pro Android TV](https://agrd.io/tvapk) do svého smartphonu jako **APK** soubor
+
+7. V **atvTools** klikněte na **Instalovat** na hlavní obrazovce a počkejte (méně než minutu), než se v seznamu aplikací objeví ikona **AdGuard pro Android TV**
+
+
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-mac/adguard-for-mac.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-mac/adguard-for-mac.md
index 0bcd5d77fc3..d2aabfde1be 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-mac/adguard-for-mac.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-mac/adguard-for-mac.md
@@ -9,7 +9,7 @@ Tento článek popisuje AdGuard pro macOS, multifunkční blokátor reklam, kter
:::
-## Funkce
+## Features
Hlavní funkce a nastavení dostupné v aplikaci AdGuard pro macOS
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index 7f86f98eed8..4e18b238c37 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Ověřuje pravost všech certifikátů pro doménu na základě zásad transpare
Nastavením `true` umožníte AdGuardu filtrovat provoz odeslaný skrze HTTP/3, nejnovější verzi protokolu HTTP založeného na QUIC.
+**Omezení**:
+
+- Prohlížeče založené na Chrome nepřijímají uživatelské certifikáty, proto v nich není podporováno filtrování HTTP/3.
+- Prohlížeče založené na Firefoxu se ve výchozím nastavení chovají podobně, ale můžete nastavit možnost `network.http.http3.disable_when_third_party_roots_found` v `about:config` na `false`, aby byly povoleny uživatelské certifikáty pro HTTP/3.
+- Safari podporuje filtrování HTTP/3 bez další konfigurace.
+
#### `network.filtering.localnetwork`
Nastavením `true` povolíte filtrování lokální sítě.
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-safari/adguard-for-safari.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-safari/adguard-for-safari.md
index c46c911eeab..0e711705264 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-safari/adguard-for-safari.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-safari/adguard-for-safari.md
@@ -9,7 +9,7 @@ Tento článek je o AdGuardu pro Safari, který chrání pouze váš prohlíže
:::
-## Funkce
+## Features
Hlavní funkce a nastavení dostupné v aplikaci AdGuard pro Safari
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-safari/features/features.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-safari/features/features.md
index ae6cef5dec9..d4d77504bab 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-safari/features/features.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-safari/features/features.md
@@ -1,5 +1,5 @@
---
-title: Funkce
+title: Features
sidebar_position: 1
---
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/adguard-for-windows.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/adguard-for-windows.md
index ef23f5cb529..ae53f7257fa 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/adguard-for-windows.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/adguard-for-windows.md
@@ -9,7 +9,7 @@ Tento článek popisuje AdGuard pro Windows, multifunkční blokátor reklam, kt
:::
-## Funkce
+## Features
Hlavní funkce a nastavení dostupné v aplikaci AdGuard pro Windows
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/features.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/features.md
index 65811e5d05e..12134e13672 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/features.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/features.md
@@ -1,5 +1,5 @@
---
-title: Funkce
+title: Features
sidebar_position: 1
---
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 383bafc9253..3c54d1e06f0 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ Tento článek popisuje AdGuard pro Windows, multifunkční blokátor reklam, kt
AdGuard pro Windows je snadno použitelný nástroj, který blokuje otravné bannery, vyskakovací okna, videoreklamy a slídiče. To ale není vše: pomáhá šetřit data, rychleji načítat webové stránky a chránit počítač před nežádoucím a potenciálně škodlivými weby. AdGuard vás také chrání před krádeží identity a chrání vaše děti před nevhodným obsahem.
-
+
Po spuštění AdGuardu pro Windows se zobrazí domovská obrazovka aplikace. Nejvýraznějším detailem je tlačítko _zapnutí/vypnutí ochrany_. Na této obrazovce můžete také sledovat statistiky blokovaných reklam, slídičů a hrozeb, zjistit aktuální verzi aplikace nebo ji aktualizovat. Dále jsou v pravém horním rohu čtyři karty: _Nastavení_, _Podpora_, _Licence_ a _O programu_. O každé z nich stojí za to mluvit zvlášť.
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index ea3e970110e..f92346b3f59 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ Tento článek popisuje AdGuard pro Windows, multifunkční blokátor reklam, kt
_Nastavení_ je část, která vyžaduje největší pozornost. Zde můžete program nakonfigurovat tak, aby plně vyhovoval vašim požadavkům: blokujte pouze to, co vám vadí, používejte DNS server důvěryhodného poskytovatele, odstraňujte soubory cookies třetích stran atd.
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### Obecná nastavení
+
-Zde můžete nastavit jazyk a motiv (tmavý nebo světlý), povolit spouštění AdGuardu při startu systému a tiché automatické aktualizace, vybrat aktualizační kanál a interval kontroly aktualizací filtrů. Pokud AdGuard pro Windows nefunguje správně a tým podpory vás požádal, abyste [shromáždili _Protokoly ladění_](/adguard-for-windows/solving-problems/adguard-logs.md), přejděte do Nastavení.
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-Úplně dole na obrazovce najdete _Pokročilá nastavení_. Bezmyšlenkovitá změna některých z nich může potenciálně způsobit problémy s výkonem AdGuardu, přerušit internetové připojení nebo ohrozit vaši bezpečnost a soukromí. Tuto část byste měli otevřít pouze v případě, že jste si jisti tím, co děláte, nebo pokud se vás na to zeptal náš tým podpory. Pokud chcete vědět, co lze nastavit v _Pokročilém nastavení_, přečtěte si [specializovaný článek](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Blokování reklam
Jedná se o hlavní modul AdGuardu pro Windows, který odstraňuje reklamy z navštívených webových stránek a aplikací nainstalovaných v zařízení. K filtrování reklam a obsahu ohrožujícího soukromí, jako jsou bannery, vyskakovací okna nebo slídiče, používá AdGuard různé filtry — skupiny pravidel s podobným účelem zapsané pomocí [speciální syntaxe](/general/ad-filtering/create-own-filters). Chcete-li pochopit, co jsou to filtry a jak fungují, přečtěte si [tento článek](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Mnoho webových stránek shromažďuje informace o svých návštěvnících, na

-Práci v Režimu utajení můžete flexibilně nastavit: můžete například zakázat, aby webová stránka obdržela požadavek na vyhledávání, který jste použili k jejímu nalezení na internetu, automaticky vymazat soubory cookies třetích stran i vlastní soubory cookies webové stránky a zakázat sdílení polohy ve vašem prohlížeči, které lze použít ke sledování vaší polohy.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-Chcete-li se dozvědět vše o Režimu utajení a jeho mnoha možnostech, přečtěte si [tento článek](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Bezpečné prohlížení
@@ -81,15 +81,15 @@ Od verze 7.20 můžete také přidávat filtry jednoduchým výběrem ze seznamu

-### Rodičovská ochrana
+### Parental control
-Existuje několik webových stránek, ke kterým by měl být omezen přístup z PC používaného dětmi. Tento úkol zajišťuje _Rodičovská ochrana_.
+Existuje několik webových stránek, ke kterým by měl být omezen přístup z PC používaného dětmi. This task is accomplished by _Parental control_.
-
+
-Modul kontroluje obsah webových stránek otevřených v prohlížeči a filtruje ty, jejichž obsah je pro děti nežádoucí: obrázky a texty pro dospělé, hrubý jazyk, násilí, propagace drog atd. Nastavení Rodičovské ochrany jsou zabezpečena heslem, takže dítě nemůže obejít omezení. Tento modul nejenže blokuje vstup na nežádoucí stránky, ale také dokáže z výsledků vyhledávání odstranit odkazy, které jsou nevhodné pro děti.
+Modul kontroluje obsah webových stránek otevřených v prohlížeči a filtruje ty, jejichž obsah je pro děti nežádoucí: obrázky a texty pro dospělé, hrubý jazyk, násilí, propagace drog atd. Parental control settings are password-protected so that the child is not able to go round the restrictions. Tento modul nejenže blokuje vstup na nežádoucí stránky, ale také dokáže z výsledků vyhledávání odstranit odkazy, které jsou nevhodné pro děti.
-V modulu _Rodičovská ochrana_ můžete povolit _Bezpečné vyhledávání_, spravovat _seznam zakázaných_, _seznam povolených_ a přizpůsobit si funkce těchto možností. Můžete také zaškrtnout políčko _Blokovat stahování spustitelných souborů_ a zabránit tak vašemu dítěti ve stahování a instalaci softwaru do PC. V modulu _Rodičovská ochrana_ jsou další dvě možnosti: můžete vybrat konkrétního uživatele Windows, který má být chráněn _Rodičovskou ochranou_ a nastavit heslo pro zabezpečení nastavení AdGuardu před změnami.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. Můžete také zaškrtnout políčko _Blokovat stahování spustitelných souborů_ a zabránit tak vašemu dítěti ve stahování a instalaci softwaru do PC. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Asistent prohlížeče
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index b2243ee8ea1..b6be40664be 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Tuto funkci povolte, pokud chcete, aby AdGuard automaticky zachycoval adresy URL
Pokud je tato možnost povolena, bude AdGuard filtrovat kromě jiných typů požadavků také požadavky odeslané skrze HTTP/3.
+**Omezení**:
+
+- Prohlížeče založené na Chrome nepřijímají uživatelské certifikáty, proto v nich není podporováno filtrování HTTP/3.
+- Prohlížeče založené na Firefoxu se ve výchozím nastavení chovají podobně, ale můžete nastavit možnost `network.http.http3.disable_when_third_party_roots_found` v `about:config` na `false`, aby byly povoleny uživatelské certifikáty pro HTTP/3.
+- Safari podporuje filtrování HTTP/3 bez další konfigurace.
+
### Použít režim přesměrování ovladače
Pokud je tato možnost povolena, AdGuard zachytí veškerý provoz a přesměruje jej na místní proxy pro další filtrování.
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 8cc69f05e70..4be7e9f9daf 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ Tento článek je o filtrech, které vytváříme pro použití v AdGuardu a jin
- **Experimentální filtr** slouží k testování některých nových pravidel filtrování, která mohou potenciálně způsobovat konflikty a narušovat práci webových stránek. Pokud tato pravidla fungují bez problémů, přidají se do hlavních filtrů. [Zobrazit pravidla](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Filtr mobilních reklam** blokuje reklamy v mobilních zařízeních. Obsahuje všechny známé sítě mobilní reklamy. [Zobrazit pravidla](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filtr** — (Základní filtrAdGuard, Filtr sociálních médií, Filtr ochrany sledování, Filtr mobilních reklam, EasyList a EasyPrivacy), který je zjednodušený pro lepší kompatibilitu s blokováním reklamy na úrovni DNS. Tento filtr používá servery [AdGuard DNS](https://adguard-dns.io/kb) k blokování reklam a sledování. [Zobrazit pravidla](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Filtr rychlých oprav** — slouží k rychlému řešení kritických problémů s filtrováním obsahu na oblíbených webech bez aktualizace rozšíření MV3. [Zobrazit pravidla](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## Zásady AdGuard filtrů
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index c648d4e827d..a7e2971dbd9 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ Tento modifikátor umožňuje zúžit pokrytí pravidla na konkrétní aplikaci
V případě počítače Mac můžete ID svazku nebo název procesu aplikace zjistit zobrazením příslušných podrobností o požadavku v záznamu filtrování.
+**Syntaxe**
+
+Modifikátor je seznam jednoho nebo více výrazů, z nichž každý je porovnáván s aplikací určitým způsobem v závislosti na svém typu. Tyto výrazy jsou odděleny symbolem `|`.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — regulární název aplikace (`example.app`). Odpovídá zadané aplikaci a je přiřazen lexikograficky.
+- **`wildcard_app`** — název aplikace končící zástupným znakem `*`, např. `org.example.*` nebo `com.ad*`. Odpovídá všem aplikacím, jejichž názvy začínají zadanou předponou. Porovnání se provádí lexikograficky.
+- **`regexp`** — regulární výraz, který začíná a končí znakem `/`. Funguje stejně jako v základních pravidlech URL, ale znaky `/`, `$`, `,` a `|` musí být uvozeny pomocí `\`.
+
**Příklady**
- `||baddomain.com^$app=org.example.app` — pravidlo pro blokování požadavků, které odpovídají zadané masce a jsou odeslány z Android aplikace `org.example.app`.
@@ -429,9 +442,23 @@ Pokud chcete, aby se pravidlo nevztahovalo na určité aplikace, začněte náze
- `||baddomain.com^$app=~org.example.app` — pravidlo pro blokování požadavků, které odpovídají zadané masce a jsou odeslány z jakékoli aplikace kromě `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — stejně jako výše, ale nyní jsou vyloučeny dvě aplikace: `org.example.app1` a `org.example.app2`.
+Zástupné znaky můžete použít v modifikátoru `$app`:
+
+- `||baddomain.com^$app=org.example.*` — použije se pro všechny aplikace, jejichž názvy balíčků začínají na `org.example.`
+
+V modifikátoru `$app` můžete použít regulární výrazy, které uzavřete do lomítek `/.../`. To umožňuje flexibilnější párování — například cílení na skupinu aplikací od stejného vydavatele nebo párování složitých vzorů.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — platí pro všechny aplikace, jejichž název balíčku začíná `org.example` (např. `org.example.app1`, `org.example.utility` atd.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — platí pro `org.example.app` a pro všechny aplikace, jejichž balíček začíná `org.example.a` nebo `org.example.b`.
+
+Modifikátor `$app` podporuje kombinování všech tří typů záznamů — prostých názvů, zástupných znaků a regulárních výrazů — v rámci stejného pravidla, ale neumožňuje kombinovat negované a nenegované výrazy dohromady.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — platí pro `org.example.app`, všechny odpovídající aplikace `org.example.*` a `org.example.[a-z]+`.
+
:::caution Omezení
-Aplikace v hodnotě modifikátoru nemohou mít zástupný znak, např. `$app=com.*.music`. Pravidla s takovým modifikátorem jsou považována za neplatná.
+- Aplikace v hodnotě modifikátoru nemohou obsahovat zástupný znak uvnitř řetězce, např. `$app=com.*.music`. Použijte místo toho regulární výraz: `$app=/com\..*\.music/`.
+- Nelze kombinovat negované (`~`) a nenegované výrazy ve stejném modifikátoru `$app` — bylo by to nejednoznačné.
:::
@@ -439,6 +466,7 @@ Aplikace v hodnotě modifikátoru nemohou mít zástupný znak, např. `$app=com
- Pouze AdGuard pro Windows, Mac a Android jsou technicky schopné používat pravidla s modifikátorem `$app`.
- V systému Windows se v názvu procesu nerozlišují velká a malá písmena, počínaje AdGuard pro Windows s [CoreLibs][] v1.12 nebo novější.
+- Podpora regulárních výrazů a kombinování různých typů záznamů (prosté názvy, zástupné znaky a regulární výrazy) v modifikátoru `$app` je k dispozici od verze CoreLibs v1.19 nebo novější.
:::
@@ -529,38 +557,23 @@ Pokud chcete, aby se pravidlo nevztahovalo na určité domény, začněte název
**`$domain` modifikátor odpovídající cílové doméně:**
-V některých případech může modifikátor `$domain` odpovídat nejen doméně odkazovače, ale také cílové doméně. K tomu dojde, pokud jsou splněny všechny následující podmínky:
-
-1. Požadavek má typ obsahu `document`
-1. Vzor pravidla neodpovídá žádné konkrétní doméně
-1. Vzor pravidla neobsahuje regulární výrazy
-1. Modifikátor `$domain` obsahuje pouze domény ve výjimkách, např. `$domain=~example.org|~example.com`
+V některých případech může modifikátor `$domain` odpovídat nejen doméně odkazovače, ale také cílové doméně.
-Následující predikát by měl být splněn, aby bylo možné provést porovnání cílové domény:
+K tomu dochází, když pravidlo obsahuje jeden z následujících modifikátorů: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-To znamená, že pokud modifikátor `$domain` obsahuje pouze domény ve výjimkách, pak pravidlo nemusí splňovat druhou a třetí podmínku, aby se cílová doména shodovala s modifikátorem `$domain`.
-
-Pokud některé z výše uvedených podmínek nejsou splněny, ale pravidlo obsahuje modifikátor [`$cookie`](#cookie-modifier) nebo [`$csp`](#csp-modifier), cílová doména bude přesto přiřazena.
-
-Pokud odkazující doména odpovídá pravidlu s `$domain`, které výslovně vylučuje doménu odkazujícího serveru, pravidlo se nepoužije, i když cílová doména také odpovídá pravidlu. To má vliv i na pravidla s modifikátory [`$cookie`](#cookie-modifier) a [`$csp`](#csp-modifier).
+Tyto modifikátory nebudou použity, pokud odkazující doména odpovídá pravidlu s `$domain`, které výslovně vylučuje odkazující doménu, i když cílová doména také odpovídá pravidlu.
**Příklady**
- `*$cookie,domain=example.org|example.com` zablokuje soubory cookie pro všechny požadavky do a z domény `example.org` a `example.com`.
-- `*$document,domain=example.org|example.com` zablokuje všechny požadavky do a z domény `example.org` a `example.com`.
+- `*$document,domain=example.org|example.com` zablokuje pouze požadavky z `example.org` a `example.com`, ale ne požadavky směřující na tyto domény.
V následujících příkladech se předpokládá, že požadavky jsou odesílány z adresy `http://example.org/page` (odkazující adresa), cílová adresa URL je `http://targetdomain.com/page`.
- `page$domain=example.org` bude přiřazena, protože odpovídá doméně odkazu.
-- `page$domain=targetdomain.com` bude přiřazena, protože odpovídá cílové doméně a splňuje všechny výše uvedené požadavky.
-- `||*page$domain=targetdomain.com` nebude přiřazena, protože vzor `||*page` odpovídá konkrétním doménám, např. `example.page`.
-- `||*page$domain=targetdomain.com,cookie` bude přiřazena, protože pravidlo obsahuje modifikátor `$cookie`, přestože vzor `||*page` může odpovídat konkrétním doménám.
-- `/banner\d+/$domain=targetdomain.com` nebude přiřazena, protože obsahuje regulární výraz.
-- `page$domain=targetdomain.com|~example.org` nebude přiřazena, protože doména odkazu je výslovně vyloučena.
+- `page$domain=targetdomain.com` nebude odpovídat, protože neodpovídá doméně odkazujícího webu.
+- `||*page$domain=targetdomain.com,cookie` bude odpovídat, protože pravidlo obsahuje modifikátor `$cookie`, i když vzor `||*page` může odpovídat konkrétním doménám.
+- `page$domain=targetdomain.com|~example.org,cookie` nebude přiřazena, protože doména odkazu je výslovně vyloučena.
##### omezení modifikátoru `$domain` {#domain-modifier-limitations}
@@ -613,7 +626,7 @@ kde:
:::caution Omezení
-1. Modifikátor `$header` lze použít pouze při příjmu záhlaví. Pokud je tedy požadavek zablokován nebo přesměrován v dřívější fázi, nelze modifikátor použít.
+1. Modifikátor `$header` lze porovnat pouze v případě, že jsou přijata záhlaví. Pokud je tedy požadavek zablokován nebo přesměrován v dřívější fázi, nelze modifikátor použít.
1. V Rozšíření prohlížeče AdGuard je modifikátor `$header` kompatibilní poze s [`$csp`](#csp-modifier), [`$removeheader`](#removeheader-modifier) (pouze hlavičky odpovědí), [`$important`](#important-modifier), [`$badfilter`](#badfilter-modifier), [`$domain`](#domain-modifier), [`$third-party`](#third-party-modifier), [`$match-case`](#match-case-modifier) s [content-type modifiers](#content-type-modifiers) jako [`$script`](#script-modifier) a [`$stylesheet`](#stylesheet-modifier). Pravidla s jinými modifikátory jsou považována za neplatná a budou vyřazena.
@@ -737,7 +750,7 @@ Funguje stejně jako modifikátor [`$third-party`](#third-party-modifier), ale z
- `||domain.com^$strict-thirdparty` — toto pravidlo bude použito na všechny domény, kromě `domain.com`. Příklad požadavku třetí strany: `http://sub.domain.com/banner.jpg` (na rozdíl od modifikátoru `$third-party`).
-:::note
+Zakazuje prohlížeči Google Chrome odesílat informace o verzi a modifikaci s požadavky na domény Google (včetně DoubleClick a Google Analytics).
Místo plného názvu modifikátoru můžete použít kratší název (alias): `$strict3p`.
@@ -1037,7 +1050,7 @@ Doporučujeme také seznámit se s [přehledem filtrů Adblock Plus](https://adb
| [$generichide](#generichide-modifier) | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| [$specifichide](#specifichide-modifier) | ✅ | ✅ | ✅ | ✅ | ❌ | ❌ | ❌ |
-:::note
+Zakazuje prohlížeči Google Chrome odesílat informace o verzi a modifikaci s požadavky na domény Google (včetně DoubleClick a Google Analytics).
- ✅ — plně podporováno
- ✅ * — podporováno, ale spolehlivost se může lišit nebo se mohou vyskytnout omezení; více informací naleznete v popisu modifikátoru
@@ -1249,7 +1262,7 @@ Například tato pravidla jsou generická:
||domain.com^$domain=~example.com
```
-A tato nejsou:
+And these are not:
```adblock
domain.com###banner
@@ -1258,7 +1271,7 @@ domain.com###banner
#### **`$genericblock`** {#genericblock-modifier}
-Zakáže generická základní pravidla na stránkách, které odpovídají pravidlu výjimky.
+Disables generic basic rules on pages that correspond to exception rule.
**Příklady**
@@ -1268,19 +1281,19 @@ Zakáže generická základní pravidla na stránkách, které odpovídají prav
:::caution Omezení
-V AdGuardu pro iOS a AdGuardu pro Safari fungují pravidla `$genericblock` jako [$document exclusion](#document-modifier) — odblokování všeho.
+In AdGuard for iOS and AdGuard for Safari, rules with `$genericblock` work as [$document exclusion](#document-modifier) — unblock everything.
:::
:::info Kompatibilita
-Pravidla s modifikátorem `$genericblock` nejsou podporována Blokátorem obsahu AdGuard, AdGuardem pro Chrome MV3.
+Rules with `$genericblock` modifier are not supported by AdGuard Content Blocker, and AdGuard for Chrome MV3.
:::
#### **`$generichide`** {#generichide-modifier}
-Zakáže všechna generická [kosmetická pravidla](#cosmetic-rules) na stránkách, které odpovídají pravidlu výjimky.
+Disables all generic [cosmetic rules](#cosmetic-rules) on pages that correspond to the exception rule.
**Příklady**
@@ -1288,13 +1301,13 @@ Zakáže všechna generická [kosmetická pravidla](#cosmetic-rules) na stránk
:::note
-Místo plného názvu modifikátoru můžete použít kratší název (alias): `$ghide`.
+You may use a shorter name (alias) instead of using the full modifier name: `$ghide`.
:::
#### **`specifichide`** {#specifichide-modifier}
-Zakáže všechna specifická pravidla pro skrývání prvků a CSS, ale ne obecná pravidla. Má opačný účinek než [`$generichide`](#generichide-modifier).
+Disables all specific element hiding and CSS rules, but not general ones. Has an opposite effect to [`$generichide`](#generichide-modifier).
**Příklady**
@@ -1302,25 +1315,25 @@ Zakáže všechna specifická pravidla pro skrývání prvků a CSS, ale ne obec
:::note
-Místo plného názvu modifikátoru můžete použít kratší název (alias): `$shide`.
+You may use a shorter name (alias) instead of using the full modifier name: `$shide`.
:::
-:::note
+Zakazuje prohlížeči Google Chrome odesílat informace o verzi a modifikaci s požadavky na domény Google (včetně DoubleClick a Google Analytics).
-Všechna kosmetická pravidla — nejen ta specifická — lze zakázat pomocí modifikátoru [`$elemhide`](#elemhide-modifier).
+All cosmetic rules — not just specific ones — can be disabled by [`$elemhide` modifier](#elemhide-modifier).
:::
:::info Kompatibilita
-Pravidla s modifikátorem `$specifichide` nejsou AdGuardem pro iOS, Adguardem pro Safari a Blokátorem obsahu AdGuard podporována.
+Rules with `$specifichide` modifier are not supported by AdGuard for iOS, AdGuard for Safari, and AdGuard Content Blocker.
:::
### Pokročilé schopnosti {#advanced-modifiers}
-Tyto modifikátory mohou zcela změnit chování základních pravidel.
+These modifiers are able to completely change the behavior of basic rules.
@@ -1359,7 +1372,7 @@ Tyto modifikátory mohou zcela změnit chování základních pravidel.
#### **`$all`** {#all-modifier}
-`$all` modifikátor je složen ze [všech modifikátorů typů obsahu](#content-type-modifiers) a [`$popup`](#popup-modifier). Např. pravidlo `||example.org^$all` se převádí na pravidlo:
+`$all` modifier is made of [all content-types modifiers](#content-type-modifiers) and [`$popup`](#popup-modifier). E.g. rule `||example.org^$all` is converting into rule:
```adblock
||example.org^$document,subdocument,font,image,media,object,other,ping,script,stylesheet,websocket,xmlhttprequest,popup
@@ -1367,7 +1380,7 @@ Tyto modifikátory mohou zcela změnit chování základních pravidel.
:::caution Omezení
-Tento modifikátor nelze použít jako výjimku se znakem `@@`.
+This modifier cannot be used as an exception with the `@@` mark.
:::
@@ -1375,19 +1388,19 @@ Tento modifikátor nelze použít jako výjimku se znakem `@@`.
:::caution Omezení
-Vzhledem k tomu, že modifikátor `$popup` je součástí `$all`, modifikátor `$all` není podporován AdGuardem pro Chrome MV3 kcůli [`$popup` omezením modifikátoru](#popup-modifier-limitations).
+Since `$popup` is a part if `$all`, the `$all` modifier is not supported by AdGuard for Chrome MV3 because of [`$popup` modifier limitations](#popup-modifier-limitations).
:::
:::info Kompatibilita
-Pravidla s modifikátorem `$all` nejsou Blokátorem obsahu AdGuard podporována.
+Rules with `$all` modifier are not supported by AdGuard Content Blocker.
:::
#### **`$badfilter`** {#badfilter-modifier}
-Pravidla s modifikátorem `$badfilter` vypnou ostatní základní pravidla, na která se vztahují. To znamená, že text vypnutého pravidla by měl odpovídat textu pravidla `$badfilter` (bez modifikátoru `$badfilter`).
+The rules with the `$badfilter` modifier disable other basic rules to which they refer. It means that the text of the disabled rule should match the text of the `$badfilter` rule (without the `$badfilter` modifier).
**Příklady**
@@ -1396,12 +1409,12 @@ Pravidla s modifikátorem `$badfilter` vypnou ostatní základní pravidla, na k
- `@@||example.com$badfilter` zakáže `@@||example.com`
- `||example.com$domain=domain.com,badfilter` zakáže `||example.com$domain=domain.com`
-Pravidla s modifikátorem `$badfilter` mohou zakázat další základní pravidla pro konkrétní domény, pokud splňují následující podmínky:
+Rules with `$badfilter` modifier can disable other basic rules for specific domains if they fulfill the following conditions:
-1. Pravidlo má modifikátor `$domain`
-1. Pravidlo nemá hodnotu modifikátoru negované domény `~` v `$domain`
+1. The rule has a `$domain` modifier
+1. The rule does not have a negated domain `~` in `$domain` modifier value
-V takovém případě pravidlo `$badfilter` zakáže odpovídající pravidlo pro domény uvedené v pravidlech `$badfilter` i v základních pravidlech. Upozorňujeme, že [logika zástupných znaků TLD](#wildcard-for-tld) funguje i zde.
+In that case, the `$badfilter` rule will disable the corresponding rule for domains specified in both the `$badfilter` and basic rules. Please note that [wildcard-TLD logic](#wildcard-for-tld) works here as well.
**Příklady**
@@ -1416,23 +1429,23 @@ V takovém případě pravidlo `$badfilter` zakáže odpovídající pravidlo pr
:::caution Omezení
-V [AdGuardu pro Chrome MV3][ext-mv3] se pravidlo s modifikátorem `$badfilter` použije v DNR pouze v případě, že úplně zruší zdrojové pravidlo. Nemůžeme ho vypočítat, pokud je zrušeno pouze částečně. [Příklady][badfilter-in-mv3].
+In [AdGuard for Chrome MV3][ext-mv3] a rule with the `$badfilter` modifier is applied in DNR only if it fully cancels the source rule. We cannot calculate it if it is only partially canceled. [Examples][badfilter-in-mv3].
:::
:::info Kompatibilita
-Pravidla s modifikátorem `$badfilter` nejsou Blokátorem obsahu AdGuard podporována.
+Rules with `$badfilter` modifier are not supported by AdGuard Content Blocker.
:::
#### **`$cookie`** {#cookie-modifier}
-Modifikátor `$cookie` zcela mění chování pravidla. Namísto blokování požadavku, tento modifikátor potlačí AdGuard nebo změní záhlaví `Cookie` a `Set-Cookie`.
+The `$cookie` modifier completely changes rule behavior. Instead of blocking a request, this modifier makes AdGuard suppress or modify the `Cookie` and `Set-Cookie` headers.
-**Vícenásobná pravidla odpovídajících jednomu požadavku**
+**Multiple rules matching a single request**
-V případě, že jednomu požadavku odpovídá více pravidel `$cookie`, použijeme každé z nich.
+In case if multiple `$cookie` rules match a single request, we will apply each of them one by one.
**Syntaxe**
@@ -1446,20 +1459,20 @@ kde:
- **`seconds`** — počet sekund aktuálního času pro posunutí data vypršení platnosti souboru cookie.
- **`strategy`** — řetězec pro strategii [Same-Site](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Set-Cookie/SameSite), která se má použít na cookies.
-Např.
+For example,
```adblock
||example.org^$cookie=NAME;maxAge=3600;sameSite=lax
```
-pokaždé, když AdGuard narazí na cookie s názvem `NAME` v požadavku na `example.org`, provede následující kroky:
+every time AdGuard encounters a cookie called `NAME` in a request to `example.org`, it will do the following:
- Nastaví datum vypršení platnosti na aktuální čas plus `3600` sekund
- Přiměje cookie použít "laxní" strategii [Same-Site](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Set-Cookie/SameSite).
-**Uvození speciálních znaků**
+**Escaping special characters**
-Pokud je pro porovnání použit regulární výraz `name`, musí být dva znaky uvozeny: čárka `,` a znak dolaru `$`. Každý z nich označte zpětným lomítkem `\`. Např. uvozená čárka vypadá takto: `\,`.
+If regular expression `name` is used for matching, two characters must be escaped: comma `,` and dollar sign `$`. Use backslash `\` to escape each of them. For example, escaped comma looks like this: `\,`.
**Příklady**
@@ -1468,7 +1481,7 @@ Pokud je pro porovnání použit regulární výraz `name`, musí být dva znaky
- `$cookie=/__utm[a-z]/` blokuje všude soubory cookie Google Analytics
- `||facebook.com^$third-party,cookie=c_user` brání Facebooku ve sledování, i když jste přihlášeni
-Existují dva způsoby, jak deaktivovat pravidla `$cookie`: primární metoda zahrnuje použití výjimky označené `@@` — `@@||example.org^$cookie`. Alternativní metoda využívá výjimku `$urlblock` (také zahrnutou pod aliasem výjimky `$document` — `$elemhide,jsinject,content,urlblock,extension`). Funguje to takto:
+There are two methods to deactivate `$cookie` rules: the primary method involves using an exception marked with `@@` — `@@||example.org^$cookie`. The alternative method employs a `$urlblock` exception (also included under the `$document` exception alias — `$elemhide,jsinject,content,urlblock,extension`). Here's how it works:
- `@@||example.org^$cookie` odblokuje všechny soubory cookie nastavené doménou `example.org`
- `@@||example.org^$urlblock` odblokuje všechny cookies nastavené doménou `example.org` a zakáže blokování všech požadavků odeslaných z `example.org`
@@ -1479,43 +1492,43 @@ Existují dva způsoby, jak deaktivovat pravidla `$cookie`: primární metoda za
:::caution Omezení
-V [AdGuardu pro Chrome MV3][ext-mv3] odstraňujeme soubory cookies dvěma způsoby: ze strany `content-script` (ke které máme přístup) a z `onBeforeSendHeaders` posluchače. Vzhledem k tomu, že `onBeforeSendHeaders` a další posluchači již nejsou blokováni, je nemůžeme ve všech případech smazat. Pomocí [tohoto testu](https://testcases.agrd.dev/Filters/cookie-rules/test-cookie-rules) můžete zkontrolovat, zda pravidlo funguje.
+In [AdGuard for Chrome MV3][ext-mv3] we delete cookies in 2 ways: from `content-script` side (to which we have access) and from `onBeforeSendHeaders` listener. Since `onBeforeSendHeaders` and other listeners are no longer blocking, we are not able to delete them in all cases. You can check if a rule works with [this test](https://testcases.agrd.dev/Filters/cookie-rules/test-cookie-rules).
:::
:::caution Omezení
-Pravidla `$cookie` podporují tři typy modifikátorů: `$domain`, `$~domain`, `$important`, `$third-party`, `$~third-party`, `strict-third-party` a `strict-first-party`.
+`$cookie` rules support these types of modifiers: `$domain`, `$~domain`, `$important`, `$third-party`, `$~third-party`, `strict-third-party`, and `strict-first-party`.
:::
:::info Kompatibilita
-Pravidla s modifikátorem `$cookie` nejsou podporována Blokátorem obsahu AdGuard, AdGuardem pro iOS a AdGuardem pro Safari.
+Rules with `$cookie` modifier are not supported by AdGuard Content Blocker, AdGuard for iOS, and AdGuard for Safari.
:::
#### **`$csp`** {#csp-modifier}
-Tento modifikátor zcela mění chování pravidla. Pokud je použitý na pravidlo, pravidlo nezablokuje odpovídající požadavek. Namísto toho se upraví záhlaví odpovědí.
+This modifier completely changes the rule behavior. If it is applied to a rule, the rule will not block the matching request. Response headers will be modified instead.
:::info
-Pro použití tohoto typu pravidel je nutné mít základní znalosti o vrstvě zabezpečení [Content Security Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy).
+In order to use this type of rules, it is required to have the basic understanding of the [Content Security Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy) security layer.
:::
-U požadavků, které odpovídají pravidlu `$csp`, posílíme zásady zabezpečení odezvy posílením zásad zabezpečení obsahu, podobně jako u zásad zabezpečení obsahu modifikátoru obsahu `$csp`. Pravidla `$csp` jsou aplikována nezávisle na jakémkoli jiném typu pravidla. Mohou je ovlivnit **pouze výjimky na úrovni dokumentu** (viz část s příklady), ale žádná jiná základní pravidla.
+For the requests matching a `$csp` rule, we will strengthen response security policy by enhancing the content security policy, similar to the content security policy of the `$csp` modifier contents. `$csp` rules are applied independently from any other rule type. **Only document-level exceptions** can influence it (see the examples section), but no other basic rules.
-**Vícenásobná pravidla odpovídajících jednomu požadavku**
+**Multiple rules matching a single request**
-V případě, že jednomu požadavku odpovídá více pravidel `$csp`, použijeme každé z nich.
+In case if multiple `$csp` rules match a single request, we will apply each of them.
**Syntaxe**
-Syntaxe hodnoty `$csp` je podobná syntaxi záhlaví Content Security Policy.
+`$csp` value syntax is similar to the Content Security Policy header syntax.
-Hodnota `$csp` může být v případě pravidel pro výjimky prázdná. Viz níže uvedený oddíl s příklady.
+`$csp` value can be empty in the case of exception rules. See examples section below.
**Příklady**
@@ -1535,17 +1548,17 @@ Hodnota `$csp` může být v případě pravidel pro výjimky prázdná. Viz ní
:::info Kompatibilita
-Pravidla s modifikátorem `$csp` nejsou podporována Blokátorem obsahu AdGuard, AdGuardem pro iOS a AdGuardem pro Safari.
+Rules with `$csp` modifier are not supported by AdGuard Content Blocker, AdGuard for iOS and AdGuard for Safari.
:::
#### **`$hls`** {#hls-modifier}
-Pravidla `$hls` upravují odpověď na shodný požadavek. Jsou určena k pohodlnému odstraňování segmentů ze seznamů stop [HLS playlists (RFC 8216)](https://datatracker.ietf.org/doc/html/rfc8216).
+`$hls` rules modify the response of a matching request. They are intended as a convenient way to remove segments from [HLS playlists (RFC 8216)](https://datatracker.ietf.org/doc/html/rfc8216).
:::note
-Slovo "segment" v tomto dokumentu znamená buď "mediální segment" nebo "seznam skladeb" jako součást "hlavního seznamu skladeb": pravidla `$hls` nerozlišují mezi "hlavním seznamem skladeb" a "mediálním seznamem skladeb".
+The word "segment" in this document means either a "Media Segment" or a "playlist" as part of a "Master Playlist": `$hls` rules do not distinguish between a "Master Playlist" and a "Media Playlist".
:::
@@ -1556,24 +1569,24 @@ Slovo "segment" v tomto dokumentu znamená buď "mediální segment" nebo "sezna
- `t` — namísto testování adresy URL segmentu otestujte každý znak segmentu podle regulárního výrazu. Segment se shodným znakem je odstraněn;
- `i` — regulární výraz nerozlišuje velká a malá písmena.
-Znaky `/`, `$` a `,` musí být uvnitř `regexp` uvozeny pomocí `\`.
+The characters `/`, `$` and `,` must be escaped with `\` inside `regexp`.
**Výjimky**
-Základní výjimky URL nesmí zakázat pravidla s modifikátorem `$hls`. Lze je zakázat, jak je popsáno níže:
+Basic URL exceptions shall not disable rules with the `$hls` modifier. They can be disabled as described below:
- `@@||example.org^$hls` zakáže všechna pravidla `$hls` pro odpovědi z URL odpovídajících `||example.org^`.
- `@@||example.org^$hls=text` zakáže všechna pravidla `$hls` s hodnotou modifikátoru `$hls` shodným s `text` pro odpovědi z URL odpovídajících `||example.org^`.
:::tip
-Pravidla `$hls` lze také zakázat pravidly výjimek `$document`, `$content` a `$urlblock`.
+`$hls` rules can also be disabled by `$document`, `$content` and `$urlblock` exception rules.
:::
:::note
-Když vícenásobná pravidla `$hls` odpovídají stejnému požadavku, jejich účinek je kumulativní.
+When multiple `$hls` rules match the same request, their effect is cumulative.
:::
@@ -1583,26 +1596,26 @@ Když vícenásobná pravidla `$hls` odpovídají stejnému požadavku, jejich
- `||example.org^$hls=/\/videoplayback\/?\?.*\&source=dclk_video_ads/i` dosáhne víceméně téhož pomocí regulárního výrazu namísto vzoru URL.
- `||example.org^$hls=/#UPLYNK-SEGMENT:.*\,ad/t` odstraní všechny segmenty, které mají odpovídající znak.
-**Anatomie seznamu stop HLS**
+**Anatomy of an HLS playlist**
-Stručné shrnutí [specifikace](https://datatracker.ietf.org/doc/html/rfc8216):
+A quick summary of the [specification](https://datatracker.ietf.org/doc/html/rfc8216):
-1. Seznam stop HLS je kolekce textových řádků
-1. Řádek může být prázdný, komentář (začíná `#`), znak (také začíná `#`, lze jej rozpoznat pouze podle názvu) nebo URL
-1. Řádek URL se nazývá "segment"
-1. Znaky se mohou vztahovat na jeden segment, tj. první řádek adresy URL za znakem, na všechny segmenty následující za znakem až do znaku se stejným názvem nebo na celý seznam skladeb
+1. An HLS playlist is a collection of text lines
+1. A line may be empty, a comment (starts with `#`), a tag (also starts with `#`, can only be recognized by name) or a URL
+1. A URL line is called a "segment"
+1. Tags may apply to a single segment, i.e. the first URL line after the tag, to all segments following the tag and until the tag with the same name, or to the whole playlist
-Některé specifické body týkající se fungování pravidel `$hls`:
+Some points specific to the operation of `$hls` rules:
-1. Při odstranění segmentu se odstraní také všechny znaky, které se vztahují pouze k tomuto segmentu
-1. Pokud se znak vztahuje na více segmentů a všechny tyto segmenty jsou odstraněny, je odstraněna i znak
-1. Protože neexistuje způsob, jak rozpoznat různé druhy znaků podle syntaxe, rozpoznáváme všechny znaky uvedené v RFC a některé nestandardní znaky, se kterými jsme se setkali v praxi. Všechny řádky začínající na `#`. Ty, které nejsou rozpoznány jako znak, jsou předány bez úprav a nejsou porovnávány s pravidly
-1. Značky nebudou přiřazeny, pokud se vztahují na celý seznam stop a k jejich odstranění nelze použít pravidla `$hls`, protože tyto typy pravidel jsou určeny pro odstraňování segmentů. Pokud víte, co děláte, můžete pomocí pravidel `$replace` odstranit nebo přepsat pouze jeden znak ze seznamu skladeb
+1. When a segment is removed, all of the tags that apply only to that segment are also removed
+1. When there is a tag that applies to multiple segments, and all of those segments are removed, the tag is also removed
+1. Since there is no way to recognize different kinds of tags by syntax, we recognize all of the tags specified by the RFC, plus some non-standard tags that we have seen in the field. Any lines starting with `#` and not recognized as a tag are passed through without modification, and are not matched against the rules
+1. Tags will not be matched if they apply to the entire playlist, and `$hls` rules cannot be used to remove them, as these rule types are intended for segment removals. If you know what you are doing, you can use `$replace` rules to remove or rewrite just a single tag from the playlist
-**Příklad transformace provedené podle pravidel:**
+**An example of a transformation done by the rules:**
-Původní odezva
+Original response
```text
#EXTM3U
@@ -1629,7 +1642,7 @@ preroll.ts
-Použitá pravidla
+Applied rules
```adblock
||example.org^$hls=preroll
@@ -1639,7 +1652,7 @@ preroll.ts
-Modifikovaná odpověď
+Modified response
```text
#EXTM3U
@@ -1667,13 +1680,13 @@ preroll.ts
:::info Kompatibilita
-Pravidla s modifikátorem `$hls` jsou podporována AdGuardem pro Windows, Mac a Android s [CoreLibs][] v1.10 nebo novější.
+Rules with the `$hls` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.10 or later.
:::
#### **`$inline-script`** {#inline-script-modifier}
-Modifikátor `$inline-script` je určen k blokování in-line JavaScriptu vloženého do webové stránky pomocí zásad zabezpečení obsahu (CSP). Zlepšuje zabezpečení a soukromí tím, že zabraňuje použití in-line reklam nebo potenciálně škodlivých skriptů. Pravidlo `||example.org^$inline-script` se převádí na syntaxi pravidel CSP:
+The `$inline-script` modifier is designed to block inline JavaScript embedded into the web page, using Content Security Policy (CSP). It improves security and privacy by preventing application of inline ads or potentially malicious scripts. The rule `||example.org^$inline-script` is converting into the CSP-syntax rule:
```adblock
||example.org^$csp=script-src 'self' 'unsafe-eval' http: https: data: blob: mediastream: filesystem:
@@ -1681,7 +1694,7 @@ Modifikátor `$inline-script` je určen k blokování in-line JavaScriptu vlože
#### **`$inline-font`** {#inline-font-modifier}
-Modifikátor `$inline-font` je určen k blokování in-line fontů vložených do webové stránky pomocí zásad zabezpečení obsahu (CSP). Zlepšuje zabezpečení a soukromí tím, že zabraňuje použití in-line fontů, které by mohly být použity ke shromažďování dat a čtení digitálních otisků. Pravidlo `||example.org^$inline-font` se převádí na syntaxi pravidel CSP:
+The `$inline-font` modifier is designed to block inline fonts embedded into the web page, using Content Security Policy (CSP). It improves security and privacy by preventing application of inline fonts that could be used for data collection and fingerprinting. The rule `||example.org^$inline-font` is converting into the CSP-syntax rule:
```adblock
||example.org^$csp=font-src 'self' 'unsafe-eval' http: https: data: blob: mediastream: filesystem:
@@ -1689,46 +1702,46 @@ Modifikátor `$inline-font` je určen k blokování in-line fontů vložených d
#### **`$jsonprune`** {#jsonprune-modifier}
-Pravidla `$jsonprune` upravují odpověď na odpovídající požadavek odstraněním položek JSON, které odpovídají upravenému výrazu [JSONPath](https://goessner.net/articles/JsonPath/). Nemění odpovědi, které nejsou platnými dokumenty JSON.
+`$jsonprune` rules modify the response to a matching request by removing JSON items that match a modified [JSONPath](https://goessner.net/articles/JsonPath/) expression. They do not modify responses which are not valid JSON documents.
-V AdGuardu pro Windows, Mac a Android s [CoreLibs][] v1.11 nebo novější, `$jsonprune` podporuje také úpravu dokumentů JSONP (padded JSON).
+In AdGuard for Windows, Mac, and Android with [CoreLibs][] v1.11 or later, `$jsonprune` also supports modifying JSONP (padded JSON) documents.
**Syntaxe**
- `||example.org^$jsonprune=expression` odstraní z odpovědi položky, které odpovídají upravenému výrazu JSONPath `expression`.
-Vzhledem ke způsobu zpracování pravidel musí být znaky `$` a `,` uvnitř `výrazu` uvozeny pomocí `\`.
+Due to the way rule parsing works, the characters `$` and `,` must be escaped with `\` inside `expression`.
-Upravená syntaxe JSONPath má oproti původní následující rozdíly:
+The modified JSONPath syntax has the following differences from the original:
-1. Výrazy skriptů nejsou podporovány
-1. Podporované výrazy filtrů jsou:
- - `?(has )` — "true", pokud má aktuální objekt zadaný klíč
- - `?(key-eq )` — "true", pokud má aktuální objekt zadaný klíč a jeho hodnota se rovná zadané hodnotě
- - `?(key-substr )` — "true", pokud je zadaná hodnota podřetězcem hodnoty zadaného klíče aktuálního objektu
-1. Mezery mimo řetězce s dvojitými nebo jednoduchými uvozovkami nemají žádný význam
-1. Lze použít řetězce s dvojitými i jednoduchými uvozovkami
-1. Výrazy končící na `..` nejsou podporovány
-1. V hranatých závorkách lze zadat vícero dílků pole
+1. Script expressions are not supported
+1. The supported filter expressions are:
+ - `?(has )` — true if the current object has the specified key
+ - `?(key-eq )` — true if the current object has the specified key, and its value is equal to the specified value
+ - `?(key-substr )` — true if the specified value is a substring of the value of the specified key of the current object
+1. Whitespace outside of double- or single-quoted strings has no meaning
+1. Both double- and single-quoted strings can be used
+1. Expressions ending with `..` are not supported
+1. Multiple array slices can be specified in square brackets
-Existují různé online nástroje, které usnadňují práci s výrazy JSONPath:
+There are various online tools that make working with JSONPath expressions more convenient:
https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfinder.com/ https://jsonpath.com/
-Mějte však na paměti, že všechny implementace JSONPath mají jedinečné vlastnosti a jsou vzájemně nekompatibilní.
+Keep in mind, though, that all JSONPath implementations have unique features/quirks and are subtly incompatible with each other.
**Výjimky**
-Základní výjimky URL nesmí zakázat pravidla s modifikátorem `$jsonprune`. Lze je zakázat, jak je popsáno níže:
+Basic URL exceptions shall not disable rules with the `$jsonprune` modifier. They can be disabled as described below:
- `@@||example.org^$jsonprune` zakáže všechna pravidla `$jsonprune` pro odpovědi z URL odpovídajících `||example.org^`.
- `@@||example.org^$jsonprune=text` zakáže všechna pravidla `$jsonprune` s hodnotou modifikátoru `$jsonprune` shodným s `text` pro odpovědi z URL odpovídajících `||example.org^`.
-Pravidla `$jsonprune` lze také zakázat pravidly výjimek `$document`, `$content` a `$urlblock`.
+`$jsonprune` rules can also be disabled by `$document`, `$content` and `$urlblock` exception rules.
:::note
-Když vícenásobná pravidla `$jsonprune` odpovídají stejnému požadavku, jsou seřazena v lexikografickém pořadí, první pravidlo je aplikováno na původní odpověď a každé ze zbývajících pravidel je aplikováno na výsledek použití předchozího.
+When multiple `$jsonprune` rules match the same request, they are sorted in lexicographical order, the first rule is applied to the original response, and each of the remaining rules is applied to the result of applying the previous one.
:::
@@ -1737,7 +1750,7 @@ Když vícenásobná pravidla `$jsonprune` odpovídají stejnému požadavku, js
- `||example.org^$jsonprune=\$..[one\, "two three"]` odstraní všechny výskyty klíčů "one" a "two three" kdekoli v dokumentu JSON.
-Vstup
+Input
```json
{
@@ -1752,7 +1765,7 @@ Když vícenásobná pravidla `$jsonprune` odpovídají stejnému požadavku, js
-Výstup
+Output
```json
{
@@ -1767,7 +1780,7 @@ Když vícenásobná pravidla `$jsonprune` odpovídají stejnému požadavku, js
- `||example.org^$jsonprune=\$.a[?(has ad_origin)]` odstraní všechny potomky `a`, které mají klíč `ad_origin`.
-Vstup
+Input
```json
{
@@ -1786,7 +1799,7 @@ Když vícenásobná pravidla `$jsonprune` odpovídají stejnému požadavku, js
-Výstup
+Output
```json
{
@@ -1803,7 +1816,7 @@ Když vícenásobná pravidla `$jsonprune` odpovídají stejnému požadavku, js
- `||example.org^$jsonprune=\$.*.*[?(key-eq 'Some key' 'Some value')]` odstraní všechny položky, které jsou na úrovni vnoření 3 a mají vlastnost "Some key" rovnu "Some value".
-Vstup
+Input
```json
{
@@ -1815,7 +1828,7 @@ Když vícenásobná pravidla `$jsonprune` odpovídají stejnému požadavku, js
-Výstup
+Output
```json
{
@@ -1826,14 +1839,14 @@ Když vícenásobná pravidla `$jsonprune` odpovídají stejnému požadavku, js
-**Vnořené výrazy JSONPath**
+**Nested JSONPath expressions**
-V AdGuardu pro Windows, Mac a Android s [CoreLibs][] v1.11 nebo novější, lze výrazy JSONPath použít jako klíče ve výrazech filtru.
+In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPath expressions may be used as keys in filter expressions.
- `||example.org^$jsonprune=\$.elems[?(má "\$.abc")]` odstraní všechny potomky `elems`, které mají vlastnost volitelnou výrazem JSONPath `$.abc`.
-Vstup
+Input
```json
{
@@ -1853,7 +1866,7 @@ V AdGuardu pro Windows, Mac a Android s [CoreLibs][] v1.11 nebo novější, lze
-Výstup
+Output
```json
{
@@ -1871,13 +1884,13 @@ V AdGuardu pro Windows, Mac a Android s [CoreLibs][] v1.11 nebo novější, lze
- `||example.org^$jsonprune=\$.elems[?(key-eq "\$.a.b.c" "abc")]` odstraní všechny potomky `elems`, které mají vlastnost volitelnou pomocí výrazu JSONPath `$.a.b.c` s hodnotou rovnou `"abc"`.
-Vstup
+Input
```json
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
@@ -1889,7 +1902,7 @@ V AdGuardu pro Windows, Mac a Android s [CoreLibs][] v1.11 nebo novější, lze
-Výstup
+Output
```json
{
@@ -1912,32 +1925,32 @@ V AdGuardu pro Windows, Mac a Android s [CoreLibs][] v1.11 nebo novější, lze
:::info Kompatibilita
-Pravidla s modifikátorem `$jsonprune` jsou podporována AdGuardem pro Windows, Mac, Android a Linux s [CoreLibs][] v1.10 nebo novější.
+Rules with the `$jsonprune` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.10 or later.
:::
#### **`$xmlprune`** {#xmlprune-modifier}
-Pravidla `$xmlprune` upravují odpověď na odpovídající požadavek odstraněním položek XML, které odpovídají upravenému výrazu[XPath 1.0](https://www.w3.org/TR/1999/REC-xpath-19991116/). Výraz musí vrátit [node-set](https://www.w3.org/TR/1999/REC-xpath-19991116/#node-sets). `$xmlprune` pravidla neupravují odpovědi, které nejsou dobře formulovanými dokumenty XML.
+`$xmlprune` rules modify the response to a matching request by removing XML items that match an [XPath 1.0](https://www.w3.org/TR/1999/REC-xpath-19991116/) expression. The expression must return a [node-set](https://www.w3.org/TR/1999/REC-xpath-19991116/#node-sets). `$xmlprune` rules do not modify responses which are not well-formed XML documents.
**Syntaxe**
- `||example.org^$xmlprune=expression` odstraní z odpovědi položky, které odpovídají výrazu XPath `expression`.
-Vzhledem ke způsobu zpracování pravidel musí být znaky `$` a `,` uvnitř `výrazu` uvozeny pomocí `\`.
+Due to the way rule parsing works, the characters `$` and `,` must be escaped with `\` inside `expression`.
**Výjimky**
-Základní výjimky URL nesmí zakázat pravidla s modifikátorem `$xmlprune`. Lze je zakázat, jak je popsáno níže:
+Basic URL exceptions shall not disable rules with the `$xmlprune` modifier. They can be disabled as described below:
- `@@||example.org^$xmlprune` zakáže všechna pravidla `$xmlprune` pro odpovědi z URL odpovídajících `||example.org^`.
- `@@||example.org^$xmlprune=text` zakáže všechna pravidla `$xmlprune` s hodnotou modifikátoru `$xmlprune` shodným s `text` pro odpovědi z URL odpovídajících `||example.org^`.
-Pravidla `$xmlprune` lze také zakázat pravidly výjimek `$document`, `$content` a `$urlblock`.
+`$xmlprune` rules can also be disabled by `$document`, `$content` and `$urlblock` exception rules.
:::note
-Když je více pravidel `$xmlprune` odpovídá stejnému požadavku, jsou použita v lexikografickém pořadí.
+When multiple `$xmlprune` rules match the same request, they are applied in lexicographical order.
:::
@@ -1946,7 +1959,7 @@ Když je více pravidel `$xmlprune` odpovídá stejnému požadavku, jsou použi
- `||example.org^$xmlprune=/bookstore/book[position() mod 2 = 1]` odstraní z knihkupectví knihy s lichými čísly.
-Vstup
+Input
```xml
@@ -1991,7 +2004,7 @@ Když je více pravidel `$xmlprune` odpovídá stejnému požadavku, jsou použi
-Výstup
+Output
```xml
@@ -2024,7 +2037,7 @@ Když je více pravidel `$xmlprune` odpovídá stejnému požadavku, jsou použi
- `||example.org^$xmlprune=/bookstore/book[year = 2003]` odstraní knihy z roku 2003 z knihkupectví.
-Vstup
+Input
```xml
@@ -2069,7 +2082,7 @@ Když je více pravidel `$xmlprune` odpovídá stejnému požadavku, jsou použi
-Výstup
+Output
```xml
@@ -2102,7 +2115,7 @@ Když je více pravidel `$xmlprune` odpovídá stejnému požadavku, jsou použi
- `||example.org^$xmlprune=//*/@*` odstraní všechny atributy ze všech prvků.
-Vstup
+Input
```xml
@@ -2122,7 +2135,7 @@ Když je více pravidel `$xmlprune` odpovídá stejnému požadavku, jsou použi
-Výstup
+Output
```xml
@@ -2150,24 +2163,24 @@ Když je více pravidel `$xmlprune` odpovídá stejnému požadavku, jsou použi
:::info Kompatibilita
-Pravidla s modifikátorem `$xmlprune` jsou podporována AdGuardem pro Windows, Mac, Android a Linux s [CoreLibs][] v1.15 nebo novější.
+Rules with the `$xmlprune` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.15 or later.
:::
#### **`$network`** {#network-modifier}
-Jedná se v podstatě o pravidla typu brány Firewall, která umožňují plně zablokovat nebo odblokovat přístup na zadanou vzdálenou adresu.
+This is basically a Firewall-like rule allowing to fully block or unblock access to a specified remote address.
-1. Pravidla `$network` odpovídají **pouze IP adresám**! Nelze je použít k zablokování nebo odblokování přístupu k doméně.
-2. Chcete-li se shodovat s adresou IPv6, musíte použít sbalenou syntaxi, např. `[2001:4860:4860::8888]$network` namísto `[2001:4860:4860:0:0:0:0:8888]$network`.
-3. Pravidlo seznamu povolených `$network` způsobí, že AdGuard bude obcházet data odpovídajícího koncového bodu, proto nebude provádět žádné další filtrování.
-4. Pokud část IP začíná a končí znakem `/`, je považována za regulární výraz.
+1. `$network` rules match **IP addresses only**! You cannot use them to block or unblock access to a domain.
+2. To match an IPv6 address, you have to use the collapsed syntax, e.g. use `[2001:4860:4860::8888]$network` instead of `[2001:4860:4860:0:0:0:0:8888]$network`.
+3. An allowlist `$network` rule makes AdGuard bypass data to the matching endpoint, hence there will be no further filtering at all.
+4. If the IP part starts and ends with `/` character, it is treated as a regular expression.
-Pro lepší pochopení regulárních výrazů doporučujeme seznámit se s tímto [článkem](#regexp-support).
+We recommend to get acquainted with this [article](#regexp-support) for better understanding of regular expressions.
:::caution Omezení
-Modifikátor `$network` lze v pravidlech použít pouze společně s modifikátory `$app` a `$important`, nikoli s žádnými jinými modifikátory.
+The `$network` modifier can only be used in rules together with the `$app` and `$important` modifiers, and not with any other modifiers.
:::
@@ -2182,32 +2195,32 @@ Modifikátor `$network` lze v pravidlech použít pouze společně s modifikáto
:::info Kompatibilita
-Pouze AdGuard pro Windows, Mac a Android jsou technicky schopné používat pravidla s modifikátorem `$network`.
+Only AdGuard for Windows, Mac, and Android are technically capable of using rules with `$network` modifier.
:::
#### **`$permissions`** {#permissions-modifier}
-Tento modifikátor zcela mění chování pravidla. Pokud je použitý na pravidlo, pravidlo nezablokuje odpovídající požadavek. Namísto toho se upraví záhlaví odpovědí.
+This modifier completely changes the rule behavior. If it is applied to a rule, the rule will not block the matching request. Response headers will be modified instead.
:::info
-Pro použití tohoto typu pravidel je nutné mít základní znalosti o vrstvě zabezpečení [Permissions Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/Permissions_Policy).
+In order to use this type of rules, it is required to have a basic understanding of the [Permissions Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/Permissions_Policy) security layer.
:::
-U požadavků, které odpovídají pravidlu `$permissions`, AdGuard posiluje zásady funkcí odpovědi přidáním dalších zásad oprávnění, které se rovnají obsahu modifikátoru `$permissions`. Pravidla `$permissions` jsou aplikována nezávisle na jakémkoli jiném typu pravidla. Mohou je ovlivnit **pouze výjimky na úrovni dokumentu** (viz část s příklady), ale žádná jiná základní pravidla.
+For the requests matching a `$permissions` rule, AdGuard strengthens response's permissions policy by adding an additional permission policy equal to the `$permissions` modifier contents. `$permissions` rules are applied independently from any other rule type. **Only document-level exceptions** can influence it (see the examples section), but no other basic rules.
**Syntaxe**
-Hodnota syntaxe `$permissions` je shodná se [syntaxí](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Permissions-Policy) záhlaví `Permissions-Policy` s následujícími výjimkami:
+`$permissions` value syntax is identical to that of the `Permissions-Policy` header [syntax](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Permissions-Policy) with the following exceptions:
-1. Čárka, která odděluje více prvků **MUSÍ být uvozena** – viz příklady níže.
-2. Místo čárky lze pro oddělení funkcí použít znak `(|)`.
+1. A comma that separates multiple features **MUST** be escaped — see examples below.
+2. A pipe character (`|`) can be used instead of a comma to separate features.
-Seznam dostupných direktiv je k dispozici [zde](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Permissions-Policy#directives).
+The list of available directives is available [here](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Permissions-Policy#directives).
-Hodnota `$permissions` může být v případě pravidel pro výjimky prázdná — viz příklady níže.
+`$permissions` value can be empty in the case of exception rules — see examples below.
**Příklady**
@@ -2220,13 +2233,13 @@ Hodnota `$permissions` může být v případě pravidel pro výjimky prázdná
:::note
-Pravidla `$permissions` jsou účinná pouze pro požadavky hlavního rámce a vedlejšího rámce. To znamená, že se použijí při načtení stránky nebo iframe.
+`$permissions` rules only take effect for main frame and sub frame requests. This means they are applied when a page is loaded or when an iframe is loaded.
:::
:::note
-Pokud existuje více pravidel `$permissions`, která odpovídají stejnému požadavku, bude do odpovědi přidáno více záhlaví `Permissions-Policy` pro každé pravidlo s jejich hodnotou `$permissions`. Pokud tedy máte dvě pravidla: `||example.org^$permissions=autoplay=()` a `||example.org^$permissions=geolocation=()\,camera=()`, která odpovídají stejnému požadavku, bude odpověď obsahovat dvě záhlaví `Permissions-Policy`: `autoplay=()` a `geolocation=()\,camera=()`.
+If there are multiple `$permissions` rules that match the same request, multiple `Permissions-Policy` headers will be added to the response for each rule with their `$permissions` value. So if you have two rules: `||example.org^$permissions=autoplay=()` and `||example.org^$permissions=geolocation=()\,camera=()` that match the same request, the response will contain two `Permissions-Policy` headers: `autoplay=()` and `geolocation=()\,camera=()`.
:::
@@ -2234,15 +2247,15 @@ Pokud existuje více pravidel `$permissions`, která odpovídají stejnému pož
:::caution Omezení
-Firefox ignoruje záhlaví `Permissions-Policy`. Další informace naleznete v [tomto hlášení](https://bugzilla.mozilla.org/show_bug.cgi?id=1694922).
+Firefox ignores the `Permissions-Policy` header. For more information, see [this issue](https://bugzilla.mozilla.org/show_bug.cgi?id=1694922).
:::
:::caution Omezení
-1. Zakázané znaky v `$permissions` hodnotě: `$`.
-2. `$permissions` je kompatibilní s omezenou sadou modifikátorů: `$domain`, `$important`, `$subdocument` a [modifikátory typu obsahu](#content-type-modifiers).
-3. Pravidla `$permissions`, která neobsahují žádné modifikátory typu obsahu [](#content-type-modifiers), budou odpovídat pouze požadavkům, jejichž typem obsahu je `document`.
+1. Characters forbidden in the `$permissions` value: `$`.
+2. `$permissions` is compatible with a limited set of modifiers: `$domain`, `$important`, `$subdocument`, and [content-type modifiers](#content-type-modifiers).
+3. `$permissions` rules that do not have any [content-type modifiers](#content-type-modifiers) will match only requests where content type is `document`.
:::
@@ -2255,15 +2268,15 @@ Firefox ignoruje záhlaví `Permissions-Policy`. Další informace naleznete v [
#### **`$redirect`** {#redirect-modifier}
-AdGuard je schopen přesměrovat webové požadavky na místní "zdroj".
+AdGuard is able to redirect web requests to a local "resource".
**Syntaxe**
-AdGuard používá stejnou syntaxi pravidel filtrování jako uBlock Origin. Je také kompatibilní s modifikátorem ABP `$rewrite=abp-resource`.
+AdGuard uses the same filtering rule syntax as uBlock Origin. Also, it is compatible with ABP `$rewrite=abp-resource` modifier.
-`$redirect` je modifikátor pro [základní pravidla filtrování](#basic-rules), takže pravidla s tímto modifikátorem podporují všechny ostatní základní modifikátory, jako jsou `$domain`, `$third-party`, `$script` atd.
+`$redirect` is a modifier for the [basic filtering rules](#basic-rules) so rules with this modifier support all other basic modifiers like `$domain`, `$third-party`, `$script`, etc.
-Hodnota modifikátoru `$redirect` musí být název zdroje, který bude použit pro přesměrování.
+The value of the `$redirect` modifier must be the name of the resource that will be used for redirection.
##### Zakázání pravidel `$redirect`
@@ -2272,15 +2285,15 @@ Hodnota modifikátoru `$redirect` musí být název zdroje, který bude použit
- `@@||example.org^$redirect` zakáže všechna pravidla `$redirect` pro URL adresy, které odpovídají `||example.org^`.
- `@@||example.org^$redirect=nooptext` zakáže všechna pravidla s `$redirect=nooptext` pro všechny požadavky, které odpovídají `||example.org^`.
-Další informace o přesměrování a použití jsou k dispozici [na GitHubu](https://github.com/AdguardTeam/Scriptlets#redirect-resources).
+More information on redirects and their usage is available [on GitHub](https://github.com/AdguardTeam/Scriptlets#redirect-resources).
##### Priority pravidel `$redirect` {#redirect-rule-priorities}
-Pravidla `$redirect` mají vyšší prioritu než běžná základní pravidla blokování. To znamená, že pokud existuje základní pravidlo blokování, pravidlo `$redirect` jej přepíše. Pravidla seznamu povolených se znakem `@@` mají vyšší prioritu než pravidla `$redirect`. Pokud se základní pravidlo s modifikátorem `$important` a pravidlem `$redirect` shoduje se stejnou adresou URL, je druhé pravidlo přepsáno, pokud není též označeno jako `$important`.
+`$redirect` rules have higher priority than regular basic blocking rules. This means that if there is a basic blocking rule, the `$redirect` rule will override it. Allowlist rules with `@@` mark have higher priority than `$redirect` rules. If a basic rule with the `$important` modifier and the `$redirect` rule matches the same URL, the latter is overridden unless it's also marked as `$important`.
-**Ve zkratce: `$important` > `@@` > `$redirect` > `basic rules`.**
+**In short: `$important` > `@@` > `$redirect` > `basic rules`.**
Další podrobnosti najdete v [prioritách pravidel](#rule-priorities).
@@ -2288,7 +2301,7 @@ Další podrobnosti najdete v [prioritách pravidel](#rule-priorities).
:::caution Omezení
-V [AdGuardu pro Chrome MV3][ext-mv3] nejsou podporována pravidla `$redirect`.
+In [AdGuard for Chrome MV3][ext-mv3] allowlist rules with `$redirect` are not supported.
:::
@@ -2301,11 +2314,11 @@ V [AdGuardu pro Chrome MV3][ext-mv3] nejsou podporována pravidla `$redirect`.
#### **`$redirect-rule`** {#redirect-rule-modifier}
-Toto je v podstatě alias [`$redirect`](#redirect-modifier), protože má stejné hodnoty "přesměrování" a logika je téměř podobná. Rozdíl je v tom, že `$redirect-rule` se použije pouze v případě, kdy je cílový požadavek blokován jiným základním pravidlem.
+This is basically an alias to [`$redirect`](#redirect-modifier) since it has the same "redirection" values and the logic is almost similar. The difference is that `$redirect-rule` is applied only in the case when the target request is blocked by a different basic rule.
Další podrobnosti najdete v [prioritách pravidel](#rule-priorities).
-Negace `$redirect-rule` funguje úplně stejně jako u běžných pravidel `$redirect`. Ještě více než to, bude `@@||example.org^$redirect` negovat jak pravidla `$redirect`, tak `$redirect-rule`.
+Negating `$redirect-rule` works exactly the same way as for regular `$redirect` rules. Even more than that, `@@||example.org^$redirect` will negate both `$redirect` and `$redirect-rule` rules.
**Příklady**
@@ -2314,21 +2327,21 @@ Negace `$redirect-rule` funguje úplně stejně jako u běžných pravidel `$red
||example.org^$redirect-rule=noopjs
```
-V tomto případě budou pouze požadavky na `example.org/script.js` "přesměrovány" na `noopjs`. Všechny ostatní požadavky na `example.org` zůstanou nedotčeny.
+In this case, only requests to `example.org/script.js` will be "redirected" to `noopjs`. All other requests to `example.org` will be kept intact.
:::info Kompatibilita
-Pravidla s modifikátorem `$redirect-rule` nejsou podporována [Blokátorem obsahu AdGuard][and-cb], [AdGuardem pro iOS][ios-app], [AdGuardem pro Safari][ext-saf] a [AdGuardem pro Chrome MV3][ext-mv3]. [Diskuse o přidání podpory pro pravidla `$redirect-rule` v rozšířeních Chrome MV3](https://github.com/w3c/webextensions/issues/493) je aktuálně otevřená.
+Rules with `$redirect-rule` modifier are not supported by [AdGuard Content Blocker][and-cb], [AdGuard for iOS][ios-app], [AdGuard for Safari][ext-saf], and [AdGuard for Chrome MV3][ext-mv3]. [The discussion about adding support for `$redirect-rule` rules in Chrome MV3 extensions](https://github.com/w3c/webextensions/issues/493) is currently open.
:::
#### **`$referrerpolicy`** {#referrerpolicy-modifier}
-Tato pravidla umožňují přepsat [zásady odkazovačů](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Referrer-Policy) stránky. V odezvách na shodné požadavky budou všechny hlavičky `Referrer-Policy` nahrazeny jedinou hlavičkou s hodnotou rovnou hodnotě modifikátoru shodného pravidla. Pokud odezva obsahuje dokument HTML se značkou `)[\s\S]*<\/VAST>/\$1<\/VAST>/i
```
-Toto pravidlo má tři části:
+There are three parts in this rule:
- `regexp` — `()(.|\s)*<\/VAST>`;
- `replacement` — `\$1<\/VAST>` kde `$` je uvozeno;
- `modifiers` — `i` pro necitlivé vyhledávání.
-Jak toto pravidlo funguje, se můžete podívat zde: http://regexr.com/3cesk
+You can see how this rule works here: http://regexr.com/3cesk
-**Vícenásobná pravidla `$replace`**
+**Multiple `$replace` rules**
1. `||example.org^$replace=/X/Y/`
2. `||example.org^$replace=/Z/Y/`
@@ -2774,7 +2787,7 @@ Jak toto pravidlo funguje, se můžete podívat zde: http://regexr.com/3cesk
- Jak pravidlo 1, tak pravidlo 2 se použijí na všechny požadavky odeslané na `example.org`.
- Pravidlo 2 je zakázáno pro požadavky odpovídající na `||example.org/page/`, **ale pravidlo 1 stále funguje!**
-**Zakázání pravidel `$replace`**
+**Disabling `$replace` rules**
- `@@||example.org^$replace` zakáže všechna pravidla `$replace` odpovídající na `||example.org^`.
- `@@||example.org^$document` nebo `@@||example.org^$content` zakáže všechna pravidla `$replace` **pocházející ze** stránek `example.org` **včetně stránky samotné**.
@@ -2788,29 +2801,29 @@ Jak toto pravidlo funguje, se můžete podívat zde: http://regexr.com/3cesk
:::info Kompatibilita
-Pravidla s modifikátorem `$replace` podporuje AdGuard pro Windows, Mac, Android a Rozšíření prohlížeče AdGuard pro Chrome, Firefox a Edge. Taková pravidla v rozšířeních pro jiné prohlížeče nefungují, protože nemohou měnit obsah na úrovni sítě.
+Rules with `$replace` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard Browser Extension for Firefox. Such rules do not work in extensions for other browsers because they are unable to modify content on the network level.
:::
#### **`$urltransform`** {#urltransform-modifier}
-Pravidla `$urltransform` vám umožňují upravit URL požadavku nahrazením textu, který odpovídá regulárnímu výrazu.
+The `$urltransform` rules allow you to modify the request URL by replacing text matched by a regular expression.
-**Funkce**
+**Features**
- Pravidla `$urltransform` se obvykle vztahují pouze na části URL týkající se cesty a dotazu, viz níže jedna výjimka.
- `$urltransform` nebude použito, pokud je původní URL blokována jinými pravidly.
- `$urltransform` se použije před pravidly `$removeparam`.
-Hodnota `$urltransform` může být pro pravidla výjimek prázdná.
+The `$urltransform` value can be empty for exception rules.
-**Vícenásobná pravidla odpovídajících jednomu požadavku**
+**Multiple rules matching a single request**
-Pokud jednomu požadavku odpovídá více pravidel `$urltransform`, použijeme každé z nich. **Pořadí je stanoveno abecedně.**
+If multiple `$urltransform` rules match a single request, we will apply each of them. **The order is defined alphabetically.**
**Syntaxe**
-`$urltransform` syntaxe je podobná nahrazování regulárními výrazy [v Perl](http://perldoc.perl.org/perlrequick.html#Search-and-replace).
+`$urltransform` syntax is similar to replacement with regular expressions [in Perl](http://perldoc.perl.org/perlrequick.html#Search-and-replace).
```text
urltransform = "/" regexp "/" replacement "/" modifiers
@@ -2820,17 +2833,17 @@ urltransform = "/" regexp "/" replacement "/" modifiers
- **`replacement`** — řetězec, který bude použit k nahrazení řetězce odpovídajícího `regexp`.
- **`modifiers`** — příznaky regulárního výrazu. Například `i` — necitlivé vyhledávání nebo `s` — jednořádkový režim.
-V hodnotě `$urltransform` musí být dva znaky uvozeny: čárka `,` a znak dolaru `$`. K tomu použijte znak zpětného lomítka `\`. Např. uvozená čárka vypadá takto: `\,`.
+In the `$urltransform` value, two characters must be escaped: the comma `,` and the dollar sign `$`. Use the backslash character `\` for this. For example, an escaped comma looks like this: `\,`.
-**Změna původu**
+**Changing the origin**
:::info Kompatibilita
-Tato část platí pouze pro AdGuard pro Windows, AdGuard pro Mac, AdGuard pro Android a Adguardem pro Linux s [CoreLibs][] v1.17 nebo novější.
+This section only applies to AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.17 or later.
:::
-Jak bylo uvedeno výše, pravidla `$urltransform` mohou normálně měnit pouze část URL obsahující cestu a dotaz. Pokud však pravidlo `regexp` začíná řetězcem `^http`, pak se prohledává celá adresa URL a pravidlo ji může upravit. Takové pravidlo se neuplatní, pokud transformace adresy URL nelze dosáhnout přesměrováním HTTP (například pokud je metoda požadavku `POST`).
+As stated above, normally `$urltransform` rules are only allowed to change the path and query parts of the URL. However, if the rule's `regexp` begins with the string `^http`, then the full URL is searched and can be modified by the rule. Such a rule will not be applied if the URL transformation can not be achieved via an HTTP redirect (for example, if the request's method is `POST`).
**Příklady**
@@ -2838,13 +2851,13 @@ Jak bylo uvedeno výše, pravidla `$urltransform` mohou normálně měnit pouze
||example.org^$urltransform=/(pref\/).*\/(suf)/\$1\$2/i
```
-Toto pravidlo má tři části:
+There are three parts in this rule:
- `regexp` — `(pref\/).*\/(suf)`;
- `replacement` — `\$1\$2` kde `$` je uvozeno;
- `modifiers` — `i` pro necitlivé vyhledávání.
-**Vícenásobná pravidla `$urltransform`**
+**Multiple `$urltransform` rules**
1. `||example.org^$urltransform=/X/Y/`
2. `||example.org^$urltransform=/Z/Y/`
@@ -2853,63 +2866,63 @@ Toto pravidlo má tři části:
- Jak pravidlo 1, tak pravidlo 2 se použijí na všechny požadavky odeslané na `example.org`.
- Pravidlo 2 je zakázáno pro požadavky odpovídající na `||example.org/page/`, **ale pravidlo 1 stále funguje!**
-**Opětovná shoda pravidel po transformaci URL**
+**Re-matching rules after transforming the URL**
-Po použití všech odpovídajících pravidel `$urltransform` bude transformovaný požadavek porovnán se všemi ostatními pravidly:
+After applying all matching `$urltransform` rules, the transformed request will be matched against all other rules:
-Např. s následujícími pravidly:
+E.g., with the following rules:
```adblock
||example.com^$urltransform=/firstpath/secondpath/
||example.com/secondpath^
```
-požadavek na `https://example.com/firstpath` bude zablokován.
+the request to `https://example.com/firstpath` will be blocked.
-**Zakázání pravidel `$urltransform`**
+**Disabling `$urltransform` rules**
- `@@||example.org^$urltransform` zakáže všechna pravidla `$urltransform` odpovídající na `||example.org^`.
- `@@||example.org^$urltransform=/Z/Y/` zakáže pravidlo s `$urltransform=/Z/Y/` pro jakýkoliv požadavek, který odpovídá `||example.org^`.
-Pravidla `$urltransform` lze také zakázat pravidly výjimek `$document` a `$urlblock`. Základní pravidla pro výjimky bez modifikátorů to však nedělají. Např. `@@||example.com^` nezakáže `$urltransform=/X/Y/` pro požadavky na **example.com**, ale `@@||example.com^$urlblock` ano.
+`$urltransform` rules can also be disabled by `$document` and `$urlblock` exception rules. But basic exception rules without modifiers do not do that. For example, `@@||example.com^` will not disable `$urltransform=/X/Y/` for requests to **example.com**, but `@@||example.com^$urlblock` will.
-**Příklad pravidla pro čištění partnerských odkazů**
+**The rule example for cleaning affiliate links**
-Mnoho webových stránek používá sledovací URL ke sledování kliknutí před přesměrováním na skutečný cíl. Tyto URL obsahují marketingové parametry a analytické tokeny, které lze odstranit, aby se zvýšila ochrana osobních údajů.
+Many websites use tracking URLs to monitor clicks before redirecting to the actual destination. These URLs contain marketing parameters and analytics tokens that can be removed to improve privacy.
-Níže je uveden příklad, jak získat čistý odkaz na cíl, abyste obešli sledovací webové stránky a přešli přímo na cíl.
+Below is an example of how to obtain the clean destination link to bypass tracking websites and go directly to the destination.
-V našem příkladu:
+In our example:
- 1. Počáteční URL (se sledováním kliknutí): `https://www.aff.example.com/visit?url=https%3A%2F%2Fwww.somestore.com%2F%26referrer%3Dhttps%3A%2F%2Fwww.aff.example.com%2F%26ref%3Dref-123`
- 1. Sledování URL po dekódování speciálních znaků: `https://www.aff.example.com/visit?url=https://www.somestore.com/`
- 1. Webové stránky, které chcete navštívit: `https://www.somestore.com`
+ 1. The initial URL (with click tracking): `https://www.aff.example.com/visit?url=https%3A%2F%2Fwww.somestore.com%2F%26referrer%3Dhttps%3A%2F%2Fwww.aff.example.com%2F%26ref%3Dref-123`
+ 1. Tracking URL after decoding special characters: `https://www.aff.example.com/visit?url=https://www.somestore.com/`
+ 1. The website you want to visit: `https://www.somestore.com`
-Abychom mohli vyčistit URL, musíme nejprve dekódovat speciální znaky (jako `%3A` → `:`, `%2F` → `/`, atd.) a získat skutečnou URL z parametrů sledování. K tomu použijeme modifikátor `$urltransform`. Následující 4 pravidla nahrazují symboly URL jejich skutečnými znaky:
+To clean the URL, we first need to decode special characters (like `%3A` → `:`, `%2F` → `/`, etc.) and extract the real URL from the tracking parameters. We will use the `$urltransform` modifier to do this. The following 4 rules replace URL-encoded symbols with their real characters:
`/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%3A/:/` `/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%2F/\//` `/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%3F/?/` `/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%3D/=/` `/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%26/&/`
-Poté musíme napsat pravidlo, které zablokuje sledovací webovou stránku a přesměruje vás přímo na cílovou adresu (somestore.com):
+After that, we need to write the rule that will block the tracking website and redirect you directly to the target address (somestore.com):
`/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com.*url=([^&]*).*/\$1/`
-Sledovací odkazy se nyní automaticky vyčistí a umožní přímou navigaci na cílovou webovou stránku bez sledování.
+Tracking links will now be automatically cleaned up, allowing direct navigation to the destination website without tracking.
:::caution Omezení
-Pravidla s modifikátorem `$urltransform` lze použít [**pouze v důvěryhodných filtrech**](#trusted-filters).
+Rules with the `$urltransform` modifier can only be used [**in trusted filters**](#trusted-filters).
:::
:::info Kompatibilita
-Pravidla s modifikátorem `$urltransform` jsou podporována AdGuardem pro Windows, Mac, Android a Linux s [CoreLibs][] v1.15 nebo novější.
+Rules with the `$urltransform` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.15 or later.
:::
#### **`noop`** {#noop-modifier}
-Modifikátor `noop` nedělá nic a lze jej použít pouze ke zvýšení čitelnosti pravidel. Skládá se ze sekvence znaků podtržítka (`_`) libovolné délky a může se v pravidle objevit tolikrát, kolikrát je potřeba.
+`noop` modifier does nothing and can be used solely to increase rules' readability. It consists of a sequence of underscore characters (`_`) of arbitrary length and can appear in a rule as often as needed.
**Příklady**
@@ -2920,19 +2933,19 @@ Modifikátor `noop` nedělá nic a lze jej použít pouze ke zvýšení čitelno
:::info Kompatibilita
-Pravidla s modifikátorem `noop` nejsou Blokátorem obsahu AdGuard podporována.
+Rules with `noop` modifier are not supported by AdGuard Content Blocker.
:::
#### **`$empty` (zastaralé)** {#empty-modifier}
-:::caution Upozornění na vyřazení
+:::caution Deprecation notice
-Tento modifikátor je zastaralý a nahrazuje jej modifikátor [`$redirect`](#redirect-modifier). Pravidla s `$empty` jsou stále podporována a nyní se převádějí na `$redirect=nooptext`, ale podpora bude v budoucnu odstraněna.
+This modifier is deprecated in favor of the [`$redirect` modifier](#redirect-modifier). Rules with `$empty` are still supported and being converted into `$redirect=nooptext` now but the support shall be removed in the future.
:::
-Obvykle se zablokované požadavky v prohlížeči tváří jako chyba serveru. Pokud použijete modifikátor `$empty`, AdGuard bude emulovat prázdnou odpověď ze serveru se stavem `200 OK`.
+Usually, blocked requests look like a server error to browser. If you use `$empty` modifier, AdGuard will emulate a blank response from the server with`200 OK` status.
**Příklady**
@@ -2940,19 +2953,19 @@ Obvykle se zablokované požadavky v prohlížeči tváří jako chyba serveru.
:::info Kompatibilita
-Pravidla s modifikátorem `$empty` nejsou podporována Blokátorem obsahu AdGuard, AdGuardem pro iOS a AdGuardem pro Safari.
+Rules with `$empty` modifier are not supported by AdGuard Content Blocker, AdGuard for iOS, and AdGuard for Safari.
:::
#### **`$mp4` (zastaralé)** {#mp4-modifier}
-:::caution Upozornění na vyřazení
+:::caution Deprecation notice
-Tento modifikátor je zastaralý a nahrazuje jej modifikátor [`$redirect`](#redirect-modifier). Pravidla s `$mp4` jsou stále podporována a nyní se převádějí na `$redirect=noopmp4-1s,media`, ale podpora bude v budoucnu odstraněna.
+This modifier is deprecated in favor of the [`$redirect` modifier](#redirect-modifier). Rules with `$mp4` are still supported and being converted into `$redirect=noopmp4-1s,media` now but the support shall be removed in the future.
:::
-Jako odpověď na zablokovaný požadavek vrátí AdGuard krátký zástupný videoklip.
+As a response to blocked request AdGuard returns a short video placeholder.
**Příklady**
@@ -2960,33 +2973,33 @@ Jako odpověď na zablokovaný požadavek vrátí AdGuard krátký zástupný vi
:::info Kompatibilita
-Pravidla s modifikátorem `$mp4` nejsou podporována Blokátorem obsahu AdGuard, AdGuardem pro iOS a AdGuardem pro Safari.
+Rules with `$mp4` modifier are not supported by AdGuard Content Blocker, AdGuard for iOS, and AdGuard for Safari.
:::
### Priority pravidel {#rule-priorities}
-Každé pravidlo má svou vlastní prioritu, což je nutné v případě, že požadavku odpovídá několik pravidel a filtrovací nástroj musí vybrat jedno z nich. Priorita se měří kladným celým číslem.
+Each rule has its own priority, which is necessary when several rules match the request and the filtering engine needs to select one of them. Priority is measured by a positive integer.
:::note Kolize
-Pokud stejnému požadavku odpovídají dvě pravidla se stejnou prioritou, implementace filtru určí, které z nich bude vybráno.
+When two rules with the same priority match the same request, the filter engine implementation determines which one is chosen.
:::
:::info
-Koncept priorit pravidel nabývá na významu ve světle Manifest V3, protože stávající pravidla je třeba převést na pravidla declarativeNetRequest.
+The concept of rule priorities becomes increasingly important in light of Manifest V3, as the existing rules need to be converted to declarativeNetRequest rules.
:::
#### Výpočet priority
-Pro výpočet priority jsme modifikátory rozdělili do různých skupin. Tyto skupiny jsou seřazeny podle priority od nejnižší po nejvyšší. Modifikátor, který výrazně zužuje oblast působnosti pravidla, zvyšuje jeho celkovou prioritu. Naopak, pokud se pravidlo vztahuje na širší okruh požadavků, jeho priorita se snižuje.
+To calculate priority, we've categorized modifiers into different groups. These groups are ranked based on their priority, from lowest to highest. A modifier that significantly narrows the scope of a rule adds more weight to its total priority. Conversely, if a rule applies to a broader range of requests, its priority decreases.
-Stojí za zmínku, že existují případy, kdy má jednoparametrový modifikátor vyšší prioritu než víceparametrový. Například v případě `$domain=example.com|example.org` má pravidlo, které zahrnuje dvě domény o něco širší oblast účinnosti než pravidlo s jednou zadanou doménou, a proto je jeho priorita nižší.
+It's worth noting that there are cases where a single-parameter modifier has a higher priority than multi-parameter ones. For instance, in the case of `$domain=example.com|example.org`, a rule that includes two domains has a slightly broader effective area than a rule with one specified domain, therefore its priority is lower.
-Základní priorita každého pravidla je 1. Pokud je vypočtená priorita číslo s pohyblivou řádovou čárkou, bude **zaokrouhlena nahoru** na nejmenší celé číslo větší nebo rovno vypočtené prioritě.
+The base priority of any rule is 1. If the calculated priority is a floating-point number, it will be **rounded up** to the smallest integer greater than or equal to the calculated priority.
:::info Kompatibilita
@@ -2997,7 +3010,7 @@ Základní priorita každého pravidla je 1. Pokud je vypočtená priorita čís
:::note
-Aliasy modifikátorů (`1p`, `3p` atd.) nejsou do těchto kategorií zahrnuty, nicméně jsou v rámci enginu využívány pro výpočet priority pravidla.
+Modifier aliases (`1p`, `3p`, etc.) are not included in these categories, however, they are utilized within the engine to compute the rule priority.
:::
@@ -3016,11 +3029,11 @@ Aliasy modifikátorů (`1p`, `3p` atd.) nejsou do těchto kategorií zahrnuty, n
- [`$to`](#to-modifier),
- omezené [typy obsahu](#content-type-modifiers) s `~`.
-Při práci s negovanou doménou, aplikací, metodou nebo typem obsahu přidáváme **1 bod** za existenci samotného modifikátoru bez ohledu na množství negovaných domén nebo typů obsahu. Je to proto, že oblast působnosti tohoto pravidla je již nyní nekonečně široká. Jednoduše řečeno, zákazem více domén, typů obsahu, metod nebo aplikací se rozsah pravidla zmenší jen minimálně.
+When dealing with a negated domain, app, method, or content-type, we add **1 point** for the existence of the modifier itself, regardless of the quantity of negated domains or content-types. This is because the rule's scope is already infinitely broad. Put simply, by prohibiting multiple domains, content-types, methods or apps, the scope of the rule becomes only minimally smaller.
#### Definované modifikátory typu obsahu, definované metody, definovaná záhlaví, $all, $popup, specifické výjimky {#priority-category-2}
-Všechny platné typy obsahu:
+All valid content types:
@@ -3037,15 +3050,15 @@ Všechny platné typy obsahu:
- [`$websocket`](#websocket-modifier),
- [`$xmlhttprequest`](#xmlhttprequest-modifier);
-Patří sem také pravidla, která implicitně přidávají všechny typy obsahu:
+This also includes rules that implicitly add all content types:
- [`$all`](#all-modifier);
-Nebo pravidla, která implicitně přidávají modifikátor `$document`:
+Or rules that implicitly add the modifier `$document`:
- [`$popup`](#popup-modifier);
-Nebo některé speciální výjimky, které implicitně přidávají `$document,subdocument`:
+Or some specific exceptions that implicitly add `$document,subdocument`:
@@ -3058,25 +3071,25 @@ Nebo některé speciální výjimky, které implicitně přidávají `$document,
- [`$specifichide`](#specifichide-modifier),
- [`$urlblock`](#urlblock-modifier);
-Nebo povolené metody skrze [`$method`](#method-modifier).
+Or allowed methods via [`$method`](#method-modifier).
-Nebo pravidla s [`$header`](#header-modifier).
+Or rules with [`$header`](#header-modifier).
-Přítomnost jakýchkoli modifikátorů typu obsahu přidává `(50 + 50 / N)`, kde `N` je např. počet přítomných modifikátorů: `||example.com^$image,skript` přidá `50 + 50 / 2 = 50 + 25 = 75` k celkové váze pravidla.
+The presence of any content-type modifiers adds `(50 + 50 / N)`, where `N` is the number of modifiers present, for example: `||example.com^$image,script` will add `50 + 50 / 2 = 50 + 25 = 75` to the total weight of the rule.
-Do této kategorie patří také `$all`, protože implicitně přidává všechny modifikátory typu obsahu, např. `$document,subdocument,image,script,media,` + `$popup`.
+The `$all` also belongs to this category, because it implicitly adds all content-type modifiers, e.g., `$document,subdocument,image,script,media,` + `$popup`.
-Do této kategorie patří i `$popup`, protože implicitně přidává modifikátor `$document`. Podobně specifické výjimky přidávají `$document,subdocument`.
+The `$popup` also belongs to this category, because it implicitly adds the modifier `$document`. Similarly, specific exceptions add `$document,subdocument`.
-Pokud je v pravidle s povolenými metodami modifikátor `$method`, přidává `(50 + 50 / N)`, kde `N` je počet povolených metod, např.: `||example.com^$method= GET|POST|PUT` přidává `50 + 50 / 3 = 50 + 16,6 = 67` k celkové váze pravidla.
+If there is a `$method` modifier in the rule with allowed methods it adds `(50 + 50 / N)`, where `N` is the number of methods allowed, for example: `||example.com^$method=GET|POST|PUT` will add `50 + 50 / 3 = 50 + 16.6 = 67` to the total weight of the rule.
-Pokud je v pravidle modifikátor `$header`, přidává se `50`.
+If there is a `$header` modifier in the rule, it adds `50`.
#### `$domain` nebo `$app` s povolenými doménami nebo aplikacemi {#priority-category-3}
-Zadané domény prostřednictvím `$domain` nebo zadané aplikace prostřednictvím `$app` přidávají `100 + 100 / N`, kde `N` je např. počet hodnot modifikátoru: `||example.com^$domain=example.com|example.org|example.net` přidává `100 + 100 / 3 = 134,3 = 135` nebo `||example.com^$app=org.example.app1|org.example.app2` sečte `100 + 100 / 2 = 151` nebo `||example.com^$domain=example.com,app=org.example.app1|org.example.app2` sečte `100 + 100/1` ($domain část) a `100 + 100/2` ($app část), celkem `350`.
+Specified domains through `$domain` or specified applications through `$app` add `100 + 100 / N`, where `N` is the number of modifier values for example: `||example.com^$domain=example.com|example.org|example.net` will add `100 + 100 / 3 = 134.3 = 135` or `||example.com^$app=org.example.app1|org.example.app2` will add `100 + 100 / 2 = 151` or `||example.com^$domain=example.com,app=org.example.app1|org.example.app2` will add `100 + 100/1` ($domain part) and `100 + 100/2` ($app part), totaling `350`.
-Hodnoty modifikátorů, které jsou regexp nebo tld, budou interpretovány jako normální položky ve tvaru `example.com` a budou počítány po jedné, např.: `||example.com^$domain=example.*` sečte `100 + 100 / 1 = 200` nebo `||example.com^$domain=example.*|adguard.*` sečte `100 + 100 / 2 = 150`.
+Modifier values that are regexps or tld will be interpreted as normal entries of the form `example.com` and counted one by one, for example: `||example.com^$domain=example.*` will add `100 + 100 / 1 = 200` or `||example.com^$domain=example.*|adguard.*` will add `100 + 100 / 2 = 150`.
#### Pravidla `$redirect` {#priority-category-6}
@@ -3085,7 +3098,7 @@ Hodnoty modifikátorů, které jsou regexp nebo tld, budou interpretovány jako
- [`$redirect`](#redirect-modifier),
- [`$redirect-rule`](#redirect-rule-modifier).
-Každé z nich přidává `10^3` k prioritě pravidla.
+Each of which adds `10^3` to rule priority.
#### Specifické výjimky {#priority-category-4}
@@ -3100,27 +3113,27 @@ Každé z nich přidává `10^3` k prioritě pravidla.
- [`$specifichide`](#specifichide-modifier),
- [`$urlblock`](#urlblock-modifier);
-Každá z nich přidává `10^4` k prioritě.
+Each of which adds `10^4` to the priority.
-Stejně jako výjimka s modifikátorem [`$document`](#document-modifier): protože je to alias pro `$elemhide,content,jsinject,urlblock,extension`. Přidá `10^4` pro každý modifikátor z [horního seznamu](#priority-category-4), celkem `10^4 * 5`.
+As well as exception with [`$document modifier`](#document-modifier): because it's an alias for `$elemhide,content,jsinject,urlblock,extension`. It will add `10^4` for each modifier from [the top list](#priority-category-4), `10^4 * 5` in total.
-Každá z těchto výjimek navíc implicitně přidává dva povolené modifikátory typu obsahu `$document,subdocument`.
+In addition, each of these exceptions implicitly adds the two allowed content-type modifiers `$document,subdocument`.
#### Pravidla seznamu povolených {#priority-category-5}
-Modifikátor `@@` přidává `10^5` k prioritě pravidla.
+Modifier `@@` adds `10^5` to rule priority.
#### Pravidla `$important` {#priority-category-7}
-Modifikátor [`$important`](#important-modifier) přidává `10^6` k prioritě pravidla.
+Modifier [`$important`](#important-modifier) adds `10^6` to rule priority.
#### Pravidla, pro která není stanovena váha priority {#priority-category-extra}
-[Ostatní modifikátory](#advanced-capabilities), které mají provádět dodatečné následné nebo předběžné zpracování požadavků, nepřidávají nic k prioritě pravidel.
+[Other modifiers](#advanced-capabilities), which are supposed to perform additional post- or pre-processing of requests, do not add anything to the rule priority.
:::note
-Modifikátor [`$replace`](#replace-modifier) má přednost před všemi pravidly blokování kategorií 1–3, stejně jako před pravidly výjimek z kategorií 3–5, **kromě** [`$content`](#content-modifier), protože výjimka s modifikátorem `$content` má přednost před všemi pravidly `$replace`.
+The [`$replace`](#replace-modifier) modifier takes precedence over all blocking rules of categories 1–3, as well as exception rules from categories 3–5, **except** [`$content`](#content-modifier), because an exception with the `$content` modifier overrides all `$replace` rules.
:::
@@ -3128,43 +3141,43 @@ Modifikátor [`$replace`](#replace-modifier) má přednost před všemi pravidly
1. `||example.com^`
- Váha pravidla bez modifikátorů: `1`.
+ Weight of the rule without modifiers: `1`.
1. `||example.com^$match-case`
- Váha pravidla: základní + váha modifikátoru z [kategorie 1](#priority-category-1): `1 + 1 = 2`.
+ Rule weight: base weight + weight of the modifier from [category 1](#priority-category-1): `1 + 1 = 2`.
1. `||example.org^$removeparam=p`
- Váha pravidla: základní váha + 0, protože $removeparam [není zahrnuto](#priority-category-extra) do výpočtu priority: `1 + 0 = 1`.
+ Rule weight: base weight + 0, since $removeparam [is not involved](#priority-category-extra) in the priority calculation: `1 + 0 = 1`.
1. `||example.org^$document,redirect=nooptext`
- Váha pravidla: základní + povolený typ obsahu, [kategorie 3](#priority-category-3) + $redirect z [kategorie 6](#priority-category-6): `1 + (100 + 100 / 1) + 1000 = 1201`.
+ Rule weight: base weight + allowed content type, [category 3](#priority-category-3) + $redirect from [category 6](#priority-category-6): `1 + (100 + 100 / 1) + 1000 = 1201`.
1. `@@||example.org^$removeparam=p,document`
- Váha pravidla: základní váha + pravidlo seznamu povolených [kategorie 5](#priority-category-5) + 0, protože $removeparam [není zapojeno](#priority-category-extra) do výpočtu priority + povolený typ obsahu [kategorie 2](#priority-category-2): `1 + 10000 + 0 + (50 + 50 / 1) = 10101`.
+ Rule weight: base weight + allowlist rule, [category 5](#priority-category-5) + 0 because $removeparam [is not involved](#priority-category-extra) in the priority calculation + allowed content type, [category 2](#priority-category-2): `1 + 10000 + 0 + (50 + 50 / 1) = 10101`.
1. `@@||example.com/ad/*$domain=example.org|example.net,important`
- Váha pravidla: základní váha + pravidlo seznamu povolených [kategorie 5](#priority-category-5) + důležité pravidlo [kategorie 7](#priority-category-7) + povolené domény [kategorie 3](#priority-category-3): `1 + 10000 + 1000000 + (100 + 100 / 2) = 1010152`.
+ Rule weight: base weight + allowlist rule, [category 5](#priority-category-5) + important rule, [category 7](#priority-category-7) + allowed domains, [category 3](#priority-category-3): `1 + 10000 + 1000000 + (100 + 100 / 2) = 1010152`.
-1. `@@||example.org^$document` bez dalších modifikátorů je aliasem pro `@@||example.com^$elemhide,content,jsinject,urlblock,extension`
+1. `@@||example.org^$document` without additional modifiers is an alias for `@@||example.com^$elemhide,content,jsinject,urlblock,extension`
- Váha pravidla: základní váha + specifické výjimky, [kategorie 4](#priority-category-4) + dva povolené typy obsahu (dokument a subdokument) [kategorie 2](#priority-category-2): `1 + 10000 * 4 + (50 + 50 / 2) = 40076`.
+ Rule weight: base weight + specific exceptions, [category 4](#priority-category-4) + two allowed content types (document and subdocument), [category 2](#priority-category-2): `1 + 10000 * 4 + (50 + 50 / 2) = 40076`.
1. `*$script,domain=a.com,denyallow=x.com|y.com`
- Váha pravidla: základní váha + povolený typ obsahu [kategorie 2](#priority-category-2) + povolená doména, [kategorie 3](#priority-category-3) + denyallow [kategorie 1](#priority-category-1): `1 + (50 + 50/1) + (100 + 100 / 1) + 1 = 303`.
+ Rule weight: base weight + allowed content type, [category 2](#priority-category-2) + allowed domain, [category 3](#priority-category-3) + denyallow, [category 1](#priority-category-1): `1 + (50 + 50/1) + (100 + 100 / 1) + 1 = 303`.
-1. `||example.com^$all` — alias na `||example.com^$document,subdocument,image,script,media,etc. + $popup`
+1. `||example.com^$all` — alias to `||example.com^$document,subdocument,image,script,media,etc. + $popup`
- Váha pravidla: základní váha + vyskakovací okno ([kategorie 1](#priority-category-1)) + povolené typy obsahu ([kategorie 2](#priority-category-2)): `1 + 1 + (50 + 50/12) = 55`.
+ Rule weight: base weight + popup ([category 1](#priority-category-1)) + allowed content types ([category 2](#priority-category-2)): `1 + 1 + (50 + 50/12) = 55`.
## Ostatní pravidla {#non-basic-rules}
-Základní pravidla však nemusí k blokování reklam stačit. Někdy potřebujete skrýt prvek nebo změnit část kódu HTML webové stránky, aniž byste cokoli porušili. Pravidla popsaná v této části jsou vytvořena speciálně pro tento účel.
+However, basic rules may not be enough to block ads. Sometimes you need to hide an element or change part of the HTML code of a web page without breaking anything. The rules described in this section are created specifically for this purpose.
| Kategorie \ Produkty | [Aplikace CoreLibs][cl-apps] | [AdGuard pro Chromium][ext-chr] | [AdGuard pro Chrome MV3][ext-mv3] | [AdGuard pro Firefox][ext-ff] | [AdGuard pro iOS][ios-app] | [AdGuard pro Safari][ext-saf] | [Blokátor obsahu AdGuard][and-cb] |
| ---------------------------------------- |:----------------------------:|:-------------------------------:|:---------------------------------:|:-----------------------------:|:--------------------------:|:-----------------------------:|:---------------------------------:|
@@ -3186,15 +3199,15 @@ Základní pravidla však nemusí k blokování reklam stačit. Někdy potřebuj
:::info
-Práce s ostatními pravidly vyžaduje základní znalost HTML a CSS. Pokud se tedy chcete naučit, jak taková pravidla vytvářet, doporučujeme seznámit se s touto [dokumentací](https://developer.mozilla.org/en-US/docs/Web/Guide/CSS/Getting_started/What_is_CSS).
+Work with non-basic rules requires the basic knowledge of HTML and CSS. So, if you want to learn how to make such rules, we recommend to get acquainted with [this documentation](https://developer.mozilla.org/en-US/docs/Web/Guide/CSS/Getting_started/What_is_CSS).
:::
### Pravidla pro skrytí prvků {#cosmetic-elemhide-rules}
-Pravidla pro skrytí prvků slouží ke skrývání prvků webových stránek. Je to podobné jako použít styl `{ display: none; }` na vybraný prvek.
+Element hiding rules are used to hide the elements of web pages. It is similar to applying `{ display: none; }` style to selected element.
-Pravidla pro skrytí prvků mohou fungovat odlišně [v závislosti na platformě](#cosmetic-rules-priority).
+Element hiding rules may operate differently [depending on the platform](#cosmetic-rules-priority).
#### Syntaxe
@@ -3206,17 +3219,17 @@ domains = [domain0, domain1[, ...[, domainN]]]
- **`selektor`** — [CSS selektor](https://developer.mozilla.org/en-US/docs/Web/Guide/CSS/Getting_Started/Selectors) definuje prvky, které mají být skryty.
- **`domains`** — omezení domény pro dané pravidlo.
-Pokud chcete omezit oblast použití pravidel na určité domény, stačí je zadat oddělené čárkami. Např.: `example.org,example.com##selector`.
+If you want to limit the rule application area to certain domains, just enter them separated with commas. For example: `example.org,example.com##selector`.
-Toto pravidlo bude také použito na všechny subdomény `example.org` a `example.com`.
+This rule will be also applied to all subdomains of `example.org` and `example.com`.
-Pokud chcete, aby se pravidlo nevztahovalo na určité domény, začněte název domény znakem `~`. Např.: `~example.org##selector`.
+Pokud chcete, aby se pravidlo nevztahovalo na určité domény, začněte název domény znakem `~`. For example: `~example.org##selector`.
-V jednom pravidle můžete použít oba přístupy. Např. `example.org,~subdomain.example.org##domain` bude fungovat pro `example.org` a všechny subdomény **kromě `subdomain.example.org`**.
+You can use both approaches in a single rule. For example, `example.org,~subdomain.example.org##domain` will work for `example.org` and all subdomains, **except `subdomain.example.org`**.
:::note
-Pravidla pro skrývání prvků na sobě nejsou závislá. Pokud je ve filtru pravidlo `example.org##selector` a přidáte `~example.org##selector`, budou obě pravidla použita nezávisle.
+Element hiding rules are not dependent on each other. If there is a rule `example.org##selector` in the filter and you add `~example.org##selector` both rules will be applied independently.
:::
@@ -3228,41 +3241,41 @@ Pravidla pro skrývání prvků na sobě nejsou závislá. Pokud je ve filtru pr
**Omezení**
-Safari nepodporuje povolené i zakázané domény. Takže pravidla jako `example.org,~foo.example.org##.textad` jsou v AdGuardu pro Safari neplatná.
+Safari does not support both allowed and disallowed domains. So the rules like `example.org,~foo.example.org##.textad` are invalid in AdGuard for Safari.
**Výjimky**
-Výjimky mohou zakázat některá pravidla pro určité domény. Jsou velmi podobné běžným pravidlům výjimek, ale namísto `##` musíte použít `#@#`.
+Exceptions can disable some rules on particular domains. They are very similar to usual exception rules, but instead of `##` you have to use `#@#`.
-Ve filtru je např. pravidlo:
+For example, there is a rule in filter:
```adblock
##.textad
```
-Pokud to chcete zakázat pro `example.com`, můžete vytvořit pravidlo výjimky:
+If you want to disable it for `example.com`, you can create an exception rule:
```adblock
example.com#@#.textad
```
-Někdy může být nutné zakázat všechna pravidla omezení. Např. k provádění testů. Za tímto účelem použijte pravidlo výjimky bez zadání domény. Úplně zakáže odpovídající pravidlo CSS elemhide na VŠECH doménách:
+Sometimes, it may be necessary to disable all restriction rules. For example, to conduct tests. To do this, use the exclusion rule without specifying a domain. It will completely disable matching CSS elemhide rule on ALL domains:
```adblock
#@#.textad
```
-Toho lze dosáhnout přidáním tohoto pravidla:
+The same can be achieved by adding this rule:
```adblock
*#@#.textad
```
-Tento druh výjimek doporučujeme používat pouze v případě, že není možné změnit samotné pravidlo skrývání. V ostatních případech je lepší změnit původní pravidlo pomocí omezení domény.
+We recommend to use this kind of exceptions only if it is not possible to change the hiding rule itself. In other cases it is better to change the original rule, using domain restrictions.
### Pravidla CSS {#cosmetic-css-rules}
-Někdy pouhé skrytí prvku k vyřešení reklamy nestačí. Např. zablokování prvku reklamy může jen narušit rozvržení stránky. V tomto případě může AdGuard použít pravidla, která jsou mnohem flexibilnější než pravidla pro skrývání. Pomocí těchto pravidel můžete v podstatě přidat na stránku libovolné styly CSS.
+Sometimes, simple hiding of an element is not enough to deal with advertising. For example, blocking an advertising element can just break the page layout. In this case AdGuard can use rules that are much more flexible than hiding rules. With these rules you can basically add any CSS styles to the page.
**Syntaxe**
@@ -3281,37 +3294,37 @@ domains = [domain0, domain1[, ...[, domainN]]]
example.com#$#body { background-color: #333!important; }
```
-Toto pravidlo použije styl `background-color: #333!important;` na prvek `body` na doménu `example.com` a všechny subdomény.
+This rule will apply a style `background-color: #333!important;` to the `body` element at `example.com` and all subdomains.
**Výjimky**
-Stejně jako u skrývání prvků existuje typ pravidel, který zakáže vybrané pravidlo stylu CSS pro určité domény. Syntaxe pravidel pro výjimky je téměř stejná, stačí jen změnit `#$#` na `#@$#`.
+Just like with element hiding, there is a type of rules that disable the selected CSS style rule for particular domains. Exception rule syntax is almost the same, you just have to change `#$#` to `#@$#`.
-Ve filtru je např. pravidlo:
+For example, there is a rule in filter:
```adblock
#$#.textad { visibility: hidden; }
```
-Pokud to chcete zakázat pro `example.com`, můžete vytvořit pravidlo výjimky:
+If you want to disable it for `example.com`, you can create an exception rule:
```adblock
example.com#@$#.textad { visibility: hidden; }
```
-Tento druh výjimek doporučujeme používat pouze v případě, že není možné změnit samotné pravidlo CSS. V ostatních případech je lepší změnit původní pravidlo pomocí omezení domény.
+We recommend to use this kind of exceptions only if it is not possible to change the CSS rule itself. In other cases it is better to change the original rule, using domain restrictions.
:::caution Omezení
-Styly, které vedou k načtení jakéhokoli zdroje, jsou zakázány. V podstatě to znamená, že ve stylu nelze použít žádný typ hodnoty ``.
+Styles that lead to loading any resource are forbidden. Basically, it means that you cannot use any `` type of value in the style.
:::
:::info Kompatibilita
-Pravidla CSS nejsou Blokátorem obsahu AdGuard podporována.
+CSS rules are not supported by AdGuard Content Blocker.
-Pravidla CSS mohou fungovat odlišně [v závislosti na platformě](#cosmetic-rules-priority).
+CSS rules may operate differently [depending on the platform](#cosmetic-rules-priority).
:::
@@ -3331,30 +3344,30 @@ Pravidla CSS mohou fungovat odlišně [v závislosti na platformě](#cosmetic-ru
- [Pseudo-třída `:not()`](#extended-css-not)
- [Pseudo-třída `:if-not()` (odstraněno)](#extended-css-if-not)
-CSS 3.0 ne vždy stačí k blokování reklam. AdGuard tento problém řeší rozšířením možností CSS o podporu nových pseudo-prvků. Vyvinuli jsme samostatnou [open-source knihovnu](https://github.com/AdguardTeam/ExtendedCss) pro výběr nestandardních prvků a aplikaci CSS stylů s rozšířenými vlastnostmi.
+CSS 3.0 is not always enough to block ads. To solve this problem AdGuard extends CSS capabilities by adding support for the new pseudo-elements. We have developed a separate [open-source library](https://github.com/AdguardTeam/ExtendedCss) for non-standard element selecting and applying CSS styles with extended properties.
-Myšlenkou rozšířených možností je možnost přiřazovat prvky DOM pomocí selektorů na základě jejich vlastní reprezentace (styl, textový obsah atd.) nebo vztahů s jinými prvky. Existuje také možnost použít styly s nestandardními vlastnostmi CSS.
+The idea of extended capabilities is an opportunity to match DOM elements with selectors based on their own representation (style, text content, etc.) or relations with other elements. There is also an opportunity to apply styles with non-standard CSS properties.
-**Oblast použití**
+**Application area**
-Rozšířené selektory lze použít v jakémkoli kosmetickém pravidle, ať už se jedná o pravidla pro [skrytí prvků](#cosmetic-elemhide-rules) nebo [pravidla CSS](#cosmetic-css-rules).
+Extended selectors can be used in any cosmetic rule, whether they are [element hiding rules](#cosmetic-elemhide-rules) or [CSS rules](#cosmetic-css-rules).
:::info Kompatibilita
-Pravidla se selektory CSS nejsou Blokátorem obsahu AdGuard podporována.
+Rules with extended CSS selectors are not supported by AdGuard Content Blocker.
:::
**Syntaxe**
-Bez ohledu na pseudo-třídy CSS, které v pravidle používáte, můžete pomocí speciálních znaků vynutit použití těchto pravidel pomocí ExtendedCss. Doporučujeme používat tyto znaky pro všechna rozšířená kosmetická pravidla CSS, aby bylo snazší je najít.
+Regardless of the CSS pseudo-classes you are using in the rule, you can use special markers to force applying these rules by ExtendedCss. It is recommended to use these markers for all extended CSS cosmetic rules so that it was easier to find them.
-Syntaxe rozšířených pravidel CSS:
+The syntax for extended CSS rules:
- `#?#` — pro skrytí prvku, `#@?#` — pro výjimky
- `#$?#` — pro pravidlo CSS, `#@$?#` — pro výjimky
-**Důrazně doporučujeme** použít tyto znaky kdykoli, když používáte rozšířený selektor CSS.
+We **strongly recommend** using these markers any time when you use an extended CSS selector.
**Příklady**
@@ -3363,49 +3376,49 @@ Syntaxe rozšířených pravidel CSS:
- `example.net#?#.banner:matches-css(width: 360px)` — toto pravidlo blokuje všechny prvky `.banner` s vlastností stylu `width: 360px`. Pravidlo platí pouze pro `example.net` a její subdomény.
- `example.net#@?#.banner:matches-css(width: 360px)` — toto pravidlo zakáže předchozí pravidlo.
-Standardní CSS selektory můžete použít pomocí knihovny ExtendedCss pomocí znaku pravidla `#?#`, např. `#?#div.banner`.
+You can apply standard CSS selectors using the ExtendedCss library by using the rule marker `#?#`, e.g. `#?#div.banner`.
-Přečtěte si další informace o [ladění rozšířených selektorů](#selectors-debugging-mode).
+Learn more about [how to debug extended selectors](#selectors-debugging-mode).
:::note
-Některé pseudo-třídy před sebou selektor nevyžadují. Přesto přidání [univerzálního selektoru](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*` usnadňuje čtení rozšířeného selektoru, i když nemá žádný vliv na chování při porovnávání. Takže selektor `#blok :has(> .inner)` funguje přesně jako `#blok *:has(> .inner)`, ale druhý je zřejmější.
+Some pseudo-classes do not require selector before it. Still adding the [universal selector](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*` makes an extended selector easier to read, even though it has no effect on the matching behavior. So selector `#block :has(> .inner)` works exactly like `#block *:has(> .inner)`, but the second one is more obvious.
-Názvy pseudo-tříd nerozlišují malá a velká písmena, např. `:HAS()` funguje jako `:has()`. Přesto se běžně používají názvy s malými písmeny.
+Pseudo-class names are case-insensitive, e.g. `:HAS()` works as `:has()`. Still the lower-case names are used commonly.
:::
#### Limitace ExtendedCss {#extended-css-limitations}
-1. CSS [komentáře](https://developer.mozilla.org/en-US/docs/Web/CSS/Comments) a [at-pravidla](https://developer.mozilla.org/en-US/docs/Web/CSS/At-rule) nejsou podporovány.
+1. CSS [comments](https://developer.mozilla.org/en-US/docs/Web/CSS/Comments) and [at-rules](https://developer.mozilla.org/en-US/docs/Web/CSS/At-rule) are not supported.
-2. Konkrétní pseudot-řída může mít svá vlastní omezení: [`:has()`](#extended-css-has-limitations), [`:xpath()`](#extended-css-xpath-limitations), [`:nth-ancestor()`](#extended-css-nth-ancestor-limitations), [`:upward()`](#extended-css-upward-limitations), [`:is()`](#extended-css-is-limitations), [`:not()`](#extended-css-not-limitations) a [`:remove()`](#extended-css-remove-limitations).
+2. Specific pseudo-class may have its own limitations: [`:has()`](#extended-css-has-limitations), [`:xpath()`](#extended-css-xpath-limitations), [`:nth-ancestor()`](#extended-css-nth-ancestor-limitations), [`:upward()`](#extended-css-upward-limitations), [`:is()`](#extended-css-is-limitations), [`:not()`](#extended-css-not-limitations), and [`:remove()`](#extended-css-remove-limitations).
#### Pseudo-třída `:has()` {#extended-css-has}
-Návrh specifikace CSS 4.0 popisuje [`:has()` pseudo-třídu](https://www.w3.org/TR/selectors-4/#relational). Bohužel [to zatím není podporováno](https://caniuse.com/css-has) všemi oblíbenými prohlížeči.
+Draft CSS 4.0 specification describes the [`:has()` pseudo-class](https://www.w3.org/TR/selectors-4/#relational). Unfortunately, [it is not yet supported](https://caniuse.com/css-has) by all popular browsers.
:::note
-Pravidla s pseudo-třídou `:has()` musí používat nativní implementaci [ `:has()`][native-has], pokud používají znak `##` a pokud je to možné, tj. bez dalších rozšířených selektorů uvnitř. Pokud není produktem podporována, bude implementace ExtendedCss použita i pro pravidla se značkou `##`.
+Rules with the `:has()` pseudo-class must use the [native implementation of `:has()`][native-has] if they use the `##` rule marker and if it is possible, i.e., there are no other extended CSS selectors inside. If it is not supported by the product, ExtendedCss implementation will be used even for rules with the `##` marker.
-V současné době ne všechny produkty AdGuardu podporují nativní implementaci `:has()`:
+Currently, not all AdGuard products support the native implementation of `:has()` yet:
- AdGuard pro Windows, AdGuard pro Mac, AdGuard pro Android a AdGuard pro Linux to **podporují** s [knihovnou CoreLibs][] v1.12 nebo novější.
- AdGuard pro iOS a AdGuard pro Safari to **podporují** s [knihovnou SafariConverterLib](#safari-converter-lib) v2.0.39 a [prohlížečem Safari v16.4][safari-16.4].
- Rozšíření prohlížeče AdGuard to zatím **nepodporuje**, ale [plánuje se][AdguardBrowserExtension#2587].
-Chcete-li vynutit použití implementace ExtendedCss `:has()`, použijte explicitně značky pravidel `#?#` nebo `#$?#`, např. `example.com#?#p:has(> a)` nebo `example.com#$?#div:has(> span) { display: none !important; }`.
+To force the ExtendedCss implementation of `:has()` to be used, use the `#?#` or `#$?#` rule markers explicitly, e.g., `example.com#?#p:has(> a)` or `example.com#$?#div:has(> span) { display: none !important; }`.
:::
-**Kompatibilita s jinými pseudo-třídami**
+**Compatibility with other pseudo-classes**
-Synonyma `:-abp-has()` podporují ExtendedCss pro lepší kompatibilitu.
+Synonyms `:-abp-has()` is supported by ExtendedCss for better compatibility.
:::danger Upozornění na odstranění
-`:if()` již není podporováno jako synonymum pro `:has()`.
+`:if()` is no longer supported as a synonym for `:has()`.
:::
@@ -3418,24 +3431,24 @@ Synonyma `:-abp-has()` podporují ExtendedCss pro lepší kompatibilitu.
- `target` — nepovinný, standardní nebo rozšířený selektor CSS může být přeskočen pro kontrolu *libovolného* prvku
- `selector` — povinný, standardní nebo rozšířený selektor CSS
-Pseudo-třída `:has()` vybere prvky `target`, které se hodí do `selector`. Také `selector` může začínat kombinátorem.
+The pseudo-class `:has()` selects the `target` elements that fit to the `selector`. Also the `selector` can start with a combinator.
-Seznam selektorů lze nastavit také v `selector`. V tomto případě se zatím porovnávají **všechny** selektory v seznamu. V budoucnu bude opraveno pro [``](https://www.w3.org/TR/selectors-4/#typedef-forgiving-relative-selector-list) jako argument.
+A selector list can be set in `selector` as well. In this case **all** selectors in the list are being matched for now. In the future it will be fixed for [``](https://www.w3.org/TR/selectors-4/#typedef-forgiving-relative-selector-list) as argument.
##### `:has()` limitations {#extended-css-has-limitations}
-Použití pseudo-třídy `:has()` je v [některých případech omezeno (2, 3)](https://bugs.chromium.org/p/chromium/issues/detail?id=669058#c54):
+Usage of the `:has()` pseudo-class is [restricted for some cases (2, 3)](https://bugs.chromium.org/p/chromium/issues/detail?id=669058#c54):
- zakazuje `:has()` uvnitř pseudo akceptující pouze složené selektory;
- zakazuje `:has()` po běžných pseudoprvcích.
-Nativní pseudo-třída `:has()` neumožňuje použití argumentů `:has()`, `:is()`, `:where()` uvnitř argumentu `:has()`, aby se nezvyšovala složitost zneplatnění `:has()`[(případ 1](https://bugs.chromium.org/p/chromium/issues/detail?id=669058#c54)). ExtendedCss však dříve takové omezení nemělo a seznamy filtrů již taková pravidla obsahují, proto jsme toto omezení do ExtendedCss nepřidali a umožnili jsme používat `:has()` uvnitř `:has()`, jak to bylo možné dříve. Chcete-li to použít, stačí vynutit použití ExtendedCss nastavením znaku pravidla `#?#`/`#$?#`.
+Native `:has()` pseudo-class does not allow `:has()`, `:is()`, `:where()` inside `:has()` argument to avoid increasing the `:has()` invalidation complexity ([case 1](https://bugs.chromium.org/p/chromium/issues/detail?id=669058#c54)). But ExtendedCss did not have such limitation earlier and filter lists already contain such rules, so we have not added this limitation to ExtendedCss and allow to use `:has()` inside `:has()` as it was possible before. To use it, just force ExtendedCss usage by setting `#?#`/`#$?#` rule marker.
-Nativní implementace neumožňuje žádné použití `:scope` uvnitř argumentu `:has()` ([[1]](https://github.com/w3c/csswg-drafts/issues/7211), [[2]](https://github.com/w3c/csswg-drafts/issues/6399)). Přesto v seznamech filtrů některá taková pravidla existují: `div:has(:scope a)`, která nadále podporujeme tím, že je jednoduše převedeme na `div:has(> a)`, jak se to dělalo dříve.
+Native implementation does not allow any usage of `:scope` inside the `:has()` argument ([[1]](https://github.com/w3c/csswg-drafts/issues/7211), [[2]](https://github.com/w3c/csswg-drafts/issues/6399)). Still, there are some such rules in filter lists: `div:has(:scope a)` which we continue to support by simply converting them to `div:has(> a)`, as it used to be done previously.
**Příklady**
-`div:has(.banner)` vybere všechny prvky `div`, které **obsahují** prvek se třídou `banner`:
+`div:has(.banner)` selects all `div` elements which **include** an element with the `banner` class:
```html
@@ -3445,7 +3458,7 @@ Nativní implementace neumožňuje žádné použití `:scope` uvnitř argumentu
```
-`div:has(> .banner)` vybere všechny `prvky div`, které **obsahují prvek třídy** `banner` jako *přímý potomek* z `div`:
+`div:has(> .banner)` selects all `div` elements which **include** an `banner` class element as a *direct child* of `div`:
```html
@@ -3455,7 +3468,7 @@ Nativní implementace neumožňuje žádné použití `:scope` uvnitř argumentu
```
-`div:has(+ .banner)` vybere všechny prvky `div` **předcházející** prvek třídy `banner`, který *bezprostředně následuje* po `div` a oba jsou potomky stejného rodu:
+`div:has(+ .banner)` selects all `div` elements **preceding** `banner` class element which *immediately follows* the `div` and both are children of the same parent:
```html
@@ -3465,7 +3478,7 @@ Nativní implementace neumožňuje žádné použití `:scope` uvnitř argumentu
Not selected
```
-`div:has(~ .banner)` vybere všechny prvky `div` **předcházející** prvek třídy `banner`, který *následuje* `div`, ale *ne nutně bezprostředně* a oba jsou potomky stejného rodu:
+`div:has(~ .banner)` selects all `div` elements **preceding** `banner` class element which *follows* the `div` but *not necessarily immediately* and both are children of the same parent:
```html
@@ -3475,7 +3488,7 @@ Nativní implementace neumožňuje žádné použití `:scope` uvnitř argumentu
general sibling
```
-`div:has(span, .banner)` vybere všechny prvky `div`, které **obsahují** prvek se třídou `span` a `banner`:
+`div:has(span, .banner)` selects all `div` elements which **include both** `span` element and `banner` class element:
```html
@@ -3486,25 +3499,25 @@ Nativní implementace neumožňuje žádné použití `:scope` uvnitř argumentu
```
-:::danger Stará syntaxe
+:::danger Old syntax
-[Zpětně kompatibilní syntaxe pro `:has()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-has)je podporována, ale **není doporučena**.
+[Backward compatible syntax for `:has()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-has) is supported but **not recommended**.
:::
#### Pseudo-třída `:contains()` {#extended-css-contains}
-Princip pseudo-třídy `:contains()` je velmi jednoduchý: umožňuje vybrat prvky, které obsahují zadaný text nebo jejichž obsah odpovídá zadanému regulárnímu výrazu. Příznaky regexp jsou podporovány.
+The `:contains()` pseudo-class principle is very simple: it allows to select the elements that contain specified text or which content matches a specified regular expression. Regexp flags are supported.
:::note
-Pseudo-třída `:contains()` používá pro porovnávání vlastnost prvku `textContent`, nikoliv `innerHTML`.
+The `:contains()` pseudo-class uses the `textContent` element property for matching, not the `innerHTML`.
:::
-**Kompatibilita s jinými pseudo-třídami**
+**Compatibility with other pseudo-classes**
-Pro lepší kompatibilitu jsou podporována synonyma `:-abp-contains()` a `:has-text()`.
+Synonyms `:-abp-contains()` and `:has-text()` are supported for better compatibility.
**Syntaxe**
@@ -3517,7 +3530,7 @@ Pro lepší kompatibilitu jsou podporována synonyma `:-abp-contains()` a `:has-
**Příklady**
-Pro DOM:
+For such DOM:
```html
@@ -3526,34 +3539,34 @@ Pro DOM:
```
-prvek `div#match` lze vybrat pomocí kteréhokoli z těchto rozšířených selektorů:
+the element `div#match` can be selected by any of these extended selectors:
```adblock
-! prostý text
+! plain text
div:contains(banner)
-! regulární výraz
+! regular expression
div:contains(/as .*banner/)
-! regulární výraz s příznaky
+! regular expression with flags
div:contains(/it .*banner/gi)
```
:::note
-Vybrán je pouze `div` s `id=match`, protože další prvek neobsahuje žádný text a `banner` je součástí kódu, nikoli textu.
+Only the `div` with `id=match` is selected because the next element does not contain any text, and `banner` is a part of code, not a text.
:::
-:::danger Stará syntaxe
+:::danger Old syntax
-[Zpětně kompatibilní syntaxe pro `:contains()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-contains)je podporována, ale **není doporučena**.
+[Backward compatible syntax for `:contains()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-contains) is supported but **not recommended**.
:::
#### Pseudo-třída `:matches-css()` {#extended-css-matches-css}
-Pseudo-třída `:matches-css()` umožňuje porovnat prvek podle jeho aktuálních vlastností stylu. Práce pseudo-třídy je založena na použití metody [`Window.getComputedStyle().`](https://developer.mozilla.org/en-US/docs/Web/API/Window/getComputedStyle).
+The `:matches-css()` pseudo-class allows to match the element by its current style properties. The work of the pseudo-class is based on using the [`Window.getComputedStyle()`](https://developer.mozilla.org/en-US/docs/Web/API/Window/getComputedStyle) method.
**Syntaxe**
@@ -3566,15 +3579,15 @@ Pseudo-třída `:matches-css()` umožňuje porovnat prvek podle jeho aktuálníc
- `property` — povinný, název vlastnosti CSS, pro kterou se má prvek zkontrolovat
- `pattern` — povinný, vzor hodnoty, který používá stejnou jednoduchou shodu se zástupnými znaky jako v základních pravidlech filtrování adres URL nebo regulární výraz. Při tomto typu porovnávání, AdGuard vždy porovnává bez ohledu na velikost písmen. V případě regulárního výrazu vypadá vzor takto: `/regexp/`.
-**Speciální znaky uvozené a neuvozené**
+**Special characters escaping and unescaping**
-Všechny vzory **non-regexp** `(`,`)`,`[`,`]` musí být **neuvozeny**, např. `:matches-css(background-image:url(data:*))`.
+For **non-regexp** patterns `(`,`)`,`[`,`]` must be **unescaped**, e.g. `:matches-css(background-image:url(data:*))`.
-Vzory **regexp** `\` by měly být **uvozeny**, např. `:matches-css(background-image: /^url\\("data:image\\/gif;base64.+/)`.
+For **regexp** patterns `\` should be **escaped**, e.g. `:matches-css(background-image: /^url\\("data:image\\/gif;base64.+/)`.
**Příklady**
-Pro DOM:
+For such DOM:
```html
@@ -3587,7 +3600,7 @@ Pro DOM:
```
-prvky `div` s pseudoprvkem `::before` a se zadanou vlastností `content` lze vybrat kterýmkoli z těchto rozšířených selektorů:
+the `div` elements with pseudo-element `::before` and with specified `content` property can be selected by any of these extended selectors:
```adblock
! string pattern
@@ -3602,25 +3615,25 @@ div:matches-css(before, content: /block me/)
:::caution Omezení
-Vzory regexp **nepodporují** příznaky.
+Regexp patterns **do not support** flags.
:::
:::info Kompatibilita
-Zastaralé pseudo-třídy `:matches-css-before()` a `:matches-css-after()` se již nedoporučují, ale stále jsou podporovány kvůli lepší kompatibilitě.
+Obsolete pseudo-classes `:matches-css-before()` and `:matches-css-after()` are no longer recommended but still are supported for better compatibility.
:::
-:::danger Stará syntaxe
+:::danger Old syntax
-[Zpětně kompatibilní syntaxe pro `:matches-css()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-matches-css) je podporována, ale **nedoporučuje se**.
+[Backward compatible syntax for `:matches-css()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-matches-css) is supported but **not recommended**.
:::
#### Pseudo-třída `:matches-attr()` {#extended-css-matches-attr}
-Pseudo-třída `:matches-attr()` umožňuje vybrat prvek podle jeho atributů, zejména pokud jsou náhodné.
+The `:matches-attr()` pseudo-class allows selecting an element by its attributes, especially if they are randomized.
**Syntaxe**
@@ -3632,34 +3645,34 @@ Pseudo-třída `:matches-attr()` umožňuje vybrat prvek podle jeho atributů, z
- `name` — povinný, jednoduchý řetězec *nebo* řetězec se zástupným znakem *nebo* regulární výraz pro shodu názvu atributu
- `value` — volitelný, jednoduchý řetězec *nebo* řetězec se zástupným znakem *nebo* regulární výraz pro shodu hodnoty atributu
-**Uvození speciálních znaků**
+**Escaping special characters**
-Pro vzory **regexp** `"` a `\` by mělo být **uvozeno**, např. `div:matches-attr(class=/[\\w]{5}/)`.
+For **regexp** patterns `"` and `\` should be **escaped**, e.g. `div:matches-attr(class=/[\\w]{5}/)`.
**Příklady**
-`div:matches-attr("ad-link")` vybere prvek `div#target1`:
+`div:matches-attr("ad-link")` selects the element `div#target1`:
```html
```
-`div:matches-attr("data-*"="adBanner")` vybere prvek `div#target2`:
+`div:matches-attr("data-*"="adBanner")` selects the element `div#target2`:
```html
```
-`div:matches-attr(*unit*=/^click$/)` vybere prvek `div#target3`:
+`div:matches-attr(*unit*=/^click$/)` selects the element `div#target3`:
```html
```
-`*:matches-attr("/.{5,}delay$/"="/^[0-9]*$/")` vybere prvek `#target4`:
+`*:matches-attr("/.{5,}delay$/"="/^[0-9]*$/")` selects the element `#target4`:
```html
@@ -3670,13 +3683,13 @@ Pro vzory **regexp** `"` a `\` by mělo být **uvozeno**, např. `div:matches-at
:::caution Omezení
-Vzory regexp **nepodporují** příznaky.
+Regexp patterns **do not support** flags.
:::
#### Pseudo-třída `:matches-property()` {#extended-css-property}
-Pseudo-třída `:matches-property()` umožňuje vybrat prvek podle jeho vlastností.
+The `:matches-property()` pseudo-class allows selecting an element by matching its properties.
**Syntaxe**
@@ -3688,19 +3701,19 @@ Pseudo-třída `:matches-property()` umožňuje vybrat prvek podle jeho vlastnos
- `name` — povinný, jednoduchý řetězec *nebo* řetězec se zástupným znakem *nebo* regulární výraz pro porovnávání názvů vlastností prvků
- `value` — volitelný, jednoduchý řetězec *nebo* řetězec se zástupným znakem *nebo* regulární výraz pro porovnávání názvů vlastností prvků
-**Uvození speciálních znaků**
+**Escaping special characters**
-Pro vzory **regexp** `"` a `\` musí být uvozeno, např. `div:matches-property(prop=/[\\w]{4}/)`.
+For **regexp** patterns `"` and `\` must be escaped, e.g. `div:matches-property(prop=/[\\w]{4}/)`.
:::note
-Vzory regexp jsou podporovány v `name` pro libovolnou vlastnost v řetězci, např. `prop./^unit[\\d]{4}$/.type`.
+Regexp patterns are supported in `name` for any property in chain, e.g. `prop./^unit[\\d]{4}$/.type`.
:::
**Příklady**
-Prvek s těmito vlastnostmi:
+An element with such properties:
```javascript
divProperties = {
@@ -3720,7 +3733,7 @@ divProperties = {
};
```
-lze vybrat pomocí některého z těchto rozšířených selektorů:
+can be selected by any of these extended selectors:
```adblock
div:matches-property(check.track)
@@ -3734,24 +3747,24 @@ div:matches-property(memoizedProps.key="null")
div:matches-property(memoizedProps._owner.src=/ad/)
```
-:::tip Pro správce filtrů
+:::tip For filter maintainers
-Chcete-li zkontrolovat vlastnosti konkrétního prvku, postupujte takto:
+To check properties of a specific element, do the following:
-1. Zkontrolujte prvek stránky nebo jej vyberte na kartě `Elements` v nástroji DevTools prohlížeče
-1. Spusťte `console.dir($0)` na kartě `Console`
+1. Inspect the page element or select it in `Elements` tab of browser DevTools
+1. Run `console.dir($0)` in `Console` tab
:::
:::caution Omezení
-Vzory regexp **nepodporují** příznaky.
+Regexp patterns **do not support** flags.
:::
#### Pseudo-třída `:xpath()` {#extended-css-xpath}
-Pseudo-třída `:xpath()` umožňuje vybrat prvek vyhodnocením výrazu XPath.
+The `:xpath()` pseudo-class allows selecting an element by evaluating an XPath expression.
**Syntaxe**
@@ -3764,22 +3777,22 @@ Pseudo-třída `:xpath()` umožňuje vybrat prvek vyhodnocením výrazu XPath.
##### `:xpath()` limitations {#extended-css-xpath-limitations}
-`cíl` lze vynechat, takže je volitelný. Pro jakoukoli jinou pseudo-třídu by to znamenalo "aplikuj na *všechny* uzly DOM", ale v případě `:xpath()` to znamená jen "aplikuj na *celý* dokument", a takovéto použití výrazně zpomaluje výběr prvků. Proto jsou pravidla jako `#?#:xpath(expression)` omezena na nahlížení do znaku `body`. Např. pravidlo `#?#:xpath(//div[@data-st-area=\'Advert\'])` je analyzováno jako `#?#body:xpath(//div[@data-st- area=\'Advert\'])`.
+`target` can be omitted so it is optional. For any other pseudo-class that would mean "apply to *all* DOM nodes", but in case of `:xpath()` it just means "apply to the *whole* document", and such applying slows elements selecting significantly. That's why rules like `#?#:xpath(expression)` are limited to looking inside the `body` tag. For example, rule `#?#:xpath(//div[@data-st-area=\'Advert\'])` is parsed as `#?#body:xpath(//div[@data-st-area=\'Advert\'])`.
-Rozšířené selektory s definovaným `target` jako *libovolný selektor* — `*:xpath(expression)` — lze stále použít, ale nedoporučuje se to, proto by měl být místo toho uveden `target`.
+Extended selectors with defined `target` as *any* selector — `*:xpath(expression)` — can still be used but it is not recommended, so `target` should be specified instead.
-Funguje správně pouze na konci selektoru, s výjimkou [pseudo-třídy :remove()](#remove-pseudos).
+Works properly only at the end of selector, except for [pseudo-class :remove()](#remove-pseudos).
**Příklady**
-`:xpath(//*[@class="banner"])` vybere prvek `div#target1`:
+`:xpath(//*[@class="banner"])` selects the element `div#target1`:
```html
```
-`:xpath(//*[@class="inner"]/..)` vybere prvek `div#target2`:
+`:xpath(//*[@class="inner"]/..)` selects the element `div#target2`:
```html
@@ -3790,7 +3803,7 @@ Funguje správně pouze na konci selektoru, s výjimkou [pseudo-třídy :remove(
#### Pseudo-třída `:nth-ancestor()` {#extended-css-nth-ancestor}
-Pseudo-třída `:nth-ancestor()` umožňuje vyhledat *nth* předka vzhledem k dříve vybranému prvku.
+The `:nth-ancestor()` pseudo-class allows to lookup the *nth* ancestor relative to the previously selected element.
```text
subject:nth-ancestor(n)
@@ -3810,11 +3823,11 @@ subject:nth-ancestor(n)
##### `:nth-ancestor()` limitations {#extended-css-nth-ancestor-limitations}
-Pseudo-třída `:nth-ancestor()` není podporována v argumentu [pseudo-třídy `:not()`](#extended-css-not).
+The `:nth-ancestor()` pseudo-class is not supported inside the argument of the [`:not()` pseudo-class](#extended-css-not).
**Příklady**
-Pro DOM:
+For such DOM:
```html
@@ -3831,11 +3844,11 @@ Pro DOM:
```
-`.child:nth-ancestor(1)` vybere prvek `div#target1`, `div[class="inner"]:nth-ancestor(3)` vybere prvek `div#target2`.
+`.child:nth-ancestor(1)` selects the element `div#target1`, `div[class="inner"]:nth-ancestor(3)` selects the element `div#target2`.
#### Pseudo-třída `:upward()` {#extended-css-upward}
-Pseudo-třída `:upward()` umožňuje vyhledat předka vzhledem k dříve vybranému prvku.
+The `:upward()` pseudo-class allows to lookup the ancestor relative to the previously selected element.
**Syntaxe**
@@ -3850,11 +3863,11 @@ subject:upward(ancestor)
##### `:upward()` limitations {#extended-css-upward-limitations}
-Pseudo-třída `:nth-upward()` není podporována v argumentu [pseudo-třídy `:not()`](#extended-css-not).
+The `:upward()` pseudo-class is not supported inside the argument of the [`:not()` pseudo-class](#extended-css-not).
**Příklady**
-Pro DOM:
+For such DOM:
```html
@@ -3871,13 +3884,13 @@ Pro DOM:
```
-`.inner:upward(div[data])` vybere prvek `div#target1`, `.inner:upward(div[id])` vybere prvek `div#target2`, `.child:upward(1)` vybere prvek `div#target1`, `.inner:upward(3)` vybere prvek `div#target2`.
+`.inner:upward(div[data])` selects the element `div#target1`, `.inner:upward(div[id])` selects the element `div#target2`, `.child:upward(1)` selects the element `div#target1`, `.inner:upward(3)` selects the element `div#target2`.
#### Pseudo-třída `:remove()` a pseudo-vlastnost `remove` {#remove-pseudos}
-Někdy je nutné odpovídající prvek odstranit namísto jeho skrytí nebo použití vlastních stylů. Chcete-li to provést, můžete použít pseudo-třídu `:remove()` a také pseudo-vlastnost `remove`.
+Sometimes, it is necessary to remove a matching element instead of hiding it or applying custom styles. In order to do it, you can use the `:remove()` pseudo-class as well as the `remove` pseudo-property.
-**Pseudo-třídu `:remove()` lze umístit pouze na konec selektoru.**
+**Pseudo-class `:remove()` can be placed only at the end of a selector.**
**Syntaxe**
@@ -3893,11 +3906,11 @@ selector { remove: true; }
##### `:remove()` a `remove` limitations {#extended-css-remove-limitations}
-Pseudo-třída `:remove()` je omezena tak, aby správně fungovala pouze na konci selektoru.
+The `:remove()` pseudo-class is limited to work properly only at the end of selector.
-Pro použití pseudo-třídy `:remove()` na libovolný prvek je třeba použít [univerzální selektor](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`. V opačném případě může být takový rozšířený selektor považován za neplatný, např. `.banner > :remove()` neplatí pro odstranění jakéhokoli podřízeného prvku třídy `banner`, takže by měl vypadat jako `.banner > *:remove()`.
+For applying the `:remove()` pseudo-class to any element, the [universal selector](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*` should be used. Otherwise such extended selector may be considered as invalid, e.g. `.banner > :remove()` is not valid for removing any child element of `banner` class element, so it should look like `.banner > *:remove()`.
-Pokud je použita pseudo-třída `:remove()` nebo pseudovlastnost `remove`, všechny vlastnosti stylu se ignorují kromě pseudovlastnosti [`debug`](#selectors-debug-mode).
+If the `:remove()` pseudo-class or the `remove` pseudo-property is used, all style properties are ignored except for the [`debug` pseudo-property](#selectors-debug-mode).
**Příklady**
@@ -3911,13 +3924,13 @@ div[class]:has(> a > img) { remove: true; }
:::note
-Pravidla s pseudovlastností `remove` musí používat znak `#$?#`: `$` pro syntaxi pravidel stylu CSS, `?` pro syntaxi ExtendedCss.
+Rules with the `remove` pseudo-property must use `#$?#` marker: `$` for CSS-style rule syntax, `?` for ExtendedCss syntax.
:::
#### Pseudo-třída `:is()` {#extended-css-is}
-Pseudo-třída `:is()` umožňuje porovnat jakýkoli prvek, který lze vybrat kterýmkoli ze selektorů, které jí byly předány. Neplatné selektory jsou přeskočeny a pseudo-třída se vypořádá s platnými selektory bez vyhození chyby. Naše implementace [nativní pseudotřídy `:is()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:is).
+The `:is()` pseudo-class allows to match any element that can be selected by any of selectors passed to it. Invalid selectors are skipped and the pseudo-class deals with valid ones with no error thrown. Our implementation of the [native `:is()` pseudo-class](https://developer.mozilla.org/en-US/docs/Web/CSS/:is).
**Syntaxe**
@@ -3930,15 +3943,15 @@ Pseudo-třída `:is()` umožňuje porovnat jakýkoli prvek, který lze vybrat kt
##### `:is()` limitations {#extended-css-is-limitations}
-Pravidla s pseudo-třídou `:is()` musí používat nativní implementaci [ `:has()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:is), pokud pravidla používají znak `##` a pokud je to možné, tj. bez dalších rozšířených selektorů uvnitř. Chcete-li vynutit použití pravidel ExtendedCss s `:is()`, použijte explicitně znak `#?#`/`#$?#`.
+Rules with the `:is()` pseudo-class must use the [native implementation of `:is()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:is) if rules use `##` marker and it is possible, i.e. with no other extended selectors inside. To force applying ExtendedCss rules with `:is()`, use `#?#`/`#$?#` marker explicitly.
-Pokud je argument `:is()` pseudo-třídy `selector` rozšířeným selektorem, vzhledem ke způsobu, jakým je v ExtendedCss v2.0 implementována pseudo-třída `:is()`, není možné ji použít na horní uzel DOM, kterým je `html`, tj. `#?#html:is()` nefunguje. Pokud tedy `target` není definován nebo je definován jako [univerzální selektor](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`, je rozšířené použití pseudo-třídy omezeno na **`html`potomky**, např. pravidla `#?#:is(...)` a `#?#*:is(...)` jsou analyzována jako `#?#html *:is(...)`. Upozorňujeme, že pro standardní argument selektoru takové omezení neexistuje, tj. `#?#html:is(.locked)` funguje bez problémů.
+If the `:is()` pseudo-class argument `selectors` is an extended selector, due to the way how the `:is()` pseudo-class is implemented in ExtendedCss v2.0, it is impossible to apply it to the top DOM node which is `html`, i.e. `#?#html:is()` does not work. So if `target` is not defined or defined as the [universal selector](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`, the extended pseudo-class applying is limited to **`html`'s children**, e.g. rules `#?#:is(...)` and `#?#*:is(...)` are parsed as `#?#html *:is(...)`. Please note that there is no such limitation for a standard selector argument, i.e. `#?#html:is(.locked)` works fine.
-[Komplexní selektory](https://www.w3.org/TR/selectors-4/#complex) s rozšířenými pseudo-třídami nejsou podporovány jako argument `selector` pro pseudo-třídu `:is()`, povoleny jsou pouze [složené](https://www.w3.org/TR/selectors-4/#compound). Další podrobnosti naleznete v příkladech níže.
+[Complex selectors](https://www.w3.org/TR/selectors-4/#complex) with extended pseudo-classes are not supported as `selectors` argument for `:is()` pseudo-class, only [compound ones](https://www.w3.org/TR/selectors-4/#compound) are allowed. Check examples below for more details.
**Příklady**
-`#container *:is(.inner, .footer)` vybere pouze prvek `div#target1`:
+`#container *:is(.inner, .footer)` selects only the element `div#target1`:
```html
@@ -3951,7 +3964,7 @@ Pokud je argument `:is()` pseudo-třídy `selector` rozšířeným selektorem, v
```
-Kvůli omezením `:is(*:not([class]) > .banner)'` nefunguje, ale lze místo něj použít `:is(*:not([class]):has(> .banner))` k výběru prvku `div#target2`:
+Due to limitations `:is(*:not([class]) > .banner)'` does not work but `:is(*:not([class]):has(> .banner))` can be used instead of it to select the element `div#target2`:
```html
@@ -3963,7 +3976,7 @@ Kvůli omezením `:is(*:not([class]) > .banner)'` nefunguje, ale lze místo něj
#### Pseudo-třída `:not()` {#extended-css-not}
-Pseudo-třída `:not()` umožňuje vybrat prvky, které se *neshodují* se selektory předávanými jako argument. Neplatné selektory argumentů nejsou povoleny a je třeba vyhodit chybu. Naše implementace pseudo-třídy [`:not()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:not).
+The `:not()` pseudo-class allows to select elements which are *not matched* by selectors passed as argument. Invalid argument selectors are not allowed and error is to be thrown. Our implementation of the [`:not()` pseudo-class](https://developer.mozilla.org/en-US/docs/Web/CSS/:not).
**Syntaxe**
@@ -3976,17 +3989,17 @@ Pseudo-třída `:not()` umožňuje vybrat prvky, které se *neshodují* se selek
##### `:not()` limitations {#extended-css-not-limitations}
-Pravidla s pseudo-třídou `:not()` musí používat nativní implementaci [ `:not()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:not), pokud pravidla používají znak `##` a pokud je to možné, tj. bez dalších rozšířených selektorů uvnitř. Chcete-li vynutit použití pravidel ExtendedCss s `:not()`, použijte explicitně znak `#?#`/`#$?#`.
+Rules with the `:not()` pseudo-class must use the [native implementation of `:not()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:not) if rules use `##` marker and it is possible, i.e. with no other extended selectors inside. To force applying ExtendedCss rules with `:not()`, use `#?#`/`#$?#` marker explicitly.
-Pokud je argument `:not()` pseudo-třídy `selector` rozšířeným selektorem, vzhledem ke způsobu, jakým je v ExtendedCss v2.0 implementována pseudo-třída `:not()`, není možné ji použít na horní uzel DOM, kterým je `html`, tj. `#?#html:not()` nefunguje. Pokud tedy `target` není definován nebo je definován jako [univerzální selektor](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`, je rozšířené použití pseudo-třídy omezeno na **`html`potomky**, např. pravidla `#?#:not(...)` a `#?#*:not(...)` jsou analyzována jako `#?#html *:not(...)`. Upozorňujeme, že pro standardní argument selektoru takové omezení neexistuje, tj. `#?#html:not(.locked)` funguje bez problémů.
+If the `:not()` pseudo-class argument `selectors` is an extended selector, due to the way how the `:not()` pseudo-class is implemented in ExtendedCss v2.0, it is impossible to apply it to the top DOM node which is `html`, i.e. `#?#html:not()` does not work. So if `target` is not defined or defined as the [universal selector](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`, the extended pseudo-class applying is limited to **`html`'s children**, e.g. rules `#?#:not(...)` and `#?#*:not(...)` are parsed as `#?#html *:not(...)`. Please note that there is no such limitation for a standard selector argument, i.e. `#?#html:not(.locked)` works fine.
-`:not()` je považována za standardní pseudo-třídu CSS uvnitř argumentu pseudo-třídy [`:upward()`](#extended-css-upward), protože `:upward()` podporuje pouze standardní selektory.
+The `:not()` is considered as a standard CSS pseudo-class inside the argument of the [`:upward()` pseudo-class](#extended-css-upward) because `:upward()` supports only standard selectors.
-"Up-looking" pseudotřídy, které jsou [`:nth-ancestor()`](#extended-css-nth-ancestor) a [`:upward()`](#extended-css-upward) nejsou podporovány uvnitř argumentu `selector` pro pseudo-třídu `:not()`.
+"Up-looking" pseudo-classes which are [`:nth-ancestor()`](#extended-css-nth-ancestor) and [`:upward()`](#extended-css-upward) are not supported inside `selectors` argument for `:not()` pseudo-class.
**Příklady**
-`#container > *:not(h2, .text)` vybere pouze prvek `div#target1`:
+`#container > *:not(h2, .text)` selects only the element `div#target1`:
```html
@@ -4001,31 +4014,31 @@ Pokud je argument `:not()` pseudo-třídy `selector` rozšířeným selektorem,
:::danger Upozornění na odstranění
-Pseudo-třída `:if-not()` je odstraněna a již není podporována. Pravidla s tímto modifikátorem jsou považována za neplatná.
+The `:if-not()` pseudo-class is removed and is no longer supported. Pravidla s tímto modifikátorem jsou považována za neplatná.
:::
-Tato pseudo-třída byla v podstatě zkratkou pro `:not(:has())`. Byla podporována ExtendedCss pro lepší kompatibilitu s některými odběry filtrů.
+This pseudo-class was basically a shortcut for `:not(:has())`. It was supported by ExtendedCss for better compatibility with some filters subscriptions.
### Přednost kosmetických pravidel {#cosmetic-rules-priority}
-Způsob, jakým jsou aplikována pravidla **pro skrývání prvků** a **CSS**, je specifický pro danou platformu.
+The way **element hiding** and **CSS rules** are applied is platform-specific.
-**V aplikacích AdGuard pro Windows, AdGuard pro Mac, AdGuard pro Android a AdGuard pro Linux** používáme soubor stylů vložený do stránky. Priorita kosmetických pravidel je stejná jako u jakéhokoli jiného souboru stylů CSS na webových stránkách. Existují však omezení: [skrytí prvku](#cosmetic-elemhide-rules) a [pravidla CSS](#cosmetic-css-rules) nemohou přepsat vložené styly. V takových případech se doporučuje použít rozšířené selektory nebo filtrování HTML.
+**In AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux**, we use a stylesheet injected into the page. The priority of cosmetic rules is the same as any other websites' CSS stylesheet. But there is a limitation: [element hiding](#cosmetic-elemhide-rules) and [CSS rules](#cosmetic-css-rules) cannot override inline styles. In such cases, it is recommended to use extended selectors or HTML filtering.
-**V Rozšíření prohlížeče AdGuard** se používají tzv. "soubory uživatelských stylů". Mají vyšší prioritu než řádkové styly.
+**In AdGuard Browser Extension**, the so-called "user stylesheets" are used. They have higher priority than even the inline styles.
-**Rozšířené selektory CSS** používají k práci JavaScript a v podstatě samy přidávají vložený styl, takže mohou přepsat jakýkoli styl.
+**Extended CSS selectors** use JavaScript to work and basically add an inline style themselves, therefore they can override any style.
## HTML pravidla filtrování {#html-filtering-rules}
-Ve většině případů stačí k filtrování reklam základní a kosmetická pravidla. Někdy je však nutné změnit kód HTML samotné stránky před jejím načtením. V takovém případě potřebujete pravidla pro filtrování obsahu HTML. Umožňují označit prvky HTML, které mají být vyříznuty před načtením stránky prohlížečem.
+In most cases, the basis and cosmetic rules are enough to filter ads. But sometimes it is necessary to change the HTML-code of the page itself before it is loaded. This is when you need filtering rules for HTML content. They allow to indicate the HTML elements to be cut out before the browser loads the page.
:::info Kompatibilita
-Pravidla filtrování HTML podporuje AdGuard pro Windows, AdGuard pro Mac, AdGuard pro Android, AdGuard pro Linux a rozšíření prohlížeče AdGuard pro Firefox. Taková pravidla v rozšířeních pro jiné prohlížeče nefungují, protože nemohou měnit obsah na úrovni sítě.
+HTML filtering rules are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, AdGuard for Linux, and AdGuard Browser Extension for Firefox. Such rules do not work in extensions for other browsers because they are unable to modify content on network level.
-Syntaxi s volitelnou hodnotou `value` v atributech podporuje AdGuard pro Windows, AdGuard pro Mac a AdGuard pro Android s knihovnou CoreLibs v1.18 nebo novější. Podporuje ji také rozšíření Rozšíření prohlížeče AdGuard v5.2 nebo novější. U ostatních produktů a předchozích verzí musí být **vždy** uvedena hodnota `value`. V opačném případě bude pravidlo považováno za nesprávné a bude ignorováno.
+The syntax with an optional `value` in the attributes is supported by AdGuard for Windows, AdGuard for Mac, and AdGuard for Android with CoreLibs v1.18 or later. It is also supported by AdGuard Browser Extension v5.2 or later. For the other products and previous versions `value` must **always** be specified. Otherwise, the rule will be treated as incorrect and ignored.
:::
@@ -4050,21 +4063,21 @@ pseudoClasses = pseudoClass *pseudoClass
### Příklady
-**Kód HTML:**
+**HTML code:**
```html
```
-**Pravidlo:**
+**Rule:**
```adblock
example.org$$script[data-src="banner"]
```
-Toto pravidlo odstraní všechny prvky `script` s atributem `data-src` obsahujícím podřetězec `banner`. Pravidlo platí pouze pro `example.org` a všechny její subdomény.
+This rule removes all `script` elements with the attribute `data-src` containing the substring `banner`. The rule applies only to `example.org` and all its subdomains.
-Pokud je hodnota atributu v pravidle vynechána, bude prvek odstraněn, pokud obsahuje zadaný atribut bez ohledu na jeho hodnotu. Tímto způsobem lze také odstranit prvky, jejichž atributy nemají vůbec žádnou hodnotu.
+If the value of the attribute is omitted in the rule, then the element will be removed if it contains the specified attribute, regardless of its value. This is also the way to remove the elements whose attributes don't have any value at all.
```html
@@ -4075,25 +4088,25 @@ Pokud je hodnota atributu v pravidle vynechána, bude prvek odstraněn, pokud ob
example.org$$div[some_attribute]
```
-Toto pravidlo odstraní všechny prvky `div` s atributem `some_attribute` na `example.org` a všech jejích subdoménách. Oba prvky `div` z výše uvedeného příkladu budou odstraněny.
+This rule removes all `div` elements with the attribute `some_attribute` on `example.org` and all its subdomains. So, the both `div` elements from the example above will be removed.
### Speciální atributy
-Kromě obvyklých atributů, jejichž hodnotu kontroluje každý prvek, existuje sada speciálních atributů, které mění způsob fungování pravidla. Níže je uveden seznam těchto atributů:
+In addition to usual attributes, which value is every element checked for, there is a set of special attributes that change the way a rule works. Below there is a list of these attributes:
#### `tag-content`
-:::caution Upozornění na vyřazení
+:::caution Deprecation notice
-Tento speciální atribut může být v budoucnu nepodporován. Raději použijte pseudo-třídu `:contains()`, pokud je k dispozici.
+This special attribute may become unsupported in the future. Prefer using the `:contains()` pseudo-class where it is available.
:::
-Jedná se o nejčastěji používaný speciální atribut. Omezí výběr na ty prvky, jejichž kód innerHTML obsahuje zadaný podřetězec.
+This is the most frequently used special attribute. It limits selection with those elements whose innerHTML code contains the specified substring.
-Musíte použít `""` k uvození `"`>, např.: `$$script[tag-content="alert(""this is ad"")"]`
+You must use `""` to escape `"`, for instance: `$$script[tag-content="alert(""this is ad"")"]`
-Podívejte se například na tento HTML kód:
+For example, take a look at this HTML code:
```html
```
-Následující pravidlo smaže všechny prvky `script` s podřetězcem `banner` v jejich kódu:
+Following rule will delete all `script` elements with a `banner` substring in their code:
```adblock
$$script[tag-content="banner"]
@@ -4109,45 +4122,45 @@ $$script[tag-content="banner"]
:::caution Omezení
-Speciální atribut `tag-content` se nesmí objevit v selektoru nalevo od kombinátoru `>`.
+The `tag-content` special attribute must not appear in a selector to the left of a `>` combinator.
:::
#### `wildcard`
-:::caution Upozornění na vyřazení
+:::caution Deprecation notice
-Tento speciální atribut může být v budoucnu nepodporován. Raději použijte pseudo-třídu `:contains()`, pokud je k dispozici.
+This special attribute may become unsupported in the future. Prefer using the `:contains()` pseudo-class where it is available.
:::
-Tento speciální atribut funguje téměř jako `tag-content` a umožňuje kontrolovat kód dokumentu innerHTML. Pravidlo zkontroluje, zda kód HTML prvku odpovídá [vyhledávacímu vzoru](https://en.wikipedia.org/wiki/Glob_(programming)).
+This special attribute works almost like `tag-content` and allows you to check the innerHTML code of the document. Rule will check if HTML code of the element fits the [search pattern](https://en.wikipedia.org/wiki/Glob_(programming)).
-Musíte použít `""` k uvození `"`>, např.: `$$script[wildcard=""banner""]`
+You must use `""` to escape `"`, for instance: `$$script[wildcard=""banner""]`
-Např.: `$$script[wildcard="*banner*text*"]`
+For example: `$$script[wildcard="*banner*text*"]`
-Kontroluje, zda prvek code obsahuje dva po sobě jdoucí podřetězce `banner` a `text`.
+It checks if the element code contains the two consecutive substrings `banner` and `text`.
:::caution Omezení
-Speciální atribut `wildcard` se nesmí objevit v selektoru nalevo od kombinátoru `>`.
+The `wildcard` special attribute must not appear in a selector to the left of a `>` combinator.
:::
#### `max-length`
-:::caution Upozornění na vyřazení
+:::caution Deprecation notice
-Tento speciální atribut může být v budoucnu nepodporován. Raději použijte pseudotřídu `:contains()` s regulárním výrazem, pokud je k dispozici.
+This special attribute may become unsupported in the future. Prefer using the `:contains()` pseudo-class with a regular expression where it is available.
:::
-Určuje maximální délku obsahu prvku HTML. Pokud je tento parametr nastaven a délka obsahu přesahuje tuto hodnotu, pravidlo se na prvek nevztahuje.
+Specifies the maximum length for content of HTML element. If this parameter is set and the content length exceeds the value, a rule does not apply to the element.
-**Výchozí hodnota**
+**Default value**
-Pokud tento parametr není zadán, považuje se `max-lenght` za 8192.
+If this parameter is not specified, the `max-length` is considered to be 8192.
Např:
@@ -4155,23 +4168,23 @@ Např:
$$div[tag-content="banner"][max-length="400"]
```
-Toto pravidlo odstraní všechny prvky `div`, jejichž kód obsahuje podřetězec `banner` a jejichž délka nepřesahuje `400` znaků.
+This rule will remove all the `div` elements, whose code contains the substring `banner` and the length of which does not exceed `400` characters.
:::caution Omezení
-Speciální atribut `max-length` se nesmí objevit v selektoru nalevo od kombinátoru `>`.
+The `max-length` special attribute must not appear in a selector to the left of a `>` combinator.
:::
#### `min-length`
-:::caution Upozornění na vyřazení
+:::caution Deprecation notice
-Tento speciální atribut může být v budoucnu nepodporován. Raději použijte pseudotřídu `:contains()` s regulárním výrazem, pokud je k dispozici.
+This special attribute may become unsupported in the future. Prefer using the `:contains()` pseudo-class with a regular expression where it is available.
:::
-Určuje minimální délku obsahu prvku HTML. Pokud je tento parametr nastaven a délka obsahu je menší než nastavená hodnota, pravidlo se na prvek nevztahuje.
+Specifies the minimum length for content of HTML element. If this parameter is set and the content length is less than preset value, a rule does not apply to the element.
Např:
@@ -4179,11 +4192,11 @@ Např:
$$div[tag-content="banner"][min-length="400"]
```
-Toto pravidlo odstraní všechny prvky `div`, jejichž kód obsahuje podřetězec `banner` a jejichž délka přesahuje `400` znaků.
+This rule will remove all the `div` elements, whose code contains the substring `banner` and the length of which exceeds `400` characters.
:::caution Omezení
-Speciální atribut `min-length` se nesmí objevit v selektoru nalevo od kombinátoru `>`.
+The `min-length` special attribute must not appear in a selector to the left of a `>` combinator.
:::
@@ -4205,53 +4218,53 @@ nebo
:::note Kompatibilita
-`:-abp-contains()` a `:has-text()` jsou synonyma pro `:contains()`.
+`:-abp-contains()` and `:has-text()` are synonyms for `:contains()`.
:::
:::info Kompatibilita
-Pseudotřída `:contains()` je podporována aplikacemi AdGuard pro Windows, AdGuard pro Mac, AdGuard pro Android a AdGuard pro Linux s [knihovnou CoreLibs][] v1.13 nebo novější.
+The `:contains()` pseudo-class is supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.13 or later.
:::
-Vyžaduje, aby vnitřní HTML prvku obsahovalo zadaný text nebo odpovídalo zadanému regulárnímu výrazu.
+Requires that the inner HTML of the element contains the specified text or matches the specified regular expression.
:::caution Omezení
-Pseudotřída `:contains()` se nesmí objevit v selektoru nalevo od kombinátoru `>`.
+A `:contains()` pseudo-class must not appear in a selector to the left of a `>` combinator.
:::
### Výjimky
-Podobně jako u pravidel skrývání existuje speciální typ pravidel, který zakáže vybrané pravidlo filtrování HTML pro určité domény. Syntaxe je stejná, jen je třeba změnit `$$` na `$@$`.
+Similar to hiding rules, there is a special type of rules that disable the selected HTML filtering rule for particular domains. The syntax is the same, you just have to change `$$` to `$@$`.
-Ve filtru je např. pravidlo:
+For example, there is a rule in filter:
```adblock
$$script[tag-content="banner"]
```
-Pokud to chcete zakázat pro `example.com`, můžete vytvořit pravidlo výjimky:
+If you want to disable it for `example.com`, you can create an exception rule:
```adblock
example.com$@$script[tag-content="banner"]
```
-Někdy může být nutné zakázat všechna pravidla omezení. Např. k provádění testů. Za tímto účelem použijte pravidlo výjimky bez zadání domény.
+Sometimes, it may be necessary to disable all restriction rules. For example, to conduct tests. To do this, use the exclusion rule without specifying a domain.
```adblock
$@$script[tag-content="banner"]
```
-Tento druh výjimek doporučujeme používat pouze v případě, že není možné změnit samotné pravidlo skrývání. V ostatních případech je lepší změnit původní pravidlo pomocí omezení domény.
+We recommend to use this kind of exceptions only if it is not possible to change the hiding rule itself. In other cases it is better to change the original rule, using domain restrictions.
## Pravidla JavaScript {#javascript-rules}
-AdGuard podporuje speciální typ pravidel, která umožňují vložit na webové stránky libovolný kód JavaScript.
+AdGuard supports a special type of rules that allows you to inject any JavaScript code to websites pages.
-**Důrazně doporučujeme** používat [skriptlety](#scriptlets) namísto pravidel JavaScript, kdykoli je to možné. Pravidla JS mají pomoci s laděním, ale jako dlouhodobé řešení by se mělo používat pravidlo skriptlet.
+We **strongly recommend** using [scriptlets](#scriptlets) instead of JavaScript rules whenever possible. JS rules are supposed to help with debugging, but as a long-time solution a scriptlet rule should be used.
**Syntaxe**
@@ -4268,51 +4281,51 @@ rule = [domains] "#%#" script
**Výjimky**
-Podobně jako u pravidel skrývání existuje speciální typ pravidel, který zakáže vybrané pravidlo JavaScript pro určité domény. Syntaxe je stejná, jen je třeba změnit `#%#` na `#@%#`.
+Similar to hiding rules, there is a special type of rules that disable the selected JavaScript rule for particular domains. The syntax is the same, you just have to change `#%#` to `#@%#`.
-Ve filtru je např. pravidlo:
+For example, there is a rule in filter:
```adblock
#%#window.__gaq = undefined;
```
-Pokud to chcete zakázat pro `example.com`, můžete vytvořit pravidlo výjimky:
+If you want to disable it for `example.com`, you can create an exception rule:
```adblock
example.com#@%#window.__gaq = undefined;
```
-Někdy může být nutné zakázat všechna pravidla omezení. Např. k provádění testů. Za tímto účelem použijte pravidlo výjimky bez zadání domény.
+Sometimes, it may be necessary to disable all restriction rules. For example, to conduct tests. To do this, use the exclusion rule without specifying a domain.
```adblock
#@%#window.__gaq = undefined;
```
-Tento druh výjimek doporučujeme používat pouze v případě, že není možné změnit samotné pravidlo skrývání. V ostatních případech je lepší změnit původní pravidlo pomocí omezení domény.
+We recommend to use this kind of exceptions only if it is not possible to change the hiding rule itself. In other cases it is better to change the original rule, using domain restrictions.
:::caution Omezení
-Typ pravidel JavaScript lze použít pouze [**v důvěryhodných filtrech**](#trusted-filters).
+JavaScript rules can only be used [**in trusted filters**](#trusted-filters).
:::
:::info Kompatibilita
-Pravidla JavaScript nejsou Blokátorem obsahu AdGuard podporována.
+JavaScript rules are not supported by AdGuard Content Blocker.
:::
## Pravidla skriptlet {#scriptlets}
-Skriptlet je funkce JavaScript, která poskytuje rozšířené možnosti pro blokování obsahu. Tyto funkce lze v AdGuard pravidlech filtrování používat deklarativním způsobem.
+Scriptlet is a JavaScript function that provides extended capabilities for content blocking. These functions can be used in a declarative manner in AdGuard filtering rules.
:::note
-AdGuard podporuje mnoho různých skriptletů. Abychom dosáhli kompatibility mezi blokátory, podporujeme také syntaxi uBO a ABP.
+AdGuard supports a lot of different scriptlets. In order to achieve cross-blocker compatibility, we also support syntax of uBO and ABP.
:::
-**Syntaxe pravidel blokování**
+**Blocking rules syntax**
```text
[domains]#%#//scriptlet(name[, arguments])
@@ -4324,21 +4337,21 @@ AdGuard podporuje mnoho různých skriptletů. Abychom dosáhli kompatibility me
**Příklady**
-1. Použijte skriptlet `abort-on-property-read` na všech stránkách `example.org` a jejích subdoménách a předejte mu argument `alert`:
+1. Apply the `abort-on-property-read` scriptlet on all pages of `example.org` and its subdomains, and pass it an `alert` argument:
```adblock
example.org#%#//scriptlet('abort-on-property-read', 'alert')
```
-1. Odstraňte třídu `branding` ze všech prvků `div[class^="inner"]` na všech stránkách `example.org` a jejích subdoménách:
+1. Remove the `branding` class from all `div[class^="inner"]` elements on all pages of `example.org` and its subdomains:
```adblock
example.org#%#//scriptlet('remove-class', 'branding', 'div[class^="inner"]')
```
-**Syntaxe pravidel pro výjimky**
+**Exception rules syntax**
-Pravidla výjimek mohou zakázat některé skriptlety v určitých doménách. Syntaxe pravidel skriptletů pro výjimky je podobná jako u běžných pravidel skriptletů, ale místo `#%#` se používá `#@%#`:
+Exception rules can disable some scriptlets on particular domains. The syntax for exception scriptlet rules is similar to normal scriptlet rules but uses `#@%#` instead of `#%#`:
```text
[domains]#@%#//scriptlet([name[, arguments]])
@@ -4350,28 +4363,28 @@ Pravidla výjimek mohou zakázat některé skriptlety v určitých doménách. S
**Příklady**
-1. Zakázat specifické pravidlo skriptletu tak, aby se pouze `abort-on-property-read` použilo pouze na `example.org` a její subdomény:
+1. Disable specific scriptlet rule so that only `abort-on-property-read` is applied only on `example.org` and its subdomains:
```adblock
example.org,example.com#%#//scriptlet("abort-on-property-read", "alert")
example.com#@%#//scriptlet("abort-on-property-read", "alert")
```
-1. Zakázat všechny skriptlety `abort-on-property-read` pro `example.com` a její subdomény:
+1. Disable all `abort-on-property-read` scriptlets for `example.com` and its subdomains:
```adblock
example.org,example.com#%#//scriptlet("abort-on-property-read", "alert")
example.com#@%#//scriptlet("abort-on-property-read")
```
-1. Zakázat všechny skriptlety pro `example.com` a její subdomény:
+1. Disable all scriptlets for `example.com` and its subdomains:
```adblock
example.org,example.com#%#//scriptlet("abort-on-property-read", "alert")
example.com#@%#//scriptlet()
```
-1. Použijte `set-constant` a `set-cookie` na libovolnou webovou stránku, ale vzhledem ke speciálnímu pravidlu výjimky pro skriplety bude na `stránce example.org` a jejích subdoménách použito pouze `set-constant`:
+1. Apply `set-constant` and `set-cookie` to any web page, but due to special scriptlet exception rule only the `set-constant` scriptlet will be applied on `example.org` and its subdomains:
```adblock
#%#//scriptlet('set-constant', 'adList', 'emptyArr')
@@ -4379,7 +4392,7 @@ Pravidla výjimek mohou zakázat některé skriptlety v určitých doménách. S
example.org#@%#//scriptlet('set-cookie')
```
-1. Použijte `adjust-setInterval` na libovolnou webovou stránku a `set-local-storage-item` na `example.com` a jejích subdoménách, ale existuje také několik pravidel pro výjimky skriptletů, takže na `example.com` a jejích subdoménách nebudou použita žádná pravidla pro skriptlety:
+1. Apply `adjust-setInterval` to any web page and `set-local-storage-item` on `example.com` and its subdomains, but there are also multiple scriptlet exception rules, so no scriptlet rules will be applied on `example.com` and its subdomains:
```adblock
#%#//scriptlet('adjust-setInterval', 'count', '*', '0.001')
@@ -4387,49 +4400,49 @@ Pravidla výjimek mohou zakázat některé skriptlety v určitých doménách. S
example.com#@%#//scriptlet()
```
-Další informace o [ladění skriptletů](#debug-scriptlets).
+Learn more about [how to debug scriptlets](#debug-scriptlets).
-Další informace o skriptletech najdete [na GitHubu](https://github.com/AdguardTeam/Scriptlets#scriptlets).
+More information about scriptlets can be found [on GitHub](https://github.com/AdguardTeam/Scriptlets#scriptlets).
:::info Kompatibilita
-Skriplety nejsou Blokátorem obsahu AdGuard podporovány.
+Scriptlet rules are not supported by AdGuard Content Blocker.
-Úplná syntaxe pravidel pro výjimky skriptletů je podporována AdGuardem pro Windows, AdGuardem pro Mac, AdGuardem pro Android a AdGuardem pro Linux s [CoreLibs][] v1.16 nebo novějšími a rozšířením prohlížeče AdGuard pro Chrome, Firefox a Edge s [TSUrlFilter][] v3.0 nebo novějším. Předchozí verze podporují pouze pravidla výjimek, která zakazují konkrétní skriptlety.
+The full syntax of scriptlet exception rules is supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.16 or later, and AdGuard Browser Extension for Chrome, Firefox, and Edge with [TSUrlFilter][] v3.0 or later. Previous versions only support exception rules that disable specific scriptlets.
:::
### Důvěryhodné skriptlety {#trusted-scriptlets}
-Důvěryhodné skriptlety jsou skriptlety [](#scriptlets) s rozšířenou funkčností. Znamená to stejnou syntaxi a omezení. Názvy důvěryhodných skriptletů mají předponu `trusted-`, např. `trusted-set-cookie`, aby je bylo možné snadno odlišit od běžných skriptletů.
+Trusted scriptlets are [scriptlets](#scriptlets) with extended functionality. It means the same syntax and restrictions. Trusted scriptlet names are prefixed with `trusted-`, e.g. `trusted-set-cookie`, to be easily distinguished from common scriptlets.
:::note
-Důvěryhodné skriptlety nejsou kompatibilní s jinými blokátory reklam kromě AdGuardu.
+Trusted scriptlets are not compatible with other ad blockers except AdGuard.
:::
:::caution Omezení
-Důvěryhodné skriplety lze použít pouze [**v důvěryhodných filtrech**](#trusted-filters).
+Trusted scriptlets rules can only be used [**in trusted filters**](#trusted-filters).
:::
:::info Kompatibilita
-Důvěryhodné skriplety nejsou Blokátorem obsahu AdGuard podporovány.
+Trusted scriptlets rules are not supported by AdGuard Content Blocker.
:::
-Další informace o [ladění skriptletů](#debug-scriptlets).
+Learn more about [how to debug scriptlets](#debug-scriptlets).
-Další informace o důvěryhodných skriptletech najdete na [GitHubu](https://github.com/AdguardTeam/Scriptlets#trusted-scriptlets).
+More information about trusted scriptlets can be found [on GitHub](https://github.com/AdguardTeam/Scriptlets#trusted-scriptlets).
## Modifikátory pro ostatní typ pravidel {#non-basic-rules-modifiers}
-Každé pravidlo lze upravit pomocí modifikátorů popsaných v následujících odstavcích.
+Each rule can be modified using the modifiers described in the following paragraphs.
-**Syntaxe** {#non-basic-rules-modifiers-syntax}
+**Syntax** {#non-basic-rules-modifiers-syntax}
```text
rule = "[$" modifiers "]" [rule text]
@@ -4439,9 +4452,9 @@ modifiers = modifier0[, modifier1[, ...[, modifierN]]]
- **`modifier`** — sada modifikátorů popsaných níže.
- **`rule text`** — pravidlo, které je třeba změnit.
-Např.: `[$domain=example.com,app=test_app]##selector`.
+For example, `[$domain=example.com,app=test_app]##selector`.
-V modifikátorech musí být uvozeny hodnoty následujících znaků: `[`, `]`, `,`a `\` (pokud se pro uvození nepoužívá). K uvození použijte `\`. Např. uvozená závorka vypadá takto: `\]`.
+In the modifiers values, the following characters must be escaped: `[`, `]`, `,`, and `\` (unless it is used for the escaping). Use `\` to escape them. For example, an escaped bracket looks like this: `\]`.
| Modifikátor \ Produkty | [Aplikace CoreLibs][cl-apps] | [AdGuard pro Chromium][ext-chr] | [AdGuard pro Chrome MV3][ext-mv3] | [AdGuard pro Firefox][ext-ff] | [AdGuard pro iOS][ios-app] | [AdGuard pro Safari][ext-saf] | [Blokátor obsahu AdGuard][and-cb] |
| ------------------------------------- |:----------------------------:|:---------------------------------------------:|:------------------------------------------------:|:---------------------------------------------:|:--------------------------:|:-----------------------------:|:---------------------------------:|
@@ -4460,7 +4473,7 @@ V modifikátorech musí být uvozeny hodnoty následujících znaků: `[`, `]`,
### **`$app`** {#non-basic-app-modifier}
-Modifikátor `$app` umožňuje zúžit pokrytí pravidla na konkrétní aplikaci, nebo seznam aplikací. Chování a syntaxe modifikátoru dokonale odpovídají příslušným [základním pravidlům modifikátoru `$app`](#app-modifier).
+`$app` modifier lets you narrow the rule coverage down to a specific application or a list of applications. The modifier's behavior and syntax perfectly match the corresponding [basic rules `$app` modifier](#app-modifier).
**Příklady**
@@ -4471,13 +4484,13 @@ Modifikátor `$app` umožňuje zúžit pokrytí pravidla na konkrétní aplikaci
:::info Kompatibilita
-Taková pravidla s modifikátorem `$app` podporuje AdGuard pro Windows, Mac, Android a Linux.
+Such rules with `$app` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux.
:::
### **`$domain`** {#non-basic-domain-modifier}
-Modifikátor `$domain` omezuje oblast použití pravidla na seznam domén a jejich subdomén. Chování a syntaxe modifikátoru dokonale odpovídají příslušným [základním pravidlům modifikátoru `$domain`](#domain-modifier).
+`$domain` modifier limits the rule application area to a list of domains and their subdomains. The modifier's behavior and syntax perfectly match the corresponding [basic rules `$domain` modifier](#domain-modifier).
**Příklady**
@@ -4485,30 +4498,30 @@ Modifikátor `$domain` omezuje oblast použití pravidla na seznam domén a jeji
- `[$domain=example.com|example.org]###adblock` — skryje prvek s atributem `id`, který se rovná `adblock` na `example.com`, `example.org` a všech subdoménách.
- `[$domain=~example.com]##.textad` — toto pravidlo skryje prvek `div` se třídou `textad` na všech doménách kromě `example.com` a jejích subdomén.
-Existují 2 způsoby, jak určit omezení domény pro ostatní pravidla:
+There are 2 ways to specify domain restrictions for non-basic rules:
-1. "klasický" způsob je zadat domény před masku pravidla a atributy: `example.com##.textad`;
-2. přístup modifikátoru spočívá v určení domén pomocí modifikátoru `$domain`: `[$domain=example.com]##.textad`.
+1. the "classic" way is to specify domains before rule mask and attributes: `example.com##.textad`;
+2. the modifier approach is to specify domains via `$domain` modifier: `[$domain=example.com]##.textad`.
-Pravidla s omezením domén smíšeného stylu jsou však považována za neplatná. Takže např. pravidlo `[$domain=example.org]example.com##.textad` bude zamítnuto.
+But rules with mixed style domains restriction are considered invalid. So, for example, the rule `[$domain=example.org]example.com##.textad` will be ignored.
### Nezákladní omezení modifikátoru `$domain` {#non-basic-domain-modifier-limitations}
:::caution Omezení
-Vzhledem k tomu, že nezákladní modifikátor `$domain` funguje stejně jako základní, má stejná [omezení](#domain-modifier-limitations).
+Since the non-basic `$domain` works the same as the basic one, it has the same [limitations](#domain-modifier-limitations).
:::
:::info Kompatibilita
-Pravidla s modifikátorem `$domain` podporuje AdGuard pro Windows, AdGuard pro macOS, AdGuard pro Android, Rozšíření prohlížeče AdGuard pro Chrome, Chrome MV3, Firefox a Edge.
+Such rules with `$domain` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, AdGuard Browser Extension for Chrome, Chrome MV3, Firefox, and Edge.
:::
### **`$path`** {#non-basic-path-modifier}
-Modifikátor `$path` omezuje oblast použití pravidel na konkrétní umístění nebo stránky na webových stránkách.
+`$path` modifier limits the rule application area to specific locations or pages on websites.
**Syntaxe**
@@ -4516,13 +4529,13 @@ Modifikátor `$path` omezuje oblast použití pravidel na konkrétní umístěn
$path ["=" pattern]
```
-`pattern` — volitelný, maska cesty, na kterou je pravidlo omezeno. Jeho syntaxe a chování jsou v podstatě stejné jako u [vzoru pro základní pravidla](#basic-rules-syntax). Můžete také použít [speciální znaky](#basic-rules-special-characters) s výjimkou `||`, což v tomto případě nemá smysl (viz příklady níže).
+`pattern` — optional, a path mask to which the rule is restricted. Its syntax and behavior are pretty much the same as with the [pattern for basic rules](#basic-rules-syntax). You can also use [special characters](#basic-rules-special-characters), except for `||`, which does not make any sense in this case (see examples below).
-Pokud není nastaven `pattern` pro `$path`, pravidlo bude platit pouze na hlavní stránce webu.
+If `pattern` is not set for `$path`, rule will apply only on the main page of website.
-Modifikátor `$path` odpovídá i řetězci dotazu.
+`$path` modifier matches the query string as well.
-Modifikátor `$path` podporuje regulární výrazy [stejným způsobem](#regexp-support) jako základní pravidla.
+`$path` modifier supports regular expressions in [the same way](#regexp-support) basic rules do.
**Příklady**
@@ -4537,13 +4550,13 @@ Modifikátor `$path` podporuje regulární výrazy [stejným způsobem](#regexp-
:::info Kompatibilita
-Pravidla s modifikátorem `$path` nejsou Blokátorem obsahu AdGuard podporována.
+Rules with `$path` modifier are not supported by AdGuard Content Blocker.
:::
### **`$url`** {#non-basic-url-modifier}
-Modifikátor `$url` omezuje oblast použití pravidla na adresy URL odpovídající zadané masce.
+`$url` modifier limits the rule application area to URLs matching the specified mask.
**Syntaxe**
@@ -4551,7 +4564,7 @@ Modifikátor `$url` omezuje oblast použití pravidla na adresy URL odpovídají
url = pattern
```
-kde `pattern` je v podstatě stejný jako [`pattern` základních pravidel](#basic-rules-syntax) za předpokladu, že [některé znaky](#non-basic-rules-modifiers-syntax) musí být uvozeny. Podporovány jsou také [speciální znaky](#basic-rules-special-characters) a [regulární výrazy](#regexp-support).
+where `pattern` is pretty much the same as [`pattern` of the basic rules](#basic-rules-syntax) assuming that [some characters](#non-basic-rules-modifiers-syntax) must be escaped. The [special characters](#basic-rules-special-characters) and [regular expressions](#regexp-support) are supported as well.
**Příklady**
@@ -4563,23 +4576,23 @@ kde `pattern` je v podstatě stejný jako [`pattern` základních pravidel](#bas
:::caution Omezení
-V rozšíření prohlížeče AdGuard, nezákladní `$url` modifikátor není kompatibilní s pravidly specifickými pro doménu a dalšími nezákladními modifikátory — [`$domain`](#non-basic-domain-modifier) a [`$path`](#non-basic-path-modifier). Např. pravidlo `[$url=/category/*]example.com###textad` nebude použito.
+In AdGuard Browser Extension, non-basic `$url` modifier is not compatible with domain-specific rules and other non-basic modifiers — [`$domain`](#non-basic-domain-modifier) and [`$path`](#non-basic-path-modifier). For example, the rule `[$url=/category/*]example.com###textad` will not be applied.
:::
:::info Kompatibilita
-Pravidla s modifikátorem `$url` jsou podporována AdGuardem pro Windows, AdGuardem pro Mac, AdGuardem pro Android a AdGuardem pro Linux s [CoreLibs][] v1.11 nebo novějším a rozšířením prohlížeče AdGuard s [TSUrlFilter][] v3.0.0 nebo novějším.
+Rules with the `$url` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.11 or later, and AdGuard Browser Extension with [TSUrlFilter][] v3.0.0 or later.
:::
## Informace pro správce filtrů
-Pokud spravujete filtr třetí strany, který je AdGuardu znám, mohly by vás zajímat informace uvedené v této části. Upozorňujeme, že nápovědy se použijí pouze na registrované filtry. Filtr je považován za registrovaný a známý pro AdGuard, pokud je přítomen v [indexu známých filtrů](https://filters.adtidy.org/extension/chromium/filters.json). Pokud chcete, aby byl váš filtr zaregistrován, odešlete žádost do [repozitáře AdguardFilters](https://github.com/AdguardTeam/AdguardFilters).
+If you maintain a third-party filter that is known to AdGuard, you might be interested in the information presented in this section. Please note that hints will be applied to registered filters only. The filter is considered to be registered and known by AdGuard, if it is present in the [known filters index](https://filters.adtidy.org/extension/chromium/filters.json). If you want your filter to be registered, please file an issue to [AdguardFilters repo](https://github.com/AdguardTeam/AdguardFilters).
### Direktivy preprocesoru
-Poskytujeme preprocesorové direktivy, které mohou být použity správci filtrů pro zlepšení kompatibility s různými blokátory reklam a poskytujeme:
+We provide preprocessor directives that can be used by filter maintainers to improve compatibility with different ad blockers and provide:
- [zahrnutý soubor](#include-directive)
- [použití pravidel podmíněně podle typu blokátoru reklam](#conditions-directive)
@@ -4587,15 +4600,15 @@ Poskytujeme preprocesorové direktivy, které mohou být použity správci filtr
:::note
-Jakákoli chyba v direktivě preprocesoru povede k tomu, že AdGuard selže při aktualizaci filtru stejným způsobem, jako kdyby adresa URL filtru byla nedostupná.
+Any mistake in a preprocessor directive will lead to AdGuard failing the filter update in the same way as if the filter URL was unavailable.
-Direktivy preprocesoru lze použít v uživatelských pravidlech nebo ve vlastních filtrech.
+Preprocessor directives can be used in the user rules or in the custom filters.
:::
#### Zahrnutý soubor {#include-directive}
-Direktiva `!#include` umožňuje zahrnout do filtru obsah zadaného souboru. Podporuje pouze soubory ze stejného původu, aby bylo zajištěno, že správce filtru má kontrolu nad zadaným souborem. Zahrnutý soubor může také obsahovat pre-direktivy (i další `!#include` direktivy). Blokátory reklam by měly zvážit případ rekurzivního `!#include` a implementovat ochranný mechanismus.
+The `!#include` directive allows to include contents of a specified file into the filter. It supports only files from the same origin to make sure that the filter maintainer is in control of the specified file. The included file can also contain pre-directives (even other `!#include` directives). Ad blockers should consider the case of recursive `!#include` and implement a protection mechanism.
**Syntaxe**
@@ -4603,17 +4616,17 @@ Direktiva `!#include` umožňuje zahrnout do filtru obsah zadaného souboru. Pod
!#include file_path
```
-kde `file_path` je absolutní nebo relativní cesta k souboru stejného původu, který má být zahrnut.
+where `file_path` is a same origin absolute or relative file path to be included.
-Soubory musí pocházet ze stejné domény, ale mohou být umístěny v jiné složce.
+The files must originate from the same domain, but may be located in a different folder.
-Pokud obsažený soubor není nalezen nebo není k dispozici, celá aktualizace filtru by měla selhat.
+If included file is not found or unavailable, the whole filter update should fail.
-Omezení stejného původu by mělo být pro místní vlastní filtry zakázáno.
+Same-origin limitation should be disabled for local custom filters.
**Příklady**
-URL filtru: `https://example.org/path/filter.txt`
+Filter URL: `https://example.org/path/filter.txt`
```adblock
! Valid (same origin):
@@ -4629,17 +4642,17 @@ URL filtru: `https://example.org/path/filter.txt`
#### Podmínky {#conditions-directive}
-Správci filtrů mohou pomocí podmínek zadávat různá pravidla v závislosti na typu blokátoru reklam. Podmíněná direktiva začínající direktivou `!#if` musí být explicitně ukončena direktivou `!#endif`. Podmínky podporují všechny základní logické operátory.
+Filter maintainers can use conditions to supply different rules depending on the ad blocker type. A conditional directive beginning with an `!#if` directive must explicitly be terminated with an `!#endif` directive. Conditions support all basic logical operators.
-Existují dva možné scénáře:
+There are two possible scenarios:
-1. Pokud blokátor reklamy narazí na direktivu `!#if` a ne `!#else`, zkompiluje kód mezi direktivami `!#if` a `!#endif` pouze v případě, že je zadaná podmínka pravdivá.
+1. When an ad blocker encounters an `!#if` directive and no `!#else` directive, it will compile the code between `!#if` and `!#endif` directives only if the specified condition is true.
-1. Pokud existuje direktiva `!#else`, bude zkompilován kód mezi `!#if` a `!#else`, pokud je podmínka pravdivá; v opačném případě bude zkompilován kód mezi `!#else` a `!#endif`.
+1. If there is an `!#else` directive, the code between `!#if` and `!#else` will be compiled if the condition is true; otherwise, the code between `!#else` and `!#endif` will be compiled.
:::note
-Na mezerách záleží. `!#if` je platná direktiva, zatímco `!# if` není.
+Whitespaces matter. `!#if` is a valid directive, while `!# if` is not.
:::
@@ -4688,7 +4701,7 @@ kde:
**Příklady**
```adblock
-! pro všechny produkty AdGuardu kromě AdGuardu pro Safari
+! for all AdGuard products except AdGuard for Safari
!#if (adguard && !adguard_ext_safari)
||example.org^$third-party
domain.com##div.ad
@@ -4696,7 +4709,7 @@ domain.com##div.ad
```
```adblock
-! direktivy lze dokonce kombinovat
+! directives even can be combined
!#if (adguard_app_android)
!#include /androidspecific.txt
!#endif
@@ -4704,20 +4717,20 @@ domain.com##div.ad
```adblock
!#if (adguard && !adguard_ext_safari)
-! pro všechny produkty AdGuardu kromě AdGuardu pro Safari
+! for all AdGuard products except AdGuard for Safari
||example.org^$third-party
domain.com##div.ad
!#else
-! pouze pro AdGuard pro Safari
-||subdomena.example.org^$third-party
+! for AdGuard for Safari only
+||subdomain.example.org^$third-party
!#endif
```
:::info Kompatibilita
-Direktiva `!#else` je podporována nástrojem [FiltersDownloader][gh-filters-downloader] v1.1.20 nebo novějším.
+The `!#else` directive is supported by the [FiltersDownloader][gh-filters-downloader] v1.1.20 or later.
-Je již podporována pro seznamy filtrů sestavené pomocí [FiltersRegistry][], ale stále nemusí být podporována produkty AdGuardu při přidání seznamu filtrů s `!#else` jako vlastních. Následující produkty ji budou podporovat ve zmíněných nebo novějších verzích:
+It is already supported for filter lists compiled by the [FiltersRegistry][], but it still may not be supported by AdGuard products when adding a filter list with `!#else` as a custom one. The following products will support it in the mentioned versions or later:
- AdGuard pro Windows, Mac a Android s [CoreLibs][] v1.13;
- Rozšíření prohlížeče AdGuard v4.2.208;
@@ -4727,9 +4740,9 @@ Je již podporována pro seznamy filtrů sestavené pomocí [FiltersRegistry][],
#### Afinita Safari {#safari-affinity-directive}
-Limit Safari pro každý blokátor obsahu je 150000 aktivních pravidel. V aplikacích AdGuard pro Safari a AdGuard pro iOS jsme však pravidla rozdělili do 6 blokátorů obsahu, čímž jsme zvýšili limit pravidel na 900000.
+Safari's limit for each content blocker is 150,000 active rules. But in AdGuard for Safari and AdGuard for iOS, we've split the rules into 6 content blockers, thus increasing the rule limit to 900,000.
-Zde je složení jednotlivých blokátorů obsahu:
+Here is the composition of each content blocker:
- AdGuard General — Blokování reklam, jazykově specifické filtry
- AdGuard Privacy — Soukromí
@@ -4738,11 +4751,11 @@ Zde je složení jednotlivých blokátorů obsahu:
- AdGuard Other — Jiné
- AdGuard Custom — Vlastní
-Uživatelská pravidla a Seznam povolených jsou přidány do každého blokátoru obsahu.
+User rules and allowlist are added to every content blocker.
:::caution
-Hlavní nevýhodou používání více blokátorů obsahu je, že pravidla různých blokátorů se uplatňují nezávisle. Na pravidla blokování to nemá vliv, ale pro pravidla odblokování mohou způsobit problémy. Pokud je pravidlo blokování v jednom blokátoru obsahu a výjimka v jiném, výjimka nebude fungovat. Správci filtrů používají `!#safari_cb_affinity` k definování afinity blokátorů obsahu Safari pro pravidla uvnitř blokování direktiv.
+The main disadvantage of using multiple content blockers is that rules from different blockers are applied independently. Blocking rules are not affected by this, but unblocking rules may cause problems. If a blocking rule is in one content blocker and an exception is in another, the exception will not work. Filter maintainers use `!#safari_cb_affinity` to define Safari content blocker affinity for the rules inside of the directive block.
:::
@@ -4771,14 +4784,14 @@ kde:
**Příklady**
```adblock
-! pro zobrazení konkrétního prvku, který je skryt základním filtrem AdGuardu:
-!#safari_cb_affinity(Obecné)
+! to unhide specific element which is hidden by AdGuard Base filter:
+!#safari_cb_affinity(general)
example.org#@#.adBanner
!#safari_cb_affinity
```
```adblock
-! pro seznam povolených základních pravidel z filtru AdGuard Tracking Protection:
+! to allowlist basic rule from AdGuard Tracking Protection filter:
!#safari_cb_affinity(privacy)
@@||example.org^
!#safari_cb_affinity
@@ -4786,7 +4799,7 @@ example.org#@#.adBanner
### Nápovědy
-"Hint" je speciální komentář, instrukce pro kompilátor filtrů používaný na straně serveru (viz [FiltersRegistry][]).
+"Hint" is a special comment, instruction to the filters compiler used on the server side (see [FiltersRegistry][]).
**Syntaxe**
@@ -4794,13 +4807,13 @@ example.org#@#.adBanner
!+ HINT_NAME1(PARAMS) HINT_NAME2(PARAMS)
```
-Lze použít více nápověd.
+Multiple hints can be applied.
#### Nápověda `NOT_OPTIMIZED`
-Pro každý filtr sestavuje AdGuard dvě verze: plnou a optimalizovanou. Optimalizovaná verze je mnohem jednodušší a neobsahuje pravidla, která se nepoužívají vůbec nebo jen zřídka.
+For each filter, AdGuard compiles two versions: full and optimized. Optimized version is much more lightweight and does not contain rules which are not used at all or used rarely.
-Frekvence používání pravidel vychází ze shromážděných statistik [pravidel filtrování](../tracking-filter-statistics). Optimalizace filtrů je však založena na více než na tom — některé filtry mají specifickou konfiguraci. Takto to vypadá pro Základní filtr:
+Rules usage frequency comes from the collected [filter rules statistics](../tracking-filter-statistics). But filters optimization is based on more than that — some filters have specific configuration. This is how it looks like for Base filter:
```text
"filter": AdGuard Base filter,
@@ -4818,21 +4831,21 @@ kde:
- **maxPercent** — horní mez hodnoty `percent` value
- **strict** — pokud je `percent < minPercent` NEBO `percent > maxPercent` a je zapnutý přísný režim, pak by kompilace filtru měla selhat, jinak je nutné použít původní pravidla
-Jinými slovy, `percent` je "úroveň komprese". Například pro Základní filtr je nastavena na 40 %. To znamená, že optimalizační algoritmus by měl odstranit 60 % pravidel.
+In other words, `percent` is the "compression level". For instance, for the Base filter it is configured to 40%. It means that optimization algorithm should strip 60% of rules.
-Nakonec zde jsou dvě verze základního filtru pro Rozšíření prohlížeče AdGuard:
+Eventually, here are the two versions of the Base filter for AdGuard Browser Extension:
- úplná: https://filters.adtidy.org/extension/chromium/filters/2.txt
- optimalizovaná: https://filters.adtidy.org/extension/chromium/filters/2_optimized.txt
-**Pokud chcete přidat pravidlo, které by nemělo být při optimalizaci odstraněno, použijte nápovědu `NOT_OPTIMIZED`:**
+**If you want to add a rule which should not be removed at optimization use the `NOT_OPTIMIZED` hint:**
```adblock
!+ NOT_OPTIMIZED
||example.org^
```
-**Toto pravidlo nebude optimalizováno pouze pro AdGuard pro Android:**
+**And this rule will not be optimized only for AdGuard for Android:**
```adblock
!+ NOT_OPTIMIZED PLATFORM(android)
@@ -4841,7 +4854,7 @@ Nakonec zde jsou dvě verze základního filtru pro Rozšíření prohlížeče
#### Nápověda `PLATFORM` a `NOT_PLATFORM`
-Slouží k zadání platforem pro použití pravidel. Seznam existujících platforem a odkazy např. na Základní filtr:
+Used to specify the platforms to apply the rules. List of existing platforms and links to Base filter, for example, for each of them:
- `windows` — AdGuard pro Windows — [https://filters.adtidy.org/windows/filters/2.txt](https://filters.adtidy.org/windows/filters/2.txt)
@@ -4871,14 +4884,14 @@ Slouží k zadání platforem pro použití pravidel. Seznam existujících plat
**Příklady**
-Toto pravidlo bude dostupné pouze v AdGuardu pro Windows, Mac a Android:
+This rule will be available only in AdGuard for Windows, Mac, Android:
```adblock
!+ PLATFORM(windows,mac,android)
||example.org^
```
-S výjimkou AdGuardu pro Safari, Blokátoru obsahu AdGuard a AdGuardu pro iOS je toto pravidlo k dispozici na všech platformách:
+Except for AdGuard for Safari, AdGuard Content Blocker, and AdGuard for iOS, this rule is available on all platforms:
```adblock
!+ NOT_PLATFORM(ext_safari, ext_android_cb, ios)
@@ -4887,9 +4900,9 @@ S výjimkou AdGuardu pro Safari, Blokátoru obsahu AdGuard a AdGuardu pro iOS je
#### `NOT_VALIDATE`
-Tato nápověda slouží k přeskočení validace pravidla. Je to užitečné pro pravidla, pro která dosud nebyla do překladače filtrů přidána podpora, nebo pro pravidla, která jsou nesprávně vyřazena.
+This hint is used to skip validation of the rule. It is useful for rules for which support has not yet been added to the filters compiler, or for rules that are incorrectly discarded.
-**Pokud chcete přidat pravidlo, které by nemělo být validováno, použijte nápovědu `NOT_VALIDATE`:**
+**If you want to add a rule that should not be validated, use the `NOT_VALIDATE` hint:**
```adblock
!+ NOT_VALIDATE
@@ -4898,13 +4911,13 @@ Tato nápověda slouží k přeskočení validace pravidla. Je to užitečné pr
## Jak ladit pravidla filtrování
-Jednoduchá pravidla filtrování je možné vytvořit "v hlavě", ale pro cokoli alespoň trochu složitějšího budete potřebovat další nástroje pro jejich ladění a iteraci. Existují nástroje, které vám s tím pomohou. V prohlížeči Chrome a jeho analogiích v ostatních prohlížečích můžete použít nástroj DevTools, ale většina produktů AdGuardu nabízí ještě jeden — Záznam filtrování.
+It may be possible to create simple filtering rules "in your head" but for anything even slightly more complicated you will need additional tools to debug and iterate them. There are tools to assist you with that. You can use DevTools in Chrome and its analogs in other browsers but most AdGuard products provide another one — Filtering log.
### Záznam filtrování
-Záznam filtrování je pokročilý nástroj, který bude užitečný především pro vývojáře filtrů. Obsahuje seznam všech webových požadavků, které procházejí skrze AdGuard, poskytuje vyčerpávající informace o každém z nich, nabízí několik možností třídění a další užitečné funkce.
+Filtering log is an advanced tool that will be helpful mostly to filter developers. It lists all web requests that pass through AdGuard, gives you exhaustive information on each of them, offers multiple sorting options, and has other useful features.
-V závislosti na tom, který AdGuard produkt používáte, se protokol filtrování může nacházet na různých místech.
+Depending on which AdGuard product you are using, Filtering log can be located in different places.
- V **AdGuardu pro Windows** jej najdete na kartě *Blokátor reklam* nebo prostřednictvím nabídky na hlavním panelu
- V **AdGuardu pro Mac** je pod *Nastavení → Pokročilé → Záznam filtrování*
@@ -4913,17 +4926,17 @@ V závislosti na tom, který AdGuard produkt používáte, se protokol filtrová
:::note
-V **AdGuardu pro iOS** a **AdGuardu pro Safari** Záznam filtrování neexistuje kvůli způsobu, jakým jsou v Safari implementovány blokátory obsahu. AdGuard tyto webové požadavky nevidí, a proto je nemůže zobrazit.
+In **AdGuard for iOS** and **AdGuard for Safari**, Filtering log does not exist because of the way content blockers are implemented in Safari. AdGuard does not see the web requests and therefore cannot display them.
:::
### Režim ladění selektorů {#selectors-debug-mode}
-Někdy můžete potřebovat zkontrolovat výkonnost daného selektoru nebo souboru stylů. Abyste to mohli provést bez přímé interakce s JavaScript, můžete použít speciální vlastnost stylu `debug`. Když `ExtendedCss` splňuje tuto vlastnost, povolí režim ladění buď pro jeden selektor, nebo pro všechny selektory v závislosti na hodnotě `debug`.
+Sometimes, you might need to check the performance of a given selector or a stylesheet. In order to do it without interacting with JavaScript directly, you can use a special `debug` style property. When `ExtendedCss` meets this property, it enables the debugging mode either for a single selector or for all selectors, depending on the `debug` value.
-Otevřete konzolu prohlížeče na webové stránce a zobrazte statistiky časování pro selektor(y), které zde byly použity. Režim ladění zobrazí následující statistiky jako objekt, kde každý z laděných selektorů je klíč a hodnota je objekt s těmito vlastnostmi:
+Open the browser console while on a web page to see the timing statistics for selector(s) that were applied there. Debugging mode displays the following stats as object where each of the debugged selectors are keys, and value is an object with such properties:
-**Vždy vytištěno:**
+**Always printed:**
- `selectorParsed` — text parsovaného selektoru se může lišit od vstupního textu
- `timings` — seznam uzlů DOM odpovídajících selektoru
@@ -4933,44 +4946,44 @@ Otevřete konzolu prohlížeče na webové stránce a zobrazte statistiky časov
- `standardDeviation` — standardní odchylka
- `timingsSum` — celkový čas potřebný k použití selektoru na stránce ve všech instancích
-**Vytištěno pouze pro odstranění pseudonymů:**
+**Printed only for remove pseudos:**
- `removed` — příznak signalizující, zda byly prvky odstraněny
-**Vytištěno, pokud prvky nejsou odstraněny:**
+**Printed if elements are not removed:**
- `matchedElements` — seznam uzlů DOM odpovídajících selektoru
- `styleApplied` — parsovaná deklarace stylu pravidla související se selektorem
**Příklady**
-**Ladění jednoho selektoru:**
+**Debugging a single selector:**
-Pokud je hodnota vlastnosti `debug` `true`, zobrazí se v konzole prohlížeče pouze informace o tomto selektoru.
+When the value of the `debug` property is `true`, only information about this selector will be shown in the browser console.
```adblock
#$?#.banner { display: none; debug: true; }
```
-**Povolení globálního ladění:**
+**Enabling global debug:**
-Pokud je hodnota vlastnosti `debug` `global`, konzola zobrazí informace o všech rozšířených selektorech CSS, které mají na aktuální stránce shodu pro všechna pravidla z libovolného povoleného filtru.
+When the value of the `debug` property is `global`, the console will display information about all extended CSS selectors that have matches on the current page, for all the rules from any of the enabled filters.
```adblock
#$?#.banner { display: none; debug: global; }
```
-**Testování rozšířených selektorů bez AdGuardu**
+**Testing extended selectors without AdGuard**
-ExtendedCss lze spustit na libovolné stránce bez použití AdGuard produktu. Za tímto účelem byste měli zkopírovat a spustit následující kód v konzoli prohlížeče:
+ExtendedCss can be executed on any page without using any AdGuard product. In order to do that you should copy and execute the following code in a browser console:
```js
!function(e,t,d){C=e.createElement(t),C.src=d,C.onload=function(){alert("ExtendedCss loaded successfully")},s=e.getElementsByTagName(t)[0],s?s.parentNode.insertBefore(C,s):(h=e.getElementsByTagName("head")[0],h.appendChild(C))}(document,"script","https://AdguardTeam.github.io/ExtendedCss/extended-css.min.js");
```
-Případně nainstalujte [uživatelský skript ExtendedCssDebugger](https://github.com/AdguardTeam/Userscripts/blob/master/extendedCssDebugger/extended-css.debugger.user.js).
+Alternatively, install the [ExtendedCssDebugger userscript](https://github.com/AdguardTeam/Userscripts/blob/master/extendedCssDebugger/extended-css.debugger.user.js).
-Nyní můžete použít `ExtendedCss` z globálního rozsahu a spustit jeho metodu [`query()`](https://github.com/AdguardTeam/ExtendedCss#extended-css-query) jako `Document.querySelectorAll()`.
+Now you can now use the `ExtendedCss` from global scope, and run its method [`query()`](https://github.com/AdguardTeam/ExtendedCss#extended-css-query) as `Document.querySelectorAll()`.
**Příklady**
@@ -4983,9 +4996,9 @@ ExtendedCss.query(selector);
### Ladění skriptletů {#debug-scriptlets}
-Pokud používáte Rozšíření prohlížeče AdGuard a chcete vyladit pravidlo [skriptlet](#scriptlets) nebo [důvěryhodný skriptlet](#trusted-scriptlets), můžete získat další informace otevřením protokolu filtrování. V takovém případě se skriptlety přepnou do režimu ladění a v konzoli prohlížeče se zobrazí více informací.
+If you are using AdGuard Browser Extension and want to debug a [scriptlet](#scriptlets) or a [trusted scriptlet](#trusted-scriptlets) rule, you can get additional information by opening the Filtering log. In that case, scriptlets will switch to debug mode and there will be more information in the browser console.
-Následující skriptlety jsou speciálně vyvinuty zejména pro účely ladění:
+The following scriptlets are especially developed for debug purposes:
- [`debug-current-inline-script`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#debug-current-inline-script)
- [`debug-on-property-read`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#debug-on-property-read)
@@ -4995,7 +5008,7 @@ Následující skriptlety jsou speciálně vyvinuty zejména pro účely laděn
- [`log-eval`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#log-eval)
- [`log`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#log)
-Následující skriptlety lze také použít pro účely ladění:
+The following scriptlets also may be used for debug purposes:
- [`json-prune`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#json-prune)
- [`prevent-fetch`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#prevent-fetch)
@@ -5011,13 +5024,13 @@ Následující skriptlety lze také použít pro účely ladění:
### Zkratky produktů {#what-product}
-1. `aplikace CoreLibs` — [AdGuard pro Windows](/adguard-for-windows/features/home-screen), [AdGuard pro Mac](/adguard-for-mac/features/main), [AdGuard pro Android](/adguard-for-android/features/protection/ad-blocking) a [AdGuard pro Linux](/adguard-for-linux)
-1. `AdGuard pro Chromium` — [Rozšíření prohlížeče AdGuard](/adguard-browser-extension/availability) pro Chrome a další prohlížeče založené na Chromium, např. nový Microsoft Edge a Opera
-1. `Adguard pro Chrome MV3` — [Rozšíření prohlížeče AdGuard pro Chrome MV3](/adguard-browser-extension/mv3-version)
-1. `Adguard pro Firefox` — [Rozšíření prohlížeče AdGuard](/adguard-browser-extension/availability) pro Firefox
-1. `AdGuard pro iOS` — [AdGuard pro iOS](/adguard-for-ios/features/safari-protection) a AdGuard pro iOS Pro (pro mobilní prohlížeč Safari)
-1. `AdGuard pro Safari` — [AdGuard pro desktopový prohlížeč Safari](/adguard-for-safari/features/general)
-1. `Blokátor obsahu AdGuard` — [blokátor obsahu](/adguard-content-blocker/overview) pro mobilní prohlížeče Android: Samsung Internet a Yandex Browser
+1. `CoreLibs apps` — [AdGuard for Windows](/adguard-for-windows/features/home-screen), [AdGuard for Mac](/adguard-for-mac/features/main), [AdGuard for Android](/adguard-for-android/features/protection/ad-blocking), and [AdGuard for Linux](/adguard-for-linux)
+1. `AdGuard for Chromium` — [AdGuard Browser Extension](/adguard-browser-extension/availability) for Chrome and other Chromium-based browsers such as Microsoft Edge and Opera
+1. `AdGuard for Chrome MV3` — [AdGuard Browser Extension for Chrome MV3](/adguard-browser-extension/mv3-version)
+1. `AdGuard for Firefox` — [AdGuard Browser Extension](/adguard-browser-extension/availability) for Firefox
+1. `AdGuard for iOS` — [AdGuard for iOS](/adguard-for-ios/features/safari-protection) and AdGuard Pro for iOS (for mobile Safari browser)
+1. `AdGuard for Safari` — [AdGuard for desktop Safari browser](/adguard-for-safari/features/general)
+1. `AdGuard Content Blocker` — [Content Blocker](/adguard-content-blocker/overview) for Android mobile browsers: Samsung Internet and Yandex Browser
### Zkratky kompatibility {#what-compatibility}
@@ -5057,8 +5070,11 @@ Následující skriptlety lze také použít pro účely ladění:
[ext-ff]: #what-product "AdGuard Browser Extension for Firefox"
[ios-app]: #what-product "AdGuard for iOS and AdGuard Pro for iOS"
[ios-app]: #what-product "AdGuard for iOS and AdGuard Pro for iOS"
+[ios-app]: #what-product "AdGuard for iOS and AdGuard Pro for iOS"
[ext-saf]: #what-product "AdGuard pro Safari"
[ext-saf]: #what-product "AdGuard for Safari"
+[ext-saf]: #what-product "AdGuard for Safari"
+[and-cb]: #what-product "AdGuard Content Blocker for Samsung Internet and Yandex Browser on Android"
[and-cb]: #what-product "AdGuard Content Blocker for Samsung Internet and Yandex Browser on Android"
[and-cb]: #what-product "AdGuard Content Blocker for Samsung Internet and Yandex Browser on Android"
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index e214b5ade90..2f8dbda285f 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ Mezi AdGuard filtry blokující reklamy patří:
- Základní filtr AdGuardu
- Filtr mobilních reklam AdGuard
- Regionální filtry rozdělené podle jazyků — čínština, holandština, francouzština, němčina, japonština, ruština, španělština/portugalština, turečtina a ukrajinština
-- Filtr rychlých oprav AdGuard
### Účel těchto filtrů
- **Základní filtr** je určen k blokování reklam na anglicky psaných webových stránkách a na těch, pro které neexistuje samostatný filtr. Obsahuje také obecná pravidla filtrování, která platí pro všechny weby bez ohledu na jazyk
- **Filtr mobilních reklam** blokuje reklamy na mobilních verzích webových stránek a v mobilních aplikacích. Neexistuje žádná segmentace na základě jazyka
- **Regionální filtry** se řídí stejnými zásadami jako **Základní filtr**, ale jsou omezeny na webové stránky v konkrétních jazycích
-- **Filtr rychlých oprav** slouží k rychlému řešení kritických problémů s filtrováním obsahu na oblíbených webech bez aktualizace rozšíření MV3.
Cílem filtrů pro blokování reklam je blokovat všechny typy reklam na webových stránkách, v aplikacích a v některých zařízeních, která mohou načítat reklamy z internetu:
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 2735ff815be..3df7d66e56c 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ Done, AdGuard for Android TV is installed.
- In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index b1adcc3ff6a..ae7977af510 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 80028b51bd2..6f24ecc69f0 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ Die maximale Anzahl der gleichzeitig aktivierten Filter beträgt **50**.
**Dynamische Regeln:** Es gilt eine strikte Obergrenze von **5.000** Regeln, darunter maximal 1.000 Regex-Regeln.
-Wenn diese Grenze überschritten wird, werden nur **5.000 umgewandelte Regeln** in der folgenden Reihenfolge angewendet: zuerst Freigabeliste, dann Benutzerregeln, benutzerdefinierte Filter und schließlich der Filter Quick Fixes.
+Wenn diese Grenze überschritten wird, werden nur **5.000 umgewandelte Regeln** in der folgenden Reihenfolge angewendet: zuerst Freigabeliste, dann Benutzerregeln und schließlich benutzerdefinierte Filter.
> **Konvertierte Regeln** sind Regeln, die mit dem [deklarativen Konverter][github-declarative-converter] in das \[DNR-Format] umgewandelt wurden.
> Während dieses Umwandlungsprozesses können einige Regeln andere überschreiben (`$badfilter`), einige können kombiniert werden (`$removeparam`), was zu einer Liste von Regeln mit einer etwas anderen Reihenfolge führt.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-browser-extension/user-scripts-api.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-browser-extension/user-scripts-api.md
index 73c4d84de24..f524a8a4588 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-browser-extension/user-scripts-api.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-browser-extension/user-scripts-api.md
@@ -5,36 +5,36 @@ sidebar_position: 8
:::info
-In diesem Artikel geht es um die AdGuard Browsereweiterung, die nur Ihren Browser schützt. To protect your entire device, [download the AdGuard app](https://adguard.com/download.html?auto=true).
+In diesem Artikel geht es um die AdGuard Browsereweiterung, die nur Ihren Browser schützt. Um Ihr gesamtes Gerät zu schützen, [laden Sie die AdGuard-App herunter](https://adguard.com/download.html?auto=true).
:::
-When adding a custom filter or user rule, a notification will appear asking you to enable the Developer mode to use these features in the extension.
+Beim Hinzufügen eines benutzerdefinierten Filters oder einer Benutzerregel wird eine Benachrichtigung angezeigt, in der Sie aufgefordert werden, den Entwicklermodus zu aktivieren, um diese Funktionen in der Erweiterung nutzen zu können.
-
+
-Starting with version 5.2, AdGuard Browser Extension uses the User Scripts API. Chrome requires this new API to follow best practices for user safety.
+Ab Version 5.2 verwendet die AdGuard-Browsererweiterung die User Scripts API. Chrome verlangt von dieser neuen API, dass bewährte Methoden für die Sicherheit der Nutzer eingehalten werden.
-## What is the User Scripts API?
+## Was ist die User Scripts API?
-The User Scripts API is a tool that allows extensions to run customized JavaScript scripts on webpages. These are often used to modify or enhance websites in ways that aren’t originally provided by the website itself.
+Die User Scripts API ist ein Tool, mit dem Erweiterungen benutzerdefinierte JavaScript-Skripte auf Webseiten ausführen können. Diese werden häufig verwendet, um Websites auf eine Weise zu verändern oder zu verbessern, die von der Website selbst nicht vorgesehen ist.
-With the shift to Chrome’s Manifest V3, many older methods of injecting scripts are limited or delayed. However, there is an exception for the User Scripts API.
+Mit der Umstellung auf Chrome's Manifest V3 sind viele ältere Methoden zur Einbindung von Skripten eingeschränkt oder verzögert. Es gibt jedoch eine Ausnahme für die User Scripts API.
-Learn more about the impacts of the MV3 policies in our [blog post](https://adguard.com/en/blog/review-issues-in-chrome-web-store.html).
+Erfahren Sie mehr über die Auswirkungen der MV3-Politik in unserem [Blogbeitrag](https://adguard.com/de/blog/review-issues-in-chrome-web-store.html).
-## How to enable the Developer mode
+## So aktivieren Sie den Entwicklermodus
-To use custom filters and JavaScript rules in the _User Rules_ tab, you must set up your browser first. This will give the extension a reliable and secure method of injecting scripts into webpages at the optimal time. Follow the instructions below depending on your Chrome version.
+Um benutzerdefinierte Filter und JavaScript-Regeln im Tab _Benutzerregeln_ verwenden zu können, müssen Sie zunächst Ihren Browser einrichten. Dadurch erhält die Erweiterung eine zuverlässige und sichere Methode, um Skripte zum optimalen Zeitpunkt in Webseiten einzuschleusen. Befolgen Sie die nachfolgenden Anweisungen je nach Ihrer Chrome-Version.
-### For Chrome versions prior to 138
+### Für Chrome-Versionen vor 138
-You must enable Developer mode for extensions. To do so, open the Chrome menu by clicking the three dots in the upper-right corner, go to _Extensions_ ⭢ _Manage extensions_, and toggle the _Developer mode_ switch.
+Sie müssen zunächst den Entwicklermodus für Erweiterungen aktivieren. Öffnen Sie dazu das Chrome-Menü, indem Sie auf die drei Punkte in der oberen rechten Ecke klicken, gehen Sie zu _Erweiterungen_ ⭢ _Erweiterungen verwalten_ und schalten Sie den Schalter _Entwicklermodus_ um.
-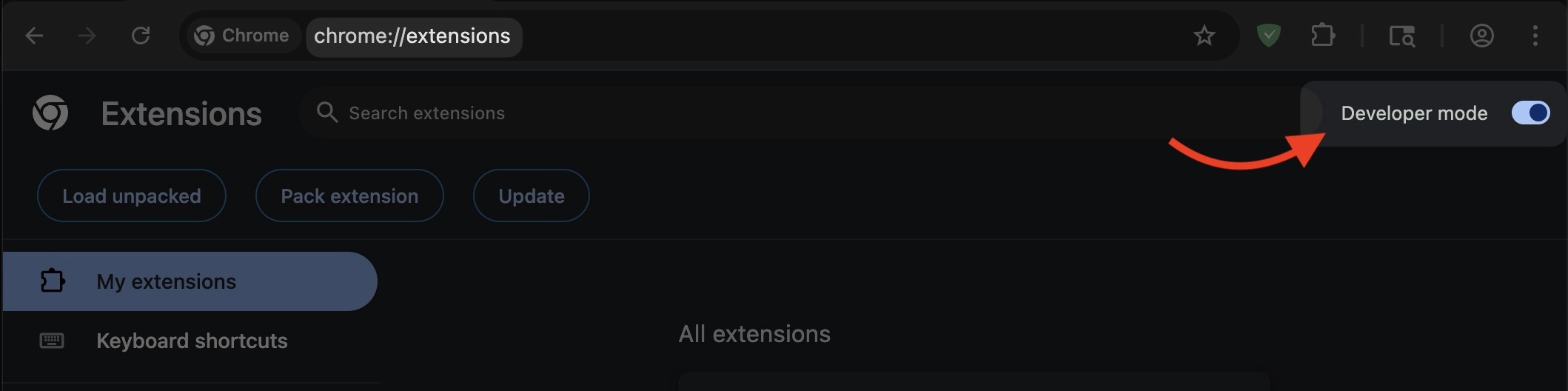
+
-### For Chrome version 138 and later
+### Für Chrome-Versionen 138 und neuer
-You must enable the _Allow user scripts_ toggle. To do so, open the Chrome menu by clicking the three dots in the upper-right corner, go to _Extensions_ ⭢ _Manage extensions_, go to AdGuard Browser Extension’s _Details_, and toggle the _Allow user scripts_ switch.
+Sie müssen das Kontrollkästchen _Benutzerskripte zulassen_ aktivieren. Öffnen Sie dazu das Chrome-Menü, indem Sie auf die drei Punkte in der oberen rechten Ecke klicken, gehen Sie zu _Erweiterungen_ ⭢ _Erweiterungen verwalten_, gehen Sie zu _Details_ der AdGuard-Browsererweiterung und schalten Sie den Schalter _Benutzerskripte zulassen_ um.
-
+
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/features.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/features.md
index 5d8c1cc89bc..c2ff7783ae6 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/features.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/features.md
@@ -35,7 +35,7 @@ Allgemeine, erweiterte und Low-Level-Einstellungen, mit denen Sie die Sprache un
## Low-Level-Einstellungen
-Descriptions of the low-level settings available in AdGuard for Android v4.3 and later.
+Beschreibungen der Low-Level-Einstellungen, die in AdGuard für Android v4.3 und höher verfügbar sind.
[Leitfaden für Low-Level-Einstellungen](/adguard-for-android/features/low-level-settings.md)
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b23cc9eccab..6d332b871dc 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound-Proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/protection/private-browser.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/protection/private-browser.md
index e40749121fc..3fd409e7391 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/protection/private-browser.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/protection/private-browser.md
@@ -11,7 +11,7 @@ Dieser Artikel behandelt AdGuard für Android, einem multifunktionalen Werbebloc
In Version 4.7 hat AdGuard für Android einen privaten In-App-Browser eingeführt. Sie können darauf vom Hauptbildschirm aus zugreifen, indem Sie auf die Schaltfläche _Privater Browser_ oder auf den Tab _Schutz_ tippen, in dem sich einige Anpassungsoptionen befinden.
-
+
Das können Sie einrichten:
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/protection/protection.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/protection/protection.md
index 20a1820dd43..f999cd6eae6 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/protection/protection.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/protection/protection.md
@@ -11,13 +11,13 @@ Dieser Artikel behandelt AdGuard für Android, einem multifunktionalen Werbebloc
Der Tab _Schutz_ umfasst die folgenden Funktionen oder Einstellungen. In dieser Wissensdatenbank finden Sie einen ausführlichen Artikel zu jedem dieser Themen.
-## Ad blocking
+## Werbeblocker
Einstellungen zum Blockieren von Werbung in Browsern und Apps
[Sperren von Werbung](/adguard-for-android/features/protection/ad-blocking.md)
-## Tracking protection
+## Tracking-Schutz
Einstellungen, mit denen Sie Tracking-Tools blockieren können, die Nutzerdaten sammeln
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index aa19ec74bee..20295d8b66e 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 589934c6191..c1ce86e3bf3 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -33,7 +33,7 @@ Fertig, AdGuard für Android TV ist installiert.
- Klicken Sie auf das AdGuard-Symbol, um die App zu starten.
- Folgen Sie den Anweisungen auf dem Bildschirm, um die Einrichtung abzuschließen.
-## Installation von AdGuard für Android TV über ADB
+## AdGuard für Android TV über ADB installieren
1. Stellen Sie sicher, dass die Android Debug Bridge (ADB) auf Ihrem Computer installiert ist. Wenn nicht, können Sie die Anweisungen auf XDA Developers befolgen: [ADB-Installationsanleitung](https://www.xda-developers.com/install-adb-windows-macos-linux).
@@ -58,3 +58,31 @@ Fertig, AdGuard für Android TV ist installiert.
- Geben Sie im Terminal den Befehl `adb install Downloads/adguard_tv.apk` ein. Ersetzen Sie gegebenenfalls `Downloads/adguard_tv.apk` durch Ihren Pfad.
- Warten Sie auf eine Meldung im Terminal, die die erfolgreiche Installation der App anzeigt.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/solving-problems/premium-activation.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/solving-problems/premium-activation.md
index 9d9497dadbb..979fd7a5e20 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/solving-problems/premium-activation.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/solving-problems/premium-activation.md
@@ -5,20 +5,20 @@ sidebar_position: 1
:::info
-Dieser Artikel behandelt AdGuard für iOS, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. To see how it works, [download the AdGuard app](https://agrd.io/download-kb-adblock).
+Dieser Artikel behandelt AdGuard für iOS, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. Um zu sehen, wie es funktioniert, laden Sie [die AdGuard-App](https://agrd.io/download-kb-adblock)herunter.
:::
-There are two ways to activate Premium features in the AdGuard for iOS app:
+Es gibt zwei Optionen, um Premium-Funktionen in der AdGuard für iOS-App zu aktivieren:
-1. **Purchase a subscription.** Just tap the **Get Premium** plaque anywhere in the app and follow the on-screen instructions. Enter your Apple Account password and confirm the purchase. You can choose a monthly, yearly, or lifetime subscription.
+1. **Ein Abonnement kaufen.** Tippen Sie einfach irgendwo in der App auf das Schild **Premium holen** und folgen Sie den Anweisungen auf dem Bildschirm. Geben Sie Ihr Apple Account-Passwort ein und bestätigen Sie den Kauf. Sie können ein monatliches, jährliches oder lebenslanges Abonnement wählen.
-2. **Use an AdGuard license.** You can buy one on the [AdGuard website](https://adguard.com/license.html). To activate it, open your AdGuard app, tap *Settings → License → Log in* and enter the same email address you used for purchase or your license key. If you have a valid license key in your account, the app will detect it automatically and activate Premium.
+2. **Eine AdGuard-Lizenz kaufen.** Sie können eine auf der [AdGuard-Website](https://adguard.com/license.html) erwerben. Um sie zu aktivieren, öffnen Sie Ihre AdGuard-App, tippen Sie auf *Einstellungen → Lizenz → Anmelden* und geben Sie dieselbe E-Mail-Adresse ein, die Sie beim Kauf verwendet haben, oder Ihren Lizenzschlüssel. Wenn Sie einen gültigen Lizenzschlüssel in Ihrem Konto haben, erkennt die App diesen automatisch und aktiviert Premium-Funktionen.
-Alternatively, to activate Premium features, you can enter a valid license key in the email field and leave the password field blank.
+Alternativ können Sie zur Aktivierung der Premium-Funktionen einen gültigen Lizenzschlüssel in das E-Mail-Feld eingeben und das Passwortfeld leer lassen.
:::note
-AdGuard Pro for iOS is our other iOS app. It can only be purchased from the [App Store](https://apps.apple.com/app/adguard-pro-adblock-privacy/id1126386264).
+AdGuard Pro für iOS ist unsere andere iOS-App. Sie kann nur im [App Store](https://apps.apple.com/app/adguard-pro-adblock-privacy/id1126386264)gekauft werden.
:::
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/solving-problems/system-wide-filtering.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/solving-problems/system-wide-filtering.md
index 94c13632192..47d295f2420 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/solving-problems/system-wide-filtering.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/solving-problems/system-wide-filtering.md
@@ -5,40 +5,40 @@ sidebar_position: 2
:::info
-Dieser Artikel behandelt AdGuard für iOS, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. To see how it works firsthand, [download the AdGuard app](https://agrd.io/download-kb-adblock).
+Dieser Artikel behandelt AdGuard für iOS, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. Um die Funktionsweise aus erster Hand zu erfahren, [laden Sie die AdGuard-App herunter](https://agrd.io/download-kb-adblock)
:::
## Über die systemweite Filterung
-System-wide filtering lets you block ads and trackers not just in Safari, but across other apps and browsers on your iOS device. iOS is a fairly closed operating system, and Apple provides limited options for blocking ads outside Safari. The only way to block ads and trackers system-wide is through [DNS filtering](https://adguard-dns.io/kb/general/dns-filtering/). This article explains how to enable it.
+Systemweites Filtering ermöglicht es Ihnen, Werbung und Tracker nicht nur in Safari, sondern auch in anderen Apps und Browsern auf Ihrem iOS-Gerät zu blockieren. iOS ist ein ziemlich geschlossenes Betriebssystem, und Apple bietet nur begrenzte Möglichkeiten zum Blockieren von Werbung außerhalb von Safari. Die einzige Möglichkeit, Werbung und Tracker systemweit zu blockieren, ist über [DNS-Filterung](https://adguard-dns.io/kb/general/dns-filtering/). In diesem Artikel wird erklärt, wie Sie diese Funktion aktivieren können.
-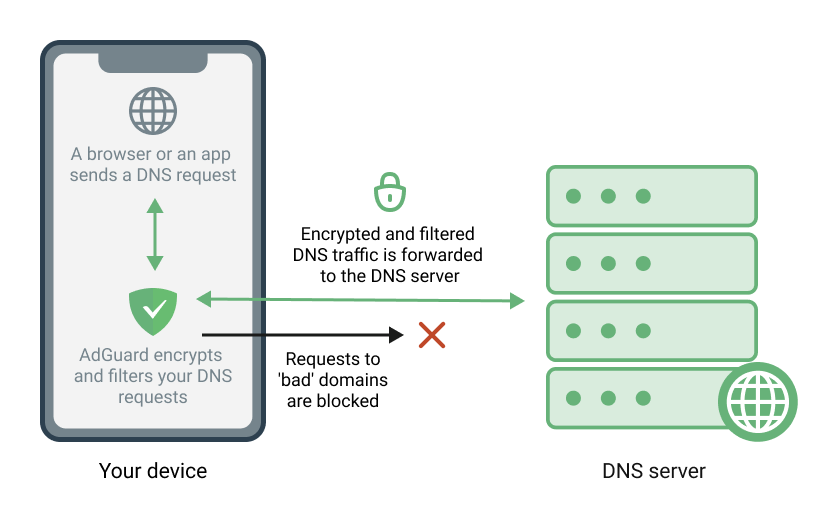
+
-The first thing you need to do is enable DNS protection:
+Als erstes muss der DNS-Schutz aktiviert werden:
-1. Open *AdGuard*.
-2. Tap the *Protection* icon (shield icon in the bottom menu bar).
-3. Turn on *DNS protection*.
+1. Öffnen Sie *AdGuard*.
+2. Tippen Sie auf das Symbol *Schutz* (Schildsymbol in der unteren Menüleiste).
+3. Schalten Sie *DNS-Schutz* ein.
-Once DNS protection is on, you have three options:
+Sobald der DNS-Schutz aktiviert ist, haben Sie drei Optionen:
-- **Use AdGuard DNS filter.** To enable it, go to *Protection* → *DNS protection* → *DNS filtering* → *DNS filters* → *AdGuard DNS filter*. With this option, you’re not tied to a specific blocking server — the filter does all the blocking.
-- **Use a blocking DNS server.** Go to *Protection* → *DNS protection* → *DNS server* and select *AdGuard DNS* or another blocking server to your liking.
-- **Add a custom DNS filter or hosts file.** You can add multiple DNS filters and hosts files. Be aware that using too many may slow down AdGuard.
+- **AdGuard DNS-Filter verwenden.** Um ihn zu aktivieren, gehen Sie zu *Schutz* → *DNS-Schutz* → *DNS-Filterung* → *DNS-Filter* → *AdGuard DNS-Filter*. Mit dieser Option sind Sie nicht an einen bestimmten Server gebunden — der Filter führt die gesamte Blockierung durch.
+- **Einen blockierenden DNS-Server verwenden.** Gehen Sie zu *Schutz* → *DNS-Schutz* → *DNS-Server* und wählen Sie *AdGuard DNS* oder einen anderen Blockierungsserver nach Ihrem Geschmack.
+- **Einen benutzerdefinierten DNS-Filter oder eine Hosts-Datei hinzufugen.** Es können mehrere DNS-Filter und Hosts-Dateien hinzugefügt werden. Beachten Sie, dass die Verwendung von zu vielen Filtern AdGuard verlangsamen kann.
-## How to add custom DNS filter and hosts file
+## Hinzufügen von benutzerdefinierten DNS-Filtern und Hosts-Dateien
-For example, let’s add the [OISD Blocklist Big](https://oisd.nl/).
+Fügen wir zum Beispiel die [OISD-Blockliste Big](https://oisd.nl/) hinzu.
-1. Copy the OISD Blocklist Big link: `https://big.oisd.nl`
-2. Open *Protection* → *DNS protection* → *DNS filtering* → *DNS filters*.
-3. Tap *Add a filter*.
-4. Paste the link into the filter URL field.
-5. Tap *Next* → *Add*.
+1. Kopieren Sie den Link für OISD Blocklist Big: `https://big.oisd.nl`
+2. Öffnen Sie *Schutz* → *DNS-Schutz* → *DNS-Filterung* → *DNS-Filter*.
+3. Tippen Sie auf *Filter hinzufügen*.
+4. Fügen Sie den Link in das URL-Feld des Filters ein.
+5. Tippen Sie auf *Weiter* → *Hinzufügen*.
-
+
-Add any number of DNS filters by repeating step 4 with a different URL. You can find various filter lists and their links at [filterlists.com](https://filterlists.com).
+Fügen Sie beliebig viele DNS-Filter hinzu, indem Sie Schritt 4 mit einer anderen URL wiederholen. Verschiedene Filterlisten und deren Links finden Sie unter [filterlists.com](https://filterlists.com).
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/web-extension.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/web-extension.md
index b1933e90aa7..3dfdabfb0d7 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/web-extension.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-ios/web-extension.md
@@ -41,48 +41,48 @@ Die Safari-Web-Erweiterung von AdGuard benötigt für ihre Funktion Zugriff auf
Die Web-Erweiterung ist kein eigenständiges Werkzeug und erfordert AdGuard für iOS. Wenn Sie AdGuard für iOS noch nicht auf Ihrem Gerät installiert haben, [installieren Sie bitte zunächst die App](../installation) und schließen Sie den Installationsvorgang ab, um die App für die Arbeit vorzubereiten.
-Once done, open the *Settings* app and scroll down to *Apps*.
+Öffnen Sie anschließend *Einstellungen* und scrollen Sie nach unten zu *Apps*.
-
+
-Then, open *Safari* → *Extensions*.
+Öffnen Sie dann *Safari* → *Erweiterungen*.
-
+
-
+
-In the **ALLOW THESE EXTENSIONS** section find **AdGuard** among the available extensions.
+Im Abschnitt **DIESE ERWEITERUNGEN ERLAUBEN** finden Sie **AdGuard** unter den verfügbaren Erweiterungen.
-
+
-Tap it, then toggle the *Allow Extension* switch on.
+Tippen Sie darauf und aktivieren Sie dann den Schalter *Erweiterung erlauben*.
-Lower on the same screen, make sure *All Websites* is set *Allow* or *Ask*. If you choose *Allow*, you won't have to give permission every time you visit a new website. If you are unsure, choose *Ask* to grant permissions on a per-site basis.
+Stellen Sie sicher, dass im selben Bildschirm bei *Alle Websites* die Option *Zulassen* oder *Fragen* ausgewählt ist. Wenn Sie *Zulassen* wählen, müssen Sie nicht jedes Mal, wenn Sie eine neue Website besuchen, Ihre Zustimmung geben. Wenn Sie sich nicht sicher sind, wählen Sie *Fragen*, um die Berechtigungen für jeden Website zu erteilen.
-
+
### In Safari
-To enable the AdGuard extension right from the Safari browser, tap the icon on the left side of the URL field:
+Um die AdGuard-Erweiterung direkt im Safari-Browser zu aktivieren, tippen Sie auf das Symbol auf der linken Seite des URL-Feldes:
-
+
-Then, tap *Manage Extensions*.
+Tippen Sie dann auf *Erweiterungen verwalten*.
-
+
-In the opened window, turn on the AdGuard switches. The top one is the AdGuard Web extension; the other six are content blockers needed for filtering.
+Schalten Sie im geöffneten Fenster die AdGuard-Schalter ein. Die oberste ist die AdGuard-Web-Erweiterung; die anderen sechs sind Inhaltsblocker, die für die Filterung benötigt werden.
-
+
-You should now be able to see AdGuard among the available extensions. To enable **Advanced protection**, open AdGuard extension, tap the yellow **i** icon, press *Enable*, and confirm the action.
+Sie sollten nun AdGuard unter den verfügbaren Erweiterungen sehen können. Um den **Erweiterten Schutz** zu aktivieren, öffnen Sie die AdGuard-Erweiterung, tippen Sie auf das gelbe Symbol **i**, drücken Sie *Aktivieren* und bestätigen Sie die Aktion.
:::note
-If you use AdGuard for iOS without Premium subscription, you won't be able to enable **Advanced protection**.
+Wenn Sie AdGuard für iOS ohne Premium-Abonnement verwenden, können Sie den **Erweiterten Schutz** nicht aktivieren.
:::
-Alternatively, you can enable **Advanced protection** directly from the app, in the **Protection** tab (second from the left in the bottom icon row).
+Alternativ können Sie den **Erweiterten Schutz** auch direkt in der App im Tab **Schutz** (zweite von links in der unteren Symbolleiste) aktivieren.
-AdGuard's Safari Web extension only works on iOS versions 15 and later.
+Die Safari-Web-Erweiterung von AdGuard funktioniert nur auf iOS-Versionen 15 und höher.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index 720e7197ecd..d5bd8b1bc9a 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verwendet einen lokalen DNS-Proxy für die Suche nach Konfigurationen in den ECH
Mit der Einstellung `true` erlauben Sie AdGuard, Datenverkehr zu filtern, der über HTTP/3, die neueste Version des auf QUIC-basierenden HTTP-Protokolls, gesendet wird.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
Indem Sie `true` setzen, aktivieren Sie die lokale Netzwerkfilterung.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/extensions.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/extensions.md
index 02b45047b7d..98849a3f136 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/extensions.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/extensions.md
@@ -11,7 +11,7 @@ Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbebloc
AdGuard kann die Funktionalität einer Website erheblich erweitern, indem er als [Userskript-Verwaltung](/general/extensions.md) fungiert. Sie können auch Ihre eigenen Skripte hinzufügen und bestehende Skripte verwalten.
-
+
**Benutzerskripte automatisch erkennen**
@@ -19,7 +19,7 @@ Wenn diese Option aktiviert ist, definiert AdGuard automatisch Browser-Anfragen
Die folgenden Erweiterungen werden mit AdGuard installiert:
-
+
**AdGuard-Assistent**
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 41979b6920e..e7ffe562bd8 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbebloc
AdGuard für Windows ist ein einfach zu bedienendes Tool, das lästige Banner, Pop-ups, Videoanzeigen und Tracker blockiert. Aber das ist noch nicht alles: Es hilft Ihnen, Datenverkehr zu sparen, Webseiten schneller zu laden und Ihren Computer vor unerwünschten und potenziell bösartigen Websites zu schützen. AdGuard schützt Sie auch vor Phishing-Websites und sorgt dafür, dass Ihre Kinder keinen Zugang zu ungeeigneten Inhalten haben.
-
+
Sobald Sie AdGuard für Windows starten, wird der Hauptbildschirm der App angezeigt. Das auffälligste Detail ist die Schaltfläche _Schutz aktivieren/deaktivieren_. Auf dieser Seite können Sie auch Statistiken über blockierte Werbung, Tracker und Bedrohungen einsehen, die aktuelle Version der App abrufen oder die App aktualisieren. Außerdem gibt es in der oberen rechten Ecke vier Registerkarten: _Einstellungen_, _Support_, _Lizenz_ und _Über_. Jeder dieser Punkte ist es wert, gesondert behandelt zu werden.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/network.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/network.md
index 7dc6513e81d..4a2bbb061db 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/network.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/network.md
@@ -11,7 +11,7 @@ Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbebloc
Das Modul _Netzwerk_ ist der Netzwerkfilterung gewidmet, und hier finden Sie zusätzliche netzwerkbezogene Optionen. Zwei davon sind standardmäßig aktiviert: _Datenverkehrsfilterung aktivieren_ und _HTTPS filtern_. Dies sind wichtige zusätzliche Vorsichtsmaßnahmen, um Ihren Webspace besser zu filtern. Die meisten Websites verwenden jetzt HTTPS, und dies gilt auch für die Werbung. Von vielen Websites, wie youtube.com, facebook.com und x.com, ist es unmöglich, Werbung ohne HTTPS-Filterung zu entfernen. Lassen Sie also die Funktion _HTTPS filtern_ aktiviert, es sei denn, Sie haben einen triftigen Grund, dies nicht zu tun.
-
+
In diesem Modul können Sie das Kontrollkästchen _AdGuard als HTTP-Proxy verwenden_ aktivieren, um AdGuard als regulären HTTP-Proxy zu verwenden, der den gesamten Datenverkehr filtert, der ihn durchläuft. Sie können auch die Funktion _Websites mit EV-Zertifikaten filtern_ aktivieren. Extended Validation (EV) SSL-Zertifikate bieten eine stärkere Sicherheitsgarantie; die Inhaber solcher Websites müssen ein gründliches und weltweit standardisiertes Identitätsprüfungsverfahren durchlaufen, das durch EV-Richtlinien definiert ist. Daher werden Websites mit solchen Zertifikaten vertraut und nicht gefiltert.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/others.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/others.md
index 59356df99f2..70184058979 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/others.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/others.md
@@ -5,7 +5,7 @@ sidebar_position: 5
:::info
-Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. To see how it works, [download the AdGuard app](https://agrd.io/download-kb-adblock).
+Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. Um zu sehen, wie es funktioniert, [laden Sie die AdGuard-App herunter](https://agrd.io/download-kb-adblock).
:::
@@ -15,11 +15,11 @@ Es gibt andere nützliche AdGuard-Optionen, die in diesem Artikel nicht unbemerk
-By clicking the _Support_ tab you will open a dialog box through which you can report a bug, submit a feature request, or simply share your opinion of the product.
+Wenn Sie auf den Tab _Support_ klicken, öffnet sich ein Dialogfeld, in dem Sie einen Fehler melden, eine Funktionsanfrage stellen oder einfach Ihre Meinung über das Produkt mitteilen können.
### Lizenz
-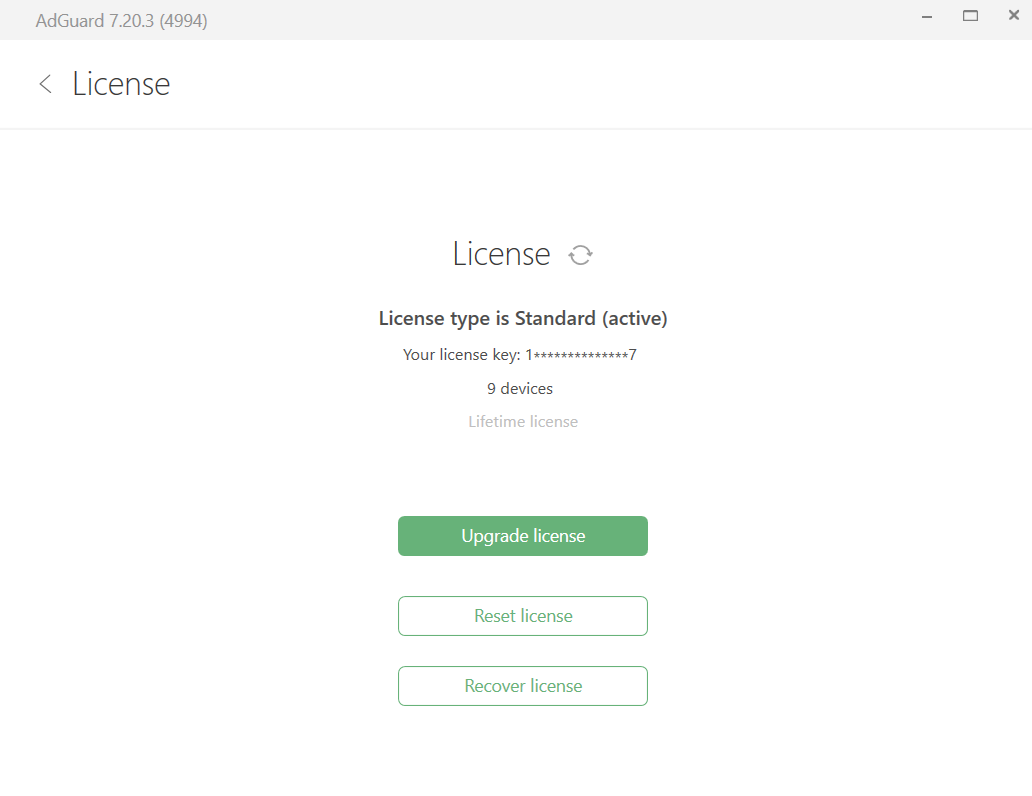
+
Auf diesem Tab finden Sie Informationen zu Ihrer Lizenz. Hier können Sie:
@@ -28,13 +28,13 @@ Auf diesem Tab finden Sie Informationen zu Ihrer Lizenz. Hier können Sie:
### Über uns
-
+! [Über die App\*border](https://cdn.adtidy.org/content/kb/ad_blocker/windows/other_features/about.png)
-In addition to information about the current version of the program, this tab provides some useful links to License agreement, Privacy policy, Acknowledgements, Discussions, and Version history pages.
+Zusätzlich zu den Informationen über die aktuelle Version des Programms bietet dieser Tab einige nützliche Links zu den Seiten Lizenzvereinbarung, Datenschutzerklärung, Danksagungen, Diskussionen und Versionsverlauf.
### Auf Aktualisierungen prüfen
-
+
Um zu prüfen, ob Filter und Benutzerskripte aktualisiert wurden, klicken Sie auf das Symbol mit den rotierenden Pfeilen in der oberen rechten Ecke des Hauptbildschirms der App.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index fffe33b1f11..445c908d870 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -5,29 +5,29 @@ sidebar_position: 2
:::info
-Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. To see how it works, [download the AdGuard app](https://agrd.io/download-kb-adblock).
+Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. Um zu sehen, wie es funktioniert, [laden Sie die AdGuard-App herunter](https://agrd.io/download-kb-adblock).
:::
_Einstellungen_ ist der Bereich, der die meiste Aufmerksamkeit erfordert. Hier können Sie die App so konfigurieren, dass sie genau Ihren Bedürfnissen entspricht: Sie blockiert nur das, was Sie stört, verwendet den DNS-Server des vertrauenswürdigen Anbieters, entfernt Cookies von Drittanbietern und so weiter.
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### Allgemeine Einstellungen
+
-Hier können Sie die Sprache und das Design (dunkel oder hell) festlegen, den Start von AdGuard beim Systemstart und automatische Aktualisierungen im Hintergrund aktivieren, den Aktualisierungskanal auswählen und die Häufigkeit der Filteraktualisierungen festlegen. Die Einstellungen sind auch der richtige Ort, wenn AdGuard für Windows nicht richtig funktioniert und das Support-Team Sie gebeten hat, _Fehlersuchprotokolle_ zu erfassen (/adguard-for-windows/solving-problems/adguard-logs.md).
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-Ganz unten auf dem Bildschirm finden Sie _Erweiterte Einstellungen_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
-### Ad blocking
+### Werbeblocker
Dies ist das Hauptmodul von AdGuard für Windows, das Werbung von den von Ihnen besuchten Websites und von den auf Ihrem Gerät installierten Apps entfernt. Um Werbung und datenschutzgefährdende Inhalte wie Banner, Pop-ups oder Tracker auszufiltern, verwendet AdGuard verschiedene Filter: Gruppen von Regeln mit einem ähnlichen Zweck, die mit einer [speziellen Syntax](/general/ad-filtering/create-own-filters) geschrieben werden. Um zu verstehen, was Filter sind und wie sie funktionieren, lesen Sie [diesen Artikel](/general/ad-filtering/how-ad-blocking-works).
-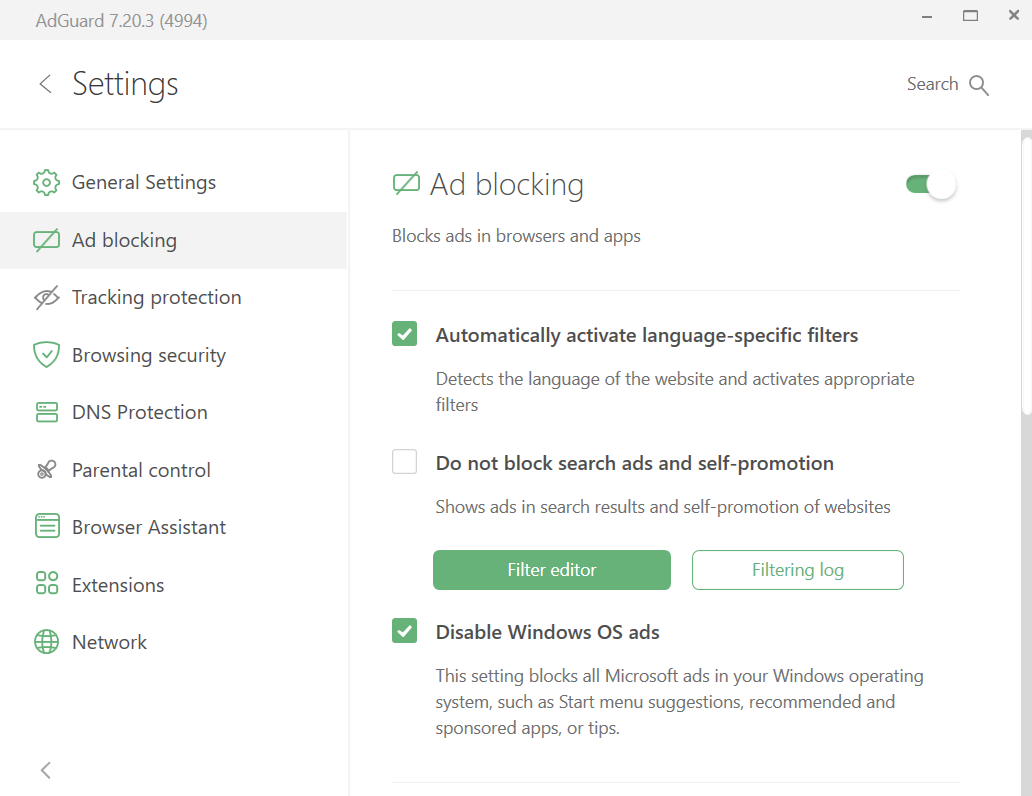
+
-In the Ad blocking module you can:
+Im Werbeblocker-Modul können Sie:
- die automatische Aktivierung von sprachspezifischen Filtern ermöglichen,
- das Sperren von [Suchanzeigen und Eigenwerbung](/general/ad-filtering/search-ads) zu deaktivieren,
@@ -40,19 +40,19 @@ In the Ad blocking module you can:
Bevor Sie mit dem manuellen Schreiben eigener Regeln beginnen, lesen Sie unsere detaillierte [Syntax-Anleitung](/general/ad-filtering/create-own-filters).
-### Tracking protection
+### Tracking-Schutz
-Viele Websites sammeln Informationen über Personen, die sie besuchen, z. B. ihre IP-Adressen, Informationen über den Browser und das installierte Betriebssystem, die Bildschirmauflösung und sogar darüber, von welcher Seite die Benutzer:innen kamen oder weitergeleitet wurden. Some web pages use cookies to mark the browser and save your personal settings, user preferences, or “recognize” you upon your next visit. _Tracking protection_ safeguards your personal information from such data and statistics gathering systems.
+Viele Websites sammeln Informationen über Personen, die sie besuchen, z. B. ihre IP-Adressen, Informationen über den Browser und das installierte Betriebssystem, die Bildschirmauflösung und sogar darüber, von welcher Seite die Benutzer:innen kamen oder weitergeleitet wurden. Einige Webseiten verwenden Cookies, um den Browser zu kennzeichnen und Ihre persönlichen Einstellungen und Vorlieben zu speichern oder Sie bei Ihrem nächsten Besuch wiederzuerkennen. _Tracking-Schutz_ schützt Ihre persönlichen Daten vor solchen Daten- und Statistikerfassungssystemen.
-
+
-Sie können die Funktionsweise dieses Moduls flexibel anpassen: Sie können z. B. verhindern, dass die Website die Suchanfrage erhält, mit der Sie sie im Internet gefunden haben, Sie können Cookies von Drittanbietern und der Website selbst automatisch löschen und Sie können die Standortfreigabe in Ihrem Browser deaktivieren, die dazu verwendet werden kann, Ihren Aufenthaltsort zu verfolgen.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-Um alles über das Modul Tracking-Schutz und seine Optionen zu erfahren, [lesen Sie diesen Artikel](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Internetsicherheit
-Internetsicherheit bietet starken Schutz vor bösartigen und Phishing-Websites. AdGuard für Windows ist natürlich kein Antivirenprogramm. It will neither stop the download of a virus when it’s already started, nor delete the already existing ones. But it will warn you if you’re about to proceed to a website whose domain has been added to our “untrusted sites” database, or to download a file from such website. Weitere Informationen über die Funktionsweise dieses Moduls finden Sie im [entsprechenden Artikel](/general/browsing-security).
+Internetsicherheit bietet starken Schutz vor bösartigen und Phishing-Websites. AdGuard für Windows ist natürlich kein Antivirenprogramm. Die App kann weder das Herunterladen eines Virus stoppen, wenn es bereits begonnen hat, noch bereits vorhandene Viren löschen. Sie werden jedoch gewarnt, wenn Sie eine Website aufrufen oder eine Datei von einer Website herunterladen, deren Domain in unserer Datenbank „Nicht vertrauenswürdige Websites“ aufgeführt ist. Weitere Informationen über die Funktionsweise dieses Moduls finden Sie im [entsprechenden Artikel](/general/browsing-security).
In diesem Modul können Sie:
@@ -60,7 +60,7 @@ In diesem Modul können Sie:
- akustische Benachrichtigungen aktivieren,
- sich bereit erklären, anonyme sicherheitsrelevante Informationen an den AdGuard-Server zu übermitteln, damit wir die Datenbank mit bösartigen und Phishing-Websites auf dem neuesten Stand halten können.
-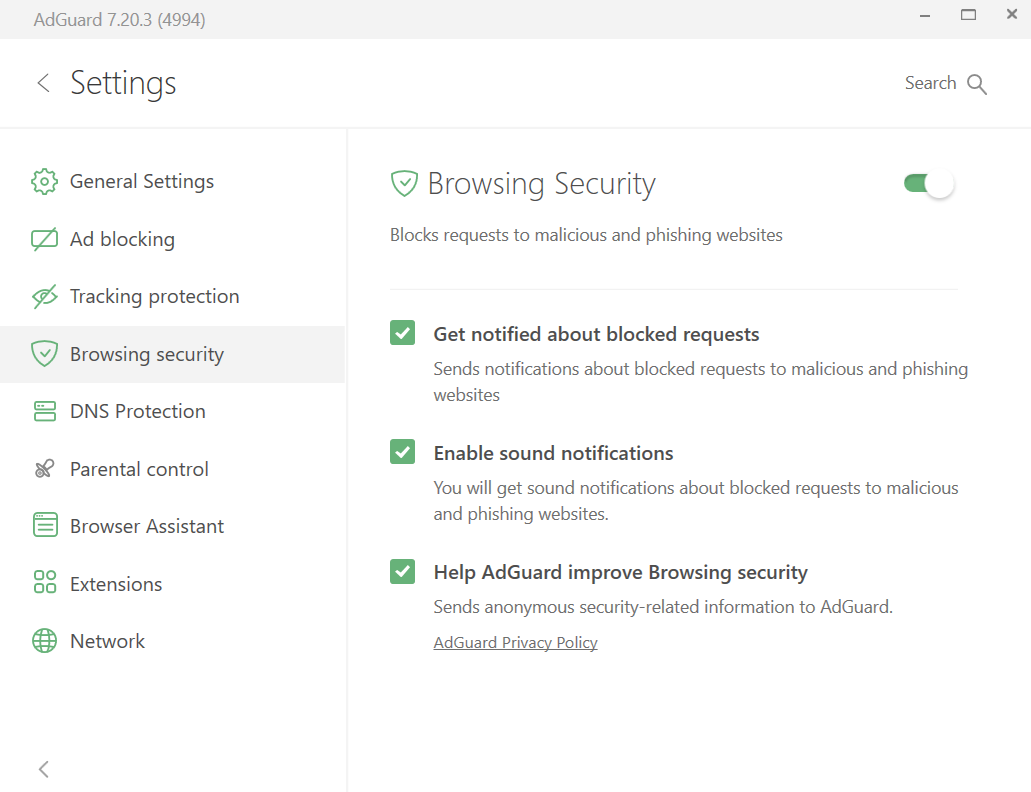
+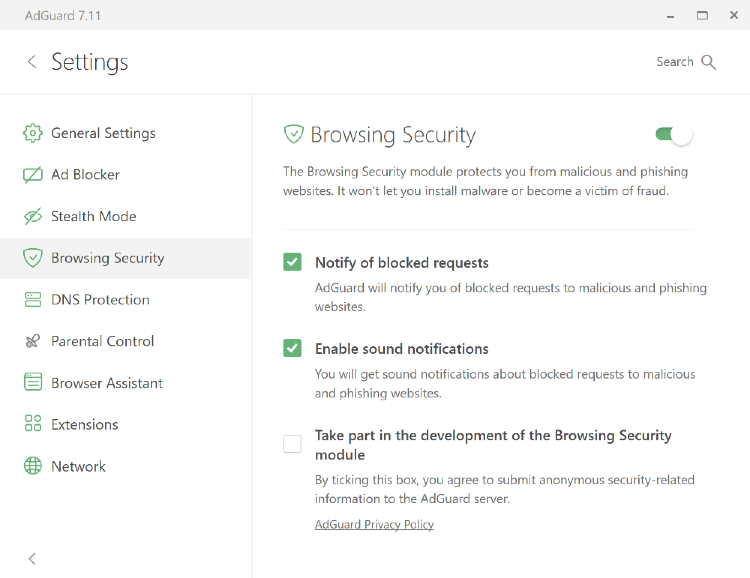
Wenn Sie mehr über Internetsicherheit erfahren möchten, lesen Sie [diesen Artikel](/general/browsing-security).
@@ -68,7 +68,7 @@ Wenn Sie mehr über Internetsicherheit erfahren möchten, lesen Sie [diesen Arti
Es gibt drei wichtige Gründe, warum Sie die DNS-Schutzeinstellungen untersuchen sollten. Erstens, um zu vermeiden, dass Ihr ISP (Internetdiensteanbieter) Sie verfolgt. Jedes Mal, wenn Sie eine Website öffnen, zum Beispiel „google.com“, sendet Ihr Browser eine Anfrage an einen DNS-Server, um die IP-Adresse der Website zu erhalten. In der Regel gehört der DNS-Server zu Ihrem Internetanbieter, der damit Ihre Online-Aktivitäten verfolgen kann. Zweitens, um Ihren DNS-Verkehr zu verschlüsseln. Und die dritte Möglichkeit ist das [Sperren von Inhalten auf DNS-Ebene](https://adguard-dns.io/kb/general/dns-filtering/).
-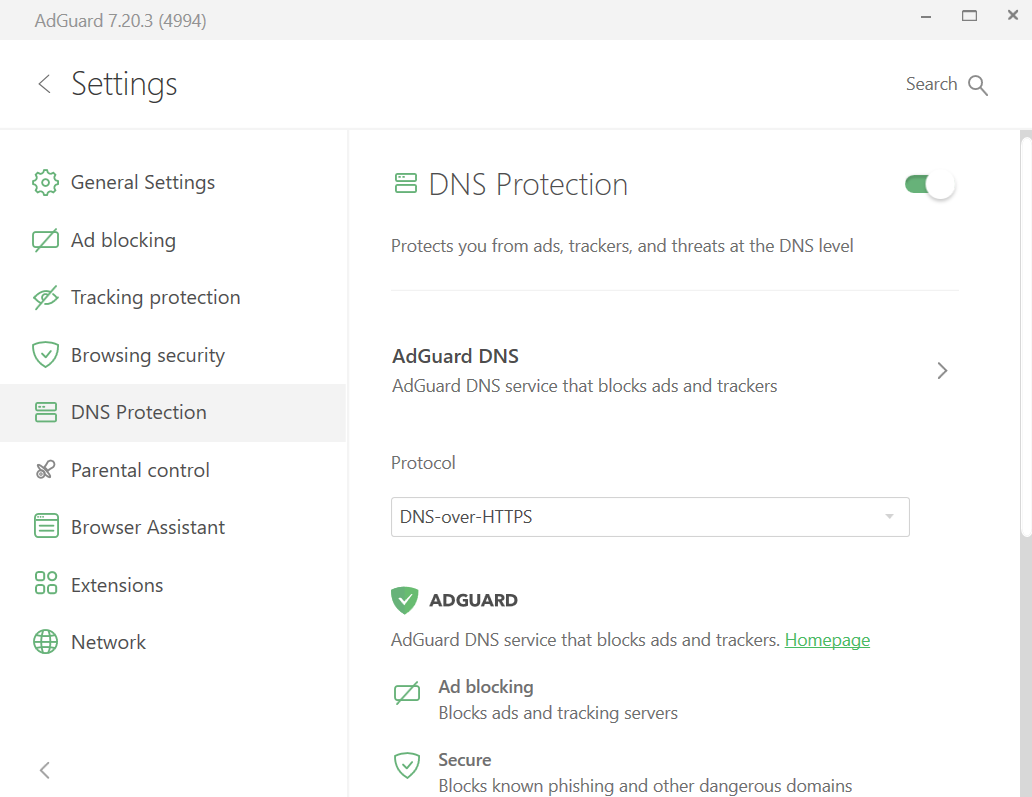
+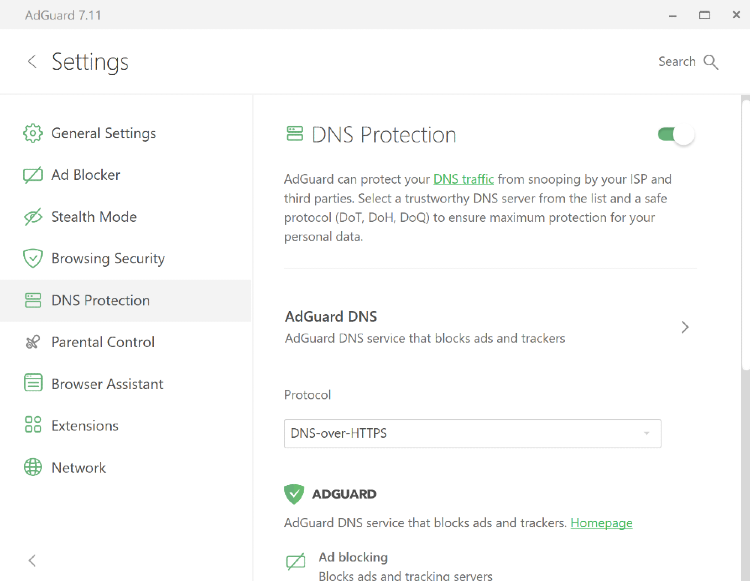
Im DNS-Schutzmodul von AdGuard für Windows können Sie DNS-Server von bekannten DNS-Anbietern auswählen, darunter AdGuard DNS, das Werbung und Tracker blockiert, AdGuard DNS Familienschutz, das auch Inhalte für Erwachsene blockiert, oder AdGuard DNS Ohne Filterung, das eine sichere und zuverlässige Verbindung bietet, aber nichts filtert. Sie können sogar benutzerdefinierte DNS-Server und -Regeln mit der [DNS-Regelsyntax](https://adguard-dns.io/kb/general/dns-filtering-syntax/) hinzufügen. Bei Bedarf können Sie [DNS-Filter Ihrer Wahl](https://filterlists.com) hinzufügen.
@@ -81,18 +81,18 @@ Ab Version 7.20 können Sie Filter auch hinzufügen, indem Sie sie einfach aus e

-### Kindersicherung
+### Parental control
-Es gibt eine Reihe von Websites, auf die der Zugriff von einem von Kindern benutzten PC aus beschränkt werden sollte. This task is accomplished by _Parental Control_.
+Es gibt eine Reihe von Websites, auf die der Zugriff von einem von Kindern benutzten PC aus beschränkt werden sollte. This task is accomplished by _Parental control_.
-
+
-Das Modul prüft den Inhalt der im Browser geöffneten Webseiten und filtert diejenigen mit für Kinder unerwünschten Inhalten: Bilder und Texte für Erwachsene, Schimpfwörter, Gewalt, Drogenpropaganda usw. Die Einstellungen der Kindersicherung sind passwortgeschützt, so dass das Kind die Einschränkungen nicht umgehen kann. Dieses Modul blockiert nicht nur die Weiterleitung auf unerwünschte Seiten, sondern kann auch die für Kinder ungeeigneten Links aus den Suchergebnissen entfernen.
+Das Modul prüft den Inhalt der im Browser geöffneten Webseiten und filtert diejenigen mit für Kinder unerwünschten Inhalten: Bilder und Texte für Erwachsene, Schimpfwörter, Gewalt, Drogenpropaganda usw. Parental control settings are password-protected so that the child is not able to go round the restrictions. Dieses Modul blockiert nicht nur die Weiterleitung auf unerwünschte Seiten, sondern kann auch die für Kinder ungeeigneten Links aus den Suchergebnissen entfernen.
-Im Modul _Kindersicherung_ können Sie die _Sichere Suche_ aktivieren und die _Sperrliste_ und die _Positivliste_ verwalten, um die Funktionsweise dieser Option anzupassen. Sie können auch das Kontrollkästchen _Herunterladen von ausführbaren Dateien sperren_ aktivieren, um zu verhindern, dass Ihr Kind Software auf den Computer herunterlädt und installiert. Im Modul _Kindersicherung_ gibt es zwei weitere Optionen: Sie können einen bestimmten Windows-Benutzer auswählen, der durch die _Kindersicherung_ geschützt werden soll, und ein Passwort festlegen, um die Einstellungen vor Änderungen zu schützen.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. Sie können auch das Kontrollkästchen _Herunterladen von ausführbaren Dateien sperren_ aktivieren, um zu verhindern, dass Ihr Kind Software auf den Computer herunterlädt und installiert. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser-Assistent
-
+
-From this tab you can easily proceed to install AdGuard Browser Assistant, which primary function is to manage filtering directly from the browser. We explained more about how to work with it and what to do if there is no Browser Assistant for your browser in the [separate article](/adguard-for-windows/browser-assistant.md).
+Von diesem Tab aus können Sie ganz einfach den AdGuard Browser-Assistenten installieren, dessen Hauptfunktion darin besteht, das Filtern direkt über den Browser zu verwalten. Wie Sie damit arbeiten und was zu tun ist, wenn es für Ihren Browser keinen Browser-Assistenten gibt, wird in einem [separaten Artikel](/adguard-for-windows/browser-assistant.md) näher erläutert.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/installation.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/installation.md
index f8c3e1d95ec..7584d90aa91 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/installation.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/installation.md
@@ -21,25 +21,25 @@ Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbebloc
## AdGuard installieren
-To install AdGuard on a Windows PC or tablet, follow these steps:
+Um AdGuard auf einem PC oder Tablet zu installieren, gehen Sie wie folgt vor:
-1. Go to the [AdGuard website](http://adguard.com) and click *Download*. You can also get the installation program from the [download page](https://adguard.com/download.html?auto=1) — the download will start automatically.
+1. Öffnen Sie die [AdGuard-Website](http://adguard.com) und klicken Sie auf *Herunterladen*. Sie können das Installationsprogramm auch von der [Download-Seite](https://adguard.com/download.html?auto=1) herunterladen. Der Download startet daraufhin automatisch.
- 
+ 
-2. Once the download is complete, open the file *adguardInstaller.exe*.
+2. Sobald der Download abgeschlossen ist, öffnen Sie die Datei *adguardInstaller.exe*.
- 
+ 
-3. You’ll see a User Account Control prompt asking if you want to allow the app to make changes to your PC. Klicken Sie auf *Ja*.
+3. Es wird das Dialogfeld der Benutzerkontensteuerung angezeigt, in dem Sie aufgefordert werden, der App zu erlauben, Änderungen an Ihrem PC vorzunehmen. Klicken Sie auf *Ja*.
-4. Choose the folder where you want AdGuard to be installed.
+4. Wählen Sie den Ordner, in dem AdGuard installiert werden soll.
- If you want to select a different location, click *Browse*, choose the folder, and click *OK*. You can also create a new folder by clicking *Make New Folder* and naming it. If you’d like a desktop shortcut, check the box *Create a desktop shortcut*. Then click *Install* to start the installation.
+ Wenn Sie einen anderen Speicherort auswählen möchten, klicken Sie auf *Durchsuchen*, wählen Sie den Ordner aus und klicken Sie auf *OK*. Sie können AdGuard auch in einem neuen Ordner installieren, indem Sie auf *Neuen Ordner erstellen* klicken und den Namen eingeben. Um eine Desktop-Verknüpfung für AdGuard zu erstellen, markieren Sie das Feld *Desktop-Verknüpfung erstellen*. Klicken Sie auf *Installieren*, um mit der Installation fortzufahren.
@@ -47,67 +47,67 @@ To install AdGuard on a Windows PC or tablet, follow these steps:
- Glückwunsch! AdGuard has been successfully installed. You’ll be prompted to set up protection according to your preferences.
+ Glückwunsch! Sie haben AdGuard erfolgreich auf Ihrem Computer installiert. Sie werden dann aufgefordert, den Schutz nach Ihren Wünschen einzurichten.
- 
+ 
- After that, the main window will open, where you can adjust the app’s settings.
+ Daraufhin öffnet sich das Hauptfenster, in dem Sie die Einstellungen der App festlegen können.
## So kann AdGuard für Windows deinstalliert werden {#uninstall}
-### Standardmodus
+### Reguläre Methode
Wenn Sie AdGuard deinstallieren oder neu installieren müssen, gehen Sie wie folgt vor:
-- For Microsoft Windows 10 & 11: Open the *Start Menu* by clicking *Start*, then select *Settings*. In the window that opens, click *Apps* → *Installed apps*. Select *AdGuard* from the list of your installed apps, click the three-dot menu, and select *Uninstall*.
+- Für Microsoft Windows 10 und 11: Öffnen Sie das *Startmenü*, indem Sie auf *Start* klicken, und wählen Sie dann *Einstellungen*. Klicken Sie im sich öffnenden Fenster auf *Apps* → *Installierte Apps*. Wählen Sie *AdGuard* aus der Liste Ihrer installierten Apps, klicken Sie auf das Drei-Punkte-Menü und wählen Sie *Deinstallieren*.
- 
+ 
-- For Microsoft Windows 8: Right-click the *empty space* in the lower left corner of the task bar and select *Control Panel*. Click *Uninstall a program* in the *Programs* section, then select *AdGuard* from the list of installed apps and press the *Uninstall* button located right above the list. Confirm the action by clicking *Uninstall AdGuard* in the window that opens.
+- Für Microsoft Windows 8: Klicken Sie mit der rechten Maustaste auf die *leere Stelle* in der unteren linken Ecke der Taskleiste und wählen Sie *Systemsteuerung*. Klicken Sie auf *Programm deinstallieren* im Bereich *Programme*, wählen Sie dann *AdGuard* aus der Liste der installierten Apps aus und klicken Sie auf die Schaltfläche *Deinstallieren*, die sich direkt über der Liste befindet. Bestätigen Sie die Aktion, indem Sie in dem sich öffnenden Fenster auf *AdGuard deinstallieren* klicken.
-- For Microsoft Windows 8.1: Right-click the *Start button* and select *Control Panel*. Click *Uninstall a program* in the *Programs* section, then select *AdGuard* from the list of installed apps and press the *Uninstall* button located right above the list. Confirm the action by clicking *Uninstall AdGuard* in the window that opens.
+- Für Microsoft Windows 8.1: Klicken Sie mit der rechten Maustaste auf die Schaltfläche *Start* und wählen Sie *Systemsteuerung*. Klicken Sie auf *Programm deinstallieren* im Bereich *Programme*, wählen Sie dann *AdGuard* aus der Liste der installierten Apps aus und klicken Sie auf die Schaltfläche *Deinstallieren*, die sich direkt über der Liste befindet. Bestätigen Sie die Aktion, indem Sie in dem sich öffnenden Fenster auf *AdGuard deinstallieren* klicken.
-- For Microsoft Windows 7: Open *Start Menu*. In the search box, type *Control Panel*. Click *Uninstall a program* in the *Programs* section, then select *AdGuard* from the list of installed apps and press the *Uninstall* button located right above the list. Confirm the action by clicking *Uninstall AdGuard* in the window that opens.
+- Für Microsoft Windows 7: Öffnen Sie das *Startmenü*. Geben Sie in das Suchfeld *Systemsteuerung* ein. Klicken Sie auf *Programm deinstallieren* im Bereich *Programme*, wählen Sie dann *AdGuard* aus der Liste der installierten Apps aus und klicken Sie auf die Schaltfläche *Deinstallieren*, die sich direkt über der Liste befindet. Bestätigen Sie die Aktion, indem Sie in dem sich öffnenden Fenster auf *AdGuard deinstallieren* klicken.
### Fortgeschrittene Methode {#advanced}
-In case regular uninstall doesn't work for any reason, you can try to use an advanced method. First of all, you need to [download the uninstaller tool](https://static.adtidy.org/windows/uninstaller/uninstal_utility.zip) created by our developers. Extract the archive to any folder on your PC and run the **Adguard.UninstallUtility.exe** file, and allow the app to make changes to your device. Then follow the instruction below:
+Falls die reguläre Deinstallation aus irgendeinem Grund nicht funktioniert, können Sie versuchen, eine erweiterte Methode zu verwenden. Zuerst müssen Sie [das von unseren Entwicklern erstellte Deinstallationstool](https://static.adtidy.org/windows/uninstaller/uninstal_utility.zip) herunterladen. Entpacken Sie das Archiv in einen beliebigen Ordner auf Ihrem PC, führen Sie die Datei **Adguard.UninstallUtility.exe** aus und erlauben Sie der App, Änderungen an Ihrem Gerät vorzunehmen. Befolgen Sie anschließend die nachstehenden Anweisungen:
-- Select *AdGuard Ad Blocker* and *Standard* uninstall type, then click *Uninstall*.
+- Wählen Sie *AdGuard Werbeblocker* und *Standard-Deinstallationstyp* und klicken Sie dann auf *Deinstallieren*.
- 
+ 
-- Click *OK* once the warning window pops up:
+- Klicken Sie auf *OK*, sobald das Warnfenster angezeigt wird:
- 
+ 
-- Wait until uninstall is finished — there will be a phrase **Uninstall complete** and a prompt to restart your computer:
+- Warten Sie, bis die Deinstallation abgeschlossen ist — es wird die Meldung **Deinstallation abgeschlossen** und eine Aufforderung zum Neustart des Computers angezeigt:
- 
+ 
:::caution
-Follow the next steps only if performing the first two steps wasn’t enough for some reason. We strongly suggest contacting our support before using steps 3-4 of advanced uninstall instruction.
+Führen Sie die nächsten Schritte nur aus, wenn die ersten beiden Schritte aus irgendeinem Grund nicht ausreichend waren. Wir empfehlen dringend, unseren Support zu kontaktieren, bevor Sie die Schritte 3-4 der erweiterten Deinstallationsanweisung ausführen.
:::
-- Select *AdGuard Ad Blocker* and *Extended* uninstall type, then click *Uninstall*. Click *Yes, continue* in the window prompt.
+- Wählen Sie *AdGuard Werbeblocker* und *Erweitert* als Deinstallationstyp und klicken Sie dann auf *Deinstallieren*. Klicken Sie in der Eingabeaufforderung auf *Ja, weiter*.
- 
+ 
-- Click *OK* once the warning window pops up:
+- Klicken Sie auf *OK*, sobald das Warnfenster angezeigt wird:
- 
+ 
-- Wait until uninstall is finished — there will be a phrase **Uninstall complete** and a prompt to restart your computer:
+- Warten Sie, bis die Deinstallation abgeschlossen ist — es wird die Meldung **Deinstallation abgeschlossen** und eine Aufforderung zum Neustart des Computers angezeigt:
- 
+ 
-AdGuard is successfully uninstalled!
+AdGuard wurde erfolgreich deinstalliert!
#### Deinstallationsprogramm im Konsolenmodus ausführen
-Besides running the advanced uninstaller in its user-interactive mode, you can also use command-line arguments to uninstall AdGuard for Windows. To do this, follow the instructions below:
+Neben der Ausführung des erweiterten Deinstallationsprogramms im benutzerinteraktiven Modus können Sie auch Befehlszeilenargumente verwenden, um AdGuard für Windows zu deinstallieren. Folgen Sie dazu den nachstehenden Anweisungen:
1. Öffnen Sie die Eingabeaufforderung durch Eingabe von *cmd* im Startmenü.
2. Verwenden Sie `/console`, um das Deinstallationsprogramm im Konsolenmodus auszuführen, ohne die interaktive Benutzeroberfläche. Alle nachstehenden Befehlszeilenparameter werden ignoriert, wenn der Modus `/console` nicht aktiviert ist.
@@ -119,6 +119,6 @@ Besides running the advanced uninstaller in its user-interactive mode, you can a
:::note
-The use of the parameters `/console` and `/adblocker` is necessary for a successful uninstall. The parameters `/advanced` and `/settings` are optional.
+Die Verwendung der Parameter `/console` und `/adblocker` ist für eine erfolgreiche Deinstallation notwendig. Die Parameter `/advanced` und `/settings` sind optional.
:::
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/connection-not-trusted.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/connection-not-trusted.md
index 162a4cf453c..fe9373b94f0 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/connection-not-trusted.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/connection-not-trusted.md
@@ -13,11 +13,11 @@ Um den HTTPS-Verkehr zu filtern und Werbung und Tracker effizient zu blockieren,
Normalerweise vertrauen Browser dem AdGuard-Zertifikat, sobald es während des Installationsvorgangs zum Zertifikatspeicher des Systems hinzugefügt wurde. In manchen Fällen reicht dies jedoch nicht aus, und Sie können auf Warnungen oder Fehler stoßen. Dies geschieht am häufigsten in Firefox-basierten Browsern wie Mozilla Firefox, PaleMoon, Waterfox usw. oder in Yandex.Browser.
-Here are some common issues:
+Hier einige häufig auftretende Probleme:
- [Fehler *Potenzielles Sicherheitsrisiko* in Firefox-basierten Browsern](#potential-security-risk-error-in-firefox-based-browsers)
- [Yandex.Browser-Zertifikat-Warnung](#yandexbrowser-certificate-warning)
-- [Non-official add-ons don’t update in Firefox-based browsers](#non-official-add-ons-dont-update-in-firefox-based-browsers)
+- [Nicht-offizielle Add-ons lassen sich in Firefox-basierten Browsern nicht aktualisieren](#non-official-add-ons-dont-update-in-firefox-based-browsers)
## Fehler *Potenzielles Sicherheitsrisiko* in Firefox-basierten Browsern
@@ -84,14 +84,14 @@ Am einfachsten ist es, wenn Sie auf die Schaltfläche **Website öffnen** klicke
Das Deaktivieren der HTTPS-Filterung im AdGuard verhindert auch, dass Yandex.Browser diese Meldung erneut anzeigt, aber sie hat einen hohen Preis: Jeder Werbung, die über HTTPS geladen werden (einschließlich **Yandex-eigener Anzeigen**), werden angezeigt — auf Websites wie YouTube, Facebook, Instagram und vielen anderen. Wir raten dringend davon ab, wenn Sie die Qualität der Werbeblockierung hoch halten möchten.
-## Non-official add-ons don’t update in Firefox-based browsers
+## Nicht-offizielle Add-ons lassen sich in Firefox-basierten Browsern nicht aktualisieren
-If you use Firefox-based browsers and have add-ons that aren’t from Mozilla’s official catalog — and HTTPS filtering is enabled in AdGuard — those add-ons won’t be able to update. Here’s why.
+Wenn Sie Firefox-basierte Browser verwenden und Add-ons nutzen, die nicht aus Mozillas offiziellem Katalog stammen — und die HTTPS-Filterung in AdGuard aktiviert ist — können diese Add-ons nicht aktualisiert werden. Hier ist der Grund dafür.
-To update add-ons, Firefox checks whether the connection to the update server is secured with a certificate issued by a trusted certificate authority (CA). Firefox-based browsers only trust certificates from CAs included in Mozilla’s built-in list — it’s a security measure to block potentially unsafe updates.
+Um Add-ons zu aktualisieren, prüft Firefox, ob die Verbindung zum Update-Server durch ein Zertifikat gesichert ist, das von einer vertrauenswürdigen Zertifizierungsstelle (CA) ausgestellt wurde. Firefox-basierte Browser vertrauen nur Zertifikaten von Zertifizierungsstellen, die in Mozillas integrierter Liste enthalten sind — eine Sicherheitsmaßnahme, um potenziell unsichere Aktualisierungen zu verhindern.
-AdGuard’s certificate, although secure, isn’t on that list. That is why Mozilla domains are excluded from HTTPS filtering in AdGuard.
+Das Zertifikat von AdGuard ist zwar sicher, ist aber nicht in dieser Liste enthalten. Aus diesem Grund sind Mozilla-Domains von der HTTPS-Filterung im AdGuard ausgeschlossen.
-However, non-official add-ons use third-party servers for updates, and those are not excluded from HTTPS filtering by default. So when Firefox checks the connection, it sees AdGuard’s certificate instead of the original one — and blocks the update.
+Nicht-offizielle Add-ons verwenden jedoch Server von Drittanbietern für Updates, und diese sind nicht standardmäßig von der HTTPS-Filterung ausgeschlossen. Sobald Firefox die Verbindung überprüft, wird er erkennt, dass das AdGuard-Zertifikat anstelle des Originalzertifikats verwendet wird und unterbindet das Update.
-If you need to check for updates for such add-ons, consider temporarily disabling AdGuard.
+Wenn Sie Updates für solche Add-ons benötigen, sollten Sie AdGuard vorübergehend deaktivieren.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/dump-file.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/dump-file.md
index abca7b3af8e..fbebfb37846 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/dump-file.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/dump-file.md
@@ -5,57 +5,57 @@ sidebar_position: 8
:::info
-Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. To see how it works, [download the AdGuard app](https://agrd.io/download-kb-adblock).
+Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. Um zu sehen, wie es funktioniert, laden Sie [die AdGuard-App](https://agrd.io/download-kb-adblock)herunter.
:::
:::note
-Data and files provided in dump files are processed in accordance with [the AdGuard Privacy Policy](https://adguard.com/en/privacy.html).
+In Dump-Dateien bereitgestellte Daten und Dateien werden gemäß [der Datenschutzerklärung von AdGuard](https://adguard.com/en/privacy.html)verarbeitet.
:::
-If you experience an issue while using AdGuard, the support team may ask you to provide a dump file. This file helps developers see what processes were running in the app at the time and identify the cause of the problem.
+Wenn bei der Verwendung von AdGuard ein Problem auftritt, kann das Support-Team Sie bitten, eine Dump-Datei zur Verfügung zu stellen. Mithilfe dieser Datei können Entwickler erkennen, welche Prozesse zu diesem Zeitpunkt in der App ausgeführt wurden, und die Ursache des Problems ermitteln.
-Follow these steps to create a dump file:
+Führen Sie die folgenden Schritte aus, um eine Dump-Datei zu erstellen:
-1. Press *Ctrl + Shift + Esc* to open *Task Manager*.
+1. Drücken Sie *Strg + Umschalt + Esc*, um den *Task-Manager* zu öffnen.
-1. In the left sidebar, click *Details*. 
-1. Right-click the process you want to create a dump file for. In the drop-down menu, click *Create memory dump file*. 
-1. Once the dump file is created, you’ll be prompted to open the folder where it’s saved. If not, you can find it in the **%tmp%** folder. 
+1. Klicken Sie in der linken Seitenleiste auf *Details*. 
+1. Klicken Sie mit der rechten Maustaste auf den Prozess, für den Sie eine Dump-Datei erstellen möchten. Klicken Sie im Auswahlmenü auf *Speicherabbilddatei erstellen*. 
+1. Sobald die Dump-Datei erstellt ist, werden Sie aufgefordert, den Ordner zu öffnen, in dem sie gespeichert ist. Wenn nicht, finden Sie sie im Ordner **%tmp%**. 
-The created dump file (`.DMP`) will have the same name as the process you selected.
+Die erstellte Dump-Datei (`.DMP`) hat denselben Namen wie der von Ihnen ausgewählte Prozess.
:::note
-AdGuard for Windows runs two processes: `Adguard.exe` and `AdguardSvc.exe`. You’ll need to create a separate dump file for each one.
+AdGuard für Windows führt zwei Prozesse aus: `Adguard.exe` und `AdguardSvc.exe`. Sie müssen für jeden eine eigene Dump-Datei erstellen.
:::
-
+
-Since dump files can be large, please compress them into an archive before sending them to support. Also, include the AdGuard logs to help us diagnose the issue more effectively. [Instructions for collecting logs](../adguard-logs).
+Da Dump-Dateien groß sein können, komprimieren Sie sie bitte in einem Archiv, bevor Sie sie an den Support senden. Fügen Sie außerdem die AdGuard-Protokolle bei, damit wir das Problem effektiver diagnostizieren können. [Anweisungen zum Erfassen von Protokollen](../adguard-logs).
-## Collecting `wfpdiag.cab` file
+## Erfassen der Datei `wfpdiag.cab`
-Our support team may request a wfpdiag.cab file, along with a minidump file, to analyze system logs more thoroughly and diagnose issues. To collect the file, please follow these steps:
+Unser Support-Team kann eine wfpdiag.cab-Datei zusammen mit einer Minidump-Datei anfordern, um die Systemprotokolle genauer analysieren und Probleme diagnostizieren zu können. Um die Datei zu erfassen, gehen Sie bitte wie folgt vor:
1. Aktivieren Sie den AdGuard-Schutz.
-1. Click *Start* and type `cmd` to open Command Prompt
+1. Klicken Sie auf *Start* und geben Sie den Befehl `cmd` ein, um die Eingabeaufforderung zu öffnen
-1. Right-click Command Prompt and choose *Run as administrator*
+1. Klicken Sie mit der rechten Maustaste auf Eingabeaufforderung und wählen Sie *Als Administrator ausführen*
:::note
- A wfpdiag.cab file is created in your current directory. You can change the location by typing `cd `.
+ Es wird eine Datei „wfpdiag.cab“ in Ihrem aktuellen Verzeichnis erstellt. Sie können den Speicherort ändern, indem Sie `cd ` eingeben.
:::
-1. To start logging, enter the following command: `netsh wfp capture start`
+1. Um die Protokollierung zu starten, geben Sie den folgenden Befehl ein: `netsh wfp capture start`
-1. Visit any website to route traffic through AdGuard and log the filtering process
+1. Besuchen Sie eine beliebige Website, um den Datenverkehr durch AdGuard zu leiten und den Filterungsprozess zu protokollieren
-1. To stop logging, enter `netsh wfp capture stop`
+1. Um die Protokollierung zu beenden, geben Sie `netsh wfp capture stop` ein
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/exporting-settings.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/exporting-settings.md
index 06a05187a0c..1a0adcdda50 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/exporting-settings.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/exporting-settings.md
@@ -11,14 +11,14 @@ Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbebloc
Die Änderungen in AdGuard für Windows v8.0 sind umfangreich, und wir hoffen, dass Ihnen die neue Version gefällt. Allerdings besteht die Möglichkeit, dass etwas nicht so läuft, wie Sie es erwartet haben. Version 8.0 ist ganz anders, schließlich ist sie nur die erste „Nightly“-Version. Wenn Ihnen die Benutzeroberfläche von Version 8.0 nicht gefällt oder es zu viele Probleme mit Funktionen oder Stabilität gibt, können Sie die vorherige Version mit den alten Einstellungen wiederherstellen.
-To ensure your settings are preserved during the whole process, it’s recommended to export them before upgrading to v8.0. If needed, you can then reinstall the version 7 and import back your saved settings.
+Um sicherzustellen, dass Ihre Einstellungen während des gesamten Prozesses erhalten bleiben, empfiehlt es sich, sie vor dem Wechsel zu v8.0 zu exportieren. Wenn gewünscht, können Sie dann die Version 7 neu installieren und Ihre gespeicherten Einstellungen wieder importieren.
Alternativ steht auch die folgende Methode zur Verfügung:
1. Öffnen Sie nach dem Umstieg auf Version 8 den Ordner `C:\ProgramData\Adguard\Backups` und suchen Sie eine ZIP-Datei mit einem Namen ähnlich `adguard_settings_7.21.5008.0-08-04-2025-13_42_15.276.zip`.
-2. Copy this ZIP file somewhere outside of `C:\ProgramData\Adguard`, for example, to the desktop. This is important because it will be deleted in the next step.
+2. Kopieren Sie diese ZIP-Datei irgendwo außerhalb von `C:\ProgramData\Adguard`, zum Beispiel auf den Desktop. Dies ist wichtig, da sie im nächsten Schritt gelöscht wird.
3. Deinstallieren Sie Version 8.0 mit der Option **Einstellungen entfernen**.
-4. Install the previous build. You can find the download link in the _Assets_ section [on GitHub](https://github.com/AdguardTeam/AdguardForWindows/releases/tag/v7.21.0-rc-2).
+4. Installieren Sie die vorherige Version. Sie finden den Download-Link im Abschnitt _Assets_ [auf GitHub](https://github.com/AdguardTeam/AdguardForWindows/releases/tag/v7.21.0-rc-2).
5. Beenden Sie Version 7 über die Taskleiste, um das Filtern zu beenden.
6. Entpacken Sie den Inhalt der ZIP-Datei aus dem ersten Schritt und ersetzen Sie folgende Dateien:
- `adguard.db` → `C:\ProgramData\Adguard`
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/known-issues.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/known-issues.md
index 933abcc6234..d4e92ad67fe 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/known-issues.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/known-issues.md
@@ -1,6 +1,6 @@
---
title: Bekannte Probleme von AdGuard für Windows
-sidebar_position: 12
+sidebar_position: 11
---
:::info
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 164147a4252..22c0ed66273 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Aktivieren Sie diese Funktion, wenn Sie möchten, dass AdGuard automatisch Filte
Ist diese Option aktiviert, filtert AdGuard zusätzlich zu den anderen Anfragetypen auch Anfragen, die über HTTP/3 gesendet werden.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Umleitungstreiber-Modus verwenden
Wenn diese Option aktiviert ist, fängt AdGuard den gesamten Datenverkehr ab und leitet ihn zur weiteren Filterung an den lokalen Proxy-Server weiter.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/minidump.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/minidump.md
index 41e10077954..e10ac044ddf 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/minidump.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/minidump.md
@@ -1,74 +1,74 @@
---
-title: How to collect BSOD minidump
+title: So sammeln Sie einen BSOD-Minidump
sidebar_position: 9
---
:::info
-Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. To see how it works, [download the AdGuard app](https://agrd.io/download-kb-adblock).
+Dieser Artikel behandelt AdGuard für Windows, einem multifunktionalen Werbeblocker, der Ihr Gerät auf Systemebene schützt. Um zu sehen, wie es funktioniert, [laden Sie die AdGuard-App herunter](https://agrd.io/download-kb-adblock).
:::
:::note
-Data and files provided in minidump files are processed in accordance with [the AdGuard Privacy Policy](https://adguard.com/en/privacy.html).
+Daten und Dateien, die in Minidump-Dateien bereitgestellt werden, werden in Übereinstimmung mit [der AdGuard-Datenschutzerklärung](https://adguard.com/en/privacy.html) verarbeitet.
:::
-Blue Screen of Death (BSOD) errors may occasionally occur while using AdGuard. When this happens, our support team may request a minidump file to help diagnose the issue. These files contain technical crash data that helps us identify and resolve the problem.
+Bei der Verwendung von AdGuard können gelegentlich „Blue Screen of Death“-Fehler (BSOD) auftreten. In diesem Fall kann unser Support-Team eine Minidump-Datei anfordern, um bei der Diagnose des Problems zu unterstützen. Diese Dateien enthalten technische Absturzdaten, die uns helfen, das Problem zu identifizieren und beheben zu können.
-## Checking for the existing minidump
+## Prüfung auf vorhandenen Minidump
-To collect minidump files, you’ll need administrator access on your computer. By default, Windows stores these files in the `C:\Windows\Minidump\` folder. The files you’re looking for will be named either `MEMORY.DMP` or follow the pattern `Mini(ddmmmyy-xxx).dmp` where the letters and numbers represent dates and sequence numbers.
+Um Minidump-Dateien sammeln zu können, werden Administratorrechte auf Ihrem Computer benötigt. Windows speichert diese Dateien standardmäßig im Ordner `C:\Windows\Minidump\`. Die Dateien, nach denen Sie suchen, tragen entweder den Namen `MEMORY.DMP` oder folgen dem Muster `Mini(ddmmmyy-xxx).dmp`, wobei die Buchstaben und Zahlen für das Datum und die laufende Nummer stehen.
-
+
-If you can’t find these files, your system may not be configured to create minidumps automatically.
+Wenn Sie diese Dateien nicht finden können, ist Ihr System möglicherweise nicht für das automatische Erstellen von Minidumps konfiguriert.
-## Configure minidump settings
+## Minidump-Einstellungen konfigurieren
-If minidumps are not created automatically, follow these steps to enable _Small Memory Dump_:
+Wenn Minidumps nicht automatisch erstellt werden, gehen Sie wie folgt vor, um _Small Memory Dump_ zu aktivieren:
-1. Press the _Windows key + R_ to open the _Run_ dialog.
+1. Drücken Sie gleichzeitig die _Windows-Taste + R_, um das Dialogfeld _Ausführen_ zu öffnen.
-2. Type `sysdm.cpl` and click _Enter_. This will open the _System properties_ window.
+2. Geben Sie `sysdm.cpl` ein und klicken Sie auf _OK_. Dadurch wird das Fenster _Systemeigenschaften_ geöffnet.
- 
+ 
-3. Navigate to _Advanced_ tab → _Startup and Recovery_ → _Settings_.
+3. Wechseln Sie zum Tab _Erweitert_ → _Start und Wiederherstellung_ → _Einstellungen_.
- 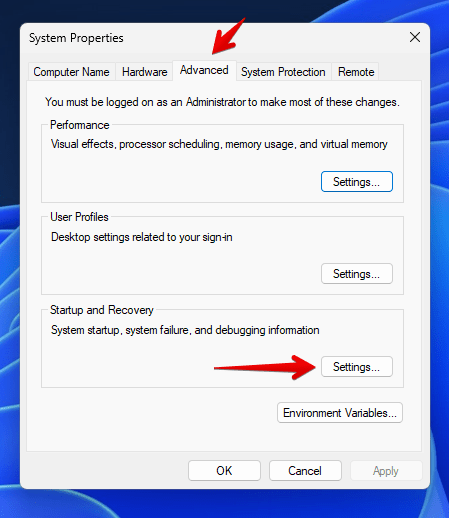
+ 
-4. Here you’ll find an option called _Write debugging information_. Make sure it’s set to _Small Memory Dump (256 KB)_ and that the path shows `%SystemRoot%\Minidump`. These settings will ensure that Windows creates the minidump files we need when a BSOD occurs.
+4. Hier finden Sie eine Option namens _Debuginformationen speichern_. Stellen Sie sicher, dass er auf _Small Memory Dump (256 KB)_ festgelegt ist und dass der Pfad `%SystemRoot%\Minidump` lautet. Diese Einstellungen stellen sicher, dass Windows die Minidump-Dateien erstellt, die wir benötigen, wenn ein BSOD auftritt.
- 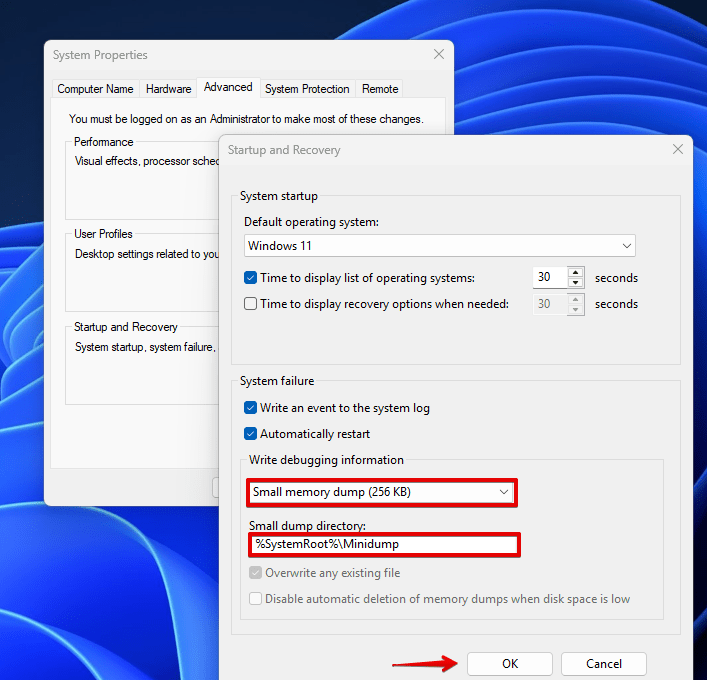
+ 
-5. Click _OK_ to save changes.
+5. Klicken Sie auf _OK_, um die Änderungen zu speichern.
-## After a crash occurs
+## Nach einem Absturz
-After experiencing a BSOD and restarting your computer, you can find the generated minidump files in the `C:\Windows\Minidump\` folder. Sorting the files by date modified makes it easy to find the most recent one corresponding to your crash.
+Nachdem ein BSOD aufgetreten ist und Sie Ihren Computer neu gestartet haben, finden Sie die erzeugten Minidump-Dateien im Ordner `C:\Windows\Minidump\`. Durch Sortieren der Dateien nach Änderungsdatum können Sie leicht die aktuellste Datei finden, die Ihrem Absturz entspricht.
-If you configured minidump settings after the crash occurred, you'll need to reproduce the issue to generate a new minidump file.
+Wenn Sie die Minidump-Einstellungen nach dem Auftreten des Absturzes konfiguriert haben, müssen Sie das Problem reproduzieren, um eine neue Minidump-Datei zu erstellen.
-## Collecting `wfpdiag.cab` file
+## Erfassen der Datei `wfpdiag.cab`
-Our support team may request a wfpdiag.cab file, along with a minidump file, to analyze system logs more thoroughly and diagnose issues. To collect the file, please follow these steps:
+Unser Support-Team kann eine wfpdiag.cab-Datei zusammen mit einer Minidump-Datei anfordern, um die Systemprotokolle genauer analysieren und Probleme diagnostizieren zu können. Um die Datei zu erfassen, gehen Sie bitte wie folgt vor:
1. Aktivieren Sie den AdGuard-Schutz.
-2. Click _Start_ and type `cmd` to open _Command Prompt_.
+2. Klicken Sie auf _Start_ und geben Sie `cmd` ein, um die _Eingabeaufforderung_ zu öffnen.
-3. Right-click _Command Prompt_ and choose _Run as administrator_.
+3. Klicken Sie mit der rechten Maustaste auf _Eingabeaufforderung_ und wählen Sie _Als Administrator ausführen_.
:::note
- A wfpdiag.cab file is created in your current directory. You can change the location by typing `cd `.
+ Es wird eine Datei „wfpdiag.cab“ in Ihrem aktuellen Verzeichnis erstellt. Sie können den Speicherort ändern, indem Sie `cd ` eingeben.
:::
-4. To start logging, enter the following command: `netsh wfp capture start`.
+4. Um die Protokollierung zu starten, geben Sie den folgenden Befehl ein: `netsh wfp capture start`.
-5. Visit any website to route traffic through AdGuard and log the filtering process.
+5. Besuchen Sie eine beliebige Website, um den Datenverkehr durch AdGuard zu leiten und den Filterungsprozess zu protokollieren.
-6. To stop logging, enter `netsh wfp capture stop`.
+6. Um die Protokollierung zu beenden, geben Sie `netsh wfp capture stop` ein.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 1290d377f0a..8c4384841db 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ In diesem Artikel geht es um die Filter, die wir für AdGuard und andere Werbebl
- **Experimenteller Filter** dient dazu, einige neue Filterregeln zu testen, die möglicherweise Konflikte verursachen und die Funktionalität von Websites beeinträchtigen können. Wenn diese Regeln ohne Probleme funktionieren, werden sie zu den Hauptfiltern hinzugefügt. [Regeln anzeigen](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Filter gegen mobile Werbung** sperrt Werbung auf mobilen Geräten. Enthält alle bekannten mobilen Werbenetzwerke. [Regeln anzeigen](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS-Filter** — setzt sich aus mehreren anderen Filtern zusammen (AdGuard Basisfilter, Social-Media-Filter, Spyware Filter, Filter gegen mobile Werbung, EasyList und EasyPrivacy) und wurde speziell vereinfacht, um besser mit dem Sperren von Werbung auf DNS-Ebene kompatibel zu sein. Dieser Filter wird von [AdGuard DNS](https://adguard-dns.io/kb)-Servern verwendet, um Werbung und Tracking zu sperren. [Regeln anzeigen](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes-Filter** wird verwendet, um schnell kritische Probleme bei der Filterung von Inhalten auf beliebten Websites zu beheben, ohne die MV3-Erweiterung zu aktualisieren. [Regeln anzeigen](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard-Filterrichtlinie
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 3627ae2888d..e4fa699bcee 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ Mit diesem Modifikator können Sie die Regelabdeckung auf eine bestimmte Anwendu
Für Mac können Sie die Bundle-ID oder den Prozessnamen der Anwendung herausfinden, indem Sie die entsprechenden Anfragedetails im Filterprotokoll anzeigen.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Beispiele**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Einschränkungen
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Regeln mit einem solchen Modifikator gelten als ungültig.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rege
- Nur AdGuard für Windows, Mac und Android ist technisch in der Lage, Regeln mit dem Modifikator `$app` zu verwenden.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,42 +557,27 @@ Wenn Sie möchten, dass die Regel nicht auf bestimmte Domains angewendet wird, b
**`$domain`-Modifikator, der der Zieldomain entspricht:**
-In einigen Fällen kann der Modifikator `$domain` nicht nur mit der Referrer-Domain, sondern auch mit der Zieldomain übereinstimmen. Dies ist der Fall, wenn alle folgenden Bedingungen erfüllt sind:
-
-1. Die Anfrage hat den Inhaltstyp `document`
-1. Das Regelmuster stimmt mit keiner bestimmten Domain überein
-1. Das Regelmuster enthält keine regulären Ausdrücke
-1. Der Modifikator `$domain` enthält nur ausgeschlossene Domains, z. B. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 UND ((2 UND 3) ODER 4)
-```
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
-
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. Dies betrifft auch Regeln mit den Modifikatoren [`$cookie`](#cookie-modifier) und [`$csp`](#csp-modifier).
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Beispiele**
- `*$cookie,domain=example.org|example.com` blockiert Cookies für alle Anfragen an und von `example.org` und `example.com`.
-- `*$document,domain=example.org|example.com` blockiert alle Anfragen an und von `example.org` und `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
-In den folgenden Beispielen wird davon ausgegangen, dass die Anfragen von `http://example.org/page` (dem Referrer) gesendet werden und die Ziel-URL `http://targetdomain.com/page` lautet.
+In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `Seite$domain=targetdomain.com|~example.org` wird nicht abgeglichen, da die Referrer-Domain explizit ausgeschlossen ist.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### Einschränkungen des Modifikators `$domain` {#domain-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
In [AdGuard for Chrome MV3][ext-mv3], `regexp` and `any_tld_domain` entries are not supported.
@@ -694,12 +707,12 @@ AdGuard will try to close the browser tab with any address that matches a blocki
##### `$popup` modifier limitations {#popup-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
-1. Der Modifikator `$popup` funktioniert am besten in der AdGuard Browsererweiterung für Chromium-basierte Browser und Firefox.
+1. The `$popup` modifier works best in AdGuard Browser Extension for Chromium-based browsers and Firefox.
1. In [AdGuard for Chrome MV3][ext-mv3] rules with the [`$popup`][popup-in-mv3] modifier would not work, so we disable converting them to declarative rules. We will try to use them only in our [TSUrlFilter][] engine and close new tabs programmatically.
-1. In AdGuard für iOS und AdGuard für Safari blockieren `$popup`-Regeln die Seite einfach sofort.
-1. In AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux, the `$popup` modifier may not detect a popup in some cases and it will not be blocked. The `$popup` modifier applies the `document` content type with a special flag which is passed to a blocking page. Die blockierende Seite selbst kann einige Prüfungen durchführen und das Fenster schließen, wenn es sich wirklich um ein Pop-up-Fenster handelt. Andernfalls sollte die Seite geladen werden. It can be combined with other request type modifiers, such as `$third-party`, `$strict-third-party`, `$strict-first-party`, and `$important`.
+1. In AdGuard for iOS and AdGuard for Safari, `$popup` rules simply block the page right away.
+1. In AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux, the `$popup` modifier may not detect a popup in some cases and it will not be blocked. The `$popup` modifier applies the `document` content type with a special flag which is passed to a blocking page. Blocking page itself can do some checks and close the window if it is really a popup. Otherwise, page should be loaded. It can be combined with other request type modifiers, such as `$third-party`, `$strict-third-party`, `$strict-first-party`, and `$important`.
:::
@@ -757,7 +770,7 @@ A restriction on third-party and custom requests. A third-party request is a req
To be considered as such, a third-party request should meet one of the following conditions:
-1. Sein Referrer ist keine Subdomain der Zieldomain oder umgekehrt. Beispielsweise ist eine Anfrage an `subdomain.example.org` von `example.org` eine Anfrage eines Drittanbieters
+1. Its referrer is not a subdomain of the target domain or vice versa. For example, a request to `subdomain.example.org` from `example.org` is not a third-party request
1. Its `Sec-Fetch-Site` header is set to `cross-site`
:::
@@ -901,7 +914,7 @@ The rule corresponds to requests caused by either `navigator.sendBeacon()` or th
##### `$ping` modifier limitations {#ping-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
AdGuard for Windows, Mac, and Android often cannot accurately detect `navigator.sendBeacon()`. Using `$ping` is not recommended in the filter lists that are supposed to be used by CoreLibs-based AdGuard products.
@@ -944,7 +957,7 @@ You may use a shorter name (alias) instead of using the full modifier name: `$fr
##### `$subdocument` modifier limitations {#subdocument-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
In AdGuard for Windows, Mac, and Android subdocuments are being detected by the [Sec-Fetch-Dest header][] if it is present. Otherwise, some main pages may be treated as subdocuments.
@@ -962,7 +975,7 @@ The rule applies only to WebSocket connections.
##### Einschränkungen des Modifikators `$websocket` {#websocket-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
For AdGuard for Safari and AdGuard for iOS, it is supported on devices with macOS Monterey (version 12) and iOS 16 or higher respectively.
@@ -1221,7 +1234,7 @@ Disables blocking of all requests sent from the pages matching the rule and disa
##### `$urlblock` modifier limitations {#urlblock-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
In AdGuard for iOS and AdGuard for Safari, rules with `$urlblock` work as [$document exclusion](#document-modifier) — unblock everything.
@@ -1246,7 +1259,7 @@ For example, these rules are generic:
*#@#.adsblock
~domain.com###banner
||domain.com^
-||domain.com^$domain=~example .com
+||domain.com^$domain=~example.com
```
And these are not:
@@ -1266,7 +1279,7 @@ Disables generic basic rules on pages that correspond to exception rule.
##### `$genericblock` modifier limitations {#genericblock-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
In AdGuard for iOS and AdGuard for Safari, rules with `$genericblock` work as [$document exclusion](#document-modifier) — unblock everything.
@@ -1373,7 +1386,7 @@ This modifier cannot be used as an exception with the `@@` mark.
##### Einschränkungen des Modifikators `$all` {#all-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
Since `$popup` is a part if `$all`, the `$all` modifier is not supported by AdGuard for Chrome MV3 because of [`$popup` modifier limitations](#popup-modifier-limitations).
@@ -1414,7 +1427,7 @@ In that case, the `$badfilter` rule will disable the corresponding rule for doma
##### Einschränkungen des Modifikators `$badfilter` {#badfilter-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
In [AdGuard for Chrome MV3][ext-mv3] a rule with the `$badfilter` modifier is applied in DNR only if it fully cancels the source rule. We cannot calculate it if it is only partially canceled. [Examples][badfilter-in-mv3].
@@ -1477,7 +1490,7 @@ There are two methods to deactivate `$cookie` rules: the primary method involves
##### `$cookie` modifier limitations {#cookie-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
In [AdGuard for Chrome MV3][ext-mv3] we delete cookies in 2 ways: from `content-script` side (to which we have access) and from `onBeforeSendHeaders` listener. Since `onBeforeSendHeaders` and other listeners are no longer blocking, we are not able to delete them in all cases. You can check if a rule works with [this test](https://testcases.agrd.dev/Filters/cookie-rules/test-cookie-rules).
@@ -1587,16 +1600,16 @@ When multiple `$hls` rules match the same request, their effect is cumulative.
A quick summary of the [specification](https://datatracker.ietf.org/doc/html/rfc8216):
-1. Eine HLS-Playlist ist eine Sammlung von Textzeilen
-1. Eine Zeile kann leer sein, ein Kommentar (beginnt mit `#`), ein Tag (beginnt ebenfalls mit `#`, kann nur anhand des Namens erkannt werden) oder eine URL
-1. Eine URL-Zeile wird als „Segment“ bezeichnet
-1. Tags können auf ein einzelnes Segment angewendet werden, d.h. die erste URL-Zeile nach dem Tag, auf alle Segmente, die dem Tag folgen, und bis zum Tag mit demselben Namen, oder auf die gesamte Playlist
+1. An HLS playlist is a collection of text lines
+1. A line may be empty, a comment (starts with `#`), a tag (also starts with `#`, can only be recognized by name) or a URL
+1. A URL line is called a "segment"
+1. Tags may apply to a single segment, i.e. the first URL line after the tag, to all segments following the tag and until the tag with the same name, or to the whole playlist
Some points specific to the operation of `$hls` rules:
-1. Wenn ein Segment entfernt wird, werden auch alle Tags entfernt, die nur für dieses Segment gelten
-1. Wenn es einen Tag gibt, der auf mehrere Segmente angewendet wird, und alle diese Segmente entfernt werden, wird auch der Tag entfernt
-1. Da es keine Möglichkeit gibt, verschiedene Arten von Tags syntaktisch zu erkennen, erkennen wir alle die durch das RFC spezifizierten Tags, plus einige nicht-standardisierte Tags, die wir im Feld gesehen haben. Any lines starting with `#` and not recognized as a tag are passed through without modification, and are not matched against the rules
+1. When a segment is removed, all of the tags that apply only to that segment are also removed
+1. When there is a tag that applies to multiple segments, and all of those segments are removed, the tag is also removed
+1. Since there is no way to recognize different kinds of tags by syntax, we recognize all of the tags specified by the RFC, plus some non-standard tags that we have seen in the field. Any lines starting with `#` and not recognized as a tag are passed through without modification, and are not matched against the rules
1. Tags will not be matched if they apply to the entire playlist, and `$hls` rules cannot be used to remove them, as these rule types are intended for segment removals. If you know what you are doing, you can use `$replace` rules to remove or rewrite just a single tag from the playlist
**An example of a transformation done by the rules:**
@@ -1701,15 +1714,15 @@ Due to the way rule parsing works, the characters `$` and `,` must be escaped wi
The modified JSONPath syntax has the following differences from the original:
-1. Skriptausdrücke werden nicht unterstützt
-1. Die unterstützten Filterausdrücke sind:
- - `?(hat )` — wahr, wenn das aktuelle Objekt den angegebenen Schlüssel hat
- - `?(key-eq )` — wahr, wenn das aktuelle Objekt den angegebenen Schlüssel hat und dessen Wert dem angegebenen Wert entspricht
- - `?(key-substr )` — wahr, wenn der angegebene Wert eine Teilzeichenfolge des Werts des angegebenen Schlüssels des aktuellen Objekts ist
-1. Leerzeichen außerhalb von Zeichenfolgen in doppelten oder einfachen Anführungszeichen haben keine Bedeutung
-1. Sowohl doppelt als auch einfach zitierte Zeichenfolgen können verwendet werden
-1. Ausdrücke, die mit `..` enden, werden nicht unterstützt
-1. Mehrere Array-Slices können in eckigen Klammern angegeben werden
+1. Script expressions are not supported
+1. The supported filter expressions are:
+ - `?(has )` — true if the current object has the specified key
+ - `?(key-eq )` — true if the current object has the specified key, and its value is equal to the specified value
+ - `?(key-substr )` — true if the specified value is a substring of the value of the specified key of the current object
+1. Whitespace outside of double- or single-quoted strings has no meaning
+1. Both double- and single-quoted strings can be used
+1. Expressions ending with `..` are not supported
+1. Multiple array slices can be specified in square brackets
There are various online tools that make working with JSONPath expressions more convenient:
@@ -1878,6 +1891,9 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
"elems": [
{
"a": {"b": {"c": 123}}
+ },
+ {
+ "a": {"b": {"c": "abc"}}
}
]
}
@@ -1951,21 +1967,21 @@ When multiple `$xmlprune` rules match the same request, they are applied in lexi
- Jeden Tag Italienisch
+ Everyday Italian
Giada De Laurentiis
2005
30.00
- Harry Potter
+ Harry Potter
J K. Rowling
2005
29.99
- XQuery Kick Start
+ XQuery Kick Start
James McGovern
Per Bothner
Kurt Cagle
@@ -1976,7 +1992,7 @@ When multiple `$xmlprune` rules match the same request, they are applied in lexi
- XML Lernen
+ Learning XML
Erik T. Ray
2003
39.95
@@ -2029,21 +2045,21 @@ When multiple `$xmlprune` rules match the same request, they are applied in lexi
- Jeden Tag Italienisch
+ Everyday Italian
Giada De Laurentiis
2005
30.00
- Harry Potter
+ Harry Potter
J K. Rowling
2005
29.99
- XQuery Kick Start
+ XQuery Kick Start
James McGovern
Per Bothner
Kurt Cagle
@@ -2054,7 +2070,7 @@ When multiple `$xmlprune` rules match the same request, they are applied in lexi
- XML Lernen
+ Learning XML
Erik T. Ray
2003
39.95
@@ -2156,7 +2172,7 @@ Rules with the `$xmlprune` modifier are supported by AdGuard for Windows, AdGuar
This is basically a Firewall-like rule allowing to fully block or unblock access to a specified remote address.
1. `$network` rules match **IP addresses only**! You cannot use them to block or unblock access to a domain.
-2. Um eine IPv6-Adresse zu erfassen, müssen Sie die komprimierte Syntax verwenden, z.B. verwenden Sie `[2001:4860:4860::8888]$network` anstelle von `[2001:4860:4860:0:0:0:0:8888]$network`.
+2. To match an IPv6 address, you have to use the collapsed syntax, e.g. use `[2001:4860:4860::8888]$network` instead of `[2001:4860:4860:0:0:0:0:8888]$network`.
3. An allowlist `$network` rule makes AdGuard bypass data to the matching endpoint, hence there will be no further filtering at all.
4. If the IP part starts and ends with `/` character, it is treated as a regular expression.
@@ -2229,7 +2245,7 @@ If there are multiple `$permissions` rules that match the same request, multiple
##### `$permissions` modifier limitations {#permissions-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
Firefox ignores the `Permissions-Policy` header. For more information, see [this issue](https://bugzilla.mozilla.org/show_bug.cgi?id=1694922).
@@ -2238,7 +2254,7 @@ Firefox ignores the `Permissions-Policy` header. For more information, see [this
:::caution Einschränkungen
1. Characters forbidden in the `$permissions` value: `$`.
-2. `$permissions` ist kompatibel mit einer begrenzten Anzahl von Modifikatoren: `$domain`, `$important`, `$subdocument` und [Inhaltstyp-Modifikatoren](#content-type-modifiers).
+2. `$permissions` is compatible with a limited set of modifiers: `$domain`, `$important`, `$subdocument`, and [content-type modifiers](#content-type-modifiers).
3. `$permissions` rules that do not have any [content-type modifiers](#content-type-modifiers) will match only requests where content type is `document`.
:::
@@ -2283,7 +2299,7 @@ Go to [rules priorities](#rule-priorities) for more details.
##### `$redirect` modifier limitations {#redirect-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
In [AdGuard for Chrome MV3][ext-mv3] allowlist rules with `$redirect` are not supported.
@@ -2385,7 +2401,7 @@ In case of multiple `$removeheader` rules matching a single request, we will app
##### `$removeheader` modifier limitations {#removeheader-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
[AdGuard for Chrome MV3][ext-mv3] has some limitations:
@@ -2630,7 +2646,7 @@ With these rules, specified UTM parameters will be removed from any request save
##### `$removeparam` modifier limitations {#removeparam-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
[AdGuard for Chrome MV3][ext-mv3] has some limitations:
@@ -4104,7 +4120,7 @@ Following rule will delete all `script` elements with a `banner` substring in th
$$script[tag-content="banner"]
```
-:::caution Beschränkungen
+:::caution Limitations
The `tag-content` special attribute must not appear in a selector to the left of a `>` combinator.
@@ -4126,7 +4142,7 @@ For example: `$$script[wildcard="*banner*text*"]`
It checks if the element code contains the two consecutive substrings `banner` and `text`.
-:::caution Beschränkungen
+:::caution Limitations
The `wildcard` special attribute must not appear in a selector to the left of a `>` combinator.
@@ -4154,7 +4170,7 @@ $$div[tag-content="banner"][max-length="400"]
This rule will remove all the `div` elements, whose code contains the substring `banner` and the length of which does not exceed `400` characters.
-:::caution Beschränkungen
+:::caution Limitations
The `max-length` special attribute must not appear in a selector to the left of a `>` combinator.
@@ -4178,7 +4194,7 @@ $$div[tag-content="banner"][min-length="400"]
This rule will remove all the `div` elements, whose code contains the substring `banner` and the length of which exceeds `400` characters.
-:::caution Beschränkungen
+:::caution Limitations
The `min-length` special attribute must not appear in a selector to the left of a `>` combinator.
@@ -4214,7 +4230,7 @@ The `:contains()` pseudo-class is supported by AdGuard for Windows, AdGuard for
Requires that the inner HTML of the element contains the specified text or matches the specified regular expression.
-:::caution Beschränkungen
+:::caution Limitations
A `:contains()` pseudo-class must not appear in a selector to the left of a `>` combinator.
@@ -4491,7 +4507,7 @@ But rules with mixed style domains restriction are considered invalid. So, for e
### Non-basic `$domain` modifier limitations {#non-basic-domain-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
Since the non-basic `$domain` works the same as the basic one, it has the same [limitations](#domain-modifier-limitations).
@@ -4558,7 +4574,7 @@ where `pattern` is pretty much the same as [`pattern` of the basic rules](#basic
#### `$url` modifier limitations {#non-basic-url-modifier-limitations}
-:::caution Beschränkungen
+:::caution Limitations
In AdGuard Browser Extension, non-basic `$url` modifier is not compatible with domain-specific rules and other non-basic modifiers — [`$domain`](#non-basic-domain-modifier) and [`$path`](#non-basic-path-modifier). For example, the rule `[$url=/category/*]example.com###textad` will not be applied.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index d1cde3729df..159bef37d77 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard-Filter zum Blockieren von Werbung umfassen:
- AdGuard Basisfilter
- AdGuard-Filter gegen mobile Werbung
- Regionale Filter nach Sprachprinzip — Chinesisch, Niederländisch, Französisch, Deutsch, Japanisch, Russisch, Spanisch/Portugiesisch, Türkisch, und Ukrainisch
-- AdGuard Quick Fixes-Filter
### Der Zweck dieser Filter
- **Der Basisfilter** blockiert Werbung auf englischsprachigen Websites und solchen, für die es keinen eigenen Filter gibt. Er enthält auch allgemeine Filterregeln, die für alle Websites unabhängig von der Sprache gelten
- **Filter gegen mobile Werbung** blockiert Werbung auf mobilen Versionen von Websites und in mobilen Apps. Es gibt keine Unterteilung nach Sprachen
- **Sprachspezifische Filter** folgen der gleichen Politik wie der **Basisfilter**, sind aber auf Websites in bestimmten Sprachen beschränkt
-- **Quick-Fixes-Filter** zur schnellen Behebung kritischer Probleme bei der Filterung von Inhalten auf beliebten Websites ohne Aktualisierung der MV3-Erweiterung.
Das Ziel von Werbeblockern ist es, alle Arten von Werbung auf Websites, in Apps und auf bestimmten Geräten, die Werbung aus dem Internet laden können, zu blockieren:
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/tracking-filter-statistics.md b/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/tracking-filter-statistics.md
index 3f45fe39728..a246a30823e 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/tracking-filter-statistics.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/general/ad-filtering/tracking-filter-statistics.md
@@ -13,7 +13,7 @@ Die Option *Bei Verbesserung der AdGuard-Filter helfen* ist standardmäßig deak
Definieren wir zunächst, was Werbefilter sind. Dank dieser Filter entfernt AdGuard Werbung von Websites. Sie werden manuell auf der Grundlage Ihrer Beschwerden über Werbung auf Websites zusammengestellt. Werbefilter sind ein wesentliches Element von AdGuard — ihre Qualität bestimmt die Gesamtqualität der von AdGuard gesperrten Werbung.
-Allerdings gibt es auch eine Kehrseite. Over the years, more and more ad filters have appeared. The more ad filters there are, the more memory AdGuard consumes, thus slowing down the rendering of webpages. At the same time, some filters expire and gradually become useless, consuming memory and slowing down the program.
+Allerdings gibt es auch eine Kehrseite. Im Laufe der Jahre sind mehr und mehr Werbefilter aufgetaucht. Und je mehr Werbefilter vorhanden sind, desto mehr Arbeitsspeicher verbraucht AdGuard und verlangsamt damit das Aufbereiten von Webseiten. Gleichzeitig verfallen einige Filter und werden allmählich nutzlos, verbrauchen Speicher und verlangsamen das Programm.
### Warum werden Statistiken benötigt?
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/general/extensions.md b/i18n/de/docusaurus-plugin-content-docs/current/general/extensions.md
index b347a7c0dad..c8da7df8cfb 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/general/extensions.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/general/extensions.md
@@ -155,10 +155,10 @@ Weitere Informationen zur Greasemonkey-API finden Sie im [Handbuch] (https://wik
```javascript
// ==UserScript==
-// @name Name as shown to the user when locale is english or unknown
-// @name:ru Name as shown to the user when locale is russian
-// @description Description as shown to the user when locale is english or unknown
-// @description:ru Description as shown to the user when locale is russian
+// @name Name, der dem Benutzer angezeigt wird, wenn das Gebietsschema „Englisch“ oder „Unbekannt“ ist
+// @name:ru Name, wie er dem Benutzer angezeigt wird, wenn das Gebietsschema „Russisch” ist
+// @description Beschreibung, die dem Benutzer angezeigt wird, wenn das Gebietsschema „Englisch“ oder „Unbekannt“ ist
+// @description:ru Beschreibung, wie sie dem Benutzer angezeigt wird, wenn das Gebietsschema „Russisch“ ist
// @icon https://myhomepage.com/myuserscript.png
// @version 1.0.0.0
// @downloadURL https://dl.myhomepage.org/myuserscript.user.js
@@ -184,7 +184,6 @@ Weitere Informationen zur Greasemonkey-API finden Sie im [Handbuch] (https://wik
// @grant GM_openInTab
// @grant GM_registerMenuCommand
// @grant GM_addElement
-// @grant window.onurlchange
// @run-at document-start
// ==/UserScript==
!function(){(
@@ -327,13 +326,13 @@ divElement.innerHTML = ADG_policyApi.convertPropertyToTrusted("div", "innerHTML"
:::info Kompatibilität
-This section only applies to AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs] v1.19 or later.
+Dieser Abschnitt gilt nur für AdGuard für Windows, AdGuard für Mac, AdGuard für Android und AdGuard für Linux mit [CoreLibs] v1.19 oder höher.
:::
-Many modern websites, such as YouTube, utilize [Single Page Application (SPA)](https://en.wikipedia.org/wiki/Single-page_application) capabilities. Unlike traditional web applications, the page does not reload when navigating between pages. Instead, the content is updated dynamically using JavaScript, allowing for a smoother user experience.
+Viele moderne Websites, wie beispielsweise YouTube, nutzen die Funktionen von [Single-Page-Webanwendung (SPA)](https://de.wikipedia.org/wiki/Single-Page-Webanwendung). Im Gegensatz zu herkömmlichen Webanwendungen wird die Seite beim Wechsel zwischen den Seiten nicht neu geladen. Stattdessen wird der Inhalt dynamisch mit JavaScript aktualisiert, was eine flüssigere Benutzererfahrung ermöglicht.
-On such websites, a userscript is invoked only once when the `@match` or `@include` directives are matched (unless `@exclude` is matched). Due to the nature of SPAs, the userscript cannot be re-invoked on subsequent page changes because the global JavaScript context remains the same. To address this issue, userscripts can use the `@grant window.onurlchange` directive.
+Auf solchen Websites wird ein Benutzerskript nur einmal aufgerufen, wenn die Anweisungen `@match` oder `@include` übereinstimmen (es sei denn, `@exclude` stimmt überein). Aufgrund der Besonderheiten von SPAs kann das Benutzerskript bei nachfolgenden Seitenwechseln nicht erneut aufgerufen werden, da der globale JavaScript-Kontext unverändert bleibt. Um dieses Problem zu beheben, können Benutzerskripte die Anweisung `@grant window.onurlchange` verwenden.
```javascript
// ==UserScript==
@@ -356,26 +355,26 @@ window.addEventListener('urlchange', (event) => {
});
```
-This will allow userscripts to listen for URL changes and handle them accordingly.
+Dadurch können Benutzerskripte auf URL-Änderungen reagieren und diese entsprechend verarbeiten.
:::note
-The `urlchange` event is only triggered for full URL changes, such as a change in the path or query, but not for fragment (hash) changes.
-Examples:
+Das Ereignis `urlchange` wird nur bei vollständigen URL-Änderungen ausgelöst, z. B. bei einer Änderung des Pfads oder der Abfrage, jedoch nicht bei Änderungen des Fragments (Hash).
+Beispiele:
-- Navigation from `https://example.com/page1` to `https://example.com/page2` will trigger the event.
-- Navigation from `https://example.com/page1?query=1` to `https://example.com/page1?query=2` will trigger the event.
-- Navigation from `https://example.com/page1#section1` to `https://example.com/page1#section2` will **NOT** trigger the event.
+- Das Navigieren von `https://example.com/page1` zu `https://example.com/page2` löst das Ereignis aus.
+- Die Navigation von `https://example.com/page1?query=1` zu `https://example.com/page1?query=2` löst das Ereignis aus.
+- Die Navigation von `https://example.com/page1#section1` zu `https://example.com/page1#section2` löst das Ereignis **NICHT** aus.
:::
:::note
-The `window.onurlchange` and `window.addEventListener('urlchange', ...)` APIs are non-standard. To use them, you must explicitly grant them in your userscript with `@grant window.onurlchange`.
+Die APIs `window.onurlchange` und `window.addEventListener(‚urlchange‘, ...)` sind nicht standardisiert. Um sie zu verwenden, müssen Sie sie in Ihrem Benutzerskript explizit mit `@grant window.onurlchange` gewähren.
:::
-If a website uses hash routing, userscripts can use the native DOM [`hashchange` event](https://developer.mozilla.org/en-US/docs/Web/API/Window/hashchange_event):
+Wenn eine Website Hash-Routing verwendet, können Benutzerskripte das native DOM-Ereignis [`hashchange`](https://developer.mozilla.org/de/docs/Web/API/Window/hashchange_event) verwenden:
```javascript
// ==UserScript==
@@ -397,47 +396,47 @@ window.addEventListener('hashchange', (event) => {
});
```
-## Userstyles
+## Benutzerstile (Userstyles)
-Userstyles allow users to change the appearance of popular websites.
+Mit Benutzerstilen kann man das Aussehen beliebter Websites ändern.
-AdGuard has the option to upload or create your own userstyles. This is an advanced feature, so you will need some knowledge of HTML and CSS.
+AdGuard bietet die Möglichkeit, eigene Benutzerstile hochzuladen oder zu erstellen. Da es sich hierbei um eine technisch anspruchsvolle Funktion handelt, benötigen Sie einige Kenntnisse in HTML und CSS.
:::info Unterstützte Apps
-Currently, two AdGuard apps allow you to create and manage userstyles: AdGuard for Windows (v7.19 or later) and AdGuard for Mac (v2.16 or later). We also plan to implement this new feature in AdGuard for Android v4.8 in the nearest future.
+Derzeit gibt es zwei AdGuard-Anwendungen, mit denen Sie Benutzerstile erstellen und verwalten können: AdGuard für Windows (v7.19 oder höher) und AdGuard für Mac (v2.16 oder höher). Es ist zudem geplant, diese neue Funktion in AdGuard für Android v4.8 in naher Zukunft zu implementieren.
:::
-This is an experimental feature, so if you encounter any problems while adding or creating a userstyle, please contact our support team at .
+Es handelt sich hierbei um eine experimentelle Funktion. Wenn Sie also beim Hinzufügen oder Erstellen eines Benutzerstils auf Probleme stoßen, wenden Sie sich bitte an unser Support-Team unter .
-### How to set up a userstyle in AdGuard
+### So richten Sie einen Benutzerstil in AdGuard ein
-You can download userstyles from various websites. One of the most popular userstyle websites is [https://userstyles.world/](https://userstyles.world/explore), which we will use as an example for the following instructions on how to set up the userstyle in AdGuard.
+Sie können Benutzerstile von verschiedenen Websites herunterladen. Eine der populärsten Benutzerstil-Websites ist [https://userstyles.world/](https://userstyles.world/explore), die hier als Beispiel für die folgenden anweisungen zur Einstellungen des Benutzerstils in AdGuard verwendet wird.
-1. Follow the link above and choose the userstyle you like
+1. Folgen Sie dem obigen Link und wählen Sie den gewünschten Benutzerstil
-2. Click _Copy_ next to the userstyle address
+2. Klicken Sie auf _Kopieren_ neben der Adresse des Benutzerstils
-3. Open AdGuard settings → _Extensions_
+3. Öffnen Sie die AdGuard-Einstellungen → _Erweiterungen_
-4. Press the [+] button and paste the userstyle link
+4. Drücken Sie auf die Schaltfläche [+] und fügen Sie den Benutzerstil-Link ein
5. Fertig!
-If you’re familiar with CSS rules, you can also create userstyles yourself.
+Wenn Sie mit den CSS-Regeln vertraut sind, können Sie auch selbst Benutzerstile erstellen.
:::note
-We don’t support userstyles that contain `@var` or `@advanced` in the metadata. AdGuard also doesn’t support `@preprocessor` without the `default` value.
+Es werden keine Benutzerstile unterstützt, die `@var` oder `@advanced` in den Metadaten enthalten. AdGuard unterstützt auch nicht `@preprocessor` ohne den `default`-Wert.
:::
-1. Open AdGuard settings → _Extensions_
+1. Öffnen Sie die AdGuard-Einstellungen → _Erweiterungen_
-2. Press the [+] button and choose the _Create userstyle_ option. A new window will appear on your screen
+2. Drücken Sie auf die Schaltfläche [+] und wählen Sie die Option _Benutzerstil erstellen_. Es wird ein neues Fenster auf Ihrem Bildschirm angezeigt
-3. To create a userstyle, first write the title with metadata, for example
+3. Um einen Benutzerstil zu erstellen, schreiben Sie zunächst den Titel mit Metadaten, zum Beispiel
```CSS
/* ==UserStyle==
@@ -446,7 +445,7 @@ We don’t support userstyles that contain `@var` or `@advanced` in the metadata
==/UserStyle== */
```
-4. Write the CSS part after the meta data. AdGuard supports website domain names matching (`@-moz-document domain(…), …`). Zum Beispiel:
+4. Schreiben Sie den CSS-Teil nach den Metadaten. AdGuard unterstützt den Abgleich von Website-Domainnamen (`@-moz-document domain(…), …`). Zum Beispiel:
```CSS
body {
@@ -454,7 +453,7 @@ We don’t support userstyles that contain `@var` or `@advanced` in the metadata
}
```
- Or:
+ oder:
```CSS
@-moz-document domain('example.org'),
@@ -464,7 +463,7 @@ We don’t support userstyles that contain `@var` or `@advanced` in the metadata
}
```
-5. Once you’re finished, press _Save and Close_. Your new userstyle has been successfully added to AdGuard
+5. Wenn Sie fertig sind, drücken Sie _Speichern und schließen_. Ihr neuer Benutzerstil wurde erfolgreich zu AdGuard hinzugefügt
### Beispiel
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/guides/minidump.md b/i18n/de/docusaurus-plugin-content-docs/current/guides/minidump.md
index 37b9fba3f58..ee2e3f7e7b0 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/guides/minidump.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/guides/minidump.md
@@ -57,23 +57,23 @@ Standardmäßig wird die Minidump-Datei im Ordner **%SystemRoot%\Minidump** gesp
## Collecting wfpdiag.cab file
-Our support team may request a wfpdiag.cab file, along with a minidump file, to analyze system logs more thoroughly and diagnose issues. To collect the file, please follow these steps:
+Unser Support-Team kann eine wfpdiag.cab-Datei zusammen mit einer Minidump-Datei anfordern, um die Systemprotokolle genauer analysieren und Probleme diagnostizieren zu können. Um die Datei zu erfassen, gehen Sie bitte wie folgt vor:
1. Aktivieren Sie den AdGuard-Schutz.
-1. Click *Start* and type `cmd` to open Command Prompt
+1. Klicken Sie auf *Start* und geben Sie den Befehl `cmd` ein, um die Eingabeaufforderung zu öffnen
-1. Right-click Command Prompt and choose *Run as administrator*
+1. Klicken Sie mit der rechten Maustaste auf Eingabeaufforderung und wählen Sie *Als Administrator ausführen*
:::note
- A wfpdiag.cab file is created in your current directory. You can change the location by typing `cd `.
+ Es wird eine Datei „wfpdiag.cab“ in Ihrem aktuellen Verzeichnis erstellt. Sie können den Speicherort ändern, indem Sie `cd ` eingeben.
:::
-1. To start logging, enter the following command: `netsh wfp capture start`
+1. Um die Protokollierung zu starten, geben Sie den folgenden Befehl ein: `netsh wfp capture start`
-1. Visit any website to route traffic through AdGuard and log the filtering process
+1. Besuchen Sie eine beliebige Website, um den Datenverkehr durch AdGuard zu leiten und den Filterungsprozess zu protokollieren
-1. To stop logging, enter `netsh wfp capture stop`
+1. Um die Protokollierung zu beenden, geben Sie `netsh wfp capture stop` ein
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/miscellaneous/contribute/beta-testing.md b/i18n/de/docusaurus-plugin-content-docs/current/miscellaneous/contribute/beta-testing.md
index 028f4777984..9b21957943f 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/miscellaneous/contribute/beta-testing.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/miscellaneous/contribute/beta-testing.md
@@ -1,5 +1,5 @@
---
-title: AdGuard Beta Testing
+title: AdGuard testen (Beta/Nightly)
sidebar_position: 1
---
@@ -17,7 +17,7 @@ Unsere Anforderungen sind einfach: Verwenden Sie AdGuard, aktualisieren Sie auf
Sie benötigen außerdem das Gerät, auf dem Sie die App installieren wollen, und [den Link zur Beta-Test-Seite](https://adguard.com/beta.html). Dort finden Sie weitere Informationen darüber, wie Sie an unserem Programm teilnehmen und AdGuard für Windows, Mac, Android und iOS testen können.
-If you would like to become a tester, please [fill out the form](https://surveys.adguard.com/beta_testing_program/form.html) to submit your application. If it is approved, you will receive a response via email within a few days.
+Wenn Sie Tester werden möchten, [füllen Sie das Formular aus](https://surveys.adguard.com/beta_testing_program/form.html), um Ihre Bewerbung zu senden. Wenn die Bewerbung genehmigt wird, erhalten Sie innerhalb weniger Tage eine Antwort per E-Mail.
:::note
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/miscellaneous/contribute/translate/rewards.md b/i18n/de/docusaurus-plugin-content-docs/current/miscellaneous/contribute/translate/rewards.md
index d42e43d81ac..fec7abb7dd0 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/miscellaneous/contribute/translate/rewards.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/miscellaneous/contribute/translate/rewards.md
@@ -55,6 +55,6 @@ Bitte beachten Sie, dass Sie mit diesem Status keine zusätzlichen Lizenzen oder
## Geschenke für aktive Mitwirkende
-To the best contributors, every year we send gifts with the AdGuard merch and give a shout out on our [blog](https://adguard.com/en/blog/best-contributors-2024.html).
+Jedes Jahr senden wir den besten Mitwirkenden Geschenke mit dem AdGuard-Merch und würdigen sie in unserem [Blog](https://adguard.com/en/blog/best-contributors-2024.html).

diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 66164bdf1b3..bbb0b25a663 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ El número máximo de filtros habilitados simultáneamente es **50**.
**Reglas dinámicas:** se impone un límite estricto de **5 000** reglas, que incluye un máximo de 1 000 reglas de expresiones regulares.
-Si se supera este límite, sólo se aplicarán **5.000 reglas convertidas** en el siguiente orden: primero Allowlist, luego Reglas del usuario, filtros personalizados y, por último, el filtro Quick Fixes.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Las reglas convertidas** son reglas que se han transformado
> a \[formato DNR] usando el [convertidor declarativo][github-declarative-converter].
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index 09fe4061924..ae8657bc941 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Proxy saliente
#### Show the Filter DNS requests setting
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 2d077df93aa..fb6f708f53c 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Asistencia técnica
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 82a1144e68f..1327fadbd5a 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ Listo, AdGuard para Android TV está instalado.
- En el terminal, introduce el comando `adb install Downloads/adguard_tv.apk`. Si es necesario, reemplaza `Downloads/adguard_tv.apk` con tu ruta.
- Espera un mensaje en la terminal indicando la instalación exitosa de la aplicación.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index d62fb897447..94a82e34351 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifica la autenticidad de todos los certificados para el dominio según la pol
Al configurar `true`, permites que AdGuard filtre el tráfico enviado a través de HTTP/3, la última versión del protocolo HTTP basado en QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
Al configurar `true`, habilita el filtrado de red local.
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 492149c18d7..6c6d44e3e0e 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ Este artículo trata sobre AdGuard para Windows, un bloqueador de anuncios multi
AdGuard para Windows es una herramienta fácil de usar que bloquea molestos banners, ventanas emergentes, anuncios de vídeo y rastreadores. Pero eso no es todo: te ayuda a ahorrar tráfico, cargar páginas web más rápido y proteger tu ordenador de sitios web indeseables y potencialmente maliciosos. AdGuard también te protege de los sitios web de phishing y mantiene a tus hijos alejados de contenidos inapropiados.
-
+
Una vez que inicies AdGuard para Windows, verás la pantalla principal de la aplicación. Su detalle más llamativo es el botón _activar/desactivar protección_. Además, en esta pantalla puedes monitorear anuncios bloqueados, rastreadores y estadísticas de amenazas, conocer la versión actual de la aplicación o actualizarla. Además, hay cuatro pestañas en la esquina superior derecha: _Configuración_, _Soporte_, _Licencia_ y _Acerca de_. Merece la pena hablar de cada uno de ellos por separado.
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index bde77a7120a..0a0274ee4a2 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ Este artículo trata sobre AdGuard para Windows, un bloqueador de anuncios multi
_Configuración_ es la sección que requiere mayor atención. Aquí es donde podrás configurar la aplicación para que cumpla plenamente con tus requisitos: bloquea sólo lo que te molesta, utiliza el servidor DNS del proveedor de confianza, elimina las cookies de terceros, etc.
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### Configuración general
+
-Aquí puedes configurar el idioma y el tema (Oscuro o Claro), habilitar el inicio de AdGuard al iniciar el sistema y las actualizaciones automáticas silenciosas, elegir el canal de actualización y filtrar el intervalo de verificación de actualización. Además, configuración es el lugar al que acudir si AdGuard para Windows no funciona correctamente y el equipo de soporte te pidió que [recopiles _Logs de depuración_](/adguard-for-windows/solving-problems/adguard-logs.md).
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-En la parte inferior de la pantalla encontrarás _Configuración avanzada_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Ad blocking
Este es el módulo principal de AdGuard para Windows que elimina anuncios de los sitios web que visitas y de las aplicaciones instaladas en tu dispositivo. Para filtrar publicidad y contenido que amenaza la privacidad, como banners, ventanas emergentes o rastreadores, AdGuard utiliza diferentes filtros: grupos de reglas con un propósito similar escrito con una [sintaxis especial](/general/ad-filtering/create-own-filters). Para comprender qué son los filtros y cómo funcionan, lee [este artículo](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Muchos sitios web recopilan información sobre sus visitantes, como sus direccio

-Puedes ajustar de manera flexible el funcionamiento del modo oculto: por ejemplo, puedes prohibir que el sitio web reciba la solicitud de búsqueda que utilizaste para encontrarlo en Internet, eliminar automáticamente las cookies de terceros y del propio sitio web y deshabilitar la opción de compartir ubicación en tu navegador, que se puede utilizar para rastrear tu ubicación real.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-Para aprender todo sobre el modo sigiloso y sus muchas opciones, [lee este artículo](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Seguridad de navegación
@@ -81,15 +81,15 @@ A partir de la v7.20, también puedes añadir filtrados simplemente seleccionán

-### Control parental
+### Parental control
-Existen varios sitios web a los que se debe restringir el acceso desde una PC utilizada por niños. This task is accomplished by _Parental Control_.
+Existen varios sitios web a los que se debe restringir el acceso desde una PC utilizada por niños. This task is accomplished by _Parental control_.
-
+
-El módulo verifica el contenido de las páginas web abiertas en el navegador y filtra aquellas con contenido no deseado para los niños: imágenes y textos para adultos, lenguaje grosero, violencia, propaganda de drogas, etc. La configuración del Control parental está protegida con contraseña para que el niño no pueda eludir las restricciones. Este módulo no sólo bloquea direcciones a sitios no deseados sino que también puede eliminar de los resultados de búsqueda los enlaces que no son apropiados para niños.
+El módulo verifica el contenido de las páginas web abiertas en el navegador y filtra aquellas con contenido no deseado para los niños: imágenes y textos para adultos, lenguaje grosero, violencia, propaganda de drogas, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. Este módulo no sólo bloquea direcciones a sitios no deseados sino que también puede eliminar de los resultados de búsqueda los enlaces que no son apropiados para niños.
-En el módulo de _Control parental_ puedes habilitar la _Búsqueda segura_ y administrar la _lista de bloqueo_ y la _lista de permitidos_ para personalizar cómo funciona esta opción. También puedes marcar la casilla _Bloquear descarga de archivos ejecutables_ para evitar que tu hijo descargue e instale software en la computadora. Hay dos opciones más en el módulo _Control parental_: puedes seleccionar un usuario específico de Windows para que esté protegido por _Control parental_ y establecer una contraseña para proteger la configuración de AdGuard contra cambios.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. También puedes marcar la casilla _Bloquear descarga de archivos ejecutables_ para evitar que tu hijo descargue e instale software en la computadora. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Asistente de navegador
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 59e74708077..35e04a43dd3 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Habilita esta función si deseas que AdGuard intercepte automáticamente las URL
Si esta opción está habilitada, AdGuard filtrará las solicitudes enviadas a través de HTTP/3 además de otros tipos de solicitudes.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Usar modo de redireccionamiento del driver
Si esta opción está habilitada, AdGuard intercepta todo el tráfico y lo redirige al servidor proxy local para un mayor filtrado.
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 964cfd30a10..2eec9b80669 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ Este artículo trata sobre los filtros que creamos para usar en AdGuard y otros
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 59641c03b4e..1966b3b7906 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ Este modificador te permite restringir la cobertura de la regla a una aplicació
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Sintaxis**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restricciones
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -490,7 +518,7 @@ Las reglas con el modificador `$denyallow` no son compatibles con AdGuard para i
`$domain` limits the rule scope to requests made **from** the specified domains and their subdomains (as indicated by the [Referer](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Referer) HTTP header).
-**Sintaxis**
+**Syntax**
El modificador es una lista de una o más expresiones separadas por el símbolo `|`, cada una de las cuales se empareja con un dominio de una manera particular dependiendo de su tipo (ver más abajo).
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. El modificador `$domain` contiene solo dominios excluidos, p. ej. `$domain=~example.org|~example.com`
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
-
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
-
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 5a130502d63..729bfa0ffd9 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ Los filtros de bloqueo de anuncios de AdGuard incluyen:
- Filtro base AdGuard
- Filtro de anuncios de AdGuard para dispositivos móviles
- Filtros regionales divididos por idiomas: chino, holandés, francés, alemán, japonés, ruso, español, portugués, turco y ucraniano
-- Filtro AdGuard Quick Fixes
### La finalidad de estos filtros
- El **Filtro base** fue diseñado para bloquear anuncios en sitios en inglés y aquellos para los cuales no hay un filtro separado. También contiene reglas generales de filtrado que se aplican a todos los sitios, independientemente del idioma
- El **Filtro de anuncios para dispositivos móviles** bloquea anuncios en versiones móviles de sitios y en teléfonos celulares y tabletas. No hay segmentación basada en el idioma
- Los **Filtros regionales** siguen la misma política que el **Filtro base**, pero están limitados a sitios en determinados idiomas
-- **Filtro Quick Filters** utilizados para resolver rápidamente problemas críticos de filtrado de contenido en sitios populares sin actualizar la extensión MV3.
El objetivo de los filtros de bloqueo de anuncios es bloquear todos los tipos de publicidad en sitios web, aplicaciones y dispositivos específicos que pueden cargar anuncios de Internet:
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index d10f3e8722a..e8bf65a8bb2 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -21,19 +21,19 @@ The old beta extension will be renamed to [**AdGuard Ad Blocker MV2**](https://c
- **Filtering log**
- 
+ 
- Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
+ Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
- _Tracking protection_ (formerly known as _Stealth mode_)
- 
+ 
- There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
+ There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
- _Phishing & malware protection_ is no longer available in the general settings. To protect yourself from malicious websites and scams, enable the appropriate _Security_ filters in the _Filters_ tab.
- 
+ 
## Limitations
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index b1adcc3ff6a..ae7977af510 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/fa/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index d10f3e8722a..e8bf65a8bb2 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -21,19 +21,19 @@ The old beta extension will be renamed to [**AdGuard Ad Blocker MV2**](https://c
- **Filtering log**
- 
+ 
- Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
+ Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
- _Tracking protection_ (formerly known as _Stealth mode_)
- 
+ 
- There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
+ There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
- _Phishing & malware protection_ is no longer available in the general settings. To protect yourself from malicious websites and scams, enable the appropriate _Security_ filters in the _Filters_ tab.
- 
+ 
## Limitations
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index b1adcc3ff6a..ae7977af510 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 7bb7456ce67..fc82ac02649 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ Le nombre maximum de filtres activés simultanément est de **50**.
Les **Règles dynamiques :** un plafond strict de **5 000** règles est imposé, ce qui inclut un maximum de 1 000 règles d'expression régulière.
-Si cette limite est dépassée, seules **5 000 règles converties** seront appliquées dans l'ordre suivant : d'abord à la Liste autorisée, puis aux Règles utilisateur, aux Filtres personnalisés et enfin — au filtre Quick Fixes des corrections rapides.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Les règles converties** sont des règles qui ont été transformées
> au \[format DNR] à l'aide du [convertisseur déclaratif][github-declarative-converter].
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index db1e4075c88..1dbec555aa4 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index b4b6e17a1f1..e01e3b9bbd7 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
Dans cette section, vous pouvez trouver des informations sur votre licence et la gérer :
- Acheter une licence AdGuard pour activer [les fonctionnalités de la version complète](/adguard-for-android/features/free-vs-full)
-- Se connecter à votre compte AdGuard ou saisir la clef de licence pour activer votre licence
-- S'inscrire pour activer votre période d'essai de 7 jours si vous ne l'avez pas encore utilisée
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Rafraîchir le statut de la licence via le menu à trois points (⋮)
- Ouvrir le compte AdGuard pour gérer votre licence
- Réinitialiser votre licence — par exemple, si vous avez atteint la limite d'appareils pour cette licence et que vous souhaitez en appliquer une autre
-
+
## Assistance
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 257552a1d2c..173a0052dbc 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ C'est fait, AdGuard pour Android TV est installé.
- Dans le terminal, saisissez la commande `adb install Downloads/adguard_tv.apk`. Si nécessaire, remplacez `Downloads/adguard_tv.apk` par votre chemin d'accès.
- Attendez un message dans le terminal indiquant l'installation réussie de l'application.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index e7c2922a270..d00ca3ad872 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Vérifie l'authenticité de tous les certificats du domaine en fonction de la po
En définissant `true`, vous autorisez AdGuard à filtrer le trafic envoyé via HTTP/3, la dernière version du protocole HTTP basé sur QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
En définissant `true`, vous activez le filtrage du réseau local.
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index c18d7bcfc8a..ca36dfb4fc7 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ Cet article parle de AdGuard pour Windows, un bloqueur de contenus multifonction
AdGuard pour Windows est un outil facile à utiliser qui bloque les bannières, les pop-ups, les publicités vidéo et les traqueurs agaçants. Mais ce n'est pas tout : il vous aide à réduire le trafic, à charger les pages web plus rapidement et à protéger votre ordinateur contre les sites web indésirables et potentiellement malveillants. AdGuard vous protège également des sites web hameçonneurs et tient vos enfants à l'écart des contenus inappropriés.
-! [Écran principal \*mobile_border] (https://cdn.adtidy.org/content/kb/ad_blocker/windows/overview/home-screen.png)
+
Une fois que vous avez démarré AdGuard pour Windows, vous verrez l'écran principal de l'application. Son détail le plus remarquable est le bouton _activer/désactiver la protection_. Cet écran vous permet également de surveiller les publicités bloquées, les traqueurs et les statistiques sur les menaces, de connaître la version actuelle de l'application ou de la mettre à jour. En outre, quatre autres onglets se trouvent dans le coin supérieur droit : _Paramètres_, _Assistance_, _Licence_ et _À propos_. Chacun de ces points mérite d'être abordé séparément.
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 394f3f04488..3998e7cbfbc 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ Cet article parle de AdGuard pour Windows, un bloqueur de contenus multifonction
_Paramètres_ est la section qui nécessite un maximum d'attention. C'est ici que vous pouvez configurer l'application pour qu'elle réponde pleinement à vos exigences : bloque uniquement ce qui vous dérange, utilise le serveur DNS du fournisseur de confiance, supprime les cookies tiers, etc.
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### Paramètres généraux
+
-Ici, vous pouvez définir la langue et le thème (Sombre ou Clair), activer le lancement d'AdGuard au démarrage du système et les mises à jour automatiques silencieuses, choisir la chaîne de mise à jour et filtrer l'intervalle de vérification des mises à jour. Les paramètres sont également l'endroit où aller si AdGuard pour Windows ne fonctionne pas correctement et si l'équipe d'assistance vous a demandé de [collecter les _journaux de débogage_](/adguard-for-windows/solving-problems/adguard-logs.md).
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-Tout en bas de l'écran, vous trouverez les _Paramètres avancés_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Ad blocking
C'est le module principal d'AdGuard pour Windows qui supprime les publicités des sites web que vous visitez et des applications installées sur votre appareil. Pour filtrer la publicité et les contenus menaçant la vie privée tels que les bannières, les pop-ups ou les traqueurs, AdGuard utilise des filtres différents — des groupes de règles ayant un objectif similaire écrites avec une [syntaxe spéciale](/general/ad-filtering/create-own- filtres). Pour comprendre ce que sont les filtres et comment ils fonctionnent, lisez [cet article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ De nombreux sites web recueillent des informations sur leurs visiteurs, telles q

-Vous pouvez ajuster le fonctionnement du Mode furtif de manière flexible : par exemple, vous pouvez interdire au site web de recevoir la requête de recherche que vous avez utilisée pour le trouver sur Internet, supprimer automatiquement les cookies de tiers et ceux du site web lui-même, et désactiver le partage de localisation dans votre navigateur, qui peut être utilisé pour suivre vos déplacements.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-Pour tout apprendre sur le Mode furtif et ses nombreuses options, [lisez cet article](/general/mode furtif).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Navigation sécurisée
@@ -81,15 +81,15 @@ Dans le module de protection DNS d'AdGuard pour Windows, vous pouvez choisir des

-### Contrôle parental
+### Parental control
-Il existe plusieurs sites web dont l'accès doit être restreint à partir d'un PC utilisé par des enfants. This task is accomplished by _Parental Control_.
+Il existe plusieurs sites web dont l'accès doit être restreint à partir d'un PC utilisé par des enfants. This task is accomplished by _Parental control_.
-
+
-Le module vérifie le contenu des pages web ouvertes dans le navigateur et filtre celles dont le contenu est indésirable pour les enfants : images et textes pour adultes, langage grossier, violence, propagande de drogue, etc. Les paramètres du Contrôle Parental sont protégés par mot de passe pour que l'enfant ne puisse pas contourner les restrictions. Ce module bloque non seulement les directions vers des sites indésirables, mais peut également supprimer des résultats de recherche les liens inappropriés pour les enfants.
+Le module vérifie le contenu des pages web ouvertes dans le navigateur et filtre celles dont le contenu est indésirable pour les enfants : images et textes pour adultes, langage grossier, violence, propagande de drogue, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. Ce module bloque non seulement les directions vers des sites indésirables, mais peut également supprimer des résultats de recherche les liens inappropriés pour les enfants.
-Dans le module _Contrôle Parental_, vous pouvez activer la _Recherche sécurisée_ et gérer la _liste de blocage_ et la _liste d'autorisation_ pour personnaliser le fonctionnement de cette option. Vous pouvez également cocher la case _Bloquer le téléchargement des fichiers exécutables_ pour empêcher votre enfant de télécharger et d'installer des logiciels sur l'ordinateur. Il existe deux autres options dans le module _Contrôle parental_ : vous pouvez sélectionner un utilisateur Windows spécifique à protéger par le _Contrôle parental_ et définir un mot de passe pour protéger les paramètres AdGuard contre toute modification.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. Vous pouvez également cocher la case _Bloquer le téléchargement des fichiers exécutables_ pour empêcher votre enfant de télécharger et d'installer des logiciels sur l'ordinateur. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Assistant de navigateur
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index f57dcbdbc10..134ffc6fae2 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Activez cette fonctionnalité si vous souhaitez qu'AdGuard intercepte automatiqu
Si cette option est activée, AdGuard filtrera les requêtes envoyées sur HTTP/3 en plus d'autres types de requêtes.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Utiliser le mode pilote de redirection
Si cette option est activée, AdGuard intercepte tout le trafic et le redirige vers le proxy local pour un filtrage ultérieur.
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 47946ab9613..dd2828e752c 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ Cet article concerne les filtres que nous créons pour les utiliser dans AdGuard
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 2c9383fe2ed..d689aff3a24 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 9653d566201..43f3a511a5f 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ Les filtres de blocage publicitaire d'AdGuard sont les suivants :
- Filtre de base AdGuard
- Filtre de publicités mobiles AdGuard
- Filtres régionaux divisés par principe linguistique : chinois, néerlandais, français, allemand, japonais, russe, espagnol/portugais, turc et ukrainien
-- AdGuard Quick Fixes filter
### L'objectif de ces filtres
- **Le filtre de base** est conçu pour bloquer les publicités sur les sites web en anglais et ceux pour lesquels il n'existe pas de filtre séparé. Il contient également des règles générales de filtrage qui s'appliquent à tous les sites web quelle que soit la langue
- Le **Filtre de publicités mobiles** bloque les publicités sur les versions mobiles des sites web et dans les applications mobiles. Il n'y a pas de segmentation basée sur la langue
- Les **Filtres régionaux** suivent la même politique que le **Filtre de base**, mais sont limités aux sites web dans certaines langues
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
L'objectif des filtres de blocage des publicités est de bloquer tous les types de publicité sur les sites web, les applications et certains appareils qui peuvent charger des publicités depuis Internet :
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 68db37af985..ae7977af510 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index d10f3e8722a..e8bf65a8bb2 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -21,19 +21,19 @@ The old beta extension will be renamed to [**AdGuard Ad Blocker MV2**](https://c
- **Filtering log**
- 
+ 
- Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
+ Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
- _Tracking protection_ (formerly known as _Stealth mode_)
- 
+ 
- There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
+ There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
- _Phishing & malware protection_ is no longer available in the general settings. To protect yourself from malicious websites and scams, enable the appropriate _Security_ filters in the _Filters_ tab.
- 
+ 
## Limitations
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index 66e29905768..99ad33c5ba7 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 932977c9dff..63b62b62ec8 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Támogatás
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index a66d97addd8..804e4edba4c 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index b1adcc3ff6a..ae7977af510 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1be6a7f2adf..4b0b4fa6fdf 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 43e2156e3c8..a85ffd8b3f8 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index b96d67b5274..a600257d38f 100644
--- a/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/hu/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ Az AdGuard hirdetésblokkoló szűrői a következők:
- AdGuard Alap szűrő
- AdGuard Mobile App Banners szűrő
- Regionális szűrők nyelvi elvek szerint - kínai, holland, francia, német, japán, orosz, spanyol/portugál, török, német, ukrán és orosz
-- AdGuard gyorsjavítások szűrő
### Ezeknek a szűrőknek a célja
- A **Az** alapszűrő célja, hogy blokkolja a hirdetéseket az angol nyelvű webhelyeken és azokon, amelyekhez nincs külön szűrő. Általános szűrési szabályokat is tartalmaz, amelyek nyelvtől függetlenül minden webhelyre vonatkoznak
- A **mobilhirdetések szűrője** blokkolja a hirdetéseket a weboldalak mobilverzióiban és a mobilalkalmazásokban. Nincs nyelvi szegmentálás
- **A** regionális szűrők ugyanazt az irányelvet követik, mint a **Alapszűrő**, de bizonyos nyelvű webhelyekre korlátozva
-- A **Gyorsjavítás szűrő** a kritikus tartalomszűrési problémák gyors megoldására szolgál népszerű weboldalakon, anélkül, hogy frissíteni kellene az MV3 kiegészítőt.
A hirdetésblokkoló szűrők célja, hogy blokkoljanak mindenféle hirdetést olyan webhelyeken, alkalmazásokban és bizonyos eszközökön, amelyek hirdetéseket tölthetnek be az internetről:
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index f8fde863287..4f518d3d32a 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ Il numero massimo di filtri abilitati contemporaneamente è **50**.
**Regole dinamiche:** è imposto un limite massimo di **5.000** regole, che include un massimo di 1.000 regole regex.
-Se questo limite viene superato, verranno applicate solo **5.000 regole convertite** nel seguente ordine: prima la Lista consentita, poi le Regole utente, i Filtri personalizzati e infine — il Filtro Quick Fixes delle correzioni rapide.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> Le **regole convertite** sono regole che sono state trasformate
> in \[formato DNR] utilizzando il [convertitore dichiarativo][github-declarative-converter].
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b4e375a9984..ed4c281028c 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Proxy in uscita
#### Show the Filter DNS requests setting
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index af9862604ed..34574ad6525 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Supporto
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 138a1d19214..66fa9bd444b 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ Done, AdGuard for Android TV is installed.
- In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index 769430f2871..918690f3168 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifica l'autenticità di tutti i certificati per il dominio in base alla Polit
Impostandolo a `true`, consenti ad AdGuard di filtrare il traffico inviato via HTTP/3, l'ultima versione del protocollo HTTP, basata su QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
Impostando `true`, abiliti il filtraggio della rete locale.
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 2c12d9f1e08..02766608846 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ Questo articolo riguarda AdGuard per Windows, un blocca-inserzioni multifunziona
AdGuard per Windows è uno strumento facile da usare che blocca banner, popup, annunci video e tracker fastidiosi. Ma non solo: aiuta a risparmiare traffico, a caricare più velocemente le pagine web e a proteggere il computer da siti web indesiderati e potenzialmente dannosi. AdGuard ti protegge anche dai siti di phishing e tiene lontani i bambini da contenuti inappropriati.
-
+
Una volta avviato AdGuard per Windows, visualizzerai la schermata principale dell'app. Il suo dettaglio più evidente è il pulsante _abilita/disabilita protezione_. Inoltre, su questa schermata, puoi monitorare le statistiche di annunci, tracciatori e minacce bloccati, scoprire la versione corrente dell'app o aggiornarla. Inoltre, sono presenti quattro schede nell'angolo superiore destro: _Impostazioni_, _Supporto_, _Licenza_ e _Informazioni_. Vale la pena parlare di ognuna di queste separatamente.
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 4eb2967a603..6dc5bab8a8f 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ Questo articolo riguarda AdGuard per Windows, un blocca-inserzioni multifunziona
_Impostazioni_ è la sezione che richiede maggiore attenzione. Qui, puoi configurare l'app così che soddisfi pienamente le tue esigenze: blocchi soltanto ciò che ti infastidisce, utilizzi il server DNS del fornitore di fiducia, rimuova i cookie di terze parti e così via.
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### Impostazioni generali
+
-Qui, puoi impostare la lingua e il tema (Scuro o Chiaro), abilitare l'avvio di AdGuard all'avvio del sistema e silenziare gli aggiornamenti automatici, scegliere il canale d'aggiornamento e filtrare l'intervallo di controllo per gli aggiornamenti. Inoltre, Impostazioni è il posto in cui andare se AdGuard per Windows non funziona correttamente e se il team di supporto ti ha richiesto di [raccogliere i _Registri di debug_](/adguard-for-windows/solving-problems/adguard-logs.md).
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-In fondo alla schermata, troverai le _Impostazioni Avanzate_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Ad blocking
Questo è il modulo principale di AdGuard per Windows che rimuove gli annunci dai siti web che visiti e dalle app installate sul tuo dispositivo. Per filtrare i contenuti inserzionistici e che minacciano la privacy, quali banner, popup, o tracciatori, AdGuard utilizza filtri differenti: gruppi di regole con uno scopo simile, scritte con una [sintassi speciale](/general/ad-filtering/create-own-filters). Per comprendere cosa sono i filtri e come funzionano, leggi [questo articolo](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Molti siti web raccolgono informazioni sui propri visitatori, quali i loro indir

-Puoi regolare in modo flessibile il funzionamento della Modalità Stealth: ad esempio, puoi impedire al sito web di ricevere la richiesta di ricerca che hai utilizzato per trovarlo su Internet, eliminare automaticamente i cookie di terze parti e del sito web e disabilitare la condivisione della posizione sul tuo browser, utilizzabile per tracciare la tua posizione.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-Per imparare tutto sulla Modalità Stealth e sulle sue tante opzioni, [leggi questo articolo](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Sicurezza di navigazione
@@ -81,15 +81,15 @@ A partire dalla v7.20, puoi anche aggiungere filtri semplicemente selezionandoli

-### Controllo Parentale
+### Parental control
-Esistono numerosi siti web a cui dovrebbe essere limitato l'accesso da un PC utilizzato da bambini. This task is accomplished by _Parental Control_.
+Esistono numerosi siti web a cui dovrebbe essere limitato l'accesso da un PC utilizzato da bambini. This task is accomplished by _Parental control_.
-
+
-Il modulo controlla i contenuti delle pagine web aperte nel browser e filtra quelle con contenuti indesiderabili per i bambini: immagini e testi per adulti, linguaggio volgare, violenza, sostanze stupefacenti, etc. Le impostazioni del Controllo Parentale sono protette da password, così che i bambini non possano aggirare le limitazioni. Questo modulo non blocca soltanto le indicazioni ai siti indesiderati, ma può anche eliminare i collegamenti inappropriati per i bambini, dai risultati di ricerca.
+Il modulo controlla i contenuti delle pagine web aperte nel browser e filtra quelle con contenuti indesiderabili per i bambini: immagini e testi per adulti, linguaggio volgare, violenza, sostanze stupefacenti, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. Questo modulo non blocca soltanto le indicazioni ai siti indesiderati, ma può anche eliminare i collegamenti inappropriati per i bambini, dai risultati di ricerca.
-Nel modulo _Controllo Parentale_, puoi abilitare la _Ricerca sicura_ e gestire l'_elenco di blocco_ e l'_elenco consentiti_ per personalizzare il funzionamento d quest'opzione. Inoltre, puoi anche spuntare la casella _Blocca download file eseguibili_ per impedire ai tuoi figli di scaricare e installare software sul computer. Esistono ancora altre due opzioni nel modulo _Controllo Parentale_: puoi selezionare un utente di Windows specifico da proteggere con il _Controllo Parentale_ e impostare una password per proteggere le impostazioni di AdGuard dalla modifica.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. Inoltre, puoi anche spuntare la casella _Blocca download file eseguibili_ per impedire ai tuoi figli di scaricare e installare software sul computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index a94a9fbf2b2..dfd3802572e 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Abilita questa funzione se desideri che AdGuard intercetti automaticamente gli U
Se quest'opzione è abilitata, AdGuard filtrerà le richieste inviate via HTTP/3, oltre ad altri tipi di richieste.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Utilizza modalità reindirizzamento driver
Se quest'opzione è abilitata, AdGuard intercetta tutto il traffico e lo reindirizza al server proxy locale per ulteriore filtraggio.
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index e617edec258..c1fb23e9af0 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ Questo articolo riguarda i filtri che creiamo per l'uso in AdGuard e altri softw
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 90a1edbecb9..c73acbbfd57 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 508577a74e3..ad6f45f4c80 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ I filtri di blocco degli annunci di AdGuard includono:
- Filtro di base di AdGuard
- Filtro Inserzioni Mobili di AdGuard
- Filtri regionali divisi per principio linguistico: cinese, olandese, francese, tedesco, giapponese, russo, spagnolo/portoghese, turco e ucraino
-- AdGuard Quick Fixes filter
### Lo scopo di questi filtri
- Il **filtro di base** è progettato per bloccare le inserzioni sui siti web in lingua inglese, nonché quelle per le quali non è presente alcun filtro separato. Inoltre, contiene le regole di filtraggio generali che si applicano a tutti i siti, indipendentemente dalla lingua
- Il **filtro delle Inserzioni Mobili** blocca le inserzioni sulle versioni mobili dei siti web, e sulle app mobili. Non esiste alcuna segmentazione basata sulla lingua
- I **filtri regionali** seguono la stessa politica del **filtro di base**, ma si limitano ai siti web in certe lingue
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
L'obiettivo dei filtri di blocco delle inserzioni è bloccare ogni tipo di inserzione sui siti web, le applicazioni, e certi dispositivi capaci di caricare inserzioni da Internet:
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 6f67f04aac9..447b4facc3b 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ Manifest V3 では、拡張子ごとに静的ルールと正規表現ルール
**動的ルール:** ルールの厳密な上限は**5,000**で、これには最大1,000個の正規表現ルールが含まれます。
-この制限を超えた場合、**5,000の変換されたルール**のみが次の順序で適用されます:最初にホワイトリスト、次にユーザールール、カスタムフィルタ、最後に臨時修正フィルタ。
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **変換されたルール**は、[宣言的コンバータ][github-declarative-converter]を使って
> \[DNR形式]に変換されたルールです。
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index 8fc4df7e7e6..b54df7c0e34 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### アウトバウンドプロキシ
#### Show the Filter DNS requests setting
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index e85c34240fd..97ec2c1b941 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## サポート
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 2735ff815be..3df7d66e56c 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ Done, AdGuard for Android TV is installed.
- In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index 8c884a05a2f..a3875b2a72d 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Chrome Certificate Transparency Policy(証明書透過性ポリシー)に基
`true` を設定すると、AdGuardがHTTP/3(QUICに基づくHTTPプロトコルの最新バージョン)経由で送信されるトラフィックをフィルタリングできるようになります。
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
`true` を設定すると、ローカル ネットワークフィルタリングが有効になります。
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 9ceda477910..ee8aecf8cd7 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ sidebar_position: 1
AdGuard for Windows は、迷惑なバナー、ポップアップ、ビデオ広告、トラッカーをブロックする使いやすいツールです。 しかし、それだけではありません。データ通信量を節約し、Web ページの読み込みを高速化し、望ましくない、または悪意のある可能性のある Web サイトからコンピューターを保護してくれます。 また、AdGuard はフィッシング Web サイトからユーザーを保護し、お子様を不適切なコンテンツから守ります。
-
+
AdGuard for Windows を起動すると、アプリのホーム画面が表示されます。 最も目立つ点は、保護を有効/無効にするボタンです。 また、この画面では、ブロックされた広告、トラッカー、脅威の数を確認したり、アプリの現在のバージョンを確認したり、アプリを更新したりすることもできます。 さらに、右上隅には「_設定_」「_サポート_」「_ライセンス_」「_バージョン情報_」の4つのタブがあります。 これらについてはそれぞれ個別に、専用記事で紹介しております。
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index a32403c478a..bb25a168c6d 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ sidebar_position: 2
「設定」は最も注意する価値のあるセクションです。 ここでは、アプリをご自身のニーズに合わせて設定することができます。気になるものだけをブロックし、信頼できるプロバイダのDNSサーバーを使用し、サードパーティCookieの削除を有効にすることなどができます。
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### 一般設定
+
-ここでは、言語とカラーテーマ(ダーク・ライト)の設定、システム起動時のAdGuardの起動と自動アップデートの有効化、アップデートチャネルの選択、フィルタ更新チェック間隔の指定などを行うことができます。 また、AdGuard for Windows が正常に動作せず、サポートチームから[「デバッグログ」を収集する](/adguard-for-windows/solving-problems/adguard-logs.md)ように依頼された場合も、「設定」が役に立ちます。
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-画面の一番下に「高度な設定」があります。 Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Ad blocking
これは AdGuard for Windows のメインモジュールで、アクセスしたウェブサイトやデバイスにインストールされたアプリから広告を削除します。 AdGuard は、バナー、ポップアップ、トラッカーなどのような、広告やプライバシーを脅かすコンテンツをフィルタリングするために、さまざまなフィルタ([特別な構文](/general/ad-filtering/create-own-filters)で記述され、同様の目的を持つルールグループ)を使用します。 フィルタとは何か、どのように機能するのかについては、[こちらの記事](/general/ad-filtering/how-ad-blocking-works)をお読みください。
@@ -46,9 +46,9 @@ In the Ad blocking module you can:

-トラッキング防止の機能を柔軟に微調整することができます。例えば、インターネット上でウェブサイトを見つけるために使用した検索要求の受信を禁止したり、サードパーティとウェブサイト独自のCookieの両方を自動的に削除したり、居場所を追跡するために使用できるブラウザの位置情報共有を無効にしたりすることができます。
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-トラッキング防止とその多くのオプションについて知るには、[こちらの記事](/general/stealth-mode)をお読みください。
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### ブラウジング・セキュリティ
@@ -81,15 +81,15 @@ v7.20 以降では、信頼できる組み込みフィルタリストからフ

-### ペアレンタルコントロール
+### Parental control
-子供が使用するパソコンで、アクセスを制限する必要があるウェブサイトは何個もあるでしょう。 This task is accomplished by _Parental Control_.
+子供が使用するパソコンで、アクセスを制限する必要があるウェブサイトは何個もあるでしょう。 This task is accomplished by _Parental control_.
-
+
-このモジュールは、ブラウザで開かれたウェブページの内容をチェックし、子供にとって好ましくない内容(大人向けの画像やテキスト、下品な言葉、暴力、薬物の宣伝など)のものをフィルタリングします。 ペアレンタルコントロールの設定はパスワードで保護されているため、子供が自分で制限をオフにすることはできません。 このモジュールは、不適切なサイトへの誘導をブロックするだけでなく、子供に不適切なリンクを検索結果から削除することもできます。
+このモジュールは、ブラウザで開かれたウェブページの内容をチェックし、子供にとって好ましくない内容(大人向けの画像やテキスト、下品な言葉、暴力、薬物の宣伝など)のものをフィルタリングします。 Parental control settings are password-protected so that the child is not able to go round the restrictions. このモジュールは、不適切なサイトへの誘導をブロックするだけでなく、子供に不適切なリンクを検索結果から削除することもできます。
-ペアレンタルコントロールモジュールでは、「_セーフサーチ_」を有効にし、「_ブラックリスト_」と「_ホワイトリスト_」を管理して、この機能の動作をカスタマイズすることができます。 「実行形式ファイルのダウンロードをブロック」を有効にしますと、お子様のコンピュータへのソフトウェアのダウンロードとインストールを防ぎます。 「_ペアレンタルコントロール_」モジュールにはさらに 2 つのオプションがあります。_ペアレンタルコントロール_で保護対象の特定の Windows ユーザーを指定するオプションと、AdGuard 設定が変更されないようにパスワードを設定するオプションです。
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. 「実行形式ファイルのダウンロードをブロック」を有効にしますと、お子様のコンピュータへのソフトウェアのダウンロードとインストールを防ぎます。 There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### ブラウザアシスタント
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 699fb262ef1..9a649a875e6 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ AdGuard に購読 URL (例: `abp:subscribe` など) を自動的に傍受させ
このオプションを有効にすると、AdGuard は、他のリクエストタイプに加えて、HTTP/3 で送信されたリクエストもフィルタリングします。
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### リダイレクト・ドライバ・モードを使用する
このオプションを有効にすると、AdGuard はすべてのトラフィックを傍受し、さらにフィルタリングするためにローカルプロキシサーバーにリダイレクトします。
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 5d932279f1c..96e635eac18 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ sidebar_position: 2
- **実験的フィルタ**は、潜在的に競合を引き起こし、ウェブサイトの作業を混乱させる可能性のある新しいフィルタリングルールをテストするために使用されています。 これらのルールが問題なく動けば、メインフィルタに追加されます。 [含まれているルールを見る](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **AdGuard モバイル広告フィルタ**は、モバイルデバイス上の広告をブロックします。 すべての既知のモバイル広告ネットワークが含まれています。 [含まれているルールを見る](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **AdGuard DNSフィルタ**は、数フィルタ(AdGuardベースフィルタ、SNS用フィルタ、スパイウェアフィルタ、モバイル広告フィルタ、EasyList、EasyPrivacy)で構成され、DNSレベルの広告ブロックとの互換性が向上するように簡素化されたフィルタです。 このフィルタは[AdGuard DNS](https://adguard-dns.io/kb)サーバーでも使用され、広告やトラッキングをブロックします。 [含まれているルールを見る](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **AdGuard 臨時修正フィルタ**は、MV3対応版 AdGuard ブラウザ拡張機能をアップデートする必要なく、人気Webサイトでのコンテンツフィルタリング問題をすばやく解決するためのフィルタです。 [含まれているルールを見る](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard フィルタポリシー
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index f82b8545920..6f29f852590 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index f2fb23d3b27..a57eb05bfd7 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuardの広告ブロックフィルタには以下が含まれます:
- AdGuard ベースフィルタ
- AdGuard モバイル広告フィルタ
- 言語ごとに分けられた地域フィルタ:中国語、オランダ語、フランス語、ドイツ語、日本語、ロシア語、スペイン語/ポルトガル語、トルコ語、ウクライナ語。例「AdGuard 日本語フィルタ」
-- AdGuard Quick Fixes filter
### これらのフィルタの目的
- 「**AdGuard ベースフィルタ**」は、英語のウェブサイトや、専用フィルタがないウェブサイトの広告をブロックするように設計されています。 言語に関係なくすべてのサイトに適用される一般的なフィルタリングルールも含まれています。
- 「**AdGuard モバイル広告フィルタ**」はウェブサイトのモバイル版の広告とモバイルアプリ内の広告をブロックします。 言語によるセグメンテーション・差別化はありません。
- **地域別フィルタ**(言語特化フィルタ)は、 **AdGuard ベースフィルタ**と同じポリシーに従いますが、特定の言語のウェブサイトに限定されます。
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
広告ブロックフィルタの目的は、インターネットから広告を読み込むことができるウェブサイト、アプリケーション、特定のデバイス上であらゆる種類の広告をブロックすることです。ブロックする広告の種類:
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 3c3ac99413d..2a18d937ba5 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ AdGuard MV3 확장 프로그램은 광고와 추적기를 효과적으로 차단
**동적 규칙:** 최대 1,000개의 정규식 규칙을 포함한 **5,000** 규칙의 엄격한 한도가 적용됩니다.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **변환된 규칙**은 [선언적 변환기][github-declarative-converter]를 이용해 \[DNR 형식]으로 변환된 규칙입니다.
> 변환 과정에서 일부 규칙들은 다른 규칙의 (`$badfilter`)를 덮어쓸 수도 있고, (`$removeparam`)와 결합될 수도 있는데, 그 결과 순서가 약간 다른 규칙 목록이 생성됩니다.
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index f08d309e3dc..eeffed336a0 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index fd2a55b6c69..361f54f098f 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## 고객 지원
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 2735ff815be..3df7d66e56c 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ Done, AdGuard for Android TV is installed.
- In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/firefox-certificates.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/firefox-certificates.md
index ccfb602441a..1d74b5b9a3f 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/firefox-certificates.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/firefox-certificates.md
@@ -11,7 +11,7 @@ This article is about AdGuard for Android, a multifunctional ad blocker that pro
AdGuard가 Firefox에서 HTTPS 트래픽을 성공적으로 필터링하기 위해서는 브라우저가 AdGuard의 인증서를 신뢰해야 합니다. Firefox 버전에 따라 브라우저가 인증서를 신뢰하도록 하는 방법은 다릅니다.
-### Method 1
+### 방법 1
:::note
@@ -35,7 +35,7 @@ Firefox Nightly가 AdGuard 인증서를 신뢰하도록 하려면 다음 단계
1. Toggle **Use third party CA certificates**.
-### Method 2
+### 방법 2
:::note
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index cd1af3644de..55923fff7f0 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Chrome 인증서 투명성 정책에 따라 도메인의 모든 인증서를 확
`true`로 설정하면 AdGuard가 QUIC 기반의 최신 버전의 HTTP 프로토콜인 HTTP/3을 통해 전송되는 트래픽을 필터링할 수 있습니다.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
`true`로 설정하면 로컬 네트워크 필터링이 활성화됩니다.
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index d2108030475..9ae38242e98 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ sidebar_position: 1
Windows용 AdGuard는 성가신 배너, 팝업, 동영상 광고 및 트래커를 차단하는 사용하기 쉬운 도구입니다. 트래픽을 절약하고, 웹 페이지를 더 빠르게 로드하며, 악성 웹사이트로부터 컴퓨터를 보호하는 데 도움이 됩니다. 또한 AdGuard는 피싱 웹사이트로부터 사용자를 보호하고 자녀가 부적절한 콘텐츠를 보지 못하도록 차단합니다.
-
+
Windows용 AdGuard를 시작하면 앱의 기본 화면이 표시됩니다. 가장 눈에 띄는 것은 **보호 기능 활성화/비활성화** 버튼입니다. 또한 이 화면에서 차단된 광고, 추적기 및 위협 통계를 모니터링하고 앱의 현재 버전을 확인하거나 업데이트할 수 있습니다. 또한 오른쪽 상단에는 4개의 탭(**설정**, **고객 지원**, **라이선스**, **정보**)이 있습니다. 각 탭에 대해 개별적으로 설명하겠습니다.
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index d7f6eb833b3..48365e6bfb1 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ sidebar_position: 2
**설정**은 가장 중요한 섹션입니다. 여기에서 특정 항목 또는 사이트 차단, 신뢰할 수 있는 제공업체의 DNS 서버 사용, 타사 쿠키 삭제 등 요구사항에 따라 앱을 설정할 수 있습니다.
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### 일반 설정
+
-여기에서 언어와 테마(다크 테마 또는 라이트 테마)를 설정하고, 시스템 시작 시 AdGuard를 실행하고 자동 업데이트를 무음으로 설정할 수 있습니다. 업데이트 채널과 업데이트 확인 간격 필터를 선택할 수도 있습니다. 또한 Windows용 AdGuard가 제대로 작동하지 않아 지원팀에서 [**디버그 로그 수집**](/adguard-for-windows/solving-problems/adguard-logs.md)을 요청하는 경우 설정으로 이동합니다.
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-화면 맨 아래에는 **고급 설정**이 있습니다. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Ad blocking
광고 차단기는 사용자가 방문하는 웹사이트와 앱에서 광고를 제거하는 Windows용 AdGuard의 메인 모듈입니다. 배너, 팝업 또는 추적기와 같은 광고 및 개인정보를 위협하는 콘텐츠를 필터링하기 위해 AdGuard는 다양한 필터([특수 구문](/general/ad-filtering/create-own-filters)으로 작성된 유사한 목적을 가진 규칙 그룹)를 사용합니다. 필터가 무엇인지, 어떻게 작동하는지 이해하려면 [이�글](/general/ad-filtering/how-ad-blocking-works)을 참조하세요.
@@ -46,9 +46,9 @@ In the Ad blocking module you can:

-스텔스 모드의 작업을 유연하게 조정할 수 있습니다. 예를 들어, 인터넷에서 웹사이트를 찾을 때 사용한 검색 요청을 해당 웹사이트가 수신하지 못하도록 하거나, 타사 쿠키와 웹사이트 자체 쿠키를 자동으로 삭제하거나, 내 위치를 추적하는 데 사용할 수 있는 브라우저의 위치 공유를 비활성화할 수 있습니다.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-스텔스 모드에 대해 자세히 알아보려면 [이 글](/general/stealth-mode)을 참조하세요.
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### 브라우징 보안
@@ -81,15 +81,15 @@ v7.20부터는 미리 구축된 신뢰할 수 있는 필터 목록에서 필터

-### 자녀 보호
+### Parental control
-자녀가 사용하는 컴퓨터에서 액세스하지 못하도록 제한해야 하는 사이트가 몇 가지 있습니다. This task is accomplished by _Parental Control_.
+자녀가 사용하는 컴퓨터에서 액세스하지 못하도록 제한해야 하는 사이트가 몇 가지 있습니다. This task is accomplished by _Parental control_.
-
+
-이 모듈은 브라우저에서 열린 웹페이지의 콘텐츠를 확인하고 성인용 이미지 및 텍스트, 거친 언어, 폭력, 마약 선전 등 어린이에게 바람직하지 않은 콘텐츠가 포함된 웹페이지를 필터링합니다. 자녀 보호 설정은 자녀가 제한을 우회할 수 없도록 비밀번호로 보호됩니다. 이 모듈은 원치 않는 사이트로 연결되는 경로를 차단할 뿐만 아니라 검색 결과에서 어린이에게 부적절한 링크를 삭제할 수도 있습니다.
+이 모듈은 브라우저에서 열린 웹페이지의 콘텐츠를 확인하고 성인용 이미지 및 텍스트, 거친 언어, 폭력, 마약 선전 등 어린이에게 바람직하지 않은 콘텐츠가 포함된 웹페이지를 필터링합니다. Parental control settings are password-protected so that the child is not able to go round the restrictions. 이 모듈은 원치 않는 사이트로 연결되는 경로를 차단할 뿐만 아니라 검색 결과에서 어린이에게 부적절한 링크를 삭제할 수도 있습니다.
-**자녀 보호** 모듈에서 **안전 검색**을 활성화하고 **차단 목록** 및 **허용 목록**을 관리하여 이 옵션의 작동 방식을 사용자 지정할 수 있습니다. 자녀가 컴퓨터에 소프트웨어를 다운로드하고 설치하지 못하도록 **실행 파일 다운로드 차단** 확인란을 선택할 수도 있습니다. **자녀 보호** 모듈에서 **자녀 보호 기능**으로 보호할 특정 Windows 사용자를 선택하고 AdGuard 설정을 변경하지 못하도록 보호할 암호를 설정할 수 있습니다.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. 자녀가 컴퓨터에 소프트웨어를 다운로드하고 설치하지 못하도록 **실행 파일 다운로드 차단** 확인란을 선택할 수도 있습니다. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### 브라우저 어시스턴트
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index be2961cf0af..ab7614e0f8d 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ AdGuard가 필터 구독 URL(예: `abp:subscribe` 등)을 자동으로 가로채
이 옵션을 활성화하면 AdGuard는 다른 요청 유형과 함께 HTTP/3을 통해 전송된 요청을 필터링합니다.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### 리디렉션 드라이버 모드 사용
이 옵션을 활성화하면 AdGuard가 모든 트래픽을 가로채서 추가 필터링을 위해 로컬 프록시 서버로 리디렉션합니다.
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index a6d46f4f6e8..eda2b8e8be6 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ sidebar_position: 2
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 2fc62d64d52..6b2c64f5632 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 9f5b929188d..189c69b29ed 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard 광고 차단 필터에는 다음이 포함됩니다.
- AdGuard 베이스 필터
- AdGuard 모바일 광고 필터
- 언어 원칙에 따라 구분된 지역 필터: 중국어, 네덜란드어, 프랑스어, 독일어, 일본어, 러시아어, 스페인어/포르투갈어, 터키어, 우크라이나어
-- AdGuard Quick Fixes filter
### 이러한 필터의 목적
- **베이스 필터**는 영어 웹사이트 및 별도의 필터가 없는 웹사이트의 광고를 차단하도록 설계되었습니다. 또한 언어에 관계없이 모든 사이트에 적용되는 일반 필터링 규칙이 포함되어 있습니다.
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. 언어에 따른 세분화가 없습니다.
- **지역 필터**는 **베이스 필터**와 동일한 정책을 따르지만 특정 언어의 웹사이트로 제한됩니다.
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
광고 차단 필터의 목표는 인터넷에서 광고를 로드할 수 있는 웹사이트, 애플리케이션 및 특정 디바이스에서 모든 유형의 광고를 차단하는 것입니다.
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/general/license/transfer.md b/i18n/ko/docusaurus-plugin-content-docs/current/general/license/transfer.md
index 2a3d09d89db..6dfa156c16e 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/general/license/transfer.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/general/license/transfer.md
@@ -9,17 +9,17 @@ sidebar_position: 4
### 기기 연결을 해제하는 방법
-#### Method 1
+#### 방법 1
-On the device that you want to unbind, open the AdGuard app and click *Reset license* or *Log out*.
+연결을 해제하려는 기기에서 AdGuard 앱을 열고 *라이선스 초기화* 또는 *로그아웃*을 클릭합니다.
-#### Method 2
+#### 방법 2
-As an alternative, you can remove the device in your AdGuard account:
+또는 AdGuard 계정에서 기기를 제거할 수 있습니다.
-1. Log in to your [AdGuard account](https://adguardaccount.com/).
+1. [AdGuard 계정](https://adguardaccount.com/)에 로그인합니다.
-1. Open *AdGuard Ad Blocker* tab.
+1. *AdGuard 광고 차단기* 탭을 엽니다.
@@ -31,7 +31,7 @@ As an alternative, you can remove the device in your AdGuard account:
-After you have unbound the number of devices you need, you will be able log in on new devices. The license will become bound to them.
+필요한 수의 기기에서 연결을 해제한 후에는 새로운 기기에서 로그인할 수 있습니다. 라이선스가 해당 기기에 연결됩니다.
## 다른 AdGuard 계정으로 라이선스를 이전하는 방법{#transferaccount}
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index d10f3e8722a..e8bf65a8bb2 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -21,19 +21,19 @@ The old beta extension will be renamed to [**AdGuard Ad Blocker MV2**](https://c
- **Filtering log**
- 
+ 
- Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
+ Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
- _Tracking protection_ (formerly known as _Stealth mode_)
- 
+ 
- There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
+ There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
- _Phishing & malware protection_ is no longer available in the general settings. To protect yourself from malicious websites and scams, enable the appropriate _Security_ filters in the _Filters_ tab.
- 
+ 
## Limitations
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index b1adcc3ff6a..ae7977af510 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/no/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 68db37af985..ae7977af510 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/no/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 68db37af985..ae7977af510 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/pl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index d8c7d56ee6d..13ed454738f 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ O número máximo de filtros ativados simultaneamente é **50**.
**Regras dinâmicas:** é imposto um limite estrito de **5.000** regras, que inclui um máximo de 1.000 regras regex.
-Se esse limite for excedido, apenas **5.000 regras convertidas** serão aplicadas na seguinte ordem: primeiro a lista de permissões, depois as Regras de usuário, filtros personalizados e, finalmente, o filtro Quick Fixes.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Regras convertidas** são regras que foram transformadas
> para o \[formato DNR] usando o [conversor declarativo][github-declarative-converter].
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index c1d4257d498..09176bb9334 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ Se esta configuração estiver ativada, o AdGuard filtrará as solicitações en
**Sobre o HTTP/3**: Esta é a versão mais recente do protocolo HTTP, baseado em QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Proxy de saída
#### Mostrar a configuração Filtrar solicitações de DNS
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 44b3da28daf..8ccc2ca23fb 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Suporte
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 2755a1108db..0ef96ed6589 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ Pronto, o AdGuard para Android TV está instalado.
- No terminal, digite o comando ’adb install Downloads/adguard_tv.apk’. Se necessário, substitua `Downloads/adguard_tv.apk` pelo seu caminho em que se encontra o arquivo baixado.
- Aguarde uma mensagem no terminal indicando que a instalação do aplicativo foi bem-sucedida.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dd14ce900ca..cdad57a981b 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifica a autenticidade de todos os certificados do domínio com base na polít
Ao definir `true`, você permite que o AdGuard filtre o tráfego enviado por HTTP/3, a versão mais recente do protocolo HTTP baseado em QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
Ao definir `true`, você habilita a filtragem de rede local.
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index d0a626700dd..fc2947a5970 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ Este artigo aborda o AdGuard para Windows, um bloqueador de anúncios multifunci
AdGuard para Windows é uma ferramenta fácil de usar que bloqueia banners, pop-ups, anúncios em vídeo e rastreadores irritantes. Mas isso não é tudo: ajuda a economizar tráfego, carregar páginas da web com mais rapidez e proteger seu computador contra sites indesejáveis e potencialmente maliciosos. O AdGuard também protege você contra sites de phishing e mantém seus filhos longe de conteúdo impróprio.
-
+
Depois de iniciar o AdGuard para Windows, você verá a tela principal do aplicativo. Seu detalhe mais notável é o botão _ativar/desativar proteção_. Além disso, nesta tela você pode monitorar anúncios bloqueados, rastreadores e estatísticas de ameaças, descobrir a versão atual do aplicativo ou atualizá-lo. Além disso, existem quatro guias no canto superior direito: _Configurações_, _Suporte_, _Licença_ e _Sobre_. Vale a pena falar sobre cada um deles separadamente.
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 86d64ab0e62..351b97b008e 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ Este artigo aborda o AdGuard para Windows, um bloqueador de anúncios multifunci
_Configurações_ é a seção que requer mais atenção. É aqui que você pode configurar o aplicativo para que atenda plenamente às suas necessidades: bloqueia apenas o que incomoda, usa o servidor DNS do provedor confiável, remove cookies de terceiros e assim por diante.
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### Configurações gerais
+
-Aqui você pode definir o idioma e o tema (escuro ou claro), ativar o lançamento do AdGuard na inicialização do sistema e atualizações automáticas silenciosas, escolher o canal de atualização e filtrar o intervalo de verificação de atualização. Além disso, você pode recorrer às configurações se o AdGuard para Windows não estiver funcionando corretamente e o Suporte ao cliente solicitar que você [colete _Logs de depuração_](/adguard-for-windows/solving-problems/adguard-logs.md).
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-Na parte inferior da tela, você encontrará as _Configurações avançadas_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Ad blocking
Este é o módulo principal do AdGuard para Windows que remove anúncios dos sites que você visita e dos aplicativos instalados no seu dispositivo. Para filtrar publicidade e conteúdo que ameaça a privacidade como banners, pop-ups ou rastreadores, o AdGuard usa filtros diferentes, ou seja, grupos de regras com finalidade semelhante escritas com uma [sintaxe especial](/general/ad-filtering/create-own-filters). Para entender o que são filtros e como funcionam, leia [este artigo](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Muitos sites coletam informações sobre seus visitantes, como endereços IP, in

-Você pode ajustar de forma flexível o funcionamento do Modo Sigiloso: por exemplo, você pode proibir o site de receber a solicitação de pesquisa que você usou para encontrá-lo na Internet, excluir automaticamente os cookies de terceiros e do próprio site e desativar o compartilhamento de localização no seu navegador, que pode ser usado para rastrear sua localização real.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-Para saber tudo sobre o Modo Sigiloso e suas diversas opções, [leia este artigo](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Segurança da navegação
@@ -81,15 +81,15 @@ A partir da versão 7.20, você também pode adicionar filtros selecionando-os a

-### Controle parental
+### Parental control
-Existem vários sites aos quais o acesso deve ser restringido a partir de um PC utilizado por crianças. This task is accomplished by _Parental Control_.
+Existem vários sites aos quais o acesso deve ser restringido a partir de um PC utilizado por crianças. This task is accomplished by _Parental control_.
-
+
-O módulo verifica o conteúdo das páginas web abertas no navegador e filtra aquelas com conteúdo indesejável para crianças: imagens e textos para adultos, linguagem grosseira, violência, propaganda de drogas, etc. As configurações do Controle Parental são protegidas por senha para que a criança não consiga contornar as restrições. Este módulo não apenas bloqueia direções para sites indesejáveis, mas também pode excluir links inadequados para crianças dos resultados da pesquisa.
+O módulo verifica o conteúdo das páginas web abertas no navegador e filtra aquelas com conteúdo indesejável para crianças: imagens e textos para adultos, linguagem grosseira, violência, propaganda de drogas, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. Este módulo não apenas bloqueia direções para sites indesejáveis, mas também pode excluir links inadequados para crianças dos resultados da pesquisa.
-No módulo _Controle parental_ você pode ativar a _Pesquisa segura_ e gerenciar a _lista de bloqueio_ e a _lista de permissões_ para personalizar o funcionamento desta opção. Você também pode marcar a caixa _Bloquear download de arquivos executáveis_ para evitar que seu filho baixe e instale software no computador. Existem mais duas opções no módulo _Controle Parental_: você pode selecionar um usuário específico do Windows para ser protegido pelo _Controle Parental_ e definir uma senha para proteger as configurações do AdGuard contra alterações.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. Você também pode marcar a caixa _Bloquear download de arquivos executáveis_ para evitar que seu filho baixe e instale software no computador. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Assistente de navegador
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index fb43e4e2794..015afe010b8 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Ative este recurso se você quiser que o AdGuard intercepte automaticamente URLs
Se esta opção estiver ativada, o AdGuard filtrará as solicitações enviadas por HTTP/3, além de outros tipos de solicitação.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Usar modo de redirecionamento de driver
Se esta opção estiver ativada, o AdGuard intercepta todo o tráfego e o redireciona para o servidor proxy local para posterior filtragem.
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index c27528967a4..271cd638410 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ Este artigo é sobre os filtros que criamos para usar no AdGuard e outros softwa
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 115a95e346a..569ac78c2ac 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ Este modificador permite que você restrinja a abrangência da regra a um aplica
Para Mac, você pode descobrir o ID do pacote ou o nome do processo do aplicativo visualizando os detalhes da solicitação no registro de filtragem.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — uma regra para bloquear solicitações que correspondem à máscara especificada e são enviadas do aplicativo `org.example.app` para Android.
@@ -429,9 +442,23 @@ Se você quer que a regra não seja aplicada a certos aplicativos, comece o nome
- `||baddomain.com^$app=~org.example.app` — uma regra para bloquear solicitações que correspondem à máscara especificada e são enviadas de qualquer aplicativo, exceto o `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — o mesmo que acima, mas agora dois aplicativos estão excluídos: `org.example.app1` e `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Os aplicativos no valor do modificador não podem ter um wildcard, por exemplo, `$app=com.*.music`. As regras com tal modificador são consideradas inválidas.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Os aplicativos no valor do modificador não podem ter um wildcard, por exemplo,
- Apenas o AdGuard para Windows, Android é tecnicamente capaz de usar regras com o modificador `$app`.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. O modificador `$domain` contém apenas domínios excluídos, por exemplo, `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` bloqueará cookies para todas as solicitações para e de `example.org` e `example.com`.
-- `*$document,domain=example.org|example.com` bloqueará todas as solicitações para e a partir de `example.org` e `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
-Nos exemplos a seguir, implica-se que as solicitações são enviadas de `http://example.org/page` (o referenciador) e a URL de destino é `http://targetdomain.com/page`.
+In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domínio=example.org` será combinado, pois corresponde ao domínio do referenciador.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domínio=targetdomain.com|~example.org` não será correspondente porque o domínio de referência foi explicitamente excluído.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -634,13 +647,13 @@ Go to [rules priorities](#rule-priorities) for more details.
**Examples**
```adblock
-! a regra de bloqueio bloqueará todas as solicitações apesar da regra de exceção
+! blocking rule will block all requests despite of the exception rule
||example.org^$important
@@||example.org^
```
```adblock
-! se a regra de exceção também tiver o modificador `$important`, ela prevalecerá e as solicitações não serão bloqueadas
+! if the exception rule also has `$important` modifier, it will prevail and requests won't be blocked
||example.org^$important
@@||example.org^$important
```
@@ -757,7 +770,7 @@ Proíbe o Google Chrome de enviar sua versão e informações de modificação c
To be considered as such, a third-party request should meet one of the following conditions:
-1. Its referrer is not a subdomain of the target domain or vice versa. Por exemplo, uma solicitação para `subdomain.example.org` de `example.org` não é uma solicitação de terceiros
+1. Its referrer is not a subdomain of the target domain or vice versa. For example, a request to `subdomain.example.org` from `example.org` is not a third-party request
1. Its `Sec-Fetch-Site` header is set to `cross-site`
:::
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 062546b1341..59c75176924 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ Os filtros de bloqueio de anúncios AdGuard incluem:
- Filtro base do AdGuard
- Filtro de anúncios para dispositivos móveis do AdGuard
- Filtros regionais divididos por idiomas: chinês, holandês, francês, alemão, japonês, russo, espanhol, português, turco e ucraniano
-- AdGuard Quick Fixes filter
### O propósito desses filtros
- O **Filtro base** foi projetado para bloquear anúncios em sites em inglês e aqueles para os quais não há filtro separado. Ele também contém regras gerais de filtragem que se aplicam a todos os sites, independentemente do idioma
- O **Filtro de anúncios para dispositivos móveis** bloqueia anúncios em versões móveis de sites e em celulares e tablets. Não há segmentação com base no idioma
- Os **Filtros regionais** seguem a mesma política do **Filtro base**, mas são limitados a sites em determinados idiomas
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
O objetivo dos filtros de bloqueio de anúncios é bloquear todos os tipos de publicidade em sites, aplicativos e determinados dispositivos que podem carregar anúncios da Internet:
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 89bbd40aee8..a787c869cbf 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Assistência
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 673e4820f4e..02232500ef6 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ Este artigo aborda o AdGuard para Windows, um bloqueador de anúncios multifunci
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 0be39a2f537..820856c851c 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ Este artigo aborda o AdGuard para Windows, um bloqueador de anúncios multifunci
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 993c0f482bd..44019e62225 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 74439443934..11a6565bdd5 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ Este artigo é sobre os filtros que criamos para usar no AdGuard e em outros sof
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 7bb3ecef552..a4c3a21e8fa 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1eb33e18724..595f075fc31 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ Numărul maxim de filtre activate simultan este **50**.
**Regulile dinamice:** o limită strictă de **5.000** reguli este impusă, care include un maxim de 1.000 de reguli regex.
-Dacă această limită este depășită, vor fi aplicate doar **5.000 de reguli convertite** în următoarea ordine: mai întâi Allowlist, apoi Reguli utilizator, filtre personalizate și, în final — filtre Quick Fixes.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Reguli convertite** sunt reguli care au fost transformate
> din \[format DNR] folosind [convertorul declarativ][github-declarative-converter].
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index 5957222b5bc..6519fb020ed 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 2fbdce9301d..47c5bd78480 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 804cd501f08..63a45ac9073 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ Finalizat, AdGuard pentru Android TV este instalat.
- În terminal, introduceți comanda `adb install Downloads/adguard_tv.apk`. Dacă este necesar, înlocuiți `Downloads/adguard_tv.apk` cu calea dvs.
- Așteptați un mesaj în terminal care să indice instalarea reușită a aplicației.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index 26043c4011e..4575a168ac7 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifică autenticitatea tuturor certificatelor pentru domeniu pe baza Politicii
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
Prin setarea `true`, activați filtrarea rețelei locale.
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 0485a96ff55..0abe0dec8db 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ Acest articol se referă la AdGuard pentru Windows, un blocant de reclame multif
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index eb985537c31..2a0245bad9a 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ Acest articol se referă la AdGuard pentru Windows, un blocant de reclame multif
_Setările_ este secțiunea care necesită cea mai mare atenție. Aici poți configura aplicația astfel încât să corespundă pe deplin cerințelor tale: blochează doar ceea ce te deranjează, utilizează serverul DNS al furnizorului de încredere, șterge cookie-urile ale terților și așa mai departe.
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### Setări Generale
+
-Aici poți seta limba și tema (Întuneric sau Lumină), activați lansarea AdGuard la pornirea sistemului și actualizările automate silențioase, alege canalul de actualizare și intervalul de verificare a actualizărilor. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-În partea de jos a ecranului vei găsi _Setările Avansate_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Ad blocking
Acesta este modul principal al AdGuard pentru Windows care elimină reclamele de pe site-urile pe care le vizitezi și din aplicațiile instalate pe dispozitivul tău. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). Pentru a înțelege ce sunt filtrele și cum funcționează, citește [acest articol](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Multe site-uri web colectează informații despre vizitatorii lor, cum ar fi adr

-Poți ajusta flexibil funcționarea Modul invizibil: de exemplu, poți interzice site-ului să primească cererea de căutare folosită pentru a-l găsi pe Internet, să ștergi automat cookie-urile atât ale terților, cât și ale site-ului web și să dezactivezi partajarea locației în browserul tău care poate fi folosită pentru a-ți urmări locația.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-Pentru a învăța totul despre Modul invizibil și opțiunile sale, [citește acest articol](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Securitate la navigare
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Asistent Browser
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 9e05e081c20..1192e66c984 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Activați această opțiune dacă doriți ca AdGuard să intercepteze automat UR
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Utilizați modul driver de redirecționare
Dacă această opțiune este activată, AdGuard intercepta tot traficul și îl va redirecționa către serverul proxy local pentru filtrarea ulterioară.
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 1ed289a64e9..fae2c09c155 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ Acest articol se referă la filtrele pe care le creăm pentru a fi utilizate în
- **Filtrul experimental** servește pentru a testa unele reguli noi de filtrare care pot provoca conflicte și probleme de funcționare a site-urilor. În cazul în care aceste reguli funcționează fără probleme, ele sunt adăugate la filtrele principale. [Vizualizați regulile](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Filtrul pentru reclame mobile** blochează reclamele pe dispozitive mobile. Conține toate rețelele mobile de reclame cunoscute. [Vizualizați regulile](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **Filtru DNS** — compus din mai multe alte filtre (filtrul de bază AdGuard, filtru Social Media, filtru de Protecție împotriva urmăririi, filtru de reclame mobile, EasyList și EasyPrivacy) și simplificat special pentru a fi mai bine compatibil cu blocarea de reclame la nivel DNS. Acest filtru este utilizat de serverele [AdGuard DNS](https://adguard-dns.io/kb) pentru a bloca reclamele și urmărirea. [Vizualizați regulile](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [Vizualizați regulile](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## Politica filtrelor AdGuard
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index cd4d9fe3248..78a98bef3f2 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Exemple**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ Dacă doriți ca regula să nu fie aplicată anumitor domenii, începeți un num
**`$domain` modifier matching target domain:**
-În unele cazuri, modificatorul `$domain` poate corespunde nu doar domeniului de referință, ci și domeniului țintă. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-Adică, dacă modificatorul `$domain` conține doar domenii excluse, atunci regula nu trebuie să îndeplinească a doua și a treia condiții pentru a corespunde domeniului țintă împotriva modificatorului `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. Acest lucru afectează regulile cu [`$cookie`](#cookie-modifier) și [`$csp`](#csp-modifier) modificatori, de asemenea.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Exemple**
- `*$cookie,domeniu=example.org|example.com` va bloca cookie-urile pentru toate solicitările către și de la `example.org` și `example.com`.
-- `*$document,domeniu=example.org|example.com` va bloca toate solicitările către și de la `example.org` și `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `pagina$domeniu=example.org` va corespunde, deoarece corespunde domeniului de referință.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `pagina$domeniu=targetdomain.com|~example.org` nu va fi corespondent deoarece domeniul de referință este exclus în mod explicit.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 1da99ee4540..1b57f63854e 100644
--- a/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/ro/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ Filtrele de blocare a reclamelor AdGuard includ:
- Filtru de bază AdGuard
- AdGuard Mobile Ads filter
- Filtre regionale împărțite pe principiu de limbă — chineză, olandeză, franceză, germană, japoneză, rusă, spaniolă/portugheză, turcă și ucraineană
-- AdGuard Quick Fixes filter
### Scopul acestor filtre
- **Filtrul de bază** este conceput pentru a bloca reclamele pe site-uri în limba engleză și pe cele pentru care nu există un filtru separat. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
Obiectivul filtrelor de blocare a reclamelor este de a bloca toate tipurile de publicitate pe site-uri, aplicații și anumite dispozitive care pot încărca reclame de pe Internet:
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index 0b62b6d858e..3a9f1305b8a 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ Bootstrap DNS для зашифрованных upstream DNS-серверов,
**О протоколе HTTP/3**: это последняя версия протокола HTTP, основанная на QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Исходящий прокси
#### Показывать настройку «Фильтровать DNS-запросы»
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index aa1505c8592..6a11e9b8a22 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ HTTPS-фильтрация позволяет AdGuard фильтровать с
В этом разделе вы можете узнать больше о лицензии и управлять ей:
- Купить лицензию AdGuard, чтобы активировать [функции полной версии](/adguard-for-android/features/free-vs-full)
-- Войти в аккаунт AdGuard или ввести код активации лицензии
-- Зарегистрироваться для активации 7-дневного пробного периода, если вы ещё не воспользовались им
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Обновить статус лицензии в меню с тремя точками (⋮)
- Открыть личный кабинет AdGuard, чтобы управлять лицензией
- Сбросить лицензию — например, если вы достигли лимита устройств для неё и хотите применить другую
-
+
## Поддержка
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 8f963ae815f..b8f4b8c816f 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ sidebar_position: 15
- В терминале введите команду `adb install Downloads/adguard_tv.apk`. Если загрузки у вас хранятся в другом месте, замените Downloads/adguard_tv.apk на свой путь до скачанного файла.
- Дождитесь сообщения в терминале об успешной установке приложения.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index b272a4f23da..873e4f73865 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ sidebar_position: 9
Установив значение `true`, вы разрешаете AdGuard фильтровать трафик, передаваемый по протоколу HTTP/3 — последней версии протокола HTTP на базе QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
Установив значение `true`, вы включите фильтрацию локальной сети.
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index aa6a6460ffd..01b630c371c 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ sidebar_position: 1
AdGuard для Windows — это простой в использовании инструмент, блокирующий раздражающие баннеры, всплывающие окна, видеорекламу и трекеры. Но это ещё не всё: он помогает экономить трафик, быстрее загружать веб-страницы, а также защищает компьютер от нежелательных и потенциально вредоносных сайтов. Также AdGuard защищает вас от фишинговых сайтов, а ваших детей — от неприемлемого контента.
-
+
После запуска AdGuard для Windows вы увидите главный экран приложения. Самая заметная деталь — _кнопка включения и выключения защиты_. Также на этом экране можно отслеживать заблокированную рекламу, статистику трекеров и угроз, узнать текущую версию приложения или обновить его. Кроме того, в правом верхнем углу находятся четыре вкладки: _Настройки_, _Поддержка_, _Лицензия_ и _О программе_. О каждой из них поговорим отдельно.
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index aaab2eacf07..ae7692a0aae 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,15 +11,15 @@ sidebar_position: 2
Раздел _Настройки_ требует наибольшего внимания. Здесь вы можете настроить приложение в соответствии с вашими требованиями: блокировать определённые элементы или сайты, использовать DNS-сервер доверенного провайдера, удалять сторонние куки и так далее.
-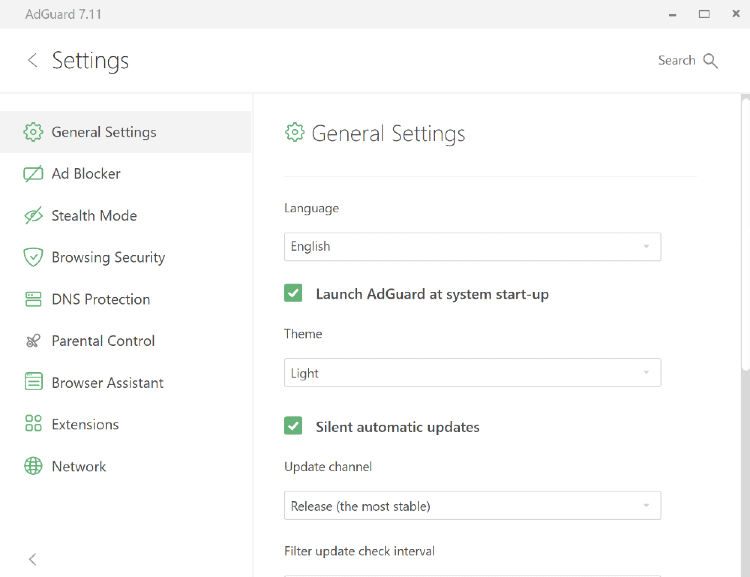
+### General settings
-### Основные настройки
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-Здесь вы можете настроить язык и тему (Тёмная или Светлая), включение AdGuard при запуске системы и бесшумные автоматические обновления, выбрать канал обновления и установить интервал проверки обновлений. Если AdGuard для Windows работает некорректно и поддержка попросила вас [собрать логи](/adguard-for-windows/solving-problems/adguard-logs.md), вам тоже следует перейти в _Настройки_.
+
-
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-В самом низу экрана вы найдёте _Расширенные настройки_. Изменение некоторых из них может потенциально вызвать проблемы с работой AdGuard, нарушить интернет-соединение или поставить под угрозу вашу безопасность и конфиденциальность. Заходите в этот раздел, только если вы уверены в своих действиях, или наша команда поддержки попросила вас об этом. [В отдельной статье](/adguard-for-windows/solving-problems/low-level-settings.md) рассказали, что находится в _Расширенных настройках_.
+
### Блокировка рекламы
@@ -46,9 +46,9 @@ sidebar_position: 2
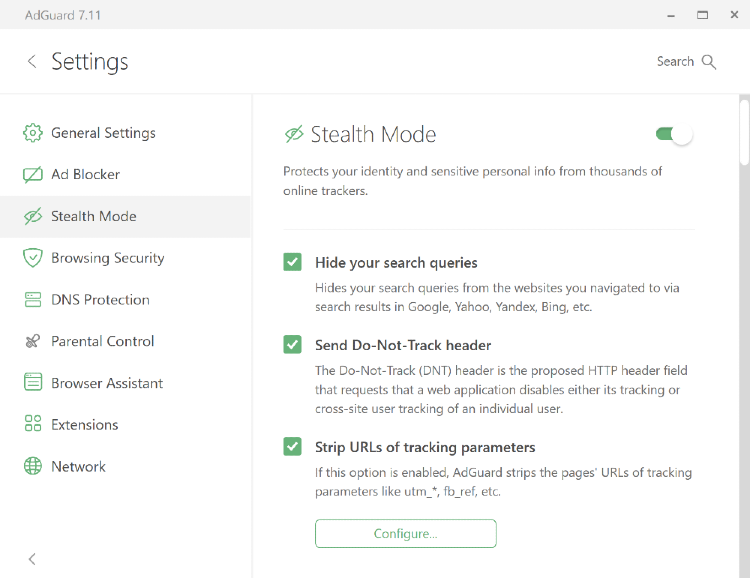
-Работа этого модуля гибко настраивается: например, вы можете запретить сайту узнавать, что вы искали в поисковой системе, прежде чем попасть на этот сайт. Вы также можете автоматически удалять cookie, как принадлежащие сайту, так и сторонние, и отключить определение местоположения в браузере — оно может использоваться для отслеживания ваших перемещений.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-[Больше о Защите от трекинга](/general/stealth-mode)
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Защита от фишинга
@@ -81,15 +81,15 @@ sidebar_position: 2

-### Родительский контроль
+### Parental control
-Бывают сайты, доступ к которым стоит ограничивать, если компьютером пользуются дети. Эту задачу выполняет _Родительский контроль_.
+Бывают сайты, доступ к которым стоит ограничивать, если компьютером пользуются дети. This task is accomplished by _Parental control_.
-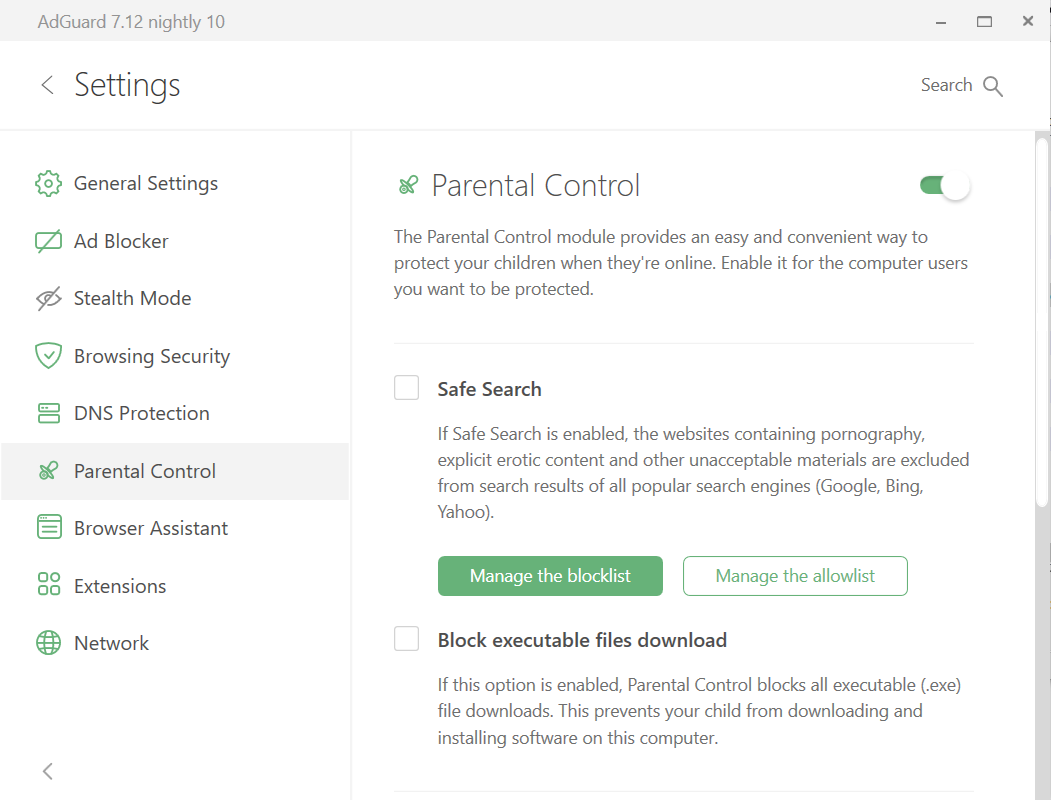
+
-Модуль проверяет содержимое веб-страниц, открытых в браузере, и отфильтровывает страницы с нежелательным для детей контентом: изображения и тексты для взрослых, ненормативная лексика, насилие, пропаганда наркотиков и т. д. Настройки Родительского контроля защищены паролем, чтобы ребёнок не смог обойти ограничения. Этот модуль не только блокирует доступ к нежелательным сайтам, но и удаляет неподходящие для детей ссылки из результатов поиска.
+Модуль проверяет содержимое веб-страниц, открытых в браузере, и отфильтровывает страницы с нежелательным для детей контентом: изображения и тексты для взрослых, ненормативная лексика, насилие, пропаганда наркотиков и т. д. Parental control settings are password-protected so that the child is not able to go round the restrictions. Этот модуль не только блокирует доступ к нежелательным сайтам, но и удаляет неподходящие для детей ссылки из результатов поиска.
-В модуле _Родительский контроль_ вы можете включить _Безопасный поиск_, а также указать, на какие сайты _Родительский контроль_ должен распространяться. Вы также можете включить функцию _Запретить загрузку программ_, чтобы ваш ребёнок не мог загружать и устанавливать программное обеспечение на компьютер. В модуле _Родительский контроль_ есть ещё две опции: вы можете выбрать конкретного пользователя Windows для защиты с помощью _Родительского контроля_ и установить пароль для защиты настроек AdGuard от изменений.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. Вы также можете включить функцию _Запретить загрузку программ_, чтобы ваш ребёнок не мог загружать и устанавливать программное обеспечение на компьютер. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Браузерный помощник
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 79dd4563287..a2e2ec51963 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ sidebar_position: 7
Если эта настройка включена, AdGuard будет фильтровать запросы, отправленные по протоколу HTTP/3, в дополнение к другим типам запросов.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Использовать драйвер в режиме перенаправления
Если эта опция включена, AdGuard перехватывает весь трафик и перенаправляет его на локальный прокси-сервер для дальнейшей фильтрации.
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index b6c485c8872..c569c3d7b36 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ sidebar_position: 2
- **Экспериментальный фильтр** предназначен для проверки некоторых новых правил фильтрации, которые потенциально могут вызывать конфликты или ломать работу сайтов. В случае успешной проверки правила из этого фильтра добавляются в основные фильтры. [Посмотреть правила](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Фильтр мобильной рекламы** блокирует рекламу на мобильных устройствах. Содержит все известные нам рекламные сети. [Посмотреть правила](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS-фильтр** составлен из нескольких фильтров (Базовый фильтр AdGuard, Фильтр социальных сетей, Фильтр счётчиков и систем аналитики, Фильтр мобильной рекламы, EasyList и EasyPrivacy) и специально упрощён для лучшей совместимости с блокировкой рекламы на DNS-уровне. Этот фильтр используется серверами [AdGuard DNS](https://adguard-dns.io/kb) для блокировки рекламы и трекинга. [Посмотреть правила](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Фильтр быстрых исправлений** используется для быстрого устранения критических проблем фильтрации контента на популярных сайтах без обновления MV3-расширения. [Посмотреть правила](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## Политика фильтров AdGuard
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index cd9e85368f3..738391d8631 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ Wildcard-символы поддерживаются для TLD-доменов
На Mac вы можете найти bundle ID или имя процесса интересующего вас приложения в деталях соответствующих запросов в Журнале фильтрации.
+**Синтаксис**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Примеры**
- `||baddomain.com^$app=org.example.app` — правило для блокировки запросов, которые соответствуют указанной маске и отправлены Android-приложением `org.example.app`.
@@ -429,9 +442,23 @@ Wildcard-символы поддерживаются для TLD-доменов
- `||baddomain.com^$app=~org.example.app` — правило для блокировки запросов, соответствующих указанной маске и отправленных из любого приложения, кроме `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — аналогично, но в исключениях два приложения: `org.example.app1` и `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Ограничения
-В модификаторе правила к приложениям нельзя добавлять подстановочный знак (*), например `$app=com.*.music`. Правила с таким модификатором считаются недействительными.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Wildcard-символы поддерживаются для TLD-доменов
- Только AdGuard для Windows, Mac и Android имеют технические возможности для поддержки правил с модификатором `$app`.
- На Windows имя процесса нечувствительно к регистру, начиная с версий AdGuard для Windows [c CoreLibs][] 1.12 или более поздней версии.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,78 +557,63 @@ entry_i = ( regular_domain / any_tld_domain / regexp )
**Модификатор `$domain`, соответствующий целевому домену:**
-В некоторых случаях модификатор `$domain` может соответствовать не только домену-рефереру, но и целевому домену. Это происходит при соблюдении всех условий:
-
-1. Тип контента запроса — `document`
-1. Шаблон правила не соответствует ни одному конкретному домену
-1. Шаблон правила не содержит регулярных выражений
-1. Модификатор `$domain` содержит только исключённые домены, например, `$domain=~example.org|~example.com`
-
-Для сопоставления целевого домена должен выполняться следующий предикат:
-
-```text
-1 И ((2 И 3) ИЛИ 4)
-```
-
-То есть, если модификатор `$domain` содержит только исключённые домены, то правилу не нужно выполнять второе и третье условия, чтобы соответствовать целевому домену `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-Если какие-либо из условий выше не выполнены, но правило содержит модификатор [`$cookie`](#cookie-modifier) или [`$csp`](#csp-modifier), модификатор всё равно будет соответствовать целевому домену.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-Если реферер соответствует правилу с `$domain`, которое явно исключает домен реферера, то правило не сработает, даже если целевой домен тоже ему соответствует. Это также касается правил с модификаторами [`$cookie`](#cookie-modifier) и [`$csp`](#csp-modifier).
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Примеры**
- `*$cookie,domain=example.org|example.com` заблокирует cookies для всех запросов от и к `example.org` и `example.com`.
-- `*$document,domain=example.org|example.com` заблокирует все запросы от и к `example.org` и `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
-В следующих примерах предполагается, что запросы отправляются от `http://example.org/page` (реферер), а целевой URL — `http://targetdomain.com/page`.
+In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` сработает, так как соответствует рефереру.
-- `page$domain=targetdomain.com` сработает, так как соответствует целевому домену и удовлетворяет всем требованиям, перечисленным выше.
-- `||*page$domain=targetdomain.com` не сработает, так как шаблон `||*page` может указывать на конкретные домены, например, `example.page`.
-- `||*page$domain=targetdomain.com,cookie` сработает, потому что правило содержит модификатор `$cookie`, несмотря на то, что шаблон `||*page` может соответствовать конкретным доменам.
-- `/banner\d+/$domain=targetdomain.com` не сработает, поскольку правило содержит регулярное выражение.
-- `page$domain=targetdomain.com|~example.org` не сработает, так как домен реферера явно исключён.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
+- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### Ограничения модификатора `$domain` {#domain-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-В [AdGuard для Chrome MV3][ext-mv3] записи `regexp` и `any_tld_domain` не поддерживаются.
+In [AdGuard for Chrome MV3][ext-mv3], `regexp` and `any_tld_domain` entries are not supported.
-AdGuard для iOS и AdGuard для Safari поддерживают модификатор `$domain`, но имеют некоторые ограничения. Подробнее об этом написано в разделе [SafariConverterLib](#safari-converter--basic--supported-with-limitations).
+AdGuard for iOS and AdGuard for Safari support the `$domain` modifier but have some limitations. For more details, see the [SafariConverterLib section](#safari-converter--basic--supported-with-limitations).
-Правила с `regexp` в модификаторе `$domain` не поддерживаются в AdGuard для Safari и AdGuard для iOS.
+Rules with `regexp` in the `$domain` modifier are not supported by AdGuard for Safari and AdGuard for iOS.
:::
:::info Совместимость
-Правила с регулярными выражениями в модификаторе `$domain` поддерживаются в AdGuard для Windows, AdGuard для Mac и AdGuard для Android [с CoreLibs][] версии 1.11 или выше и в Браузерном расширении AdGuard [с TSUrlFilter][] версии 3.0.0 или выше.
+Rules with regular expressions in the `$domain` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.11 or later, and AdGuard Browser Extension with [TSUrlFilter][] v3.0.0 or later.
-В AdGuard для Windows, Mac и Android с [CoreLibs][] 1.12 или более поздней версии вместо модификатора `$domain` можно также использовать `$from`.
+In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.12 or later the `$domain` modifier can be alternatively spelled as `$from`.
:::
#### **`$header`** {#header-modifier}
-Модификатор `$header` позволяет сопоставлять HTTP-ответ, имеющий определённый заголовок, с определённым значением (опционально).
+The `$header` modifier allows matching the HTTP response having a specific header with (optionally) a specific value.
-**Синтаксис**
+**Syntax**
```text
$header "=" h_name [":" h_value]
h_value = string / regexp
```
-где:
+where:
- **`h_name`** (обязательно) — имя HTTP-заголовка. Сопоставляется без учёта регистра символов.
- **`h_value`** (опционально) — выражение для сопоставления значения HTTP-заголовка, может быть одним из:
- **`string`** — последовательность символов. Лексикографически сопоставляется со значением заголовка;
- **`regexp`** — регулярное выражение, начинается и заканчивается символом `/`. Паттерн работает так же, как и в основных URL-правилах, но символы `/`, `$` и `,` должны быть экранированы с помощью `\`.
-Часть модификатора со значением заголовка `":" h_value` может быть опущена. В этом случае модификатор сопоставляет только имя заголовка.
+The modifier part, `":" h_value`, may be omitted. In that case, the modifier matches the header name only.
**Примеры**
@@ -613,41 +626,41 @@ h_value = string / regexp
:::caution Ограничения
-1. Модификатор `$header` может быть сопоставлен, только когда заголовки получены. Если запрос блокируется или перенаправляется на более ранней стадии, модификатор не может быть применён.
+1. The `$header` modifier can be matched only when headers are received. So if the request is blocked or redirected at an earlier stage, the modifier cannot be applied.
-1. В Браузерном расширении AdGuard модификатор `$header` совместим только с [`$csp`](#csp-modifier), [`$removeheader`](#removeheader-modifier) (только заголовки ответов), [`$important`](#important-modifier), [`$badfilter`](#badfilter-modifier), [`$domain`](#domain-modifier), [`$third-party`](#third-party-modifier), [`$match-case`](#match-case-modifier) и [модификаторы типа контента](#content-type-modifiers), такие как [`$script`](#script-modifier) и [`$stylesheet`](#stylesheet-modifier). Правила с другими модификаторами считаются некорректными и не будут применены.
+1. In AdGuard Browser Extension, the `$header` modifier is only compatible with [`$csp`](#csp-modifier), [`$removeheader`](#removeheader-modifier) (response headers only), [`$important`](#important-modifier), [`$badfilter`](#badfilter-modifier), [`$domain`](#domain-modifier), [`$third-party`](#third-party-modifier), [`$match-case`](#match-case-modifier), and [content-type modifiers](#content-type-modifiers) such as [`$script`](#script-modifier) and [`$stylesheet`](#stylesheet-modifier). The rules with other modifiers are considered invalid and will be discarded.
:::
:::info Совместимость
-Правила с модификатором `$header` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.11 или выше и в Браузерном расширении AdGuard c [TSUrlFilter][] версии 3.0.0 или выше.
+Rules with the `$header` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.11 or later, and AdGuard Browser Extension with [TSUrlFilter][] v3.0.0 or later.
:::
#### **`$important`** {#important-modifier}
-Модификатор `$important`, применённый к правилу, повышает его приоритет по сравнению с правилами без такого модификатора. Это относится даже к базовым правилам исключений.
+The `$important` modifier applied to a rule increases its priority over rules without the identical modifier. Even over basic exception rules.
-Перейдите [к приоритетам правил](#rule-priorities) для более подробной информации.
+Go to [rules priorities](#rule-priorities) for more details.
**Примеры**
```adblock
-! блокирующее правило заблокирует все запросы, несмотря на правило-исключение
+! blocking rule will block all requests despite of the exception rule
||example.org^$important
@@||example.org^
```
```adblock
-! если правило-исключение тоже содержит модификатор `$important`, его приоритет будет выше, и запросы не будут заблокированы
+! if the exception rule also has `$important` modifier, it will prevail and requests won't be blocked
||example.org^$important
@@||example.org^$important
```
#### **`$match-case`** {#match-case-modifier}
-Этот модификатор определяет правило, которое применяется только к адресам с совпадением регистра символов. По умолчанию регистр символов не учитывается.
+This modifier defines a rule which applies only to addresses that match the case. Default rules are case-insensitive.
**Примеры**
@@ -655,15 +668,15 @@ h_value = string / regexp
:::info Совместимость
-Правила с `$match-case` поддерживаются в AdGuard для iOS и AdGuard для Safari с SafariConverterLib версии 2.0.43 или выше.
+Rules with the `$match-case` are supported by AdGuard for iOS and AdGuard for Safari with SafariConverterLib v2.0.43 or later.
-Все остальные продукты уже поддерживают этот модификатор.
+All other products already support this modifier.
:::
#### **`$method`** {#method-modifier}
-Этот модификатор ограничивает область действия правила запросами, использующими указанный набор методов HTTP. Допускаются отрицательные методы. Методы должны быть указаны строчными буквами, но сопоставляются они без учёта регистра. Чтобы добавить несколько методов в одно правило, используйте в качестве разделителя вертикальную черту `|`.
+This modifier limits the rule scope to requests that use the specified set of HTTP methods. Negated methods are allowed. The methods must be specified in all lowercase characters, but are matched case-insensitively. To add multiple methods to one rule, use the vertical bar `|` as a separator.
**Примеры**
@@ -674,19 +687,19 @@ h_value = string / regexp
:::caution Ограничения
-Правила, где к одному методу применяется инверсия (~), а к другому нет, считаются недействительными. Так, например, правило `||evil.com^$method=get|~head` будет проигнорировано.
+Rules with mixed negated and not negated values are considered invalid. So, for example, the rule `||evil.com^$method=get|~head` will be ignored.
:::
:::info Совместимость
-Правила с модификатором `$method` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] 1.12 или более поздней версии, а также в Браузерном расширении AdGuard для Chrome, Firefox и Edge с [TSUrlFilter][] 2.1.1 или более поздней версии.
+Rules with `$method` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.12 or later, and AdGuard Browser Extension for Chrome, Firefox, and Edge with [TSUrlFilter][] v2.1.1 or later.
:::
#### **`$popup`** {#popup-modifier}
-AdGuard будет пытаться закрыть браузерную вкладку с любым адресом, подходящим под правило с этим модификатором. Обратите внимание, что не все вкладки можно закрыть.
+AdGuard will try to close the browser tab with any address that matches a blocking rule with this modifier. Please note that not all the tabs can be closed.
**Примеры**
@@ -694,24 +707,24 @@ AdGuard будет пытаться закрыть браузерную вкла
##### Ограничения модификатора `$popup` {#popup-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-1. Модификатор `$popup` лучше всего работает в расширении AdGuard для браузеров на базе Chromium и Firefox.
-1. В [AdGuard для Chrome MV3][ext-mv3] правила с модификатором [`$popup`][popup-in-mv3] не будут работать, поэтому мы отключаем их преобразование в декларативные правила. Мы попытаемся использовать их только в нашем движке [TSUrlFilter][] и закрывать новые вкладки программно.
-1. В AdGuard для iOS и AdGuard для Safari `$popup`-правила просто заблокируют страницу.
-1. В AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux модификатор `$popup` в некоторых случаях может не обнаружить всплывающее окно, и оно не будет заблокировано. Модификатор `$popup` применяет тип контента `document` со специальным флагом, который передаётся блокирующей странице. Блокирующая страница сама может провести некоторые проверки и закрыть окно, если это действительно всплывающее окно. В противном случае страница должна быть загружена. Его можно комбинировать с другими модификаторами типа запроса, такими как `$third-party`, `$strict-third-party`, `$strict-first-party` и `$important`.
+1. The `$popup` modifier works best in AdGuard Browser Extension for Chromium-based browsers and Firefox.
+1. In [AdGuard for Chrome MV3][ext-mv3] rules with the [`$popup`][popup-in-mv3] modifier would not work, so we disable converting them to declarative rules. We will try to use them only in our [TSUrlFilter][] engine and close new tabs programmatically.
+1. In AdGuard for iOS and AdGuard for Safari, `$popup` rules simply block the page right away.
+1. In AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux, the `$popup` modifier may not detect a popup in some cases and it will not be blocked. The `$popup` modifier applies the `document` content type with a special flag which is passed to a blocking page. Blocking page itself can do some checks and close the window if it is really a popup. Otherwise, page should be loaded. It can be combined with other request type modifiers, such as `$third-party`, `$strict-third-party`, `$strict-first-party`, and `$important`.
:::
:::info Совместимость
-Правила с модификатором `$popup` не поддерживаются в AdGuard Content Blocker.
+Rules with the `$popup` modifier are not supported by AdGuard Content Blocker.
:::
#### **`$strict-first-party`** {#strict-first-party-modifier}
-Работает так же, как модификатор [`$~third-party`](#third-party-modifier), но обрабатывает запрос как запрос первой стороны только в том случае, если реферер и источник имеют одинаковое имя хоста.
+Works the same as the [`$~third-party`](#third-party-modifier) modifier, but only treats the request as first-party if the referrer and origin have exactly the same hostname.
**Примеры**
@@ -719,19 +732,19 @@ AdGuard будет пытаться закрыть браузерную вкла
:::note
-Вы можете использовать более короткое название (псевдоним) вместо полного названия модификатора: `$strict1p`.
+You can use a shorter name (alias) instead of using the full modifier name: `$strict1p`.
:::
:::info Совместимость
-Правила с модификатором `$strict-first-party` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.16 или выше.
+Rules with the `$strict-first-party` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.16 or later.
:::
#### **`$strict-third-party`** {#strict-third-party-modifier}
-Работает так же, как модификатор [`$third-party`](#third-party-modifier), но ещё обрабатывает запросы от домена к его поддоменам и наоборот как сторонние запросы.
+Works the same as the [`$third-party`](#third-party-modifier) modifier but also treats requests from the domain to its subdomains and vice versa as third-party requests.
**Примеры**
@@ -739,26 +752,26 @@ AdGuard будет пытаться закрыть браузерную вкла
:::note
-Вы можете использовать более короткое название (псевдоним) вместо полного названия модификатора: `$strict3p`.
+You can use a shorter name (alias) instead of using the full modifier name: `$strict3p`.
:::
:::info Совместимость
-Правила с модификатором `$strict-third-party` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.16 или выше.
+Rules with the `$strict-third-party` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.16 or later.
:::
#### **`$third-party`** {#third-party-modifier}
-Ограничение на сторонние или пользовательские запросы. Сторонним является запрос, отправленный с внешнего домена. Например, запрос к домену `example.org`, отправленный с домена `domain.com`, является сторонним.
+A restriction on third-party and custom requests. A third-party request is a request from an external domain. For example, a request to `example.org` from `domain.com` is a third-party request.
:::note
-Чтобы считаться таковым, сторонний запрос должен соответствовать одному из следующих условий:
+To be considered as such, a third-party request should meet one of the following conditions:
-1. Его реферер — это не поддомен целевого домена, или наоборот. Например, запрос к `subdomain.example.org`, отправленный с домена `example.org`, не является сторонним
-1. Значение его заголовка `Sec-Fetch-Site` — `cross-site`
+1. Its referrer is not a subdomain of the target domain or vice versa. For example, a request to `subdomain.example.org` from `example.org` is not a third-party request
+1. Its `Sec-Fetch-Site` header is set to `cross-site`
:::
@@ -768,7 +781,7 @@ AdGuard будет пытаться закрыть браузерную вкла
- `||domain.com^$third-party` — правило применяется на всех сайтах, кроме `domain.com` и его поддоменов. Пример стороннего запроса: `http://example.org/banner.jpg`.
-Если указан модификатор `$~third-party`, то правило применяется только к запросам, которые не являются сторонними. То есть эти запросы отправлены с того же домена.
+If there is a `$~third-party` modifier, the rule is only applied to the requests that are not from third parties. Which means, they have to be sent from the same domain.
**`$~third-party`:**
@@ -776,13 +789,13 @@ AdGuard будет пытаться закрыть браузерную вкла
:::note
-Вы можете использовать более короткое название (псевдоним) вместо полного названия модификатора: `$3p`.
+You may use a shorter name (alias) instead of using the full modifier name: `$3p`.
:::
#### **`$to`** {#to-modifier}
-`$to` ограничивает область действия правила запросами, сделанными **на** указанные домены и их поддомены. Чтобы добавить несколько доменов в одно правило, используйте символ `|` в качестве разделителя.
+`$to` limits the rule scope to requests made **to** the specified domains and their subdomains. Чтобы добавить несколько доменов в одно правило, используйте символ `|` в качестве разделителя.
**Примеры**
@@ -792,27 +805,27 @@ AdGuard будет пытаться закрыть браузерную вкла
:::caution Ограничения
-[`$denyallow`](#denyallow-modifier) не может использоваться вместе с `$to`. Его можно выразить инвертированным `$to`: `$denyallow=a.com|b.com` эквивалентно `$to=~a.com|~b.com`.
+[`$denyallow`](#denyallow-modifier) cannot be used together with `$to`. Его можно выразить инвертированным `$to`: `$denyallow=a.com|b.com` эквивалентно `$to=~a.com|~b.com`.
:::
:::info Совместимость
-Правила с модификатором `$to` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.12 или выше и в Браузерном расширении AdGuard c [TSUrlFilter][] версии 2.1.3 или выше.
+Rules with the `$to` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.12 or later, and AdGuard Browser Extension with [TSUrlFilter][] v2.1.3 or later.
:::
### Модификаторы типа контента {#content-type-modifiers}
-Существует целый набор модификаторов, которые ограничивают область применения правила только определённым типом контента. Эти модификаторы можно комбинировать, чтобы, например, распространить правило одновременно и на картинки, и на скрипты.
+There is a set of modifiers, which can be used to limit the rule's application area to certain type of content. These modifiers can also be combined to cover, for example, both images and scripts.
:::info Совместимость
-Существует большая разница в том, как AdGuard определяет тип контента на разных платформах. В случае Браузерного расширения AdGuard, тип контента для каждого запроса предоставляется самим браузером. В случае AdGuard для Windows, Mac и Android для определения используется следующая методика: сначала мы пытаемся определить тип запроса по заголовку запроса `Sec-Fetch-Dest` или по расширению имени файла. Если запрос не заблокирован на этом этапе, то тип запроса уточняется с использованием заголовка `Content-Type` в начале ответа, полученного от сервера.
+There is a big difference in how AdGuard determines the content type on different platforms. For AdGuard Browser Extension, content type for every request is provided by the browser. AdGuard for Windows, Mac, and Android use the following method: first, the apps try to determine the type of the request by the `Sec-Fetch-Dest` request header or by the filename extension. If the request is not blocked at this stage, the type will be determined using the `Content-Type` header at the beginning of the server response.
:::
-**Примеры модификаторов типа контента**
+**Examples of content-type modifiers**
- `||example.org^$image` — соответствует всем картинкам с домена `example.org`.
- `||example.org^$script,stylesheet` — соответствует всем скриптам и стилям с домена `example.org`.
@@ -848,11 +861,11 @@ AdGuard будет пытаться закрыть браузерную вкла
#### **`$document`** {#document-modifier}
-Правило соответствует запросам документов основного фрейма, то есть HTML-документам, которые загружаются во вкладке браузера. Оно не подходит для iframe, для них существует модификатор [`$subdocument`](#subdocument-modifier).
+The rule corresponds to the main frame document requests, i.e. HTML documents that are loaded in the browser tab. It does not match iframes, there is a [`$subdocument` modifier](#subdocument-modifier) for these.
-По умолчанию AdGuard не блокирует запросы, которые загружаются во вкладке браузера (например, «обход основного фрейма»). Идея заключается в том, чтобы не препятствовать загрузке страниц, поскольку пользователь явно указал, что он хочет, чтобы эта страница была загружена. Однако, если использовать модификатор `$document`, то AdGuard не будет использовать эту логику и предотвратит загрузку страницы. А именно, ответит «страницей блокировки».
+By default, AdGuard does not block the requests that are loaded in the browser tab (e.g. "main frame bypass"). The idea is not to prevent pages from loading as the user clearly indicated that they want this page to be loaded. However, if the `$document` modifier is specified explicitly, AdGuard does not use that logic and prevents the page load. Instead, it responds with a "blocking page".
-Если этот модификатор используется в правиле-исключении (`@@`), то оно полностью отключает блокировку на соответствующих страницах. Это равносильно одновременному использованию модификаторов `$elemhide`, `$content`, `$urlblock`, `$jsinject` и `$extension`.
+If this modifier is used with an exclusion rule (`@@`), it completely disables blocking on corresponding pages. It is equivalent to using `$elemhide`, `$content`, `$urlblock`, `$jsinject`, `$extension` modifiers simultaneously.
**Примеры**
@@ -865,71 +878,71 @@ AdGuard будет пытаться закрыть браузерную вкла
:::note
-Вы можете использовать более короткое имя (псевдоним) вместо полного имени модификатора: `$doc`.
+You may use a shorter name (alias) instead of using the full modifier name: `$doc`.
:::
#### **`$font`** {#font-modifier}
-Правило соответствует запросам к шрифтам, например файлам с расширением `.woff`.
+The rule corresponds to requests for fonts, e.g. `.woff` filename extension.
#### **`$image`** {#image-modifier}
-Правило соответствует запросам к изображениям.
+The rule corresponds to images requests.
#### **`$media`** {#media-modifier}
-Правило соответствует запросам к медиафайлам — музыке и видео, например файлам `.mp4`.
+The rule corresponds to requests for media files — music and video, e.g. `.mp4` files.
#### **`$object`** {#object-modifier}
-Правило соответствует ресурсам плагинов браузера, например Java или Flash.
+The rule corresponds to browser plugins resources, e.g. Java or Flash.
:::info Совместимость
-Правила с модификатором `$object` не поддерживаются в AdGuard для Safari и AdGuard для iOS.
+Rules with `$object` modifier are not supported by AdGuard for Safari and AdGuard for iOS.
:::
#### **`$other`** {#other-modifier}
-Правило применяется к запросам, тип которых не был определён или не соответствует перечисленным выше типам.
+The rule applies to requests for which the type has not been determined or does not match the types listed above.
#### **`$ping`** {#ping-modifier}
-Правило соответствует запросам, вызванным либо `navigator.sendBeacon()`, либо атрибутом `ping` в ссылках.
+The rule corresponds to requests caused by either `navigator.sendBeacon()` or the `ping` attribute on links.
##### Ограничения модификатора `$ping` {#ping-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-AdGuard для Windows, Mac и Android часто не может точно определить `navigator.sendBeacon()`. Не рекомендуется использовать `$ping` в фильтрах, которые должны использоваться продуктами AdGuard на базе CoreLibs.
+AdGuard for Windows, Mac, and Android often cannot accurately detect `navigator.sendBeacon()`. Using `$ping` is not recommended in the filter lists that are supposed to be used by CoreLibs-based AdGuard products.
:::
:::info Совместимость
-Правила с модификатором `$ping` не поддерживаются в AdGuard для Safari и AdGuard для iOS.
+Rules with `$ping` modifier are not supported by AdGuard for Safari and AdGuard for iOS.
:::
#### **`$script`** {#script-modifier}
-Правило соответствует запросам скриптов, например JavaScript, VBScript.
+The rule corresponds to script requests, e.g. JavaScript, VBScript.
#### **`$stylesheet`** {#stylesheet-modifier}
-Правило соответствует запросам к файлам CSS.
+The rule corresponds to CSS files requests.
:::note
-Вы можете использовать более короткое имя (псевдоним) вместо полного имени модификатора: `$css`.
+You may use a shorter name (alias) instead of using the full modifier name: `$css`.
:::
#### **`$subdocument`** {#subdocument-modifier}
-Правило соответствует запросам к встроенным страницам — HTML-тегам `frame` и `iframe`.
+The rule corresponds to requests for built-in pages — HTML tags `frame` and `iframe`.
**Примеры**
@@ -938,75 +951,75 @@ AdGuard для Windows, Mac и Android часто не может точно о
:::note
-Вы можете использовать более короткое имя (псевдоним) вместо полного имени модификатора: `$frame`.
+You may use a shorter name (alias) instead of using the full modifier name: `$frame`.
:::
##### Ограничения модификатора `$subdocument` {#subdocument-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-В AdGuard для Windows, Mac и Android поддокументы определяются [по заголовку Sec-Fetch-Dest][], если он присутствует. В противном случае некоторые основные страницы могут рассматриваться как поддокументы.
+In AdGuard for Windows, Mac, and Android subdocuments are being detected by the [Sec-Fetch-Dest header][] if it is present. Otherwise, some main pages may be treated as subdocuments.
:::
:::info Совместимость
-Правила с модификатором `$subdocument` не поддерживаются в AdGuard Content Blocker.
+Rules with `$subdocument` modifier are not supported by AdGuard Content Blocker.
:::
#### **`$websocket`** {#websocket-modifier}
-Правило применяется только к соединениям WebSocket.
+The rule applies only to WebSocket connections.
##### Ограничения модификатора `$websocket` {#websocket-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-Что касается AdGuard для Safari и AdGuard для iOS, то они поддерживаются на устройствах с macOS Monterey (версия 12) и iOS 16 и выше соответственно.
+For AdGuard for Safari and AdGuard for iOS, it is supported on devices with macOS Monterey (version 12) and iOS 16 or higher respectively.
:::
:::info Совместимость
-Модификатор `$websocket` поддерживается во всех продуктах AdGuard, кроме AdGuard Content Blocker.
+`$websocket` modifier is supported in all AdGuard products except AdGuard Content Blocker.
:::
#### **`$xmlhttprequest`** {#xmlhttprequest-modifier}
-Правило применяется только к ajax-запросам (запросам, отправленным через объект JavaScript `XMLHttpRequest`).
+The rule applies only to ajax requests (requests sent via the JavaScript object `XMLHttpRequest`).
:::note
-Вы можете использовать более короткое имя (псевдоним) вместо полного имени модификатора: `$xhr`.
+You may use a shorter name (alias) instead of using the full modifier name: `$xhr`.
:::
:::info Совместимость
-AdGuard для Windows, Mac и Android часто не может точно определить этот тип модификатора и иногда определяет его как [`$other`](#other-modifier) или [`$script`](#script-modifier). Они могут точно обнаружить этот тип контента только при фильтрации современных браузеров, поддерживающих [Fetch metadata request headers](https://developer.mozilla.org/en-US/docs/Glossary/Fetch_metadata_request_header).
+AdGuard for Windows, Mac, Android when filtering older browsers cannot accurately detect this type and sometimes detects it as [`$other`](#other-modifier) or [`$script`](#script-modifier). They can only reliably detect this content type when filtering modern browsers that support [Fetch metadata request headers](https://developer.mozilla.org/en-US/docs/Glossary/Fetch_metadata_request_header).
:::
#### **`$object-subrequest` (удалён)** {#object-subrequest-modifier}
-:::danger Уведомление об удалении
+:::danger Removal notice
-Модификатор `$object-subrequest` удалён и больше не поддерживается. Правила с ним считаются недействительными. Правило соответствует запросам плагинов браузера (обычно это Flash).
+`$object-subrequest` modifier is removed and is no longer supported. Rules with it are considered as invalid. The rule corresponds to requests by browser plugins (it is usually Flash).
:::
#### **`$webrtc` (удалён)** {#webrtc-modifier}
-:::danger Уведомление об удалении
+:::danger Removal notice
-Этот модификатор удалён и больше не поддерживается. Правила с ним считаются недействительными. Если вы хотите блокировать WebRTC, рассмотрите возможность использования [скриптлета](#scriptlets) `nowebrtc`.
+This modifier is removed and is no longer supported. Rules with it are considered as invalid. If you need to suppress WebRTC, consider using the `nowebrtc` [scriptlet](#scriptlets).
:::
-Правило применяется только к WebRTC-соединениям.
+The rule applies only to WebRTC connections.
**Примеры**
@@ -1015,11 +1028,11 @@ AdGuard для Windows, Mac и Android часто не может точно о
### Модификаторы правил исключений {#exception-modifiers}
-Правила исключений отключают действие других базовых правил для адресов, которым они соответствуют. Они начинаются с маркера `@@`. К ним можно применить все основные модификаторы, перечисленные выше, а также несколько специальных модификаторов.
+Exception rules disable the other basic rules for the addresses to which they correspond. They begin with a `@@` mark. All the basic modifiers listed above can be applied to them and they also have a few special modifiers.
:::note Визуальное представление
-Рекомендуем также прочитать [шпаргалку по фильтрам от Adblock Plus](https://adblockplus.org/filter-cheatsheet#blocking), чтобы лучше понять, как строятся правила исключений.
+We recommend to get acquainted with [the Adblock Plus filter cheatsheet](https://adblockplus.org/filter-cheatsheet#blocking), for better understanding of how exception rules should be made.
:::
@@ -1047,22 +1060,22 @@ AdGuard для Windows, Mac и Android часто не может точно о
:::info
-По умолчанию, без указания дополнительных модификаторов типа контента, модификаторы правил исключений перекрывают другие базовые правила только для запросов основного фрейма документа (подробнее об основном фрейме документа написано в разделе о модификаторе [`$document`](#document-modifier)).
+By default, without specifying additional content type modifiers, exception rule modifiers override other basic rules only for main frame document requests (see [`$document`](#document-modifier) for more information about main frame document).
Например:
- Сайт `example.com` содержит `iframe`, указывающий на `example1.com.`.
- Применено правило `#%#//console.log('test')`.
-В этом случае журнал будет отображаться в консоли дважды: один раз для основного фрейма документа и один раз для `iframe`.
+In this case, the log will appear twice in the console: once for the main frame document and once for `iframe`.
-Если вы добавите правило `@@|||example.com^$jsinject`, журнал будет отображаться только один раз для `iframe`.
+If you add the `@@||example.com^$jsinject` rule, the log will appear only once for `iframe`.
:::
#### **`$content`** {#content-modifier}
-Отключает [HTML-фильтрацию](#html-filtering-rules), правила [`$hls`](#hls-modifier), [`$replace`](#replace-modifier)и [`$jsonprune`](#jsonprune-modifier) на страницах, соответствующих правилу.
+Disables [HTML filtering](#html-filtering-rules), [`$hls`](#hls-modifier), [`$replace`](#replace-modifier), and [`$jsonprune`](#jsonprune-modifier) rules on the pages that match the rule.
**Примеры**
@@ -1070,7 +1083,7 @@ AdGuard для Windows, Mac и Android часто не может точно о
#### **`$elemhide`** {#elemhide-modifier}
-Отключает любые [косметические правила](#cosmetic-rules) на страницах, подходящих под правило.
+Disables any [cosmetic rules](#cosmetic-rules) on the pages matching the rule.
**Примеры**
@@ -1078,25 +1091,25 @@ AdGuard для Windows, Mac и Android часто не может точно о
:::note
-Вы можете использовать более короткое название (псевдоним) вместо полного названия модификатора: `$ehide`.
+You may use a shorter name (alias) instead of using the full modifier name: `$ehide`.
:::
#### **`$extension`** {#extension-modifier}
-Отключает пользовательские скрипты — определённые или все для данного домена.
+Disables specific userscripts or all userscripts for a given domain.
-**Синтаксис**
+**Syntax**
```text
$extension[="userscript_name1"[|"userscript_name2"[|"userscript_name3"[...]]]]
```
-`userscript_name(i)` обозначает имя конкретного пользовательского скрипта, который должен быть отключён модификатором. Модификатор может содержать любое количество имён пользовательских скриптов или не содержать их вовсе. В последнем случае модификатор отключает все пользовательские скрипты.
+`userscript_name(i)` stands for a specific userscript name to be disabled by the modifier. The modifier can contain any number of userscript names or none. In the latter case the modifier disables all the userscripts.
-Имена пользовательских скриптов обычно содержат пробелы или другие специальные символы, поэтому необходимо заключать их в кавычки. Поддерживаются как одинарные (`'`), так и двойные (`"`) ASCII-кавычки. Несколько имён пользовательских скриптов должны быть разделены вертикальной чертой (`|`). Однако если имя пользовательского скрипта представляет собой одно слово без специальных символов, то его можно использовать без кавычек.
+Userscript names usually contain spaces or other special characters, which is why you should enclose the name in quotes. Both single (`'`) and double (`"`) ASCII quotes are supported. Multiple userscript names should be separated with a pipe (`|`). However, if a userscript name is a single word without any special characters, it can be used without quotes.
-Вы также можете исключить пользовательский скрипт, добавив перед ним символ `~`. В этом случае пользовательский скрипт не будет отключён модификатором.
+You can also exclude a userscript by adding a `~` character before it. In this case, the userscript will not be disabled by the modifier.
```adblock
$extension=~"userscript name"
@@ -1104,11 +1117,11 @@ $extension=~"userscript name"
:::note
-Исключая пользовательский скрипт из фильтрации, обязательно выносите символ `~` за кавычки.
+When excluding a userscript, you must place `~` outside the quotes.
:::
-Если имя пользовательского скрипта содержит кавычки (`"`), запятые (`,`) или вертикальную черту (`|`), они должны быть экранированы обратной косой чертой (`\`).
+If a userscript's name includes quotes (`"`), commas (`,`), or pipes (`|`), they must be escaped with a backslash (`\`).
```adblock
$extension="userscript name\, with \"quote\""
@@ -1133,7 +1146,7 @@ $extension="userscript name\, with \"quote\""
#### **`$jsinject`** {#jsinject-modifier}
-Запрещает добавлять JavaScript-код на страницу. О скриптлетах и javascript-правилах речь пойдёт ниже.
+Forbids adding of JavaScript code to the page. You can read about scriptlets and javascript rules further.
**Примеры**
@@ -1141,31 +1154,31 @@ $extension="userscript name\, with \"quote\""
##### Ограничения модификатора `$jsinject` {#jsinject-modifier-limitations}
-:::info Ограничения
+:::info Limitations
-Правила с модификатором [`$jsinject`][jsinject-in-mv3] не могут быть преобразованы в DNR в [AdGuard для Chrome MV3][ext-mv3]. Мы используем их только в движке [TSUrlFilter][] для отключения некоторых косметических правил.
+Rules with the [`$jsinject`][jsinject-in-mv3] modifier cannot be converted to DNR in [AdGuard for Chrome MV3][ext-mv3]. We only use them in the [TSUrlFilter][] engine to disable some cosmetic rules.
:::
:::info Совместимость
-Модификатор `$jsinject` не поддерживается AdGuard для Chrome MV3 ([пока что][jsinject-in-mv3]) и AdGuard Content Blocker.
+The `$jsinject` modifier is not supported by AdGuard for Chrome MV3 ([yet][jsinject-in-mv3]) and AdGuard Content Blocker.
:::
#### **`$stealth`** {#stealth-modifier}
-Отключает Защиту от трекинга (ранее Антитрекинг) для всех страниц и запросов, подходящих под это правило.
+Disables the Tracking protection (formerly Stealth Mode) module for all corresponding pages and requests.
-**Синтаксис**
+**Syntax**
```text
$stealth [= opt1 [| opt2 [| opt3 [...]]]]
```
-Здесь `opt(i)` — опции Защиты от трекинга, отключённые модификатором. Модификатор может содержать любое количество опций (см. ниже) или не содержать их вовсе. В последнем случае модификатор отключает Защиту от трекинга полностью.
+`opt(i)` stand for certain Tracking protection options disabled by the modifier. The modifier can contain any number of specific options (see below) or none. In the latter case the modifier disables all the Tracking protection features.
-Список доступных опций модификатора:
+The list of the available modifier options:
- `searchqueries` отключает опцию [**Скрывать поисковые запросы**](../../stealth-mode#searchqueries)
- `donottrack` отключает опцию [**Просить сайты не отслеживать вас**](../../stealth-mode#donottrack)
@@ -1192,7 +1205,7 @@ $stealth [= opt1 [| opt2 [| opt3 [...]]]]
:::note
-Блокировка куки и удаление параметров отслеживания достигается с помощью правил с модификаторами [`$cookie`](#cookie-modifier), [`$urltransform`](#urltransform-modifier) и [`$removeparam`](#removeparam-modifier). Правила-исключения, которые содержат только модификатор `$stealth`, не будут выполнять эти действия. Если вы хотите полностью отключить все функции Защиты от трекинга для определённого домена, нужно включить в правило все три модификатора: `@@||example.org^$stealth,removeparam,cookie`.
+Blocking cookies and removing tracking parameters is achieved by using rules with the [`$cookie`](#cookie-modifier), [`$urltransform`](#urltransform-modifier) and [`$removeparam`](#removeparam-modifier) modifiers. Exception rules that contain only the `$stealth` modifier will not do these things. If you want to completely disable all Tracking protection features for a given domain, you must include all three modifiers: `@@||example.org^$stealth,removeparam,cookie`.
:::
@@ -1213,7 +1226,7 @@ $stealth [= opt1 [| opt2 [| opt3 [...]]]]
#### **`$urlblock`** {#urlblock-modifier}
-Отключает все правила [`$cookie`](#cookie-modifier) и блокировку всех запросов со страниц, соответствующих правилу.
+Disables blocking of all requests sent from the pages matching the rule and disables all [`$cookie`](#cookie-modifier) rules.
**Примеры**
@@ -1221,23 +1234,23 @@ $stealth [= opt1 [| opt2 [| opt3 [...]]]]
##### Ограничения модификатора `$urlblock` {#urlblock-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-В AdGuard для iOS и AdGuard для Safari правила с `$urlblock` работают как [исключение $document](#document-modifier) — они разблокируют всё.
+In AdGuard for iOS and AdGuard for Safari, rules with `$urlblock` work as [$document exclusion](#document-modifier) — unblock everything.
:::
:::info Совместимость
-Правила с модификатором `$urlblock` не поддерживаются в AdGuard Content Blocker и AdGuard для Chrome MV3.
+Rules with `$urlblock` modifier are not supported by AdGuard Content Blocker, and AdGuard for Chrome MV3.
:::
#### Generic-правила {#exception-modifiers-generic-rules}
-Перед тем, как перейти к описанию следующих модификаторов, необходимо ввести определение *generic-правил*. Правило относится к generic-правилам, если его действие не ограничено конкретными доменами. Также поддерживается wildcard-символ `*`.
+Before we can proceed to the next modifiers, we have to make a definition of *generic rules*. The rule is generic if it is not limited to specific domains. Wildcard character `*` is supported as well.
-Например, это generic-правила:
+For example, these rules are generic:
```adblock
###banner
@@ -1249,7 +1262,7 @@ $stealth [= opt1 [| opt2 [| opt3 [...]]]]
||domain.com^$domain=~example.com
```
-А это уже не generic-правила:
+And these are not:
```adblock
domain.com###banner
@@ -1258,7 +1271,7 @@ domain.com###banner
#### **`$genericblock`** {#genericblock-modifier}
-Отключает все базовые generic-правила на страницах, подходящих под правило-исключение.
+Disables generic basic rules on pages that correspond to exception rule.
**Примеры**
@@ -1266,21 +1279,21 @@ domain.com###banner
##### Ограничения модификатора `$genericblock` {#genericblock-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-В AdGuard для iOS и AdGuard для Safari правила `$genericblock` работают как [исключение $document](#document-modifier) — они разблокируют всё.
+In AdGuard for iOS and AdGuard for Safari, rules with `$genericblock` work as [$document exclusion](#document-modifier) — unblock everything.
:::
:::info Совместимость
-Правила с модификатором `$genericblock` не поддерживаются в AdGuard Content Blocker и AdGuard для Chrome MV3.
+Rules with `$genericblock` modifier are not supported by AdGuard Content Blocker, and AdGuard for Chrome MV3.
:::
#### **`$generichide`** {#generichide-modifier}
-Отключает все [косметические правила](#cosmetic-rules) generic на страницах, соответствующих правилу-исключению.
+Disables all generic [cosmetic rules](#cosmetic-rules) on pages that correspond to the exception rule.
**Примеры**
@@ -1288,13 +1301,13 @@ domain.com###banner
:::note
-Вы можете использовать более короткое имя (псевдоним) вместо полного имени модификатора: `$ghide`.
+You may use a shorter name (alias) instead of using the full modifier name: `$ghide`.
:::
#### **`specifichide`** {#specifichide-modifier}
-Отключает все specific-правила скрытия элементов и CSS-правила, но не отключает general-правила. Имеет эффект, противоположный [`$generichide`](#generichide-modifier).
+Disables all specific element hiding and CSS rules, but not general ones. Has an opposite effect to [`$generichide`](#generichide-modifier).
**Примеры**
@@ -1302,25 +1315,25 @@ domain.com###banner
:::note
-Вы можете использовать более короткое имя (псевдоним) вместо полного имени модификатора: `$shide`.
+You may use a shorter name (alias) instead of using the full modifier name: `$shide`.
:::
:::note
-Все косметические правила, а не только specific, можно отключить модификатором [`$elemhide`](#elemhide-modifier).
+All cosmetic rules — not just specific ones — can be disabled by [`$elemhide` modifier](#elemhide-modifier).
:::
:::info Совместимость
-Правила с модификатором `$specifichide` не поддерживаются в AdGuard для iOS, AdGuard для Safari и AdGuard Content Blocker.
+Rules with `$specifichide` modifier are not supported by AdGuard for iOS, AdGuard for Safari, and AdGuard Content Blocker.
:::
### Расширенные возможности {#advanced-modifiers}
-Модификаторы, описанные в этом разделе, полностью меняют поведение базовых правил.
+These modifiers are able to completely change the behavior of basic rules.
@@ -1359,7 +1372,7 @@ domain.com###banner
#### **`$all`** {#all-modifier}
-Модификатор `$all` состоит из [всех модификаторов content-type](#content-type-modifiers) и [`$popup`](#popup-modifier). Например, правило `||example.org^$all` конвертируется в правило:
+`$all` modifier is made of [all content-types modifiers](#content-type-modifiers) and [`$popup`](#popup-modifier). E.g. rule `||example.org^$all` is converting into rule:
```adblock
||example.org^$document,subdocument,font,image,media,object,other,ping,script,stylesheet,websocket,xmlhttprequest,popup
@@ -1367,27 +1380,27 @@ domain.com###banner
:::caution Ограничения
-Этот модификатор нельзя использовать как исключение с маркером `@@`.
+This modifier cannot be used as an exception with the `@@` mark.
:::
##### Ограничения модификатора `$all` {#all-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-Так как `$popup` является частью `$all`, модификатор `$all` не поддерживается в AdGuard для Chrome MV3 из-за ограничений модификатора [`$popup`](#popup-modifier-limitations).
+Since `$popup` is a part if `$all`, the `$all` modifier is not supported by AdGuard for Chrome MV3 because of [`$popup` modifier limitations](#popup-modifier-limitations).
:::
:::info Совместимость
-Правила с модификатором `$all` не поддерживаются в AdGuard Content Blocker.
+Rules with `$all` modifier are not supported by AdGuard Content Blocker.
:::
#### **`$badfilter`** {#badfilter-modifier}
-Правила, содержащие модификатор `$badfilter`, отключают другие базовые правила, на которые они ссылаются. Это означает, что текст отключённого правила должен соответствовать тексту `$badfilter`-правила (за исключением самого модификатора `$badfilter`).
+The rules with the `$badfilter` modifier disable other basic rules to which they refer. It means that the text of the disabled rule should match the text of the `$badfilter` rule (without the `$badfilter` modifier).
**Примеры**
@@ -1396,12 +1409,12 @@ domain.com###banner
- `@@||example.com$badfilter` отключает `@@||example.com`
- `||example.com$domain=domain.com,badfilter` отключает `||example.com$domain=domain.com`
-Правила с модификатором `$badfilter` могут отключать другие базовые правила для определённых доменов, если они соответствуют следующим условиям:
+Rules with `$badfilter` modifier can disable other basic rules for specific domains if they fulfill the following conditions:
-1. В правиле есть модификатор `$domain`
-1. В модификаторе `$domain` нет отрицания домена `~`
+1. The rule has a `$domain` modifier
+1. The rule does not have a negated domain `~` in `$domain` modifier value
-В этом случае, правило с `$badfilter` отключит соответствующее правило для доменов, указанных как в правиле с `$badfilter`, так и в базовом правиле. Обратите внимание, что [логика wildcard для доменов верхнего уровня (TLD)](#wildcard-for-tld) здесь также применима.
+In that case, the `$badfilter` rule will disable the corresponding rule for domains specified in both the `$badfilter` and basic rules. Please note that [wildcard-TLD logic](#wildcard-for-tld) works here as well.
**Примеры**
@@ -1414,52 +1427,52 @@ domain.com###banner
##### Ограничения модификатора `$badfilter` {#badfilter-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-В [AdGuard для Chrome MV3][ext-mv3] правило с модификатором `$badfilter` применяется в DNR только в том случае, если оно полностью отменяет исходное правило. Мы не можем рассчитать его, если оно отменено лишь частично. [Примеры][badfilter-in-mv3].
+In [AdGuard for Chrome MV3][ext-mv3] a rule with the `$badfilter` modifier is applied in DNR only if it fully cancels the source rule. We cannot calculate it if it is only partially canceled. [Examples][badfilter-in-mv3].
:::
:::info Совместимость
-Правила с модификатором `$badfilter` не поддерживаются в AdGuard Content Blocker.
+Rules with `$badfilter` modifier are not supported by AdGuard Content Blocker.
:::
#### **`$cookie`** {#cookie-modifier}
-Модификатор `$cookie` полностью меняет поведение правила. Вместо того, чтобы блокировать запрос, этот модификатор позволяет AdGuard блокировать или изменять заголовки `Cookie` или `Set-Cookie`.
+The `$cookie` modifier completely changes rule behavior. Instead of blocking a request, this modifier makes AdGuard suppress or modify the `Cookie` and `Set-Cookie` headers.
-**Несколько правил, соответствующих одному запросу**
+**Multiple rules matching a single request**
-В случае, когда несколько правил `$cookie` соответствуют одному запросу, мы применим каждое из них по очереди.
+In case if multiple `$cookie` rules match a single request, we will apply each of them one by one.
-**Синтаксис**
+**Syntax**
```adblock
$cookie [= name[; maxAge = seconds [; sameSite = strategy ]]]
```
-где:
+where:
- **`name`** — опционально, строка или регулярное выражение для сопоставления с именем куки.
- **`seconds`** — количество секунд, на которое сместится истечение срока действия куки.
- **`strategy`** — строка для стратегии [Same-Site](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Set-Cookie/SameSite), которая будет применена к куки.
-Например,
+For example,
```adblock
||example.org^$cookie=NAME;maxAge=3600;sameSite=lax
```
-каждый раз, когда AdGuard встречает куки с именем `NAME` в запросе к `example.org`, он будет делать следующее:
+every time AdGuard encounters a cookie called `NAME` in a request to `example.org`, it will do the following:
- Установит дату истечения срока хранения на текущее время плюс `3600` секунд
- Позволяет куки использовать стратегию [Same-Site](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Set-Cookie/SameSite).
-**Экранирование специальных символов**
+**Escaping special characters**
-Если для сопоставления используется регулярное выражение `name`, необходимо экранировать два символа: запятую `,` и знак доллара `$`. Используйте обратный слеш `\` для экранирования каждого из них. Например, экранированная запятая будет выглядеть так: `\,`.
+If regular expression `name` is used for matching, two characters must be escaped: comma `,` and dollar sign `$`. Use backslash `\` to escape each of them. For example, escaped comma looks like this: `\,`.
**Примеры**
@@ -1468,7 +1481,7 @@ $cookie [= name[; maxAge = seconds [; sameSite = strategy ]]]
- `$cookie=/__utm[a-z]/` блокирует куки Google Analytics везде
- `||facebook.com^$third-party,cookie=c_user` не позволяет Facebook отслеживать вас, даже если вы вошли в систему
-Существует два способа деактивации правил `$cookie`: основной предполагает использование исключения с `@@` — `@@||example.org^$cookie`. Альтернативный метод использует исключение `$urlblock` (также входящее в псевдоним исключения `$document` — `$elemhide,jsinject,content,urlblock,extension`). Вот как это работает:
+There are two methods to deactivate `$cookie` rules: the primary method involves using an exception marked with `@@` — `@@||example.org^$cookie`. The alternative method employs a `$urlblock` exception (also included under the `$document` exception alias — `$elemhide,jsinject,content,urlblock,extension`). Here's how it works:
- `@@||example.org^$cookie` разблокирует все куки-файлы, установленные `example.org`
- `@@||example.org^$urlblock` разблокирует все файлы куки, установленные `example.org`, и отключает блокировку всех запросов, отправленных с `example.org`
@@ -1477,45 +1490,45 @@ $cookie [= name[; maxAge = seconds [; sameSite = strategy ]]]
##### Ограничения модификатора `$cookie` {#cookie-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-В [AdGuard for Chrome MV3][ext-mv3] мы удаляем куки двумя способами: из `content-script`, к которому у нас есть доступ, и из слушателя событий `onBeforeSendHeaders`. Поскольку `onBeforeSendHeaders` и другие слушатели больше не блокируют выполнение запроса, мы не можем удалить их во всех случаях. Вы можете проверить, работает ли правило, [с помощью этого теста](https://testcases.agrd.dev/Filters/cookie-rules/test-cookie-rules).
+In [AdGuard for Chrome MV3][ext-mv3] we delete cookies in 2 ways: from `content-script` side (to which we have access) and from `onBeforeSendHeaders` listener. Since `onBeforeSendHeaders` and other listeners are no longer blocking, we are not able to delete them in all cases. You can check if a rule works with [this test](https://testcases.agrd.dev/Filters/cookie-rules/test-cookie-rules).
:::
:::caution Ограничения
-Правила `$cookie` поддерживают эти типы модификаторов: `$domain`, `$~domain`, `$important`, `$third-party`, `$~third-party`, `strict-third-party` и `strict-first-party`.
+`$cookie` rules support these types of modifiers: `$domain`, `$~domain`, `$important`, `$third-party`, `$~third-party`, `strict-third-party`, and `strict-first-party`.
:::
:::info Совместимость
-Правила с модификатором `$cookie` не поддерживаются в AdGuard Content Blocker, AdGuard для iOS и AdGuard для Safari.
+Rules with `$cookie` modifier are not supported by AdGuard Content Blocker, AdGuard for iOS, and AdGuard for Safari.
:::
#### **`$csp`** {#csp-modifier}
-Этот модификатор полностью меняет поведение правила. Когда он применяется к правилу, оно не блокирует соответствующий запрос. Вместо этого изменяются заголовки ответа.
+This modifier completely changes the rule behavior. If it is applied to a rule, the rule will not block the matching request. Response headers will be modified instead.
:::info
-Чтобы использовать правила этого типа, необходимо базовое понимание слоя безопасности [Content Security Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy).
+In order to use this type of rules, it is required to have the basic understanding of the [Content Security Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy) security layer.
:::
-Для запросов, подходящих под `$csp`-правило, мы усилим политику безопасности ответа, добавив дополнительную политику, равнозначную содержимому модификатора `$csp`. Правила `$csp` применяются независимо от правил любого другого типа. На него могут повлиять **только исключения на уровне документа** (см. раздел с примерами), но никак не другие базовые правила.
+For the requests matching a `$csp` rule, we will strengthen response security policy by enhancing the content security policy, similar to the content security policy of the `$csp` modifier contents. `$csp` rules are applied independently from any other rule type. **Only document-level exceptions** can influence it (see the examples section), but no other basic rules.
-**Несколько правил, соответствующих одному запросу**
+**Multiple rules matching a single request**
-В случае, когда несколько правил `$csp` соответствуют одному запросу, мы применим каждое из них.
+In case if multiple `$csp` rules match a single request, we will apply each of them.
-**Синтаксис**
+**Syntax**
-Синтаксис значений `$csp` похож на синтаксис заголовков Политики Безопасности Контента.
+`$csp` value syntax is similar to the Content Security Policy header syntax.
-Значение `$csp` может быть пустым в случае правил-исключений. См. примеры ниже.
+`$csp` value can be empty in the case of exception rules. See examples section below.
**Примеры**
@@ -1535,45 +1548,45 @@ $cookie [= name[; maxAge = seconds [; sameSite = strategy ]]]
:::info Совместимость
-Правила с модификатором `$csp` не поддерживаются в AdGuard Content Blocker, AdGuard для iOS и AdGuard для Safari.
+Rules with `$csp` modifier are not supported by AdGuard Content Blocker, AdGuard for iOS and AdGuard for Safari.
:::
#### **`$hls`** {#hls-modifier}
-Правила `$hls` модифицируют ответ на соответствующий правилу запрос. Они предназначены для удаления сегментов из [HLS-плейлистов (RFC 8216)](https://datatracker.ietf.org/doc/html/rfc8216).
+`$hls` rules modify the response of a matching request. They are intended as a convenient way to remove segments from [HLS playlists (RFC 8216)](https://datatracker.ietf.org/doc/html/rfc8216).
:::note
-Слово segment в документации означает Media Segment или playlist (как часть Master Playlist): с точки зрения правил `$hls`, Master Playlist и Media Playlist неразличимы.
+The word "segment" in this document means either a "Media Segment" or a "playlist" as part of a "Master Playlist": `$hls` rules do not distinguish between a "Master Playlist" and a "Media Playlist".
:::
-**Синтаксис**
+**Syntax**
- `||example.org^$hls=urlpattern` удаляет сегменты, URL которых соответствует паттерну `urlpattern`. Паттерн работает так же, как в базовых URL-правилах, однако символы `/`, `$` и `,` в составе `urlpattern` необходимо экранировать с помощью `\`.
- `||example.org^$hls=/regexp/options` удаляет сегменты, в которых URL-адрес или один из тегов (для определённых параметров, если они есть) соответствуют регулярному выражению `regexp`. Доступные значения `options`:
- `t` — вместо URL-адреса сегмента проверять каждый тег сегмента на соответствие регулярному выражению. Сегмент с соответствующим тегом будет удалён;
- `i` — сделать регулярное выражение нечувствительным к регистру символов.
-Символы `/`, `$` и `,` должны быть экранированы символом `\` внутри `regexp`.
+The characters `/`, `$` and `,` must be escaped with `\` inside `regexp`.
**Исключения**
-Базовые URL-исключения не должны отключать правила с модификатором `$hls`. Отключить их можно следующим образом:
+Basic URL exceptions shall not disable rules with the `$hls` modifier. They can be disabled as described below:
- `@@||example.org^$hls` отключает все правила `$hls` для ответов от URL-адресов, соответствующих `||example.org^ URL`.
- `@@||example.org^$hls=text` отключает все правила `$hls`, у которых значение модификатора `$hls` равно `text`, для ответов с URL-адресов, соответствующих `||example.org^ URL`.
:::tip
-`$hls` также можно отключить с помощью правил-исключений с модификаторами `$document`, `$content` и `$urlblock`.
+`$hls` rules can also be disabled by `$document`, `$content` and `$urlblock` exception rules.
:::
:::note
-Если несколько правил `$hls` соответствуют одному и тому же запросу, их эффект суммируется.
+When multiple `$hls` rules match the same request, their effect is cumulative.
:::
@@ -1583,26 +1596,26 @@ $cookie [= name[; maxAge = seconds [; sameSite = strategy ]]]
- `||example.org^$hls=/\/videoplayback\/?\?.*\&source=dclk_video_ads/i` делает почти то же самое, но с помощью регулярного выражения вместо URL-паттерна.
- `||example.org^$hls=/#UPLYNK-SEGMENT:.*\,ad/t` удаляет все сегменты с соответствующим тегом.
-**О формате HLS-плейлистов**
+**Anatomy of an HLS playlist**
-Краткое описание [спецификации](https://datatracker.ietf.org/doc/html/rfc8216):
+A quick summary of the [specification](https://datatracker.ietf.org/doc/html/rfc8216):
-1. HLS-плейлист — это набор текстовых строк
-1. Можно использовать пустую строку, комментарий (начинается с `#`), тег (тоже начинается с `#`, распознаётся по содержанию) или URL
-1. Строка с URL называется сегментом
-1. Тег может относиться к одному сегменту, т.е. к первой строке с URL, следующей после данного тега, ко всем последующим сегментам (пока не встретится тег с тем же названием) или ко всему плейлисту
+1. An HLS playlist is a collection of text lines
+1. A line may be empty, a comment (starts with `#`), a tag (also starts with `#`, can only be recognized by name) or a URL
+1. A URL line is called a "segment"
+1. Tags may apply to a single segment, i.e. the first URL line after the tag, to all segments following the tag and until the tag with the same name, or to the whole playlist
-Замечания, касающиеся правил `$hls`:
+Some points specific to the operation of `$hls` rules:
-1. Когда сегмент удаляется, все теги, относящиеся только к нему, тоже удаляются
-1. Теги, относящиеся к нескольким сегментам, удаляются, если все эти сегменты были удалены
-1. Поскольку различные типы тегов невозможно распознать по синтаксису, мы распознаем все теги, указанные в RFC, плюс некоторые нестандартные теги, которые встречались нам в полевых условиях. Любые строки, начинающиеся с `#` и не распознанные как тег, пропускаются без модификации и не сопоставляются с правилами
-1. Теги не будут сопоставлены, если они применяются ко всему списку воспроизведения, а правила `$hls` нельзя использовать для их удаления, поскольку эти типы правил предназначены для удаления сегментов. Если вы знаете, что делаете, вы можете использовать правила `$replace` для удаления или перезаписи только одного тега из плейлиста
+1. When a segment is removed, all of the tags that apply only to that segment are also removed
+1. When there is a tag that applies to multiple segments, and all of those segments are removed, the tag is also removed
+1. Since there is no way to recognize different kinds of tags by syntax, we recognize all of the tags specified by the RFC, plus some non-standard tags that we have seen in the field. Any lines starting with `#` and not recognized as a tag are passed through without modification, and are not matched against the rules
+1. Tags will not be matched if they apply to the entire playlist, and `$hls` rules cannot be used to remove them, as these rule types are intended for segment removals. If you know what you are doing, you can use `$replace` rules to remove or rewrite just a single tag from the playlist
-**Пример работы правил:**
+**An example of a transformation done by the rules:**
-Исходный ответ
+Original response
```text
#EXTM3U
@@ -1629,7 +1642,7 @@ preroll.ts
-Применённые правила
+Applied rules
```adblock
||example.org^$hls=preroll
@@ -1639,7 +1652,7 @@ preroll.ts
-Модифицированный ответ
+Modified response
```text
#EXTM3U
@@ -1667,13 +1680,13 @@ preroll.ts
:::info Совместимость
-Правила с модификатором `$hls` поддерживаются AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.10 или выше.
+Rules with the `$hls` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.10 or later.
:::
#### **`$inline-script`** {#inline-script-modifier}
-Модификатор `$inline-script` предназначен для блокировки встроенного в страницу кода JavaScript с использованием политики безопасности контента (CSP). Он повышает безопасность, не позволяя загружать встроенную рекламу или потенциально вредоносные скрипты. Правило `||example.org^$inline-script` конвертируется в правило синтаксиса CSP:
+The `$inline-script` modifier is designed to block inline JavaScript embedded into the web page, using Content Security Policy (CSP). It improves security and privacy by preventing application of inline ads or potentially malicious scripts. The rule `||example.org^$inline-script` is converting into the CSP-syntax rule:
```adblock
||example.org^$csp=script-src 'self' 'unsafe-eval' http: https: data: blob: mediastream: filesystem:
@@ -1681,7 +1694,7 @@ preroll.ts
#### **`$inline-font`** {#inline-font-modifier}
-Модификатор `$inline-font` предназначен для блокировки встроенных в страницу шрифтов с использованием политики безопасности контента (CSP). Он повышает безопасность, не позволяя загружать встроенные шрифты, которые могут использоваться для сбора данных и фингерпринтинга. Правило `||example.org^$inline-font` конвертируется в правило синтаксиса CSP:
+The `$inline-font` modifier is designed to block inline fonts embedded into the web page, using Content Security Policy (CSP). It improves security and privacy by preventing application of inline fonts that could be used for data collection and fingerprinting. The rule `||example.org^$inline-font` is converting into the CSP-syntax rule:
```adblock
||example.org^$csp=font-src 'self' 'unsafe-eval' http: https: data: blob: mediastream: filesystem:
@@ -1689,46 +1702,46 @@ preroll.ts
#### **`$jsonprune`** {#jsonprune-modifier}
-Правила `$jsonprune` модифицируют ответ на соответствующий запрос, удаляя JSON-элементы, которые соответствуют модифицированному выражению [JSONPath](https://goessner.net/articles/JsonPath/). Эти правила не изменяют ответы, которые не являются действительными JSON-документами.
+`$jsonprune` rules modify the response to a matching request by removing JSON items that match a modified [JSONPath](https://goessner.net/articles/JsonPath/) expression. They do not modify responses which are not valid JSON documents.
-В AdGuard для Windows, Mac и Android [с CoreLibs][] версии 1.11 или выше `$jsonprune` также поддерживает модификацию документов JSONP (padded JSON).
+In AdGuard for Windows, Mac, and Android with [CoreLibs][] v1.11 or later, `$jsonprune` also supports modifying JSONP (padded JSON) documents.
-**Синтаксис**
+**Syntax**
- `||example.org^$jsonprune=expression` удаляет из ответа элементы, соответствующие изменённому JSONPath-выражению `expression`.
-Из-за особенностей работы парсинга правил символы `$` и `,` внутри `expression` должны экранироваться символом `\`.
+Due to the way rule parsing works, the characters `$` and `,` must be escaped with `\` inside `expression`.
-Модифицированный синтаксис JSONPath имеет следующие отличия от оригинального:
+The modified JSONPath syntax has the following differences from the original:
-1. Выражения на сценарном языке (script expressions) не поддерживаются
-1. Поддерживаемые предикаты (filter expressions):
- - `?(has )` — верно, если текущий объект содержит указанный ключ
- - `?(key-eq )` — верно, если текущий объект содержит указанный ключ и его значение равно указанному
- - `?(key-substr )` — верно, если указанное значение является подстрокой значения ключа текущего объекта
-1. Пробелы вне двойных или одинарных кавычек игнорируются
-1. Можно использовать строки как с двойными, так и с одинарными кавычками
-1. Выражения, оканчивающиеся на `..`, не поддерживаются
-1. Разрешено указывать несколько срезов массива (array slices) в квадратных скобках
+1. Script expressions are not supported
+1. The supported filter expressions are:
+ - `?(has )` — true if the current object has the specified key
+ - `?(key-eq )` — true if the current object has the specified key, and its value is equal to the specified value
+ - `?(key-substr )` — true if the specified value is a substring of the value of the specified key of the current object
+1. Whitespace outside of double- or single-quoted strings has no meaning
+1. Both double- and single-quoted strings can be used
+1. Expressions ending with `..` are not supported
+1. Multiple array slices can be specified in square brackets
-Существуют различные онлайн-инструменты, которые делают работу с выражениями JSONPath удобнее:
+There are various online tools that make working with JSONPath expressions more convenient:
https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfinder.com/ https://jsonpath.com/
-Обратите внимание, что различные имплементации JSONPath обладают уникальными особенностями и могут быть несовместимы друг с другом.
+Keep in mind, though, that all JSONPath implementations have unique features/quirks and are subtly incompatible with each other.
**Исключения**
-Базовые URL-исключения не должны отключать правила с модификатором `$jsonprune`. Отключить их можно следующим образом:
+Basic URL exceptions shall not disable rules with the `$jsonprune` modifier. They can be disabled as described below:
- `@@||example.org^$jsonprune` отключает все правила `$jsonprune` для ответов от URL-адресов, соответствующих `||example.org^`.
- `@@||example.org^$jsonprune=text` отключает все правила `$jsonprune`, у которых значение модификатора `$jsonprune` равно `text`, для ответов с URL-адресов, соответствующих `||example.org^ URL`.
-`$jsonprune` также можно отключить с помощью правил-исключений с модификаторами `$document`, `$content` и `$urlblock`.
+`$jsonprune` rules can also be disabled by `$document`, `$content` and `$urlblock` exception rules.
:::note
-Когда одному и тому же запросу соответствует несколько правил с модификатором `$jsonprune`, они сортируются в лексикографическом порядке: первое правило применяется к исходному ответу, а каждое из оставшихся правил применяется к результату применения предыдущего.
+When multiple `$jsonprune` rules match the same request, they are sorted in lexicographical order, the first rule is applied to the original response, and each of the remaining rules is applied to the result of applying the previous one.
:::
@@ -1737,7 +1750,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
- `||example.org^$jsonprune=\$..[one\, "two three"]` удаляет все вхождения ключей one и two three в любом месте JSON-документа.
-До
+Input
```json
{
@@ -1752,7 +1765,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
-После
+Output
```json
{
@@ -1767,7 +1780,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
- `||example.org^$jsonprune=\$.a[?(has ad_origin)]` удаляет всех прямых потомков `a`, которые обладают свойством `ad_origin`.
-До
+Input
```json
{
@@ -1786,7 +1799,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
-После
+Output
```json
{
@@ -1803,7 +1816,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
- `||example.org^$jsonprune=\$.*.*[?(key-eq 'Some key' 'Some value')]` удаляет все элементы на уровне вложенности 3, обладающие свойством Some key, равным Some value.
-До
+Input
```json
{
@@ -1815,7 +1828,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
-После
+Output
```json
{
@@ -1826,14 +1839,14 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
-**Вложенные выражения JSONPath**
+**Nested JSONPath expressions**
-В AdGuard для Windows, Mac и Android [с CoreLibs][] версии 1.11 или выше выражения JSONPath могут быть использованы как ключи в выражениях фильтра.
+In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPath expressions may be used as keys in filter expressions.
- `||example.org^$jsonprune=\$.elems[?(has "\$.a.b.c")]` удаляет всех прямых потомков `elems`, которые обладают свойством, выбираемым JSONPath-выражением `$.a.b.c`.
-До
+Input
```json
{
@@ -1853,7 +1866,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
-После
+Output
```json
{
@@ -1871,13 +1884,13 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
- `||example.org^$jsonprune=\$.elems[?(key-eq "\$.a.b.c" "abc")]` удаляет всех прямых потомков `elems`, которые обладают свойством, выбираемым выражением JSONPath `$.a.b.c` со значением, равным `"abc"`.
-До
+Input
```json
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
@@ -1889,7 +1902,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
-После
+Output
```json
{
@@ -1912,32 +1925,32 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
:::info Совместимость
-Правила с модификатором `$jsonprune` поддерживаются в AdGuard для Windows, AdGuard для Mac и AdGuard для Android с [CoreLibs][] версии 1.10 или выше.
+Rules with the `$jsonprune` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.10 or later.
:::
#### **`$xmlprune`** {#xmlprune-modifier}
-Правила `$xmlprune` модифицируют ответ на соответствующий запрос, удаляя XML-элементы, которые соответствуют модифицированному выражению [XPath 1.0](https://www.w3.org/TR/1999/REC-xpath-19991116/). Выражение должно возвращать [набор узлов](https://www.w3.org/TR/1999/REC-xpath-19991116/#node-sets). Правила `$xmlprune` не изменяют ответы, которые не являются правильно сформированными XML-документами.
+`$xmlprune` rules modify the response to a matching request by removing XML items that match an [XPath 1.0](https://www.w3.org/TR/1999/REC-xpath-19991116/) expression. The expression must return a [node-set](https://www.w3.org/TR/1999/REC-xpath-19991116/#node-sets). `$xmlprune` rules do not modify responses which are not well-formed XML documents.
-**Синтаксис**
+**Syntax**
- `||example.org^$xmlprune=expression` удаляет из ответа элементы, соответствующие XPath-выражению `expression`.
-Из-за особенностей работы парсинга правил символы `$` и `,` внутри `expression` должны экранироваться символом `\`.
+Due to the way rule parsing works, the characters `$` and `,` must be escaped with `\` inside `expression`.
**Исключения**
-Базовые URL-исключения не должны отключать правила с модификатором `$xmlprune`. Отключить их можно следующим образом:
+Basic URL exceptions shall not disable rules with the `$xmlprune` modifier. They can be disabled as described below:
- `@@||example.org^$xmlprune` отключает все правила `$xmlprune` для ответов от URL-адресов, соответствующих `||example.org^`.
- `@@||example.org^$xmlprune=text` отключает все правила `$xmlprune`, у которых значение модификатора `$xmlprune` равно `text`, для ответов с URL-адресов, соответствующих `||example.org^ URL`.
-`$xmlprune` также можно отключить с помощью правил-исключений с модификаторами `$document`, `$content` и `$urlblock`.
+`$xmlprune` rules can also be disabled by `$document`, `$content` and `$urlblock` exception rules.
:::note
-Если одному и тому же запросу соответствует несколько правил `$xmlprune`, они применяются в лексикографическом порядке.
+When multiple `$xmlprune` rules match the same request, they are applied in lexicographical order.
:::
@@ -1946,7 +1959,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
- `||example.org^$xmlprune=/bookstore/book[position() mod 2 = 1]` удаляет книги с нечётными номерами из книжного магазина.
-До
+Input
```xml
@@ -1991,7 +2004,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
-После
+Output
```xml
@@ -2024,7 +2037,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
- `||example.org^$xmlprune=/bookstore/book[year = 2003]` удаляет книги за 2003 год из книжного магазина.
-До
+Input
```xml
@@ -2069,7 +2082,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
-После
+Output
```xml
@@ -2102,7 +2115,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
- `||example.org^$xmlprune=//*/@*` удаляет все атрибуты из всех элементов.
-До
+Input
```xml
@@ -2122,7 +2135,7 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
-После
+Output
```xml
@@ -2150,24 +2163,24 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
:::info Совместимость
-Правила с модификатором `$xmlprune` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.15 или выше.
+Rules with the `$xmlprune` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.15 or later.
:::
#### **`$network`** {#network-modifier}
-По сути, это правила типа Firewall, позволяющие полностью блокировать или разблокировать доступ к указанному удалённому адресу.
+This is basically a Firewall-like rule allowing to fully block or unblock access to a specified remote address.
-1. Правила `$network` соответствуют **только IP-адресам**! Вы не можете использовать их, чтобы блокировать или разблокировать доступ к домену.
-2. Чтобы сопоставить адрес IPv6, вы должны использовать сжатый синтаксис, например, использовать `[2001:4860:4860::8888]$network` вместо `[2001:4860:4860:0:0:0:0:8888]$network`.
-3. Правило белого списка `$network` заставляет AdGuard обходить данные до соответствующей конечной точки, поэтому никакой дальнейшей фильтрации не будет.
-4. Если часть IP начинается и заканчивается символом `/`, она рассматривается как регулярное выражение.
+1. `$network` rules match **IP addresses only**! You cannot use them to block or unblock access to a domain.
+2. To match an IPv6 address, you have to use the collapsed syntax, e.g. use `[2001:4860:4860::8888]$network` instead of `[2001:4860:4860:0:0:0:0:8888]$network`.
+3. An allowlist `$network` rule makes AdGuard bypass data to the matching endpoint, hence there will be no further filtering at all.
+4. If the IP part starts and ends with `/` character, it is treated as a regular expression.
-Рекомендуем ознакомиться [с этой статьёй](#regexp-support) для лучшего понимания регулярных выражений.
+We recommend to get acquainted with this [article](#regexp-support) for better understanding of regular expressions.
:::caution Ограничения
-Модификатор `$network` можно использовать в правилах только вместе с модификаторами `$app` и `$important`, но не с какими-либо другими модификаторами.
+The `$network` modifier can only be used in rules together with the `$app` and `$important` modifiers, and not with any other modifiers.
:::
@@ -2182,32 +2195,32 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
:::info Совместимость
-Только в AdGuard для Windows, Mac и Android есть технические возможности для поддержки правил с модификатором `$network`.
+Only AdGuard for Windows, Mac, and Android are technically capable of using rules with `$network` modifier.
:::
#### **`$permissions`** {#permissions-modifier}
-Этот модификатор полностью меняет поведение правила. Когда он применяется, правило не блокирует соответствующий запрос. Вместо этого изменяются заголовки ответа.
+This modifier completely changes the rule behavior. If it is applied to a rule, the rule will not block the matching request. Response headers will be modified instead.
:::info
-Чтобы использовать правила этого типа, необходимо базовое понимание слоя безопасности [Permissions Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/Permissions_Policy).
+In order to use this type of rules, it is required to have a basic understanding of the [Permissions Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/Permissions_Policy) security layer.
:::
-Для запросов, соответствующих правилу `$permissions`, AdGuard усиливает «политику разрешений» ответа, добавляя дополнительную политику, равную содержимому модификатора `$permissions`. Правила `$permissions` применяются независимо от правил любого другого типа. На него могут повлиять **только исключения на уровне документа** (см. раздел с примерами), но никак не другие базовые правила.
+For the requests matching a `$permissions` rule, AdGuard strengthens response's permissions policy by adding an additional permission policy equal to the `$permissions` modifier contents. `$permissions` rules are applied independently from any other rule type. **Only document-level exceptions** can influence it (see the examples section), but no other basic rules.
-**Синтаксис**
+**Syntax**
-Синтаксис значений `$permissions` идентичен [синтаксису](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Permissions-Policy) заголовка `Permissions-Policy` со следующими исключениями:
+`$permissions` value syntax is identical to that of the `Permissions-Policy` header [syntax](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Permissions-Policy) with the following exceptions:
-1. Запятая, разделяющая несколько функций, **должна быть экранирована** — см. примеры ниже.
-2. Вместо запятой для разделения функций можно использовать символ вертикальной черты (`|`).
+1. A comma that separates multiple features **MUST** be escaped — see examples below.
+2. A pipe character (`|`) can be used instead of a comma to separate features.
-[Список доступных директив](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Permissions-Policy#directives)
+The list of available directives is available [here](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Permissions-Policy#directives).
-Значение `$permissions` может быть пустым в случае правил исключения — смотрите примеры ниже.
+`$permissions` value can be empty in the case of exception rules — see examples below.
**Примеры**
@@ -2220,29 +2233,29 @@ https://www.site24x7.com/tools/jsonpath-finder-validator.html https://jsonpathfi
:::note
-Правила `$permissions` действуют только для запросов основного фрейма и подфреймов. Это означает, что они применяются при загрузке страницы или при загрузке iframe.
+`$permissions` rules only take effect for main frame and sub frame requests. This means they are applied when a page is loaded or when an iframe is loaded.
:::
:::note
-Если имеется несколько правил `$permissions`, соответствующих одному и тому же запросу, к ответу для каждого правила будут добавлены несколько заголовков `Permissions-Policy` со своими значениями `$permissions`. Итак, если у вас есть два правила: `||example.org^$permissions=autoplay=()` и `||example.org^$permissions=geolocation=()\,camera=()`, которые соответствуют одному и тому же запросу, ответ будет содержать два заголовка `Permissions-Policy`: `autoplay=()` и `geolocation=()\,camera=()`.
+If there are multiple `$permissions` rules that match the same request, multiple `Permissions-Policy` headers will be added to the response for each rule with their `$permissions` value. So if you have two rules: `||example.org^$permissions=autoplay=()` and `||example.org^$permissions=geolocation=()\,camera=()` that match the same request, the response will contain two `Permissions-Policy` headers: `autoplay=()` and `geolocation=()\,camera=()`.
:::
##### Ограничения модификатора `$permissions` {#permissions-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-Firefox игнорирует заголовок `Permissions-Policy`. Подробнее см. [на сайте Bugzilla](https://bugzilla.mozilla.org/show_bug.cgi?id=1694922).
+Firefox ignores the `Permissions-Policy` header. For more information, see [this issue](https://bugzilla.mozilla.org/show_bug.cgi?id=1694922).
:::
:::caution Ограничения
-1. В модификаторе `$permissions` запрещён символ `$`.
-2. `$permissions` совместим с ограниченным набором модификаторов: `$domain`, `$important`, `$subdocument` и [модификаторами типа контента](#content-type-modifiers).
-3. Правила с модификатором `$permissions`, не содержащие [модификаторов типа контента](#content-type-modifiers), будут применяться только к тем запросам, которые имеют тип контента `document`.
+1. Characters forbidden in the `$permissions` value: `$`.
+2. `$permissions` is compatible with a limited set of modifiers: `$domain`, `$important`, `$subdocument`, and [content-type modifiers](#content-type-modifiers).
+3. `$permissions` rules that do not have any [content-type modifiers](#content-type-modifiers) will match only requests where content type is `document`.
:::
@@ -2255,15 +2268,15 @@ Firefox игнорирует заголовок `Permissions-Policy`. Подро
#### **`$redirect`** {#redirect-modifier}
-AdGuard способен перенаправлять веб-запросы на локальный «ресурс».
+AdGuard is able to redirect web requests to a local "resource".
-**Синтаксис**
+**Syntax**
-AdGuard использует тот же синтаксис правил фильтрации, что и uBlock Origin. Также он совместим с модификатором ABP `$rewrite=abp-resource`.
+AdGuard uses the same filtering rule syntax as uBlock Origin. Also, it is compatible with ABP `$rewrite=abp-resource` modifier.
-`$redirect` — это модификатор для [базовых правил фильтрации](#basic-rules), поэтому правила с этим модификатором поддерживают остальные базовые модификаторы, такие как `$domain`, `$third-party`, `$script` и т. д.
+`$redirect` is a modifier for the [basic filtering rules](#basic-rules) so rules with this modifier support all other basic modifiers like `$domain`, `$third-party`, `$script`, etc.
-Значение модификатора `$redirect` должно быть именем ресурса, который будет использован для переадресации.
+The value of the `$redirect` modifier must be the name of the resource that will be used for redirection.
##### Отключение правил `$redirect`
@@ -2272,23 +2285,23 @@ AdGuard использует тот же синтаксис правил фил
- `@@||example.org^$redirect` отключит все правила `$redirect` для URL-адресов, соответствующих `||example.org^`.
- `@@||example.org^$redirect=nooptext` отключит все правила с `$redirect=nooptext` для любого запроса, который соответствует `||example.org^`.
-Больше информации о редиректах и их использовании доступно [на GitHub](https://github.com/AdguardTeam/Scriptlets#redirect-resources).
+More information on redirects and their usage is available [on GitHub](https://github.com/AdguardTeam/Scriptlets#redirect-resources).
##### Приоритеты правил `$redirect` {#redirect-rule-priorities}
-У правил с `$redirect` более высокий приоритет, чем у обычных базовых правил блокировки. Это означает, что если существует базовое правило блокировки, то правило `$redirect` будет его отменять. У правил белого списка с пометкой `@@` более высокий приоритет, чем у правил `$redirect`. Если базовое правило с модификатором `$important` и правило `$redirect` соответствуют одному и тому же URL-адресу, последнее переопределяется, если оно также не помечено как `$important`.
+`$redirect` rules have higher priority than regular basic blocking rules. This means that if there is a basic blocking rule, the `$redirect` rule will override it. Allowlist rules with `@@` mark have higher priority than `$redirect` rules. If a basic rule with the `$important` modifier and the `$redirect` rule matches the same URL, the latter is overridden unless it's also marked as `$important`.
-**`$important` > `@@` > `$redirect` > `базовые правила`.**
+**In short: `$important` > `@@` > `$redirect` > `basic rules`.**
-Перейдите [к приоритетам правил](#rule-priorities) для более подробной информации.
+Go to [rules priorities](#rule-priorities) for more details.
##### Ограничения модификатора `$redirect` {#redirect-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-В [AdGuard для Chrome MV3][ext-mv3] правила белого списка с `$redirect` не поддерживаются.
+In [AdGuard for Chrome MV3][ext-mv3] allowlist rules with `$redirect` are not supported.
:::
@@ -2301,11 +2314,11 @@ AdGuard использует тот же синтаксис правил фил
#### **`$redirect-rule`** {#redirect-rule-modifier}
-По сути это другое имя [`$redirect`](#redirect-modifier), поскольку он имеет те же значения «перенаправления» и почти аналогичную логику. Разница в том, что `$redirect-rule` применяется только в том случае, если целевой запрос заблокирован другим базовым правилом.
+This is basically an alias to [`$redirect`](#redirect-modifier) since it has the same "redirection" values and the logic is almost similar. The difference is that `$redirect-rule` is applied only in the case when the target request is blocked by a different basic rule.
-Перейдите [к приоритетам правил](#rule-priorities) для более подробной информации.
+Go to [rules priorities](#rule-priorities) for more details.
-Отключение `$redirect-rule` работает точно так же, как для обычных правил `$redirect`. Даже более того, `@@||example.org^$redirect` будет отключать как правило `$redirect`, так и `$redirect-rule`.
+Negating `$redirect-rule` works exactly the same way as for regular `$redirect` rules. Even more than that, `@@||example.org^$redirect` will negate both `$redirect` and `$redirect-rule` rules.
**Примеры**
@@ -2314,21 +2327,21 @@ AdGuard использует тот же синтаксис правил фил
||example.org^$redirect-rule=noopjs
```
-В этом случае только запросы к `example.org/script.js` будут перенаправлены на `noopjs`. Все остальные запросы к `example.org` останутся без изменений.
+In this case, only requests to `example.org/script.js` will be "redirected" to `noopjs`. All other requests to `example.org` will be kept intact.
:::info Совместимость
-Правила с модификатором `$redirect-rule` не поддерживаются в [AdGuard Content Blocker][and-cb], [AdGuard для iOS][ios-app], [AdGuard для Safari][ext-saf] и [AdGuard для Chrome MV3][ext-mv3]. [Обсуждение о том, чтобы добавить поддержку правил `$redirect-rule` в расширения Chrome MV3](https://github.com/w3c/webextensions/issues/493), сейчас открыто.
+Rules with `$redirect-rule` modifier are not supported by [AdGuard Content Blocker][and-cb], [AdGuard for iOS][ios-app], [AdGuard for Safari][ext-saf], and [AdGuard for Chrome MV3][ext-mv3]. [The discussion about adding support for `$redirect-rule` rules in Chrome MV3 extensions](https://github.com/w3c/webextensions/issues/493) is currently open.
:::
#### **`$referrerpolicy`** {#referrerpolicy-modifier}
-Эти правила позволяют переопределять [политику реферера страницы](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Referrer-Policy). В ответах на соответствующие запросы все заголовки `Referrer-Policy` заменит один заголовок со значением, равным значению модификатора правила сопоставления. Если ответ содержит HTML-документ с тегом `)[\s\S]*<\/VAST>/\$1<\/VAST>/i
```
-У этого правила три части:
+There are three parts in this rule:
- `regexp` (регулярное выражение) — `()(.|\s)*<\/VAST>`;
- `replacement` (замена) — `\$1<\/VAST>` где `$` экранируется;
- `modifiers` (флаги регулярных выражений) — `i` для поиска без учёта регистра.
-Здесь вы можете увидеть, как работает это правило: http://regexr.com/3cesk
+You can see how this rule works here: http://regexr.com/3cesk
-**Несколько правил с `$replace`**
+**Multiple `$replace` rules**
1. `||example.org^$replace=/X/Y/`
2. `||example.org^$replace=/Z/Y/`
@@ -2774,7 +2787,7 @@ replace = "/" regexp "/" replacement "/" modifiers
- Правила 1 и 2 будут применены ко всем запросам, отправленным к `example.org`.
- Правило 2 отключено для запросов, соответствующих `||example.org/page/`, **но правило 1 при этом всё равно работает!**
-**Отключение правил с `$replace`**
+**Disabling `$replace` rules**
- `@@||example.org^$replace` отключит все правила `$replace`, соответствующие `||example.org^`.
- `@@||example.org^$document` или `@@||example.org^$content` отключит все правила `$replace`, **исходящие** со страниц домена `example.org`, **включая саму эту страницу**.
@@ -2788,29 +2801,29 @@ replace = "/" regexp "/" replacement "/" modifiers
:::info Совместимость
-Правила с модификатором `$replace` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android, а также в Браузерном расширении AdGuard для Firefox. Другие расширения не могут модифицировать содержимое страниц на сетевом уровне, поэтому там эти правила не работают.
+Rules with `$replace` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard Browser Extension for Firefox. Such rules do not work in extensions for other browsers because they are unable to modify content on the network level.
:::
#### **`$urltransform`** {#urltransform-modifier}
-Правила `$urltransform` позволяют изменять URL-адрес запроса, заменяя текст, соответствующий регулярным выражениям.
+The `$urltransform` rules allow you to modify the request URL by replacing text matched by a regular expression.
-**Функции**
+**Features**
- Правила `$urltransform` обычно применяются только к частям URL-адреса, относящимся к пути и запросу, одно исключение см. ниже.
- `$urltransform` не будет применяться, если исходный URL-адрес заблокирован другими правилами.
- `$urltransform` будет применяться перед правилами `$removeparam`.
-Значение `$urltransform` может быть пустым для правил исключений.
+The `$urltransform` value can be empty for exception rules.
-**Несколько правил, соответствующих одному запросу**
+**Multiple rules matching a single request**
-Если несколько правил `$urltransform` соответствуют одному запросу, мы применим каждое из них. **Правила будут применяться в алфавитном порядке.**
+If multiple `$urltransform` rules match a single request, we will apply each of them. **The order is defined alphabetically.**
-**Синтаксис**
+**Syntax**
-Синтаксис `$urltransform` аналогичен замене регулярными выражениями [в Perl](http://perldoc.perl.org/perlrequick.html#Search-and-replace).
+`$urltransform` syntax is similar to replacement with regular expressions [in Perl](http://perldoc.perl.org/perlrequick.html#Search-and-replace).
```text
urltransform = "/" regexp "/" replacement "/" modifiers
@@ -2820,17 +2833,17 @@ urltransform = "/" regexp "/" replacement "/" modifiers
- **`replacement`** — строка, которая будет использована для замены строки в соответствии с `regexp`.
- **`modifiers `** — флаги регулярных выражений. Например, `i` — поиск без учёта регистра, `s` — режим одной строки.
-В значении `$urltransform` необходимо экранировать два символа: запятую `,` и знак доллара `$`. Для этого используйте обратный слеш `\`. Например, экранированная запятая будет выглядеть так: `\,`.
+In the `$urltransform` value, two characters must be escaped: the comma `,` and the dollar sign `$`. Use the backslash character `\` for this. For example, an escaped comma looks like this: `\,`.
-**Изменение происхождения**
+**Changing the origin**
:::info Совместимость
-Этот раздел относится только к AdGuard для Windows, AdGuard для Mac и AdGuard для Android с [CoreLibs][] 1.17 или более поздней версии.
+This section only applies to AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.17 or later.
:::
-Как указано выше, обычно правилам `$urltransform` разрешено изменять только части пути и запроса URL-адреса. Однако, если `regexp` правила начинается со строки `^http`, то полный URL ищется и может быть изменён правилом. Такое правило не будет применяться, если преобразование URL не может быть выполнено с помощью HTTP-перенаправления (например, если метод запроса — `POST`).
+As stated above, normally `$urltransform` rules are only allowed to change the path and query parts of the URL. However, if the rule's `regexp` begins with the string `^http`, then the full URL is searched and can be modified by the rule. Such a rule will not be applied if the URL transformation can not be achieved via an HTTP redirect (for example, if the request's method is `POST`).
**Примеры**
@@ -2838,13 +2851,13 @@ urltransform = "/" regexp "/" replacement "/" modifiers
||example.org^$urltransform=/(pref\/).*\/(suf)/\$1\$2/i
```
-У этого правила три части:
+There are three parts in this rule:
- `regexp` — `(pref\/).*\/(suf)`;
- `replacement` — `\$1\$2`, где `$` экранируется;
- `modifiers` (флаги регулярных выражений) — `i` для поиска без учёта регистра.
-**Несколько правил с `$urltransform`**
+**Multiple `$urltransform` rules**
1. `||example.org^$urltransform=/X/Y/`
2. `||example.org^$urltransform=/Z/Y/`
@@ -2853,63 +2866,63 @@ urltransform = "/" regexp "/" replacement "/" modifiers
- Правила 1 и 2 будут применены ко всем запросам, отправленным к `example.org`.
- Правило 2 отключено для запросов, соответствующих `||example.org/page/`, **но правило 1 при этом всё равно работает!**
-**Повторное сопоставление правил после преобразования URL**
+**Re-matching rules after transforming the URL**
-После применения всех соответствующих правил `$urltransform` преобразованный запрос будет сопоставлен со всеми остальными правилами:
+After applying all matching `$urltransform` rules, the transformed request will be matched against all other rules:
-Например, при следующих правилах:
+E.g., with the following rules:
```adblock
||example.com^$urltransform=/firstpath/secondpath/
||example.com/secondpath^
```
-запрос к `https://example.com/firstpath` будет заблокирован.
+the request to `https://example.com/firstpath` will be blocked.
-**Отключение правил с `$urltransform`**
+**Disabling `$urltransform` rules**
- `@@||example.org^$urltransform` отключит все правила с `$urltransform`, где есть `||example.org^`.
- `@@||example.org^$urltransform=/Z/Y/` отключит правило с `$urltransform=/Z/Y/` для любого запроса, соответствующего `||example.org^`.
-Правила с `$urltransform` также можно отключить, используя правила исключений с `$document` и `$urlblock`. Но базовые правила исключений без модификаторов не могут этого сделать. Например, `@@||example.com^` не отключит `$urltransform=/X/Y/` для запросов к **example.com**, а `@@||example.com^$urlblock` отключит.
+`$urltransform` rules can also be disabled by `$document` and `$urlblock` exception rules. But basic exception rules without modifiers do not do that. For example, `@@||example.com^` will not disable `$urltransform=/X/Y/` for requests to **example.com**, but `@@||example.com^$urlblock` will.
-**Пример правила для очистки партнерских ссылок**
+**The rule example for cleaning affiliate links**
-Многие сайты используют отслеживающие URL-адреса для мониторинга кликов перед перенаправлением на непосредственно запрашиваемый адрес. Эти URL содержат маркетинговые параметры и аналитические токены, которые можно удалить, чтобы повысить конфиденциальность.
+Many websites use tracking URLs to monitor clicks before redirecting to the actual destination. These URLs contain marketing parameters and analytics tokens that can be removed to improve privacy.
-Ниже показано, как получить чистую целевую ссылку, чтобы обойти отслеживающие сайты и сразу перейти на нужную страницу.
+Below is an example of how to obtain the clean destination link to bypass tracking websites and go directly to the destination.
-В нашем примере:
+In our example:
- 1. Исходный URL (с отслеживанием кликов): `https://www.aff.example.com/visit?url=https%3A%2F%2Fwww.somestore.com%2F%26referrer%3Dhttps%3A%2F%2Fwww.aff.example.com%2F%26ref%3Dref-123`
- 1. Отслеживающий URL после расшифровки специальных символов: `https://www.aff.example.com/visit?url=https://www.somestore.com/`
- 1. Сайт, который вы хотите посетить: `https://www.somestore.com`
+ 1. The initial URL (with click tracking): `https://www.aff.example.com/visit?url=https%3A%2F%2Fwww.somestore.com%2F%26referrer%3Dhttps%3A%2F%2Fwww.aff.example.com%2F%26ref%3Dref-123`
+ 1. Tracking URL after decoding special characters: `https://www.aff.example.com/visit?url=https://www.somestore.com/`
+ 1. The website you want to visit: `https://www.somestore.com`
-Для очистки URL сначала нужно декодировать специальные символы (например, `%3A` → `:`, `%2F` → `/` и т. д.) и извлечь настоящий URL из отслеживающих параметров. Для этого мы используем модификатор `$urltransform`. Следующие 4 правила заменяют символы, закодированные в URL, на их реальные значения:
+To clean the URL, we first need to decode special characters (like `%3A` → `:`, `%2F` → `/`, etc.) and extract the real URL from the tracking parameters. We will use the `$urltransform` modifier to do this. The following 4 rules replace URL-encoded symbols with their real characters:
`/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%3A/:/` `/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%2F/\//` `/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%3F/?/` `/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%3D/=/` `/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/%26/&/`
-После этого нужно написать правило, которое заблокирует трекинговый сайт и перенаправит вас непосредственно на целевой адрес (somestore.com):
+After that, we need to write the rule that will block the tracking website and redirect you directly to the target address (somestore.com):
`/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com\/visit\?url=/$urltransform=/^https?:\/\/(?:[a-z0-9-]+\.)*?aff\.example\.com.*url=([^&]*).*/\$1/`
-Теперь отслеживающие ссылки будут автоматически очищаться, что позволит переходить на целевой сайт сразу без отслеживания.
+Tracking links will now be automatically cleaned up, allowing direct navigation to the destination website without tracking.
:::caution Ограничения
-Правила с модификатором `$urltransform` могут использоваться [**только в доверенных фильтрах**](#trusted-filters).
+Rules with the `$urltransform` modifier can only be used [**in trusted filters**](#trusted-filters).
:::
:::info Совместимость
-Правила с модификатором `$urltransform` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.15 или выше.
+Rules with the `$urltransform` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.15 or later.
:::
#### **`noop`** {#noop-modifier}
-Модификатор `noop` не делает ничего и используется только для того, чтобы улучшить читаемость правил. Он состоит из последовательности символов нижнего подчёркивания (`_`) произвольной длины и может фигурировать в правиле так часто, как это необходимо.
+`noop` modifier does nothing and can be used solely to increase rules' readability. It consists of a sequence of underscore characters (`_`) of arbitrary length and can appear in a rule as often as needed.
**Примеры**
@@ -2920,19 +2933,19 @@ urltransform = "/" regexp "/" replacement "/" modifiers
:::info Совместимость
-Правила с модификатором `noop` не поддерживаются в AdGuard Content Blocker.
+Rules with `noop` modifier are not supported by AdGuard Content Blocker.
:::
#### **`$empty` (устаревший)** {#empty-modifier}
-:::caution Скоро устареет
+:::caution Deprecation notice
-Этот модификатор считается устаревшим. Вместо него теперь используется [модификатор `$redirect`](#redirect-modifier). Правила с `$empty` всё ещё поддерживаются и преобразуются в `$redirect=nooptext`, но в будущем перестанут поддерживаться.
+This modifier is deprecated in favor of the [`$redirect` modifier](#redirect-modifier). Rules with `$empty` are still supported and being converted into `$redirect=nooptext` now but the support shall be removed in the future.
:::
-Обычно заблокированный запрос выглядит для браузера как ошибка сервера. В случае применения модификатора `$empty` AdGuard эмулирует пустой ответ сервера со статусом `200 OK`.
+Usually, blocked requests look like a server error to browser. If you use `$empty` modifier, AdGuard will emulate a blank response from the server with`200 OK` status.
**Примеры**
@@ -2940,19 +2953,19 @@ urltransform = "/" regexp "/" replacement "/" modifiers
:::info Совместимость
-Правила с модификатором `$empty` не поддерживаются в AdGuard Content Blocker, AdGuard для iOS и AdGuard для Safari.
+Rules with `$empty` modifier are not supported by AdGuard Content Blocker, AdGuard for iOS, and AdGuard for Safari.
:::
#### **`$mp4` (устаревший)** {#mp4-modifier}
-:::caution Скоро устареет
+:::caution Deprecation notice
-Этот модификатор считается устаревшим. Вместо него теперь используется [модификатор `$redirect`](#redirect-modifier). Правила с `$mp4` всё ещё поддерживаются и преобразуются в `$redirect=noopmp4-1s,media`, но в будущем перестанут поддерживаться.
+This modifier is deprecated in favor of the [`$redirect` modifier](#redirect-modifier). Rules with `$mp4` are still supported and being converted into `$redirect=noopmp4-1s,media` now but the support shall be removed in the future.
:::
-В качестве ответа на заблокированный запрос AdGuard возвращает короткую видео-заглушку.
+As a response to blocked request AdGuard returns a short video placeholder.
**Примеры**
@@ -2960,33 +2973,33 @@ urltransform = "/" regexp "/" replacement "/" modifiers
:::info Совместимость
-Правила с модификатором `$mp4` не поддерживаются в AdGuard Content Blocker, AdGuard для iOS и AdGuard для Safari.
+Rules with `$mp4` modifier are not supported by AdGuard Content Blocker, AdGuard for iOS, and AdGuard for Safari.
:::
### Приоритеты правил {#rule-priorities}
-Каждое правило имеет свой приоритет, что необходимо, когда запросу соответствует несколько правил и фильтрующий механизм должен выбрать одно из них. Приоритет измеряется целым положительным числом.
+Each rule has its own priority, which is necessary when several rules match the request and the filtering engine needs to select one of them. Priority is measured by a positive integer.
-:::note Конфликты
+:::note Collisions
-Когда два правила с одинаковым приоритетом соответствуют одному и тому же запросу, реализация механизма фильтрации определяет, какое из них будет выбрано.
+When two rules with the same priority match the same request, the filter engine implementation determines which one is chosen.
:::
:::info
-Концепция приоритетов правил становится всё более важной в свете Manifest V3, поскольку существующие правила должны быть преобразованы в правила declarativeNetRequest.
+The concept of rule priorities becomes increasingly important in light of Manifest V3, as the existing rules need to be converted to declarativeNetRequest rules.
:::
#### Расчёт приоритетов
-Для расчёта приоритета мы разделили модификаторы на разные группы. Эти группы ранжируются по степени приоритетности, от низшей к высшей. Модификатор, существенно сужающий область действия правила, увеличивает вес его общего приоритета. И наоборот, если правило применяется к более широкому кругу запросов, то его приоритет снижается.
+To calculate priority, we've categorized modifiers into different groups. These groups are ranked based on their priority, from lowest to highest. A modifier that significantly narrows the scope of a rule adds more weight to its total priority. Conversely, if a rule applies to a broader range of requests, its priority decreases.
-Следует отметить, что существуют случаи, когда модификатор с одним параметром имеет более высокий приоритет, чем тот, у которого много параметров. Например, в случае `$domain=example.com|example.org` правило, включающее два домена, имеет несколько более широкую область действия, чем правило с одним указанным доменом, поэтому его приоритет ниже.
+It's worth noting that there are cases where a single-parameter modifier has a higher priority than multi-parameter ones. For instance, in the case of `$domain=example.com|example.org`, a rule that includes two domains has a slightly broader effective area than a rule with one specified domain, therefore its priority is lower.
-Базовый приоритет любого правила равен 1. Если вычисленный приоритет — число с плавающей точкой, то оно будет **округлено в большую сторону** до наименьшего целого числа, большего или равного вычисленному приоритету.
+The base priority of any rule is 1. If the calculated priority is a floating-point number, it will be **rounded up** to the smallest integer greater than or equal to the calculated priority.
:::info Совместимость
@@ -2997,7 +3010,7 @@ urltransform = "/" regexp "/" replacement "/" modifiers
:::note
-Псевдонимы-модификаторы (`1p`, `3p` и т. д.) не входят в эти категории, однако они используются в движке для вычисления приоритета правила.
+Modifier aliases (`1p`, `3p`, etc.) are not included in these categories, however, they are utilized within the engine to compute the rule priority.
:::
@@ -3016,11 +3029,11 @@ urltransform = "/" regexp "/" replacement "/" modifiers
- [`$to`](#to-modifier),
- ограниченные модификаторы [сontent-type](#content-type-modifiers) с `~`.
-При работе с исключаемым доменом, приложением, методом или типом содержимого мы добавляем **1 балл** за существование самого модификатора, независимо от количества исключаемых доменов или типов содержимого. Это связано с тем, что область действия правила и так бесконечно широка. Проще говоря, запрещая несколько доменов, модификаторов content-type, методов или приложений, мы лишь немного сужаем область действия правила.
+When dealing with a negated domain, app, method, or content-type, we add **1 point** for the existence of the modifier itself, regardless of the quantity of negated domains or content-types. This is because the rule's scope is already infinitely broad. Put simply, by prohibiting multiple domains, content-types, methods or apps, the scope of the rule becomes only minimally smaller.
#### Определённые модификаторы content-type, методы, заголовки, $all, $popup, специальные исключения {#priority-category-2}
-Все правильные типы контента:
+All valid content types:
@@ -3037,15 +3050,15 @@ urltransform = "/" regexp "/" replacement "/" modifiers
- [`$websocket`](#websocket-modifier),
- [`$xmlhttprequest`](#xmlhttprequest-modifier);
-Сюда также входят правила, которые неявно добавляют все типы контента:
+This also includes rules that implicitly add all content types:
- [`$all`](#all-modifier);
-Или правила, которые неявно добавляют модификатор `$document`:
+Or rules that implicitly add the modifier `$document`:
- [`$popup`](#popup-modifier);
-Или некоторые специальные исключения, которые неявно добавляют `$document,subdocument`:
+Or some specific exceptions that implicitly add `$document,subdocument`:
@@ -3058,25 +3071,25 @@ urltransform = "/" regexp "/" replacement "/" modifiers
- [`$specifichide`](#specifichide-modifier),
- [`$urlblock`](#urlblock-modifier);
-Или методы, разрешённые модификатором [`$method`](#method-modifier).
+Or allowed methods via [`$method`](#method-modifier).
-Или правила с [`$header`](#header-modifier).
+Or rules with [`$header`](#header-modifier).
-Наличие любых модификаторов content-type добавляет `(50 + 50 / N)`, где `N` — количество модификаторов, например: `||example.com^$image,script` добавит `50 + 50 / 2 = 50 + 25 = 75` к общему весу правила.
+The presence of any content-type modifiers adds `(50 + 50 / N)`, where `N` is the number of modifiers present, for example: `||example.com^$image,script` will add `50 + 50 / 2 = 50 + 25 = 75` to the total weight of the rule.
-`$all` также относится к этой категории, поскольку он неявно добавляет все модификаторы content-type, например, `$document,subdocument,image,script,media,` + `$popup`.
+The `$all` also belongs to this category, because it implicitly adds all content-type modifiers, e.g., `$document,subdocument,image,script,media,` + `$popup`.
-К этой категории относится и `$popup`, поскольку неявно добавляет модификатор `$document`. Аналогично, конкретные исключения добавляют `$document,subdocument`.
+The `$popup` also belongs to this category, because it implicitly adds the modifier `$document`. Similarly, specific exceptions add `$document,subdocument`.
-Если в правиле есть модификатор `$method` с разрешёнными методами, то он добавляет `(50 + 50 / N)`, где `N` — количество разрешённых методов, например: `||example.com^$method=GET|POST|PUT` добавит `50 + 50 / 3 = 50 + 16,6 = 67` к общему весу правила.
+If there is a `$method` modifier in the rule with allowed methods it adds `(50 + 50 / N)`, where `N` is the number of methods allowed, for example: `||example.com^$method=GET|POST|PUT` will add `50 + 50 / 3 = 50 + 16.6 = 67` to the total weight of the rule.
-Если в правиле есть модификатор `$header`, то он добавляет `50`.
+If there is a `$header` modifier in the rule, it adds `50`.
#### `$domain` или `$app` с разрешёнными доменами или приложениями {#priority-category-3}
-Домены или приложения, указанные с помощью `$domain` и `$app` соответственно, добавят `100 + 100 / N`, где `N` — количество значений модификатора, например: `||example.com^$domain=example.com|example.org|example.net` добавит `100 + 100 / 3 = 135` или `||example.com^$app=org.example.app1|org.example.app2` добавит `100 + 100 / 2 = 100 + 51 = 151` или `||example.com^$domain=example.com,app=org.example.app1|org.example.app2` добавит `100 + 100/1` (часть $domain) и `100 + 100/2` (часть $app) — в сумме `350`.
+Specified domains through `$domain` or specified applications through `$app` add `100 + 100 / N`, where `N` is the number of modifier values for example: `||example.com^$domain=example.com|example.org|example.net` will add `100 + 100 / 3 = 134.3 = 135` or `||example.com^$app=org.example.app1|org.example.app2` will add `100 + 100 / 2 = 151` or `||example.com^$domain=example.com,app=org.example.app1|org.example.app2` will add `100 + 100/1` ($domain part) and `100 + 100/2` ($app part), totaling `350`.
-Значения модификаторов regexps или tld будут интерпретироваться как обычные записи вида `example.com` и считаться по одному, например: `||example.com^$domain=example.*` будет добавлено `100 + 100 / 1 = 200` или `||example.com^$domain=example.*|adguard.*` будет добавлено `100 + 100 / 2 = 150`.
+Modifier values that are regexps or tld will be interpreted as normal entries of the form `example.com` and counted one by one, for example: `||example.com^$domain=example.*` will add `100 + 100 / 1 = 200` or `||example.com^$domain=example.*|adguard.*` will add `100 + 100 / 2 = 150`.
#### Правила `$redirect` {#priority-category-6}
@@ -3085,7 +3098,7 @@ urltransform = "/" regexp "/" replacement "/" modifiers
- [`$redirect`](#redirect-modifier),
- [`$redirect-rule`](#redirect-rule-modifier).
-Каждое из них добавляет `10^3` к приоритету правила.
+Each of which adds `10^3` to rule priority.
#### Особые исключения {#priority-category-4}
@@ -3100,27 +3113,27 @@ urltransform = "/" regexp "/" replacement "/" modifiers
- [`$specifichide`](#specifichide-modifier),
- [`$urlblock`](#urlblock-modifier);
-Каждое из них добавляет `10^4` к приоритету.
+Each of which adds `10^4` to the priority.
-Исключение с модификатором [`$document`](#document-modifier) в том числе: это псевдоним для `$elemhide, content,jsinject,urlblock,extension`. Оно добавит `10^4` для каждого модификатора из [верхнего списка](#priority-category-4), `10^4 * 5` в сумме.
+As well as exception with [`$document modifier`](#document-modifier): because it's an alias for `$elemhide,content,jsinject,urlblock,extension`. It will add `10^4` for each modifier from [the top list](#priority-category-4), `10^4 * 5` in total.
-Кроме того, каждое из этих исключений неявно добавляет два разрешённых модификатора типа контента: `$document,subdocument`.
+In addition, each of these exceptions implicitly adds the two allowed content-type modifiers `$document,subdocument`.
#### Правила белого списка {#priority-category-5}
-Модификатор `@@` добавляет `10^5` к приоритету правила.
+Modifier `@@` adds `10^5` to rule priority.
#### Правила `$important` {#priority-category-7}
-Модификатор [`$important`](#important-modifier) добавляет `10^6` к приоритету правила.
+Modifier [`$important`](#important-modifier) adds `10^6` to rule priority.
#### Правила, для которых нет веса приоритета {#priority-category-extra}
-[Прочие модификаторы](#advanced-capabilities), которые должны выполнять дополнительную пост- или предобработку запросов, ничего не добавляют к приоритету правил.
+[Other modifiers](#advanced-capabilities), which are supposed to perform additional post- or pre-processing of requests, do not add anything to the rule priority.
:::note
-Модификатор [`$replace`](#replace-modifier) имеет приоритет над всеми блокирующими правилами категорий 1–3, а также над правилами исключений из категорий 3–5, **кроме** [`$content`](#content-modifier), поскольку исключение с модификатором `$content` отменяет все правила `$replace`.
+The [`$replace`](#replace-modifier) modifier takes precedence over all blocking rules of categories 1–3, as well as exception rules from categories 3–5, **except** [`$content`](#content-modifier), because an exception with the `$content` modifier overrides all `$replace` rules.
:::
@@ -3128,43 +3141,43 @@ urltransform = "/" regexp "/" replacement "/" modifiers
1. `||example.com^`
- Вес правила без модификаторов: `1`.
+ Weight of the rule without modifiers: `1`.
1. `||example.com^$match-case`
- Вес правила: базовый вес + вес модификатора из [категории 1](#priority-category-1): `1 + 1 = 2`.
+ Rule weight: base weight + weight of the modifier from [category 1](#priority-category-1): `1 + 1 = 2`.
1. `||example.org^$removeparam=p`
- Вес правила: базовый вес + 0, так как $removeparam [не участвует](#priority-category-extra) в расчёте приоритета: `1 + 0 = 1`.
+ Rule weight: base weight + 0, since $removeparam [is not involved](#priority-category-extra) in the priority calculation: `1 + 0 = 1`.
1. `||example.org^$document,redirect=nooptext`
- Вес правила: базовый вес + допустимый тип содержимого, [категория 3](#priority-category-3) + $redirect из [категории 6](#priority-category-6): `1 + (100 + 100 / 1) + 1000 = 1201`.
+ Rule weight: base weight + allowed content type, [category 3](#priority-category-3) + $redirect from [category 6](#priority-category-6): `1 + (100 + 100 / 1) + 1000 = 1201`.
1. `@@||example.org^$removeparam=p,document`
- Вес правила: базовый вес + правило белого списка, [категория 5](#priority-category-5) + 0, потому что $removeparam [не участвует](#priority-category-extra) в расчёте приоритета + разрешённый тип контента, [категория 2](#priority-category-2): `1 + 10000 + 0 + (50 + 50 / 1) = 10101`.
+ Rule weight: base weight + allowlist rule, [category 5](#priority-category-5) + 0 because $removeparam [is not involved](#priority-category-extra) in the priority calculation + allowed content type, [category 2](#priority-category-2): `1 + 10000 + 0 + (50 + 50 / 1) = 10101`.
1. `@@||example.com/ad/*$domain=example.org|example.net,important`
- Вес правила: базовый вес + правило белого списка, [категория 5](#priority-category-5) + важное правило, [категория 7](#priority-category-7) + разрешённые домены, [категория 3](#priority-category-3): `1 + 10000 + 1000000 + (100 + 100 / 2) = 1010152`.
+ Rule weight: base weight + allowlist rule, [category 5](#priority-category-5) + important rule, [category 7](#priority-category-7) + allowed domains, [category 3](#priority-category-3): `1 + 10000 + 1000000 + (100 + 100 / 2) = 1010152`.
-1. `@@||example.org^$document` без дополнительных модификаторов — это псевдоним для `@@|||example.com^$elemhide,content,jsinject,urlblock,extension`
+1. `@@||example.org^$document` without additional modifiers is an alias for `@@||example.com^$elemhide,content,jsinject,urlblock,extension`
- Вес правила: базовый вес + специфические исключения, [категория 4](#priority-category-4) + два разрешённых типа контента (document и subdocument), [категория 2](#priority-category-2): `1 + 10000 * 4 + (50 + 50 / 2) = 40076`.
+ Rule weight: base weight + specific exceptions, [category 4](#priority-category-4) + two allowed content types (document and subdocument), [category 2](#priority-category-2): `1 + 10000 * 4 + (50 + 50 / 2) = 40076`.
1. `*$script,domain=a.com,denyallow=x.com|y.com`
- Вес правила: базовый вес + разрешённый тип контента, [категория 2](#priority-category-2) + разрешённый домен, [категория 3](#priority-category-3) + отказ, [категория 1](#priority-category-1): `1 + (50 + 50/1) + (100 + 100 / 1) + 1 = 303`.
+ Rule weight: base weight + allowed content type, [category 2](#priority-category-2) + allowed domain, [category 3](#priority-category-3) + denyallow, [category 1](#priority-category-1): `1 + (50 + 50/1) + (100 + 100 / 1) + 1 = 303`.
-1. `||example.com^$all` — псевдоним для `||example.com^$document,subdocument,image,script,media и т. д. + $popup`
+1. `||example.com^$all` — alias to `||example.com^$document,subdocument,image,script,media,etc. + $popup`
- Вес правила: базовый вес + всплывающее окно ([категория 1](#priority-category-1)) + разрешённые типы контента ([категория 2](#priority-category-2)): `1 + 1 + (50 + 50/12) = 55`.
+ Rule weight: base weight + popup ([category 1](#priority-category-1)) + allowed content types ([category 2](#priority-category-2)): `1 + 1 + (50 + 50/12) = 55`.
## Другие правила {#non-basic-rules}
-Базовых правил может быть недостаточно для блокировки рекламы. Иногда для этого требуется скрыть какой-нибудь элемент или изменить часть HTML-кода страницы, при этом ничего не сломав. Для этого предназначены правила, описанные в данном разделе.
+However, basic rules may not be enough to block ads. Sometimes you need to hide an element or change part of the HTML code of a web page without breaking anything. The rules described in this section are created specifically for this purpose.
| Категории \ Продукты | [Приложения CoreLibs][cl-apps] | [AdGuard для Chromium][ext-chr] | [AdGuard для Chrome MV3][ext-mv3] | [AdGuard для Firefox][ext-ff] | [AdGuard для iOS][ios-app] | [AdGuard для Safari][ext-saf] | [AdGuard Content Blocker][and-cb] |
| --------------------------------------------- |:------------------------------:|:-------------------------------:|:---------------------------------:|:-----------------------------:|:--------------------------:|:-----------------------------:|:---------------------------------:|
@@ -3186,17 +3199,17 @@ urltransform = "/" regexp "/" replacement "/" modifiers
:::info
-Для работы с косметическими правилами необходимы знания HTML и CSS. Если вы хотите научиться создавать такие правила, рекомендуем ознакомиться [с этой документацией](https://developer.mozilla.org/en-US/docs/Web/Guide/CSS/Getting_started/What_is_CSS).
+Work with non-basic rules requires the basic knowledge of HTML and CSS. So, if you want to learn how to make such rules, we recommend to get acquainted with [this documentation](https://developer.mozilla.org/en-US/docs/Web/Guide/CSS/Getting_started/What_is_CSS).
:::
### Правила скрытия элементов {#cosmetic-elemhide-rules}
-Правила скрытия элементов предназначены, как это следует из их названия, для скрытия элементов веб-страниц. По сути это аналогично применению стиля `{ display: none; }` к выбранному элементу.
+Element hiding rules are used to hide the elements of web pages. It is similar to applying `{ display: none; }` style to selected element.
-Правила скрытия элементов работают по-разному, и их приоритет меняется [в зависимости от платформы](#cosmetic-rules-priority).
+Element hiding rules may operate differently [depending on the platform](#cosmetic-rules-priority).
-#### Синтаксис
+#### Syntax
```text
rule = [domains] "##" selector
@@ -3206,17 +3219,17 @@ domains = [domain0, domain1[, ...[, domainN]]]
- **`selector`** — [CSS селектор](https://developer.mozilla.org/en-US/docs/Web/Guide/CSS/Getting_Started/Selectors), определяет элементы, которые нужно скрыть.
- **`domains`** — доменное ограничение для правила.
-Если вы хотите ограничить область действия одним или более доменами, просто перечислите их через запятую. Например: `example.org,example.com##selector`.
+If you want to limit the rule application area to certain domains, just enter them separated with commas. For example: `example.org,example.com##selector`.
-Это правило будет работать также на всех поддоменах `example.org` и `example.com`.
+This rule will be also applied to all subdomains of `example.org` and `example.com`.
-Если вы хотите, чтобы правило не применялось к определённым доменам, начните доменное имя со знака `~`. Например: `~example.org##selector`.
+Если вы хотите, чтобы правило не применялось к определённым доменам, начните доменное имя со знака `~`. For example: `~example.org##selector`.
-Вы можете использовать оба подхода в одном правиле. Например, правило `example.org,~subdomain.example.org##domain` будет работать для домена `example.org` и всех его поддоменов, **кроме `subdomain.example.org`**.
+You can use both approaches in a single rule. For example, `example.org,~subdomain.example.org##domain` will work for `example.org` and all subdomains, **except `subdomain.example.org`**.
:::note
-Правила скрытия не зависят друг от друга. Если в фильтре есть правило `example.org##selector` и вы добавляете правило `~example.org##selector`, то оба этих правила будут применены независимо друг от друга.
+Element hiding rules are not dependent on each other. If there is a rule `example.org##selector` in the filter and you add `~example.org##selector` both rules will be applied independently.
:::
@@ -3228,43 +3241,43 @@ domains = [domain0, domain1[, ...[, domainN]]]
**Ограничения**
-Safari не поддерживает одновременно разрешённые и запрещённые домены. Поэтому правила вида `example.org,~foo.example.org##.textad` не работают в AdGuard для Safari.
+Safari does not support both allowed and disallowed domains. So the rules like `example.org,~foo.example.org##.textad` are invalid in AdGuard for Safari.
**Исключения**
-Исключения могут отключать некоторые правила на определённых доменах. Они очень похожи на обычные правила-исключения, только вместо `##` нужно использовать `#@#`.
+Exceptions can disable some rules on particular domains. They are very similar to usual exception rules, but instead of `##` you have to use `#@#`.
-Например, в фильтре есть правило:
+For example, there is a rule in filter:
```adblock
##.textad
```
-Если вы хотите отключить его для домена `example.com`, вы можете создать правило исключения:
+If you want to disable it for `example.com`, you can create an exception rule:
```adblock
example.com#@#.textad
```
-В некоторых случаях может потребоваться отключение всех запрещающих правил. Например, на время тестирования. Для этого воспользуйтесь правилом исключения без указания домена. Это полностью отключит соответствующее правило CSS elemhide для ВСЕХ доменов:
+Sometimes, it may be necessary to disable all restriction rules. For example, to conduct tests. To do this, use the exclusion rule without specifying a domain. It will completely disable matching CSS elemhide rule on ALL domains:
```adblock
#@#.textad
```
-Правило такого вида даст аналогичный результат:
+The same can be achieved by adding this rule:
```adblock
*#@#.textad
```
-Применять такие исключения рекомендуется только в случае, когда изменить само правило скрытия невозможно. Во всех остальных случаях лучше изменить исходное правило, используя ограничение на домены.
+We recommend to use this kind of exceptions only if it is not possible to change the hiding rule itself. In other cases it is better to change the original rule, using domain restrictions.
### CSS-правила {#cosmetic-css-rules}
-Иногда недостаточно просто скрыть какой-либо элемент, чтобы заблокировать рекламу. Например, блокировка рекламного элемента может просто сломать вёрстку сайта. Для таких случаев AdGuard позволяет использовать гораздо более гибкие правила, чем обычные правила скрытия. С помощью таких правил вы можете добавить на страницу практически любой CSS-стиль.
+Sometimes, simple hiding of an element is not enough to deal with advertising. For example, blocking an advertising element can just break the page layout. In this case AdGuard can use rules that are much more flexible than hiding rules. With these rules you can basically add any CSS styles to the page.
-**Синтаксис**
+**Syntax**
```text
rule = [domains] "#$#" selector "{" style "}"
@@ -3281,37 +3294,37 @@ domains = [domain0, domain1[, ...[, domainN]]]
example.com#$#body { background-color: #333!important; }
```
-Это правило применит стиль `background-color: #333!important;` к элементу `body` для домена `example.com` и всех его поддоменов.
+This rule will apply a style `background-color: #333!important;` to the `body` element at `example.com` and all subdomains.
**Исключения**
-По аналогии с правилами скрытия существует специальный тип правил, отключающий действие выбранного правила CSS-стилей для определённых доменов. Синтаксис правил-исключений практически такой же, только маркер `#$#` заменяется на `#@$#`.
+Just like with element hiding, there is a type of rules that disable the selected CSS style rule for particular domains. Exception rule syntax is almost the same, you just have to change `#$#` to `#@$#`.
-Например, в фильтре есть правило:
+For example, there is a rule in filter:
```adblock
#$#.textad { visibility: hidden; }
```
-Если вы хотите отключить его для домена `example.com`, вы можете создать правило исключения:
+If you want to disable it for `example.com`, you can create an exception rule:
```adblock
example.com#@$#.textad { visibility: hidden; }
```
-Применять такие исключения рекомендуется только в случае, когда невозможно изменить само CSS-правило. Во всех остальных случаях лучше изменить исходное правило, используя ограничение на домены.
+We recommend to use this kind of exceptions only if it is not possible to change the CSS rule itself. In other cases it is better to change the original rule, using domain restrictions.
:::caution Ограничения
-Запрещено использование стилей, которые могут приводить к загрузке каких-либо ресурсов. Это означает, что нельзя использовать атрибуты типа ``.
+Styles that lead to loading any resource are forbidden. Basically, it means that you cannot use any `` type of value in the style.
:::
:::info Совместимость
-CSS-правила не поддерживаются в AdGuard Content Blocker.
+CSS rules are not supported by AdGuard Content Blocker.
-CSS-правила работают по-разному, и их приоритет меняется [в зависимости от платформы](#cosmetic-rules-priority).
+CSS rules may operate differently [depending on the platform](#cosmetic-rules-priority).
:::
@@ -3331,30 +3344,30 @@ CSS-правила работают по-разному, и их приорит
- [Псевдокласс `:not()`](#extended-css-not)
- [Псевдокласс `:if-not()` (удалён)](#extended-css-if-not)
-Возможностей CSS 3.0 не всегда хватает для блокировки рекламы. Чтобы решить эту проблему, AdGuard расширяет возможности CSS, добавляя поддержку новых псевдоэлементов. Мы разработали отдельную [библиотеку с открытым исходным кодом](https://github.com/AdguardTeam/ExtendedCss) для выбора нестандартных элементов и применения CSS-стилей с расширенными свойствами.
+CSS 3.0 is not always enough to block ads. To solve this problem AdGuard extends CSS capabilities by adding support for the new pseudo-elements. We have developed a separate [open-source library](https://github.com/AdguardTeam/ExtendedCss) for non-standard element selecting and applying CSS styles with extended properties.
-Идея расширенных возможностей заключается в возможности сопоставлять элементы DOM с селекторами на основе их собственного представления (стиль, текстовое содержимое и т. д.) или отношений с другими элементами. Также есть возможность применять стили с нестандартными свойствами CSS.
+The idea of extended capabilities is an opportunity to match DOM elements with selectors based on their own representation (style, text content, etc.) or relations with other elements. There is also an opportunity to apply styles with non-standard CSS properties.
-**Область применения**
+**Application area**
-Расширенные селекторы можно применять в любом косметическом правиле, будь то [правила скрытия элементов](#cosmetic-elemhide-rules) или [CSS-правила](#cosmetic-css-rules).
+Extended selectors can be used in any cosmetic rule, whether they are [element hiding rules](#cosmetic-elemhide-rules) or [CSS rules](#cosmetic-css-rules).
:::info Совместимость
-Правила с расширенными CSS-селекторами не поддерживаются в AdGuard Content Blocker.
+Rules with extended CSS selectors are not supported by AdGuard Content Blocker.
:::
-**Синтаксис**
+**Syntax**
-Независимо от того, какие CSS-псевдоклассы вы используете в правиле, вы можете использовать специальные маркеры для принудительного применения этих правил с помощью ExtendedCss. Рекомендуется использовать эти маркеры для всех расширенных косметических CSS-правил, чтобы их было легче отличить.
+Regardless of the CSS pseudo-classes you are using in the rule, you can use special markers to force applying these rules by ExtendedCss. It is recommended to use these markers for all extended CSS cosmetic rules so that it was easier to find them.
-Синтаксис расширенных CSS-правил:
+The syntax for extended CSS rules:
- `#?#` — для скрытия элемента, `#@?#` — для исключений
- `#$?#` — для CSS-правил, `#@$?#` — для исключений
-Мы **настоятельно рекомендуем** использовать эти маркеры каждый раз, когда вы используете расширенный CSS-селектор.
+We **strongly recommend** using these markers any time when you use an extended CSS selector.
**Примеры**
@@ -3363,53 +3376,53 @@ CSS-правила работают по-разному, и их приорит
- `example.net#?#.banner:matches-css(width: 360px)` — это правило блокирует все элементы `.banner`, которые содержат стиль `width: 360px`. При этом правило будет работать только для домена `example.net` и всех его поддоменов.
- `example.net#@?#.banner:matches-css(width: 360px)` — это правило отключает действие предыдущего правила.
-Вы можете применять стандартные CSS-селекторы с помощью библиотеки ExtendedCss, используя маркер правила `#?#`. Например, `#?#div.banner`.
+You can apply standard CSS selectors using the ExtendedCss library by using the rule marker `#?#`, e.g. `#?#div.banner`.
-Подробнее [об отладке расширенных селекторов](#selectors-debugging-mode).
+Learn more about [how to debug extended selectors](#selectors-debugging-mode).
:::note
-Некоторые псевдоклассы не требуют селектора перед ними. Несмотря на это, добавление [универсального селектора](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*` облегчает чтение расширенного селектора, хотя и не влияет на поведение при подборе. Поэтому селектор `#block :has(> .inner)` работает точно так же, как `#block *:has(> .inner)`, но второй более понятен.
+Some pseudo-classes do not require selector before it. Still adding the [universal selector](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*` makes an extended selector easier to read, even though it has no effect on the matching behavior. So selector `#block :has(> .inner)` works exactly like `#block *:has(> .inner)`, but the second one is more obvious.
-Названия псевдоклассов не чувствительны к регистру, например, `:HAS()` работает как `:has()`. Несмотря на это, в основном используются названия в нижнем регистре.
+Pseudo-class names are case-insensitive, e.g. `:HAS()` works as `:has()`. Still the lower-case names are used commonly.
:::
#### Ограничения ExtendedCss {#extended-css-limitations}
-1. [Комментарии](https://developer.mozilla.org/en-US/docs/Web/CSS/Comments) CSS и [at-правила](https://developer.mozilla.org/en-US/docs/Web/CSS/At-rule) не поддерживаются.
+1. CSS [comments](https://developer.mozilla.org/en-US/docs/Web/CSS/Comments) and [at-rules](https://developer.mozilla.org/en-US/docs/Web/CSS/At-rule) are not supported.
-2. Специфичные псевдоклассы могут иметь свои ограничения: [`:has()`](#extended-css-has-limitations), [`:xpath()`](#extended-css-xpath-limitations), [`:nth-ancestor()`](#extended-css-nth-ancestor-limitations), [`:upward()`](#extended-css-upward-limitations), [`:is()`](#extended-css-is-limitations), [`:not()`](#extended-css-not-limitations), и [`:remove()`](#extended-css-remove-limitations).
+2. Specific pseudo-class may have its own limitations: [`:has()`](#extended-css-has-limitations), [`:xpath()`](#extended-css-xpath-limitations), [`:nth-ancestor()`](#extended-css-nth-ancestor-limitations), [`:upward()`](#extended-css-upward-limitations), [`:is()`](#extended-css-is-limitations), [`:not()`](#extended-css-not-limitations), and [`:remove()`](#extended-css-remove-limitations).
#### Псевдокласс `:has()` {#extended-css-has}
-Проект спецификации CSS 4.0 описывает [псевдокласс `:has()`](https://www.w3.org/TR/selectors-4/#relational). К сожалению, популярные браузеры [пока не поддерживают этот псевдокласс](https://caniuse.com/css-has).
+Draft CSS 4.0 specification describes the [`:has()` pseudo-class](https://www.w3.org/TR/selectors-4/#relational). Unfortunately, [it is not yet supported](https://caniuse.com/css-has) by all popular browsers.
:::note
-Правила с псевдоклассом `:has()` должны использовать [нативную реализацию `:has()`][native-has], если они содержат маркер правила `##` и если это возможно, то есть внутри нет других расширенных CSS-селекторов. Если продукт не поддерживает реализацию ExtendedCss, она будет использоваться даже для правил с маркером `##`.
+Rules with the `:has()` pseudo-class must use the [native implementation of `:has()`][native-has] if they use the `##` rule marker and if it is possible, i.e., there are no other extended CSS selectors inside. If it is not supported by the product, ExtendedCss implementation will be used even for rules with the `##` marker.
-Сейчас не все продукты AdGuard поддерживают нативную реализацию `:has()`:
+Currently, not all AdGuard products support the native implementation of `:has()` yet:
- AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux **поддерживают** её с [CoreLibs][] версии 1.12.
- AdGuard для iOS и AdGuard для Safari **поддерживают** её с [SafariConverterLib](#safari-converter-lib) версии 2.0.39 и [браузера Safari версии 16.4][safari-16.4].
- Браузерное расширение AdGuard **пока не поддерживает** её, но это [планируется][AdguardBrowserExtension#2587].
-Чтобы принудительно использовать реализацию ExtendedCss для `:has()`, используйте маркеры правила `#?#` или `#$?#` явно, например, `example.com#?#p:has(> a)` или `example.com#$?#div:has(> span) { display: none !important; }`.
+To force the ExtendedCss implementation of `:has()` to be used, use the `#?#` or `#$?#` rule markers explicitly, e.g., `example.com#?#p:has(> a)` or `example.com#$?#div:has(> span) { display: none !important; }`.
:::
-**Совместимость с другими псевдоклассами**
+**Compatibility with other pseudo-classes**
-Синонимы `:-abp-has()` поддерживаются ExtendedCss для лучшей совместимости.
+Synonyms `:-abp-has()` is supported by ExtendedCss for better compatibility.
-:::danger Уведомление об удалении
+:::danger Removal notice
-`:if()` больше не поддерживается как синоним для `:has()`.
+`:if()` is no longer supported as a synonym for `:has()`.
:::
-**Синтаксис**
+**Syntax**
```text
[target]:has(selector)
@@ -3418,24 +3431,24 @@ CSS-правила работают по-разному, и их приорит
- `target` — необязательный, стандартный или расширенный CSS-селектор, может быть пропущен для проверки *любых* элементов
- `subject` — обязателен. Стандартный или расширенный CSS-селектор
-Псевдокласс `:has()` выбирает `target`-элементы, которые подходят под `selector`. Также `селектор` может начинаться с комбинатора.
+The pseudo-class `:has()` selects the `target` elements that fit to the `selector`. Also the `selector` can start with a combinator.
-Список селекторов можно задать и в `selector`. В этом случае **все** селекторы в списке будут сопоставляться. В будущем это будет исправлено для [``](https://www.w3.org/TR/selectors-4/#typedef-forgiving-relative-selector-list) в качестве аргумента.
+A selector list can be set in `selector` as well. In this case **all** selectors in the list are being matched for now. In the future it will be fixed for [``](https://www.w3.org/TR/selectors-4/#typedef-forgiving-relative-selector-list) as argument.
##### Ограничения `:has()` {#extended-css-has-limitations}
-Использование псевдокласса `:has()` [ограничено для некоторых случаев (2, 3)](https://bugs.chromium.org/p/chromium/issues/detail?id=669058#c54):
+Usage of the `:has()` pseudo-class is [restricted for some cases (2, 3)](https://bugs.chromium.org/p/chromium/issues/detail?id=669058#c54):
- запретить `:has()` внутри псевдоселекторов, принимающих только составные селекторы;
- запретить `:has()` после обычных псевдоэлементов.
-Родной псевдокласс `:has()` не позволяет использовать `:has()`, `:is()` и `:where()` внутри `:has()`-аргумента, чтобы избежать увеличения сложности недействительности аргумента `:has()` ([случай 1](https://bugs.chromium.org/p/chromium/issues/detail?id=669058#c54)). Но ранее ExtendedCss не имел такого ограничения, а списки фильтров уже содержат такие правила, поэтому мы не стали добавлять это ограничение в ExtendedCss и разрешили использовать `:has()` внутри `:has()`, как это было возможно ранее. Чтобы использовать его, просто принудительно используйте ExtendedCss, установив маркер `#?#`/`#$?#`.
+Native `:has()` pseudo-class does not allow `:has()`, `:is()`, `:where()` inside `:has()` argument to avoid increasing the `:has()` invalidation complexity ([case 1](https://bugs.chromium.org/p/chromium/issues/detail?id=669058#c54)). But ExtendedCss did not have such limitation earlier and filter lists already contain such rules, so we have not added this limitation to ExtendedCss and allow to use `:has()` inside `:has()` as it was possible before. To use it, just force ExtendedCss usage by setting `#?#`/`#$?#` rule marker.
-Нативная реализация не позволяет использовать `:scope` внутри аргумента `:has()` ([[1]](https://github.com/w3c/csswg-drafts/issues/7211), [[2]](https://github.com/w3c/csswg-drafts/issues/6399)). Тем не менее, в списках фильтров есть правила `div:has(:scope a)`, которые мы продолжаем поддерживать, просто преобразуя их в `div:has(> a)`, как это делалось ранее.
+Native implementation does not allow any usage of `:scope` inside the `:has()` argument ([[1]](https://github.com/w3c/csswg-drafts/issues/7211), [[2]](https://github.com/w3c/csswg-drafts/issues/6399)). Still, there are some such rules in filter lists: `div:has(:scope a)` which we continue to support by simply converting them to `div:has(> a)`, as it used to be done previously.
**Примеры**
-`div:has(.banner)` выбирает все `div`-элементы, которые **включают** элемент с классом `banner`:
+`div:has(.banner)` selects all `div` elements which **include** an element with the `banner` class:
```html
@@ -3445,7 +3458,7 @@ CSS-правила работают по-разному, и их приорит
```
-`div:has(> .banner)` выбирает все `div`-элементы, которые **включают** элемент класса `banner` в качестве *прямого дочернего* элемента `div`:
+`div:has(> .banner)` selects all `div` elements which **include** an `banner` class element as a *direct child* of `div`:
```html
@@ -3455,7 +3468,7 @@ CSS-правила работают по-разному, и их приорит
```
-`div:has(+ .banner)` выбирает все `div`-элементы, **предшествующие** элементу класса `banner`, который *непосредственно следует* за `div`, и оба являются детьми одного родителя:
+`div:has(+ .banner)` selects all `div` elements **preceding** `banner` class element which *immediately follows* the `div` and both are children of the same parent:
```html
@@ -3465,7 +3478,7 @@ CSS-правила работают по-разному, и их приорит
Not selected
```
-`div:has(~ .banner)` выбирает все `div`-элементы, **предшествующие** элементу класса `banner`, который *следует* за `div`, но *не обязательно сразу*, и оба являются детьми одного родителя:
+`div:has(~ .banner)` selects all `div` elements **preceding** `banner` class element which *follows* the `div` but *not necessarily immediately* and both are children of the same parent:
```html
@@ -3475,7 +3488,7 @@ CSS-правила работают по-разному, и их приорит
general sibling
```
-`div:has(span, .banner)` выбирает все элементы `div`, которые **включают в себя** как элемент `span`, так и элемент класса `banner`:
+`div:has(span, .banner)` selects all `div` elements which **include both** `span` element and `banner` class element:
```html
@@ -3486,27 +3499,27 @@ CSS-правила работают по-разному, и их приорит
```
-:::danger Старый синтаксис
+:::danger Old syntax
-[Синтаксис обратной совместимости для `:has()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-has) поддерживается, но **не рекомендуется**.
+[Backward compatible syntax for `:has()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-has) is supported but **not recommended**.
:::
#### Псевдокласс `:contains()` {#extended-css-contains}
-Принцип действия псевдокласса `:contains()` очень прост: он позволяет выбрать элементы, которые содержат заданный текст или содержимое которых соответствует указанному регулярному выражению. Поддерживаются флаги регулярных выражений.
+The `:contains()` pseudo-class principle is very simple: it allows to select the elements that contain specified text or which content matches a specified regular expression. Regexp flags are supported.
:::note
-Псевдокласс `:contains()` использует для сопоставления свойство элемента `textContent`, а не `innerHTML`.
+The `:contains()` pseudo-class uses the `textContent` element property for matching, not the `innerHTML`.
:::
-**Совместимость с другими псевдоклассами**
+**Compatibility with other pseudo-classes**
-Синонимы `:-abp-contains()` и `:has-text()` поддерживаются для лучшей совместимости.
+Synonyms `:-abp-contains()` and `:has-text()` are supported for better compatibility.
-**Синтаксис**
+**Syntax**
```text
[target]:contains(match)
@@ -3517,7 +3530,7 @@ CSS-правила работают по-разному, и их приорит
**Примеры**
-Для таких DOM:
+For such DOM:
```html
@@ -3526,36 +3539,36 @@ CSS-правила работают по-разному, и их приорит
```
-элемент `div#match` может быть выбран любым из этих расширенных селекторов:
+the element `div#match` can be selected by any of these extended selectors:
```adblock
! plain text
div:contains(banner)
-! регулярное выражение
+! regular expression
div:contains(/as .*banner/)
-! регулярное выражение с флагами
+! regular expression with flags
div:contains(/it .*banner/gi)
```
:::note
-Выбран только `div` с `id=match`, так как следующий элемент не содержит текст, а `banner` — это часть кода, а не текст.
+Only the `div` with `id=match` is selected because the next element does not contain any text, and `banner` is a part of code, not a text.
:::
-:::danger Старый синтаксис
+:::danger Old syntax
-[Синтаксис обратной совместимости для `:contains()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-contains) поддерживается, но **не рекомендуется**.
+[Backward compatible syntax for `:contains()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-contains) is supported but **not recommended**.
:::
#### Псевдокласс `:matches-css()` {#extended-css-matches-css}
-Псевдокласс `:matches-css()` позволяет сопоставить элемент по свойствам его текущего стиля. Работа псевдокласса основана на использовании метода [`Window.getComputedStyle()`](https://developer.mozilla.org/en-US/docs/Web/API/Window/getComputedStyle).
+The `:matches-css()` pseudo-class allows to match the element by its current style properties. The work of the pseudo-class is based on using the [`Window.getComputedStyle()`](https://developer.mozilla.org/en-US/docs/Web/API/Window/getComputedStyle) method.
-**Синтаксис**
+**Syntax**
```text
[target]:matches-css([pseudo-element, ] property: pattern)
@@ -3566,15 +3579,15 @@ div:contains(/it .*banner/gi)
- `property` — требуется, название CSS-свойства, которое будет проверено у элемента
- `pattern` — требуется, шаблон значений, который использует то же простое сопоставление с подстановочными знаками, что и в основных правилах фильтрации URL-адресов, или регулярное выражение. При таком типе сопоставления AdGuard не учитывает регистр. В случае с регулярными выражениями шаблон будет выглядеть так: `/regexp/`.
-**Экранирование и снятие специальных символов**
+**Special characters escaping and unescaping**
-Для **нерегулярных выражений** паттерны `(`,`)`,`[`,`]` должны быть **без экранирования**, например, `:matches-css(background-image:url(data:*))`.
+For **non-regexp** patterns `(`,`)`,`[`,`]` must be **unescaped**, e.g. `:matches-css(background-image:url(data:*))`.
-Для **регулярных выражений** паттерны `\` должны быть **экранированы**, например, `:matches-css(background-image: /^url\\("data:image\\/gif;base64.+/)`.
+For **regexp** patterns `\` should be **escaped**, e.g. `:matches-css(background-image: /^url\\("data:image\\/gif;base64.+/)`.
**Примеры**
-Для таких DOM:
+For such DOM:
```html
@@ -3587,42 +3600,42 @@ div:contains(/it .*banner/gi)
```
-`div`-элементы с псевдоэлементом `::before` и с указанным свойством `content` могут быть выбраны любым из этих расширенных селекторов:
+the `div` elements with pseudo-element `::before` and with specified `content` property can be selected by any of these extended selectors:
```adblock
-! паттерн строки
+! string pattern
div:matches-css(before, content: block me)
-! паттерн строки с подстановочным знаком
+! string pattern with wildcard
div:matches-css(before, content: block*)
-! паттерн регулярного выражения
+! regular expression pattern
div:matches-css(before, content: /block me/)
```
:::caution Ограничения
-Паттерны регулярных выражений **не поддерживают** флаги.
+Regexp patterns **do not support** flags.
:::
:::info Совместимость
-Устаревшие псевдоклассы `:matches-css-before()` и `:matches-css-after()` больше не рекомендуются, но по-прежнему поддерживаются для лучшей совместимости.
+Obsolete pseudo-classes `:matches-css-before()` and `:matches-css-after()` are no longer recommended but still are supported for better compatibility.
:::
-:::danger Старый синтаксис
+:::danger Old syntax
-[Синтаксис обратной совместимости для `:matches-css()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-matches-css) поддерживается, но **не рекомендуется**.
+[Backward compatible syntax for `:matches-css()`](https://github.com/AdguardTeam/ExtendedCss#old-syntax-matches-css) is supported but **not recommended**.
:::
#### Псевдокласс `:matches-attr()` {#extended-css-matches-attr}
-Псевдокласс `:matches-attr()` позволяет выбрать элемент по его атрибутам, особенно если они рандомизированы.
+The `:matches-attr()` pseudo-class allows selecting an element by its attributes, especially if they are randomized.
-**Синтаксис**
+**Syntax**
```text
[target]:matches-attr("name"[="value"])
@@ -3632,34 +3645,34 @@ div:matches-css(before, content: /block me/)
- `name` — требуется, простая строка, *или* строка с подстановочным знаком, *или* регулярное выражение для сопоставления имени атрибута
- `value` — необязательный, простая строка, *или* строка с подстановочным знаком, *или* регулярное выражение для сопоставления значения атрибута
-**Экранирование специальных символов**
+**Escaping special characters**
-Для паттернов **регулярных выражений** `"` и `\` должны быть **экранированы**, например, `div:matches-attr(class=/[\\w]{5}/)`.
+For **regexp** patterns `"` and `\` should be **escaped**, e.g. `div:matches-attr(class=/[\\w]{5}/)`.
**Примеры**
-`div:matches-attr("ad-link")` выбирает элемент `div#target1`:
+`div:matches-attr("ad-link")` selects the element `div#target1`:
```html
```
-`div:matches-attr("data-*"="adBanner")` выбирает элемент `div#target2`:
+`div:matches-attr("data-*"="adBanner")` selects the element `div#target2`:
```html
```
-`div:matches-attr(*unit*=/^click$/)` выбирает элемент `div#target3`:
+`div:matches-attr(*unit*=/^click$/)` selects the element `div#target3`:
```html
```
-`*:matches-attr("/.{5,}delay$/"="/^[0-9]*$/")` выбирает элемент `#target4`:
+`*:matches-attr("/.{5,}delay$/"="/^[0-9]*$/")` selects the element `#target4`:
```html
@@ -3670,15 +3683,15 @@ div:matches-css(before, content: /block me/)
:::caution Ограничения
-Паттерны регулярных выражений **не поддерживают** флаги.
+Regexp patterns **do not support** flags.
:::
#### Псевдокласс `:matches-property()` {#extended-css-property}
-Псевдокласс `:matches-property()` позволяет выбирать элемент, сопоставляя его свойства.
+The `:matches-property()` pseudo-class allows selecting an element by matching its properties.
-**Синтаксис**
+**Syntax**
```text
[target]:matches-property("name"[="value"])
@@ -3688,19 +3701,19 @@ div:matches-css(before, content: /block me/)
- `name` — требуется, простая строка, *или* строка с подстановочным знаком, *или* регулярное выражение для сопоставления имени свойства элемента
- `value` — необязательный, простая строка, *или* строка с подстановочным знаком, *или* регулярное выражение для сопоставления значения свойства элемента
-**Экранирование специальных символов**
+**Escaping special characters**
-Для паттернов **регулярных выражений** `"` и `\` должны быть экранированы, например, `div:matches-property(prop=/[\\w]{4}/)`.
+For **regexp** patterns `"` and `\` must be escaped, e.g. `div:matches-property(prop=/[\\w]{4}/)`.
:::note
-Паттерны регулярных выражений поддерживаются в `name` для любого свойства в цепочке, например, `prop./^unit[\\d]{4}$/.type`.
+Regexp patterns are supported in `name` for any property in chain, e.g. `prop./^unit[\\d]{4}$/.type`.
:::
**Примеры**
-Элемент с такими свойствами:
+An element with such properties:
```javascript
divProperties = {
@@ -3720,7 +3733,7 @@ divProperties = {
};
```
-может быть выбран любым из этих расширенных селекторов:
+can be selected by any of these extended selectors:
```adblock
div:matches-property(check.track)
@@ -3734,26 +3747,26 @@ div:matches-property(memoizedProps.key="null")
div:matches-property(memoizedProps._owner.src=/ad/)
```
-:::tip Для разработчиков фильтров
+:::tip For filter maintainers
-Чтобы проверить свойства конкретного элемента, сделайте следующее:
+To check properties of a specific element, do the following:
-1. Проверьте элемент страницы или выберите его в Инструментах разработчика браузера во вкладке `Элементы`
-1. Запустите `console.dir($0)` во вкладке `Консоль`
+1. Inspect the page element or select it in `Elements` tab of browser DevTools
+1. Run `console.dir($0)` in `Console` tab
:::
:::caution Ограничения
-Паттерны регулярных выражений **не поддерживают** флаги.
+Regexp patterns **do not support** flags.
:::
#### Псевдокласс `:xpath()` {#extended-css-xpath}
-Псевдокласс `:xpath()` позволяет выбирать элементы согласно выражению XPath.
+The `:xpath()` pseudo-class allows selecting an element by evaluating an XPath expression.
-**Синтаксис**
+**Syntax**
```text
[target]:xpath(expression)
@@ -3764,22 +3777,22 @@ div:matches-property(memoizedProps._owner.src=/ad/)
##### Ограничения `:xpath()` {#extended-css-xpath-limitations}
-`target` можно опустить, поэтому использовать его необязательно. Для любого другого псевдокласса это будет означать «применить ко *всем* узлам DOM», но в случае `:xpath()` это просто означает «применить к *целому* документу», и такое применение значительно замедляет выбор элементов. Вот почему такие правила, как `#?#:xpath(expression)`, ограничены поиском внутри тега `body`. Например, правило `#?#:xpath(//div[@data-st-area=\'Advert\'])` парсится как `#?#body:xpath(//div[@data-st- area=\'Advert\'])`.
+`target` can be omitted so it is optional. For any other pseudo-class that would mean "apply to *all* DOM nodes", but in case of `:xpath()` it just means "apply to the *whole* document", and such applying slows elements selecting significantly. That's why rules like `#?#:xpath(expression)` are limited to looking inside the `body` tag. For example, rule `#?#:xpath(//div[@data-st-area=\'Advert\'])` is parsed as `#?#body:xpath(//div[@data-st-area=\'Advert\'])`.
-Расширенные селекторы с `target`, определённым как *любой* селектор, — `*:xpath(expression)` — всё ещё можно использовать, но не рекомендуется. Поэтому следует уточнить `target`.
+Extended selectors with defined `target` as *any* selector — `*:xpath(expression)` — can still be used but it is not recommended, so `target` should be specified instead.
-Корректно работает только в конце селектора, за исключением псевдокласса [:remove()](#remove-pseudos).
+Works properly only at the end of selector, except for [pseudo-class :remove()](#remove-pseudos).
**Примеры**
-`:xpath(//*[@class="banner"])` выбирает элемент `div#target1`:
+`:xpath(//*[@class="banner"])` selects the element `div#target1`:
```html
```
-`:xpath(//*[@class="inner"]/..)` выбирает элемент `div#target2`:
+`:xpath(//*[@class="inner"]/..)` selects the element `div#target2`:
```html
@@ -3790,7 +3803,7 @@ div:matches-property(memoizedProps._owner.src=/ad/)
#### Псевдокласс `:nth-ancestor()` {#extended-css-nth-ancestor}
-Псевдокласс `:nth-ancestor()` позволяет искать *n-ного* предка по отношению к ранее выбранному элементу.
+The `:nth-ancestor()` pseudo-class allows to lookup the *nth* ancestor relative to the previously selected element.
```text
subject:nth-ancestor(n)
@@ -3799,7 +3812,7 @@ subject:nth-ancestor(n)
- `subject` — обязателен. Стандартный или расширенный CSS-селектор
- `n` — обязателен. Число >= 1 и < 256, расстояние до нужного родителя от элемента, выбранного `subject`
-**Синтаксис**
+**Syntax**
```text
subject:nth-ancestor(n)
@@ -3810,11 +3823,11 @@ subject:nth-ancestor(n)
##### Ограничения `:nth-ancestor()` {#extended-css-nth-ancestor-limitations}
-Псевдокласс `:nth-ancestor()` не поддерживается внутри аргумента псевдокласса [`:not()`](#extended-css-not).
+The `:nth-ancestor()` pseudo-class is not supported inside the argument of the [`:not()` pseudo-class](#extended-css-not).
**Примеры**
-Для таких DOM:
+For such DOM:
```html
@@ -3831,13 +3844,13 @@ subject:nth-ancestor(n)
```
-`.child:nth-ancestor(1)` выбирает элемент `div#target1`, `div[class="inner"]:nth-ancestor(3)` выбирает элемент `div#target2`.
+`.child:nth-ancestor(1)` selects the element `div#target1`, `div[class="inner"]:nth-ancestor(3)` selects the element `div#target2`.
#### Псевдокласс `:upward()` {#extended-css-upward}
-Псевдокласс `:upward()` позволяет искать предка по отношению к ранее выбранному элементу.
+The `:upward()` pseudo-class allows to lookup the ancestor relative to the previously selected element.
-**Синтаксис**
+**Syntax**
```text
subject:upward(ancestor)
@@ -3850,11 +3863,11 @@ subject:upward(ancestor)
##### Ограничения `:upward()` {#extended-css-upward-limitations}
-Псевдокласс `:upward()` не поддерживается внутри аргумента псевдокласса [`:not()`](#extended-css-not).
+The `:upward()` pseudo-class is not supported inside the argument of the [`:not()` pseudo-class](#extended-css-not).
**Примеры**
-Для таких DOM:
+For such DOM:
```html
@@ -3871,21 +3884,21 @@ subject:upward(ancestor)
```
-`.inner:upward(div[data])` выбирает элемент `div#target1`, `.inner:upward(div[id])` выбирает элемент `div#target2`, `.child:upward(1)` выбирает элемент `div#target1`, `.inner:upward(3)` выбирает элемент `div#target2`.
+`.inner:upward(div[data])` selects the element `div#target1`, `.inner:upward(div[id])` selects the element `div#target2`, `.child:upward(1)` selects the element `div#target1`, `.inner:upward(3)` selects the element `div#target2`.
#### Псевдокласс `:remove()` и псевдосвойство `remove` {#remove-pseudos}
-Иногда необходимо удалить определённый элемент, а не просто скрыть его или применить какие-либо правила стиля. Для этого можно использовать псевдокласс `:remove()`, а также псевдосвойство `remove`.
+Sometimes, it is necessary to remove a matching element instead of hiding it or applying custom styles. In order to do it, you can use the `:remove()` pseudo-class as well as the `remove` pseudo-property.
-**Псевдокласс `:remove()` может быть только в конце селектора.**
+**Pseudo-class `:remove()` can be placed only at the end of a selector.**
-**Синтаксис**
+**Syntax**
```text
! pseudo-class
selector:remove()
-! псевдосвойство
+! pseudo-property
selector { remove: true; }
```
@@ -3893,11 +3906,11 @@ selector { remove: true; }
##### Ограничения `:remove()` и `remove` {#extended-css-remove-limitations}
-Псевдокласс `:remove()` может корректно работать только в конце селектора.
+The `:remove()` pseudo-class is limited to work properly only at the end of selector.
-Для применения псевдокласса `:remove()` к любому элементу следует использовать [универсальный селектор](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`. В противном случае такой расширенный селектор может считаться некорректным. Например, `.banner > :remove()` недействителен для удаления любого дочернего элемента класса `banner`, поэтому он должен выглядеть как `.banner > *:remove()`.
+For applying the `:remove()` pseudo-class to any element, the [universal selector](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*` should be used. Otherwise such extended selector may be considered as invalid, e.g. `.banner > :remove()` is not valid for removing any child element of `banner` class element, so it should look like `.banner > *:remove()`.
-Если используется псевдокласс `:remove()` или псевдосвойство `remove`, все свойства стиля игнорируются, кроме псевдосвойства [`debug`](#selectors-debug-mode).
+If the `:remove()` pseudo-class or the `remove` pseudo-property is used, all style properties are ignored except for the [`debug` pseudo-property](#selectors-debug-mode).
**Примеры**
@@ -3911,15 +3924,15 @@ div[class]:has(> a > img) { remove: true; }
:::note
-Правила с псевдосвойством `remove` должны использовать маркер `#$?#`: `$` для синтаксиса правил CSS-стиля, `?` для синтаксиса ExtendedCss.
+Rules with the `remove` pseudo-property must use `#$?#` marker: `$` for CSS-style rule syntax, `?` for ExtendedCss syntax.
:::
#### Псевдокласс `:is()` {#extended-css-is}
-Псевдокласс `:is()` позволяет сопоставить любой элемент, который может быть выбран любым из переданных ему селекторов. Некорректные селекторы пропускаются, и псевдокласс работает с допустимыми селекторами без каких-либо ошибок. Наша реализация [нативного`:is()` псевдокласса](https://developer.mozilla.org/ru/docs/Web/CSS/:is).
+The `:is()` pseudo-class allows to match any element that can be selected by any of selectors passed to it. Invalid selectors are skipped and the pseudo-class deals with valid ones with no error thrown. Our implementation of the [native `:is()` pseudo-class](https://developer.mozilla.org/en-US/docs/Web/CSS/:is).
-**Синтаксис**
+**Syntax**
```text
[target]:is(selectors)
@@ -3930,15 +3943,15 @@ div[class]:has(> a > img) { remove: true; }
##### Ограничения `:is()` {#extended-css-is-limitations}
-Правила с псевдоклассом `:is()` должны использовать [нативную реализацию `:is()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:is), если они используют маркер `##` и если это возможно, то есть без других расширенных селекторов внутри. Чтобы принудительно применить правила ExtendedCss с `:is()`, используйте маркер `#?#`/`#$?#` явно.
+Rules with the `:is()` pseudo-class must use the [native implementation of `:is()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:is) if rules use `##` marker and it is possible, i.e. with no other extended selectors inside. To force applying ExtendedCss rules with `:is()`, use `#?#`/`#$?#` marker explicitly.
-Если `selectors` аргумент псевдокласса `:is()` — расширенный селектор, то из-за того, как псевдокласс `:is()` реализован в ExtendedCss 2.0, его невозможно применить к верхнему узлу DOM, который является `html`, т.е. `#?#html:is()` не работает. Таким образом, если `target` не определён или определён как [универсальный селектор](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`, применение расширенного псевдокласса ограничено **`html`дочерними элементами**, например, правила `#?#:is(...)` и `#?#*:is(...)` парсятся как `#?#html *:is(...)`. Обратите внимание, что для стандартного аргумента селектора такого ограничения нет, т.е. `#?#html:is(.locked)` работает нормально.
+If the `:is()` pseudo-class argument `selectors` is an extended selector, due to the way how the `:is()` pseudo-class is implemented in ExtendedCss v2.0, it is impossible to apply it to the top DOM node which is `html`, i.e. `#?#html:is()` does not work. So if `target` is not defined or defined as the [universal selector](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`, the extended pseudo-class applying is limited to **`html`'s children**, e.g. rules `#?#:is(...)` and `#?#*:is(...)` are parsed as `#?#html *:is(...)`. Please note that there is no such limitation for a standard selector argument, i.e. `#?#html:is(.locked)` works fine.
-[Сложные селекторы](https://www.w3.org/TR/selectors-4/#complex) с расширенными псевдоклассами не поддерживаются в качестве аргумента `selectors` для псевдокласса `:is()` — разрешены только [составные](https://www.w3.org/TR/selectors-4/#compound). Ознакомьтесь с примерами, чтобы разобраться в деталях.
+[Complex selectors](https://www.w3.org/TR/selectors-4/#complex) with extended pseudo-classes are not supported as `selectors` argument for `:is()` pseudo-class, only [compound ones](https://www.w3.org/TR/selectors-4/#compound) are allowed. Check examples below for more details.
**Примеры**
-`#container *:is(.inner, .footer)` выбирает только элемент `div#target1`:
+`#container *:is(.inner, .footer)` selects only the element `div#target1`:
```html
@@ -3951,7 +3964,7 @@ div[class]:has(> a > img) { remove: true; }
```
-Из-за ограничений `:is(*:not([class]) > .banner)'` не работает, но `:is(*:not([class]):has(> .banner))` можно использовать вместо него для выбора элемента `div#target2`:
+Due to limitations `:is(*:not([class]) > .banner)'` does not work but `:is(*:not([class]):has(> .banner))` can be used instead of it to select the element `div#target2`:
```html
@@ -3963,9 +3976,9 @@ div[class]:has(> a > img) { remove: true; }
#### Псевдокласс `:not()` {#extended-css-not}
-Псевдокласс `:not()` позволяет выбрать элементы, которые *не соответствуют* селекторам, переданным в качестве аргумента. Неправильные селекторы аргументов не допускаются, и будет выдана ошибка. Наша реализация [псевдокласса`:not()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:not).
+The `:not()` pseudo-class allows to select elements which are *not matched* by selectors passed as argument. Invalid argument selectors are not allowed and error is to be thrown. Our implementation of the [`:not()` pseudo-class](https://developer.mozilla.org/en-US/docs/Web/CSS/:not).
-**Синтаксис**
+**Syntax**
```text
[target]:not(selectors)
@@ -3976,17 +3989,17 @@ div[class]:has(> a > img) { remove: true; }
##### Ограничения `:not()` {#extended-css-not-limitations}
-Правила с псевдоклассом `:not()` должны использовать [нативную реализацию `:not()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:not), если они используют маркер `##` и если это возможно, то есть без других расширенных селекторов внутри. Чтобы принудительно применить правила ExtendedCss с `:not()`, используйте маркер `#?#`/`#$?#` явно.
+Rules with the `:not()` pseudo-class must use the [native implementation of `:not()`](https://developer.mozilla.org/en-US/docs/Web/CSS/:not) if rules use `##` marker and it is possible, i.e. with no other extended selectors inside. To force applying ExtendedCss rules with `:not()`, use `#?#`/`#$?#` marker explicitly.
-Если `selectors` аргумент псевдокласса `:not()` — расширенный селектор, то из-за того, как псевдокласс `:not()` реализован в ExtendedCss 2.0, его невозможно применить к верхнему узлу DOM, который является `html`, т.е. `#?#html:not()` не работает. Таким образом, если `target` не определён или определён как [универсальный селектор](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`, применение расширенного псевдокласса ограничено **дочерними `html`-элементами**, например, правила `#?#:not(...)` и `#?#*:not(...)` парсятся как `#?#html *:not(...)`. Обратите внимание, что для стандартного аргумента селектора такого ограничения нет, т.е. `#?#html:not(.locked)` работает нормально.
+If the `:not()` pseudo-class argument `selectors` is an extended selector, due to the way how the `:not()` pseudo-class is implemented in ExtendedCss v2.0, it is impossible to apply it to the top DOM node which is `html`, i.e. `#?#html:not()` does not work. So if `target` is not defined or defined as the [universal selector](https://www.w3.org/TR/selectors-4/#the-universal-selector) `*`, the extended pseudo-class applying is limited to **`html`'s children**, e.g. rules `#?#:not(...)` and `#?#*:not(...)` are parsed as `#?#html *:not(...)`. Please note that there is no such limitation for a standard selector argument, i.e. `#?#html:not(.locked)` works fine.
-Псевдокласс `:not()` рассматривается как стандартный псевдокласс CSS внутри аргумента псевдокласса [`:upward()`](#extended-css-upward), поскольку `:upward()` поддерживает только стандартные селекторы.
+The `:not()` is considered as a standard CSS pseudo-class inside the argument of the [`:upward()` pseudo-class](#extended-css-upward) because `:upward()` supports only standard selectors.
-«Восходящие» псевдоклассы [`:nth-ancestor()`](#extended-css-nth-ancestor) и [`:upward()`](#extended-css-upward) не поддерживаются внутри аргумента `selectors` для псевдокласса `:not()`.
+"Up-looking" pseudo-classes which are [`:nth-ancestor()`](#extended-css-nth-ancestor) and [`:upward()`](#extended-css-upward) are not supported inside `selectors` argument for `:not()` pseudo-class.
**Примеры**
-`#container > *:not(h2, .text)` выбирает только элемент `div#target1`:
+`#container > *:not(h2, .text)` selects only the element `div#target1`:
```html
@@ -3999,37 +4012,37 @@ div[class]:has(> a > img) { remove: true; }
#### Псевдокласс `:if-not()` (удалён) {#extended-css-if-not}
-:::danger Уведомление об удалении
+:::danger Removal notice
-Псевдокласс `:if-not()` удалён и больше не поддерживается. Правила с ним считаются недействительными.
+The `:if-not()` pseudo-class is removed and is no longer supported. Rules with it are considered as invalid.
:::
-Этот псевдокласс изначально был сокращением для `:not(:has())`. Он поддерживался ExtendedCss для лучшей совместимости с подписками на некоторые фильтры.
+This pseudo-class was basically a shortcut for `:not(:has())`. It was supported by ExtendedCss for better compatibility with some filters subscriptions.
### Приоритет косметических правил {#cosmetic-rules-priority}
-То, как применяются правила **скрытия элементов** и **CSS-правила**, зависит от платформы.
+The way **element hiding** and **CSS rules** are applied is platform-specific.
-**В AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux** мы используем таблицу стилей, встроенную в страницу. Приоритет у косметических правил такой же, как и у любых других таблиц стилей CSS на сайтах. Но есть ограничение: [правила скрытия элементов](#cosmetic-elemhide-rules) и [CSS-правила](#cosmetic-css-rules) не могут обходить встроенные стили. В таких случаях рекомендуется использовать расширенные селекторы или HTML-фильтрацию.
+**In AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux**, we use a stylesheet injected into the page. The priority of cosmetic rules is the same as any other websites' CSS stylesheet. But there is a limitation: [element hiding](#cosmetic-elemhide-rules) and [CSS rules](#cosmetic-css-rules) cannot override inline styles. In such cases, it is recommended to use extended selectors or HTML filtering.
-**В Браузерном расширении AdGuard** используются так называемые «пользовательские таблицы стилей». Их приоритет выше, даже чем у встроенных стилей.
+**In AdGuard Browser Extension**, the so-called "user stylesheets" are used. They have higher priority than even the inline styles.
-**Расширенные CSS-селекторы** используют для работы JavaScript и добавляют встроенные стили сами, поэтому могут игнорировать любой стиль.
+**Extended CSS selectors** use JavaScript to work and basically add an inline style themselves, therefore they can override any style.
## Правила фильтрации HTML {#html-filtering-rules}
-В большинстве случаев для фильтрации рекламы достаточно базовых и косметических правил. Но иногда необходимо изменить HTML-код самой страницы перед её загрузкой. Для этого применяются правила фильтрации HTML-контента. Они позволяют указать, какие HTML-элементы необходимо вырезать из страницы перед тем, как страница попадёт в браузер.
+In most cases, the basis and cosmetic rules are enough to filter ads. But sometimes it is necessary to change the HTML-code of the page itself before it is loaded. This is when you need filtering rules for HTML content. They allow to indicate the HTML elements to be cut out before the browser loads the page.
:::info Совместимость
-Правила HTML-фильтрации поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android, AdGuard для Linux, а также в Браузерном расширении AdGuard для Firefox. Такие правила не работают в расширениях для других браузеров, потому что они не могут модифицировать содержимое страниц на сетевом уровне.
+HTML filtering rules are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, AdGuard for Linux, and AdGuard Browser Extension for Firefox. Such rules do not work in extensions for other browsers because they are unable to modify content on network level.
-Синтаксис с необязательным `value` в атрибутах поддерживается в AdGuard для Windows, AdGuard для Mac и AdGuard для Android с CoreLibs версии 1.18 или выше. Он также поддерживается Браузерным расширением AdGuard версии 5.2 или выше. Для других продуктов и предыдущих версий значение `value` должно быть **всегда** указано. В противном случае правило будет считаться неправильным и игнорироваться.
+The syntax with an optional `value` in the attributes is supported by AdGuard for Windows, AdGuard for Mac, and AdGuard for Android with CoreLibs v1.18 or later. It is also supported by AdGuard Browser Extension v5.2 or later. For the other products and previous versions `value` must **always** be specified. Otherwise, the rule will be treated as incorrect and ignored.
:::
-### Синтаксис
+### Syntax
```text
selector = [tagName] [attributes] [pseudoClasses]
@@ -4050,21 +4063,21 @@ pseudoClasses = pseudoClass *pseudoClass
### Примеры
-**HTML-код:**
+**HTML code:**
```html
```
-**Правило:**
+**Rule:**
```adblock
example.org$$script[data-src="banner"]
```
-Это правило удалит из кода страниц все элементы `script` с атрибутом `data-src`, содержащим подстроку `banner`. Правило применяется только к `example.org` и всем его поддоменам.
+This rule removes all `script` elements with the attribute `data-src` containing the substring `banner`. The rule applies only to `example.org` and all its subdomains.
-Если значение атрибута опущено в правиле, то элемент будет удалён, если он содержит указанный атрибут, независимо от его значения. Таким же образом можно удалить элементы, атрибуты которых не имеют вообще никакого значения.
+If the value of the attribute is omitted in the rule, then the element will be removed if it contains the specified attribute, regardless of its value. This is also the way to remove the elements whose attributes don't have any value at all.
```html
@@ -4075,25 +4088,25 @@ example.org$$script[data-src="banner"]
example.org$$div[some_attribute]
```
-Это правило удаляет все элементы `div` с атрибутом `some_attribute` на `example.org` и всех его поддоменах. Таким образом, оба элемента `div` из приведённого выше примера будут удалены.
+This rule removes all `div` elements with the attribute `some_attribute` on `example.org` and all its subdomains. So, the both `div` elements from the example above will be removed.
### Специальные атрибуты
-Помимо обычных атрибутов, значение которых проверяется у каждого элемента, существует набор специальных атрибутов, которые изменяют принцип работы правила. Ниже приведён список этих атрибутов:
+In addition to usual attributes, which value is every element checked for, there is a set of special attributes that change the way a rule works. Below there is a list of these attributes:
#### `tag-content`
-:::caution Скоро устареет
+:::caution Deprecation notice
-В будущем этот специальный атрибут может перестать поддерживаться. Предпочтительнее использовать псевдокласс `:contains()` там, где это возможно.
+This special attribute may become unsupported in the future. Prefer using the `:contains()` pseudo-class where it is available.
:::
-Это наиболее часто используемый специальный атрибут. Он ограничивает выбор теми элементами, внутренний HTML-код которых содержит указанную подстроку.
+This is the most frequently used special attribute. It limits selection with those elements whose innerHTML code contains the specified substring.
-Используйте `""` для экранирования `"`, например: `$$script[tag-content="alert(""this is ad"")"]`
+You must use `""` to escape `"`, for instance: `$$script[tag-content="alert(""this is ad"")"]`
-Например, рассмотрим такой HTML-код:
+For example, take a look at this HTML code:
```html
```
-Следующее правило удалит все `script`-элементы с подстрокой `banner` в их коде:
+Following rule will delete all `script` elements with a `banner` substring in their code:
```adblock
$$script[tag-content="banner"]
```
-:::caution Ограничения
+:::caution Limitations
-Специальный атрибут `tag-content` не должен появляться в селекторе слева от комбинатора `>`.
+The `tag-content` special attribute must not appear in a selector to the left of a `>` combinator.
:::
#### `wildcard`
-:::caution Скоро устареет
+:::caution Deprecation notice
-В будущем этот специальный атрибут может перестать поддерживаться. Предпочтительнее использовать псевдокласс `:contains()` там, где это возможно.
+This special attribute may become unsupported in the future. Prefer using the `:contains()` pseudo-class where it is available.
:::
-Этот специальный атрибут работает почти как `tag-content` и позволяет проверить внутренний HTML-код документа. Правило проверит, удовлетворяет ли HTML-код элемента заданному [шаблону поиска](https://en.wikipedia.org/wiki/Glob_(programming)).
+This special attribute works almost like `tag-content` and allows you to check the innerHTML code of the document. Rule will check if HTML code of the element fits the [search pattern](https://en.wikipedia.org/wiki/Glob_(programming)).
-Используйте `""` для экранирования `"`, например: `$$script[wildcard=""banner""]`
+You must use `""` to escape `"`, for instance: `$$script[wildcard=""banner""]`
-Например: `$$script[wildcard="*banner*text*"]`
+For example: `$$script[wildcard="*banner*text*"]`
-Оно проверяет, что код элемента содержит две последовательные подстроки `banner` и `text`.
+It checks if the element code contains the two consecutive substrings `banner` and `text`.
-:::caution Ограничения
+:::caution Limitations
-Специальный атрибут `wildcard` не должен появляться в селекторе слева от комбинатора `>`.
+The `wildcard` special attribute must not appear in a selector to the left of a `>` combinator.
:::
#### `max-length`
-:::caution Скоро устареет
+:::caution Deprecation notice
-В будущем этот специальный атрибут может перестать поддерживаться. Предпочтительнее использовать псевдокласс `:contains()` там, где это возможно.
+This special attribute may become unsupported in the future. Prefer using the `:contains()` pseudo-class with a regular expression where it is available.
:::
-Задает максимальную длину содержимого HTML-элемента. Если этот параметр задан и длина содержимого превышает заданное значение, правило не применяется к элементу.
+Specifies the maximum length for content of HTML element. If this parameter is set and the content length exceeds the value, a rule does not apply to the element.
-**Значение по умолчанию**
+**Default value**
-Если этот параметр не задан, то `max-length` считается равным 8192.
+If this parameter is not specified, the `max-length` is considered to be 8192.
Например:
@@ -4155,23 +4168,23 @@ $$script[tag-content="banner"]
$$div[tag-content="banner"][max-length="400"]
```
-Это правило удалит все элементы `div`, код которых содержит подстроку `banner` и длина которых не превышает `400` символов.
+This rule will remove all the `div` elements, whose code contains the substring `banner` and the length of which does not exceed `400` characters.
-:::caution Ограничения
+:::caution Limitations
-Специальный атрибут `max-length` не должен появляться в селекторе слева от комбинатора `>`.
+The `max-length` special attribute must not appear in a selector to the left of a `>` combinator.
:::
#### `min-length`
-:::caution Скоро устареет
+:::caution Deprecation notice
-В будущем этот специальный атрибут может перестать поддерживаться. Предпочтительнее использовать псевдокласс `:contains()` там, где это возможно.
+This special attribute may become unsupported in the future. Prefer using the `:contains()` pseudo-class with a regular expression where it is available.
:::
-Задаёт минимальную длину содержимого HTML-элемента. Если этот параметр задан и длина содержимого меньше заданного значения, правило не применяется к элементу.
+Specifies the minimum length for content of HTML element. If this parameter is set and the content length is less than preset value, a rule does not apply to the element.
Например:
@@ -4179,11 +4192,11 @@ $$div[tag-content="banner"][max-length="400"]
$$div[tag-content="banner"][min-length="400"]
```
-Это правило удалит все элементы `div`, код которых содержит подстроку `banner` и длина которых превышает `400` символов.
+This rule will remove all the `div` elements, whose code contains the substring `banner` and the length of which exceeds `400` characters.
-:::caution Ограничения
+:::caution Limitations
-Специальный атрибут `min-length` не должен появляться в селекторе слева от комбинатора `>`.
+The `min-length` special attribute must not appear in a selector to the left of a `>` combinator.
:::
@@ -4191,69 +4204,69 @@ $$div[tag-content="banner"][min-length="400"]
#### `:contains()`
-##### Синтаксис
+##### Syntax
```text
-:contains(текст без кавычек)
+:contains(unquoted text)
```
или
```text
-:contains(/reg(ular)?ex(pression)?/)
+:contains(/reg(ular )?ex(pression)?/)
```
-:::note Совместимость
+:::note Compatibility
-`:-abp-contains()` и `:has-text()` являются синонимами для `:contains()`.
+`:-abp-contains()` and `:has-text()` are synonyms for `:contains()`.
:::
:::info Совместимость
-Псевдокласс `:contains()` поддерживается AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.13 или выше.
+The `:contains()` pseudo-class is supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.13 or later.
:::
-Требует, чтобы внутренний HTML-код элемента содержал указанный текст или соответствовал указанному регулярному выражению.
+Requires that the inner HTML of the element contains the specified text or matches the specified regular expression.
-:::caution Ограничения
+:::caution Limitations
-Псевдокласс `:contains()` не должен появляться в селекторе слева от комбинатора `>`.
+A `:contains()` pseudo-class must not appear in a selector to the left of a `>` combinator.
:::
### Исключения
-По аналогии с правилами скрытия, существует специальный тип правил, отключающий действие выбранного правила HTML-фильтрации для определённых доменов. Синтаксис тот же, просто нужно заменить `$$` на `$@$`.
+Similar to hiding rules, there is a special type of rules that disable the selected HTML filtering rule for particular domains. The syntax is the same, you just have to change `$$` to `$@$`.
-Например, в фильтре есть правило:
+For example, there is a rule in filter:
```adblock
$$script[tag-content="banner"]
```
-Если вы хотите отключить его для домена `example.com`, вы можете создать правило исключения:
+If you want to disable it for `example.com`, you can create an exception rule:
```adblock
example.com$@$script[tag-content="banner"]
```
-В некоторых случаях может потребоваться отключение всех запрещающих правил. Например, на время тестирования. Для этого воспользуйтесь правилом исключения без указания домена.
+Sometimes, it may be necessary to disable all restriction rules. For example, to conduct tests. To do this, use the exclusion rule without specifying a domain.
```adblock
$@$script[tag-content="banner"]
```
-Применять такие исключения рекомендуется только в случае, когда изменить само правило скрытия невозможно. Во всех остальных случаях лучше изменить исходное правило, используя ограничение на домены.
+We recommend to use this kind of exceptions only if it is not possible to change the hiding rule itself. In other cases it is better to change the original rule, using domain restrictions.
## Правила JavaScript {#javascript-rules}
-AdGuard поддерживает особый тип правил, который позволяет внедрять любой код JavaScript на страницы сайтов.
+AdGuard supports a special type of rules that allows you to inject any JavaScript code to websites pages.
-Мы **настоятельно рекомендуем** использовать [скриптлеты](#scriptlets) вместо JavaScript-правил везде, где это возможно. JS-правила должны помочь в процессе отладки, но в качестве долгосрочного решения следует использовать скриптлеты.
+We **strongly recommend** using [scriptlets](#scriptlets) instead of JavaScript rules whenever possible. JS rules are supposed to help with debugging, but as a long-time solution a scriptlet rule should be used.
-**Синтаксис**
+**Syntax**
```text
rule = [domains] "#%#" script
@@ -4268,51 +4281,51 @@ rule = [domains] "#%#" script
**Исключения**
-По аналогии с правилами скрытия, существует специальный тип правил, отключающий действие выбранного javascript-правила фильтрации для определённых доменов. Синтаксис тот же, просто нужно заменить `#%#` на `#@%#`.
+Similar to hiding rules, there is a special type of rules that disable the selected JavaScript rule for particular domains. The syntax is the same, you just have to change `#%#` to `#@%#`.
-Например, в фильтре есть правило:
+For example, there is a rule in filter:
```adblock
#%#window.__gaq = undefined;
```
-Если вы хотите отключить его для домена `example.com`, вы можете создать правило исключения:
+If you want to disable it for `example.com`, you can create an exception rule:
```adblock
example.com#@%#window.__gaq = undefined;
```
-В некоторых случаях может потребоваться отключение всех запрещающих правил. Например, на время тестирования. Для этого воспользуйтесь правилом исключения без указания домена.
+Sometimes, it may be necessary to disable all restriction rules. For example, to conduct tests. To do this, use the exclusion rule without specifying a domain.
```adblock
#@%#window.__gaq = undefined;
```
-Применять такие исключения рекомендуется только в случае, когда изменить само правило скрытия невозможно. Во всех остальных случаях лучше изменить исходное правило, используя ограничение на домены.
+We recommend to use this kind of exceptions only if it is not possible to change the hiding rule itself. In other cases it is better to change the original rule, using domain restrictions.
:::caution Ограничения
-Правила JavaScript можно использовать только [**в доверенных фильтрах**](#trusted-filters).
+JavaScript rules can only be used [**in trusted filters**](#trusted-filters).
:::
:::info Совместимость
-JavaScript-правила не поддерживаются в AdGuard Content Blocker.
+JavaScript rules are not supported by AdGuard Content Blocker.
:::
## Правила скриптлета {#scriptlets}
-Скриптлет — это функция JavaScript с расширенными возможностями для блокировки контента. Такие функции могут использоваться в декларативной манере в правилах фильтрации AdGuard.
+Scriptlet is a JavaScript function that provides extended capabilities for content blocking. These functions can be used in a declarative manner in AdGuard filtering rules.
:::note
-AdGuard поддерживает множество различных скриптлетов. Чтобы добиться совместимости между различными блокировщиками, мы также поддерживаем синтаксис uBO и ABP.
+AdGuard supports a lot of different scriptlets. In order to achieve cross-blocker compatibility, we also support syntax of uBO and ABP.
:::
-**Синтаксис правил блокировки**
+**Blocking rules syntax**
```text
[domains]#%#//scriptlet(name[, arguments])
@@ -4324,21 +4337,21 @@ AdGuard поддерживает множество различных скри
**Примеры**
-1. Применить скриптлет `abort-on-property-read` на всех страницах сайта `example.org` и его поддоменах, и передать ему аргумент `alert`:
+1. Apply the `abort-on-property-read` scriptlet on all pages of `example.org` and its subdomains, and pass it an `alert` argument:
```adblock
example.org#%#//scriptlet('abort-on-property-read', 'alert')
```
-1. Удалить класс `branding` из всех элементов `div[class^="inner"]` на всех страницах сайта `example.org` и его поддоменах:
+1. Remove the `branding` class from all `div[class^="inner"]` elements on all pages of `example.org` and its subdomains:
```adblock
example.org#%#//scriptlet('remove-class', 'branding', 'div[class^="inner"]')
```
-**Синтаксис правил исключений**
+**Exception rules syntax**
-Правила исключений могут отключать некоторые скриптлеты на определённых доменах. Синтаксис правил исключений скриптлетов аналогичен обычным правилам скриптлетов, но использует `#@%#` вместо `#%#`:
+Exception rules can disable some scriptlets on particular domains. The syntax for exception scriptlet rules is similar to normal scriptlet rules but uses `#@%#` instead of `#%#`:
```text
[domains]#@%#//scriptlet([name[, arguments]])
@@ -4350,28 +4363,28 @@ AdGuard поддерживает множество различных скри
**Примеры**
-1. Отключить определённое правило скриптлетов, чтобы только `abort-on-property-read` применялось только на `example.org` и его поддоменах:
+1. Disable specific scriptlet rule so that only `abort-on-property-read` is applied only on `example.org` and its subdomains:
```adblock
example.org,example.com#%#//scriptlet("abort-on-property-read", "alert")
example.com#@%#//scriptlet("abort-on-property-read", "alert")
```
-1. Отключить все скриптлеты `abort-on-property-read` для `example.com` и его поддоменов:
+1. Disable all `abort-on-property-read` scriptlets for `example.com` and its subdomains:
```adblock
example.org,example.com#%#//scriptlet("abort-on-property-read", "alert")
example.com#@%#//scriptlet("abort-on-property-read")
```
-1. Отключить все скриптлеты для `example.com` и его поддоменов:
+1. Disable all scriptlets for `example.com` and its subdomains:
```adblock
example.org,example.com#%#//scriptlet("abort-on-property-read", "alert")
example.com#@%#//scriptlet()
```
-1. Применить `set-constant` и `set-cookie` к любой веб-странице. Из-за специального правила исключения скриптов только скрипт `set-constant` будет применён на `example.org` и его поддоменах:
+1. Apply `set-constant` and `set-cookie` to any web page, but due to special scriptlet exception rule only the `set-constant` scriptlet will be applied on `example.org` and its subdomains:
```adblock
#%#//scriptlet('set-constant', 'adList', 'emptyArr')
@@ -4379,7 +4392,7 @@ AdGuard поддерживает множество различных скри
example.org#@%#//scriptlet('set-cookie')
```
-1. Применить `adjust-setInterval` к любой веб-странице и `set-local-storage-item` на `example.com` и его поддоменах, но есть также несколько правил исключения скриптлетов, поэтому правила скриптлетов не будут применяться на `example.com` и его поддоменах:
+1. Apply `adjust-setInterval` to any web page and `set-local-storage-item` on `example.com` and its subdomains, but there are also multiple scriptlet exception rules, so no scriptlet rules will be applied on `example.com` and its subdomains:
```adblock
#%#//scriptlet('adjust-setInterval', 'count', '*', '0.001')
@@ -4387,49 +4400,49 @@ AdGuard поддерживает множество различных скри
example.com#@%#//scriptlet()
```
-Подробнее [об отладке скриптлетов](#debug-scriptlets).
+Learn more about [how to debug scriptlets](#debug-scriptlets).
-Более подробную информацию о скриптлетах можно найти [на GitHub](https://github.com/AdguardTeam/Scriptlets#scriptlets).
+More information about scriptlets can be found [on GitHub](https://github.com/AdguardTeam/Scriptlets#scriptlets).
:::info Совместимость
-Скриптлеты не поддерживаются в AdGuard Content Blocker.
+Scriptlet rules are not supported by AdGuard Content Blocker.
-Полный синтаксис правил-исключений скриптлетов поддерживается AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.16 или выше, а также Браузерным расширением AdGuard для Chrome, Firefox и Edge с [TSUrlFilter][] версии 3.0 или выше. Предыдущие версии поддерживали только правила исключений, которые отключали определённые скриптлеты.
+The full syntax of scriptlet exception rules is supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.16 or later, and AdGuard Browser Extension for Chrome, Firefox, and Edge with [TSUrlFilter][] v3.0 or later. Previous versions only support exception rules that disable specific scriptlets.
:::
### Доверенные скриптлеты {#trusted-scriptlets}
-Доверенные скриптлеты — это [скриптлеты](#scriptlets) с расширенной функциональностью. У них тот же синтаксис и ограничения. У имён доверенных скриптлетов есть префикс `trusted-`, например, `trusted-set-cookie`, чтобы их было легко отличить от обычных скриптлетов.
+Trusted scriptlets are [scriptlets](#scriptlets) with extended functionality. It means the same syntax and restrictions. Trusted scriptlet names are prefixed with `trusted-`, e.g. `trusted-set-cookie`, to be easily distinguished from common scriptlets.
:::note
-Доверенные скриптлеты несовместимы с другими блокировщиками рекламы, кроме AdGuard.
+Trusted scriptlets are not compatible with other ad blockers except AdGuard.
:::
:::caution Ограничения
-Правила доверенных скриптлетов могут использоваться только [**в доверенных фильтрах**](#trusted-filters).
+Trusted scriptlets rules can only be used [**in trusted filters**](#trusted-filters).
:::
:::info Совместимость
-Правила доверенных скриптлетов не поддерживаются в AdGuard Content Blocker.
+Trusted scriptlets rules are not supported by AdGuard Content Blocker.
:::
-Подробнее [об отладке скриптлетов](#debug-scriptlets).
+Learn more about [how to debug scriptlets](#debug-scriptlets).
-Более подробную информацию о доверенных скриптлетах можно найти [на GitHub](https://github.com/AdguardTeam/Scriptlets#trusted-scriptlets).
+More information about trusted scriptlets can be found [on GitHub](https://github.com/AdguardTeam/Scriptlets#trusted-scriptlets).
## Модификаторы для небазовых правил {#non-basic-rules-modifiers}
-Любое правило можно изменить с помощью модификаторов, описанных ниже.
+Each rule can be modified using the modifiers described in the following paragraphs.
-**Синтаксис** {#non-basic-rules-modifiers-syntax}
+**Syntax** {#non-basic-rules-modifiers-syntax}
```text
rule = "[$" modifiers "]" [rule text]
@@ -4439,9 +4452,9 @@ modifiers = modifier0[, modifier1[, ...[, modifierN]]]
- **`modifier`** — набор модификаторов, описанных ниже.
- **`rule text`** — правило, которое нужно модифицировать.
-Например: `[$domain=example.com,app=test_app]##selector`.
+For example, `[$domain=example.com,app=test_app]##selector`.
-В значениях модификаторов следующие символы должны быть экранированы: `[`, `]`, `,` и `\` (если он не используется для экранирования). Используйте `\`, чтобы экранировать их. Например, экранированная скобка выглядит так: `\]`.
+In the modifiers values, the following characters must be escaped: `[`, `]`, `,`, and `\` (unless it is used for the escaping). Use `\` to escape them. For example, an escaped bracket looks like this: `\]`.
| Модификатор \ Продукты | [Приложения CoreLibs][cl-apps] | [AdGuard для Chromium][ext-chr] | [AdGuard для Chrome MV3][ext-mv3] | [AdGuard для Firefox][ext-ff] | [AdGuard для iOS][ios-app] | [AdGuard для Safari][ext-saf] | [AdGuard Content Blocker][and-cb] |
| ------------------------------------- |:------------------------------:|:---------------------------------------------:|:------------------------------------------------:|:---------------------------------------------:|:--------------------------:|:-----------------------------:|:---------------------------------:|
@@ -4460,7 +4473,7 @@ modifiers = modifier0[, modifier1[, ...[, modifierN]]]
### **`$app`** {#non-basic-app-modifier}
-Модификатор `$app` ограничивает действие правила до конкретного приложения или списка приложений. Поведение и синтаксис модификатора полностью совпадают с соответствующим [модификатором `$app` для базовых правил](#app-modifier).
+`$app` modifier lets you narrow the rule coverage down to a specific application or a list of applications. The modifier's behavior and syntax perfectly match the corresponding [basic rules `$app` modifier](#app-modifier).
**Примеры**
@@ -4471,13 +4484,13 @@ modifiers = modifier0[, modifier1[, ...[, modifierN]]]
:::info Совместимость
-Правила с модификатором `$app` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux.
+Such rules with `$app` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux.
:::
### **`$domain`** {#non-basic-domain-modifier}
-Модификатор `$domain` ограничивает область действия правила списком доменов и их поддоменов. Поведение и синтаксис модификатора полностью совпадают с соответствующим [модификатором `$domain` для базовых правил](#domain-modifier).
+`$domain` modifier limits the rule application area to a list of domains and their subdomains. The modifier's behavior and syntax perfectly match the corresponding [basic rules `$domain` modifier](#domain-modifier).
**Примеры**
@@ -4485,44 +4498,44 @@ modifiers = modifier0[, modifier1[, ...[, modifierN]]]
- `[$domain=example.com|example.org]` скрывает элемент с атрибутом `id` равным `adblock` на доменах `example.com`, `example.org` и всех их поддоменах.
- `[$domain=~example.com]##.textad` скрывает `div`-элементы с классом `textad` на всех доменах, кроме `example.com` и всех его поддоменов.
-Существует 2 способа указать ограничения домена для небазовых правил:
+There are 2 ways to specify domain restrictions for non-basic rules:
-1. «классический»: обозначить ограничение на домены перед маской и атрибутами правила: `example.com##.textad`;
-2. с помощью модификаторов: обозначить ограничение на домены через модификатор `$domain`: `[$domain=example.com]##.textad`.
+1. the "classic" way is to specify domains before rule mask and attributes: `example.com##.textad`;
+2. the modifier approach is to specify domains via `$domain` modifier: `[$domain=example.com]##.textad`.
-Однако правила с ограничением доменов смешанного стиля считаются недействительными. Так, например, правило `[$domain=example.org]example.com##.textad` будет проигнорировано.
+But rules with mixed style domains restriction are considered invalid. So, for example, the rule `[$domain=example.org]example.com##.textad` will be ignored.
### Небазовые ограничения модификатора `$domain` {#non-basic-domain-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-Так как небазовый `$domain` работает так же, как и базовый, он имеет те же [ограничения](#domain-modifier-limitations).
+Since the non-basic `$domain` works the same as the basic one, it has the same [limitations](#domain-modifier-limitations).
:::
:::info Совместимость
-Такие правила с модификатором `$domain` поддерживаются AdGuard для Windows, AdGuard для Mac, AdGuard для Android, Браузерным расширением AdGuard для Chrome, Chrome MV3, Firefox и Edge.
+Such rules with `$domain` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, AdGuard Browser Extension for Chrome, Chrome MV3, Firefox, and Edge.
:::
### **`$path`** {#non-basic-path-modifier}
-Модификатор `$path` ограничивает область применения правила определёнными местами или страницами на сайтах.
+`$path` modifier limits the rule application area to specific locations or pages on websites.
-**Синтаксис**
+**Syntax**
```text
$path ["=" pattern]
```
-`pattern` — опционально, маска пути, которой ограничивается правило. Его синтаксис и поведение почти такие же, как [в шаблоне базовых правил](#basic-rules-syntax). Вы также можете использовать [специальные символы](#basic-rules-special-characters), кроме `||`, который в этом случае не имеет смысла (см. примеры ниже).
+`pattern` — optional, a path mask to which the rule is restricted. Its syntax and behavior are pretty much the same as with the [pattern for basic rules](#basic-rules-syntax). You can also use [special characters](#basic-rules-special-characters), except for `||`, which does not make any sense in this case (see examples below).
-Если не задан `pattern` для `$path`, правило будет применяться только на главной странице сайта.
+If `pattern` is not set for `$path`, rule will apply only on the main page of website.
-Модификатор `$path` также соответствует строке запроса.
+`$path` modifier matches the query string as well.
-Модификатор `$path` поддерживает регулярные выражения [так же, как и базовые правила](#regexp-support).
+`$path` modifier supports regular expressions in [the same way](#regexp-support) basic rules do.
**Примеры**
@@ -4537,21 +4550,21 @@ $path ["=" pattern]
:::info Совместимость
-Правила с модификатором `$path` не поддерживаются AdGuard Content Blocker.
+Rules with `$path` modifier are not supported by AdGuard Content Blocker.
:::
### **`$url`** {#non-basic-url-modifier}
-Модификатор `$url` ограничивает действие правила URL-адресами, соответствующими указанной маске.
+`$url` modifier limits the rule application area to URLs matching the specified mask.
-**Синтаксис**
+**Syntax**
```text
url = pattern
```
-где `pattern` практически то же самое, что и [`pattern` базовых правил](#basic-rules-syntax) за исключением того, что [некоторые символы](#non-basic-rules-modifiers-syntax) должны быть экранированы. [Специальные символы](#basic-rules-special-characters) и [регулярные выражения](#regexp-support) также поддерживаются.
+where `pattern` is pretty much the same as [`pattern` of the basic rules](#basic-rules-syntax) assuming that [some characters](#non-basic-rules-modifiers-syntax) must be escaped. The [special characters](#basic-rules-special-characters) and [regular expressions](#regexp-support) are supported as well.
**Примеры**
@@ -4561,25 +4574,25 @@ url = pattern
#### Ограничения модификатора `$url` {#non-basic-url-modifier-limitations}
-:::caution Ограничения
+:::caution Limitations
-В Браузерном расширении AdGuard небазовый модификатор `$url` несовместим с доменно-специфичными правилами и другими небазовыми модификаторами — [`$domain`](#non-basic-domain-modifier) и [`$path`](#non-basic-path-modifier). Например, правило `[$url=/category/*]example.com###textad` не будет применено.
+In AdGuard Browser Extension, non-basic `$url` modifier is not compatible with domain-specific rules and other non-basic modifiers — [`$domain`](#non-basic-domain-modifier) and [`$path`](#non-basic-path-modifier). For example, the rule `[$url=/category/*]example.com###textad` will not be applied.
:::
:::info Совместимость
-Правила с модификатором `$url` поддерживаются в AdGuard для Windows, AdGuard для Mac, AdGuard для Android и AdGuard для Linux с [CoreLibs][] версии 1.11 или выше, и Браузерным расширением AdGuard с [TSUrlFilter][] версии 3.0.0 или выше.
+Rules with the `$url` modifier are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux with [CoreLibs][] v1.11 or later, and AdGuard Browser Extension with [TSUrlFilter][] v3.0.0 or later.
:::
## Информация для разработчиков фильтров
-Если вы разрабатываете сторонний фильтр, известный AdGuard, вам может быть интересна информация, представленная в этом разделе. Имейте в виду, что подсказки будут применяться только к зарегистрированным фильтрам. Фильтр считается зарегистрированным и известным AdGuard, если он присутствует [в индексе известных фильтров](https://filters.adtidy.org/extension/chromium/filters.json). Если вы хотите, чтобы ваш фильтр был зарегистрирован, направьте запрос в [репозиторий AdguardFilters](https://github.com/AdguardTeam/AdguardFilters).
+If you maintain a third-party filter that is known to AdGuard, you might be interested in the information presented in this section. Please note that hints will be applied to registered filters only. The filter is considered to be registered and known by AdGuard, if it is present in the [known filters index](https://filters.adtidy.org/extension/chromium/filters.json). If you want your filter to be registered, please file an issue to [AdguardFilters repo](https://github.com/AdguardTeam/AdguardFilters).
### Директивы препроцессора
-Мы предоставляем директивы препроцессора, которые могут использоваться разработчиками фильтров для улучшения совместимости с различными блокировщиками рекламы, а также обеспечиваем:
+We provide preprocessor directives that can be used by filter maintainers to improve compatibility with different ad blockers and provide:
- [включение файла](#include-directive)
- [условное применение правил по типу блокировщика рекламы](#conditions-directive)
@@ -4587,66 +4600,66 @@ url = pattern
:::note
-Любая ошибка в директиве препроцессора приведёт к тому, что AdGuard не сможет обновить фильтр так же, как если бы URL-адрес фильтра был недоступен.
+Any mistake in a preprocessor directive will lead to AdGuard failing the filter update in the same way as if the filter URL was unavailable.
-Препроцессорные директивы можно использовать в пользовательских правилах или фильтрах.
+Preprocessor directives can be used in the user rules or in the custom filters.
:::
#### Включение файла {#include-directive}
-Директива `!#include` позволяет включить содержимое указанного файла в фильтр. Она поддерживает только файлы из того же источника, чтобы удостовериться, что разработчик фильтров является владельцем указанного файла. Включённый файл также может содержать директивы препроцессора (даже другие`!#include`-директивы). Блокировщики должны принимать во внимание случай рекурсивного использования `!#include` и внедрять защитный механизм.
+The `!#include` directive allows to include contents of a specified file into the filter. It supports only files from the same origin to make sure that the filter maintainer is in control of the specified file. The included file can also contain pre-directives (even other `!#include` directives). Ad blockers should consider the case of recursive `!#include` and implement a protection mechanism.
-**Синтаксис**
+**Syntax**
```adblock
!#include file_path
```
-где `file_path` — абсолютный или относительный путь к файлу одного и того же источника, который должен быть включён.
+where `file_path` is a same origin absolute or relative file path to be included.
-Файлы должны находиться на том же домене, но могут быть расположены в другой директории.
+The files must originate from the same domain, but may be located in a different folder.
-Если включённый файл не найден или недоступен, не будут работать обновления всего фильтра.
+If included file is not found or unavailable, the whole filter update should fail.
-Ограничение по источнику должно быть отключено для локальных пользовательских фильтров.
+Same-origin limitation should be disabled for local custom filters.
**Примеры**
-URL фильтра: `https://example.org/path/filter.txt`
+Filter URL: `https://example.org/path/filter.txt`
```adblock
-! Корректный (тот же источник):
+! Valid (same origin):
!#include https://example.org/path/includedfile.txt
!
-! Корректный (относительный путь):
+! Valid (relative path):
!#include /includedfile.txt
!#include ../path2/includedfile.txt
!
-! Некорректный (другой источник):
+! Invalid (another origin):
!#include https://domain.com/path/includedfile.txt
```
#### Условия {#conditions-directive}
-Разработчики фильтра могут использовать условия, чтобы подставлять разные правила в зависимости от типа блокировщика. Директива с условием, начинающаяся с директивы `!#if`, должна явно прерываться директивой `!#endif`. Условия поддерживают все основные логические операторы.
+Filter maintainers can use conditions to supply different rules depending on the ad blocker type. A conditional directive beginning with an `!#if` directive must explicitly be terminated with an `!#endif` directive. Conditions support all basic logical operators.
-Есть два возможных сценария:
+There are two possible scenarios:
-1. Если блокировщик рекламы встречает директиву `!#if` и не встречает директиву `!#else`, то он компилирует код между директивами `!#if` и `!#endif` только в том случае, если указанное условие истинно.
+1. When an ad blocker encounters an `!#if` directive and no `!#else` directive, it will compile the code between `!#if` and `!#endif` directives only if the specified condition is true.
-1. Если существует директива `!#else`, код между `!#if` и `!#else` будет скомпилирован, если условие истинно; в противном случае будет скомпилирован код между `!#else` и `!#endif`.
+1. If there is an `!#else` directive, the code between `!#if` and `!#else` will be compiled if the condition is true; otherwise, the code between `!#else` and `!#endif` will be compiled.
:::note
-Пробелы имеют значение. `!#if` является допустимой директивой, а `!# if` — нет.
+Whitespaces matter. `!#if` is a valid directive, while `!# if` is not.
:::
-**Синтаксис**
+**Syntax**
```adblock
-!#if (условия)
+!#if (conditions)
rules_list
!#endif
```
@@ -4654,14 +4667,14 @@ rules_list
или
```adblock
-!#if (условия)
+!#if (conditions)
true_conditions_rules_list
!#else
false_conditions_rules_list
!#endif
```
-где:
+where:
- `!#if (условия)` — начало блока при выполнении условий
- `conditions` — точно так же, как и в случае с некоторыми популярными языками программирования, условия препроцессинга основаны на константах, объявляемых блокировщиками. Разработчики блокировщиков самостоятельно определяют, какие именно константы объявлять. Возможные значения:
@@ -4688,7 +4701,7 @@ false_conditions_rules_list
**Примеры**
```adblock
-! для всех продуктов AdGuard, кроме AdGuard для Safari
+! for all AdGuard products except AdGuard for Safari
!#if (adguard && !adguard_ext_safari)
||example.org^$third-party
domain.com##div.ad
@@ -4696,7 +4709,7 @@ domain.com##div.ad
```
```adblock
-! директивы можно комбинировать
+! directives even can be combined
!#if (adguard_app_android)
!#include /androidspecific.txt
!#endif
@@ -4704,20 +4717,20 @@ domain.com##div.ad
```adblock
!#if (adguard && !adguard_ext_safari)
-! для всех продуктов AdGuard, кроме AdGuard для Safari
+! for all AdGuard products except AdGuard for Safari
||example.org^$third-party
domain.com##div.ad
!#else
-! только для AdGuard для Safari
+! for AdGuard for Safari only
||subdomain.example.org^$third-party
!#endif
```
:::info Совместимость
-Директива `!#else` поддерживается [FiltersDownloader][gh-filters-downloader] версии 1.1.20 или выше.
+The `!#else` directive is supported by the [FiltersDownloader][gh-filters-downloader] v1.1.20 or later.
-Он уже поддерживается для списков фильтров, составленных с помощью [FiltersRegistry][], но всё ещё может не поддерживаться продуктами AdGuard при добавлении списка фильтров с `!#else` в качестве пользовательского. Следующие продукты будут поддерживать его в указанных версиях или более поздних версиях:
+It is already supported for filter lists compiled by the [FiltersRegistry][], but it still may not be supported by AdGuard products when adding a filter list with `!#else` as a custom one. The following products will support it in the mentioned versions or later:
- AdGuard для Windows, Mac и Android c [CoreLibs][] 1.13;
- Браузерное расширение AdGuard 4.2.208;
@@ -4727,9 +4740,9 @@ domain.com##div.ad
#### Правила фильтрации в Safari {#safari-affinity-directive}
-Лимит каждого блокировщика контента Safari — 150 000 активных правил. Но в AdGuard для Safari и AdGuard для iOS мы разделили правила на 6 блокировщиков контента, тем самым увеличив лимит правил до 900 000.
+Safari's limit for each content blocker is 150,000 active rules. But in AdGuard for Safari and AdGuard for iOS, we've split the rules into 6 content blockers, thus increasing the rule limit to 900,000.
-Какие фильтры содержатся в каждом блокировщике контента:
+Here is the composition of each content blocker:
- AdGuard General — Блокировка рекламы, Языковые
- AdGuard Privacy — Антитрекинг
@@ -4738,15 +4751,15 @@ domain.com##div.ad
- AdGuard Other — Другие
- AdGuard Custom — Собственные
-Пользовательские правила и белый список добавляются в каждый блокировщик контента.
+User rules and allowlist are added to every content blocker.
:::caution
-Основной недостаток использования нескольких блокировщиков контента в том, что правила из разных блокировщиков применяются независимо друг от друга. На правила блокировки это не влияет, но с правилами разблокировки могут быть проблемы. Если правило блокировки есть в одном блокировщике контента, а исключение — в другом, то исключение не сработает. Разработчики фильтров используют `!#safari_cb_affinity`, чтобы указать, к какому блокировщику контента принадлежат правила.
+The main disadvantage of using multiple content blockers is that rules from different blockers are applied independently. Blocking rules are not affected by this, but unblocking rules may cause problems. If a blocking rule is in one content blocker and an exception is in another, the exception will not work. Filter maintainers use `!#safari_cb_affinity` to define Safari content blocker affinity for the rules inside of the directive block.
:::
-**Синтаксис**
+**Syntax**
```adblock
!#safari_cb_affinity(content_blockers)
@@ -4754,7 +4767,7 @@ rules_list
!#safari_cb_affinity
```
-где:
+where:
- `!#safari_cb_affinity(content_blockers)` — начало блока
- `content_blockers` — список блокировщиков контента, разделённых запятой. Возможные значения:
@@ -4771,14 +4784,14 @@ rules_list
**Примеры**
```adblock
-! чтобы не скрывать указанный элемент, который скрывается Базовым фильтром:
+! to unhide specific element which is hidden by AdGuard Base filter:
!#safari_cb_affinity(general)
example.org#@#.adBanner
!#safari_cb_affinity
```
```adblock
-! чтобы разблокировать запрос, который блокируется Фильтром счётчиков и систем аналитики:
+! to allowlist basic rule from AdGuard Tracking Protection filter:
!#safari_cb_affinity(privacy)
@@||example.org^
!#safari_cb_affinity
@@ -4786,31 +4799,31 @@ example.org#@#.adBanner
### Подсказки
-Hint (подсказка) — это специальный комментарий, инструкция к компилятору фильтров, используемому на стороне сервера (см. [FiltersRegistry][]).
+"Hint" is a special comment, instruction to the filters compiler used on the server side (see [FiltersRegistry][]).
-**Синтаксис**
+**Syntax**
```adblock
!+ HINT_NAME1(PARAMS) HINT_NAME2(PARAMS)
```
-Можно применить несколько подсказок.
+Multiple hints can be applied.
#### Подсказка `NOT_OPTIMIZED`
-Для каждого фильтра AdGuard существуют две версии: полная и оптимизированная. Оптимизированная версия намного легче и не содержит правил, которые не используются вообще или используются редко.
+For each filter, AdGuard compiles two versions: full and optimized. Optimized version is much more lightweight and does not contain rules which are not used at all or used rarely.
-Частота использования правил определяется собранной [статистикой по рекламным фильтрам](../tracking-filter-statistics). Но оптимизация основана также на исходной конфигурации для каждого фильтра. Например, вот так это выглядит для Базового фильтра:
+Rules usage frequency comes from the collected [filter rules statistics](../tracking-filter-statistics). But filters optimization is based on more than that — some filters have specific configuration. This is how it looks like for Base filter:
```text
-"filter": Базовый фильтр AdGuard,
+"filter": AdGuard Base filter,
"percent": 30,
"minPercent": 20,
"maxPercent": 40,
"strict": true
```
-где:
+where:
- **filter** — идентификатор фильтра
- **percent** — ожидаемый процент оптимизации `~= (количество правил в оптимизированном фильтре) / (количество правил в исходном фильтре) * 100`
@@ -4818,21 +4831,21 @@ Hint (подсказка) — это специальный комментари
- **maxPercent** — верхняя граница значения `percent`
- **strict** — если включены `percent < minPercent` или `percent > maxPercent` и строгий режим, то компиляция фильтра должна завершиться неудачно, в противном случае должны использоваться оригинальные правила
-Другими словами, `percent` — это «уровень сжатия». Например, для Базового фильтра он настроен на 40%. Это означает, что алгоритм оптимизации должен убрать 60% правил.
+In other words, `percent` is the "compression level". For instance, for the Base filter it is configured to 40%. It means that optimization algorithm should strip 60% of rules.
-В итоге, вот так выглядят версии Базового фильтра для Браузерного расширения AdGuard для Chrome:
+Eventually, here are the two versions of the Base filter for AdGuard Browser Extension:
- полная: https://filters.adtidy.org/extension/chromium/filters/2.txt
- оптимизированная: https://filters.adtidy.org/extension/chromium/filters/2_optimized.txt
-**Если вы хотите добавить правило, которое не должно удаляться при оптимизации, используйте подсказку `NOT_OPTIMIZED`:**
+**If you want to add a rule which should not be removed at optimization use the `NOT_OPTIMIZED` hint:**
```adblock
!+ NOT_OPTIMIZED
||example.org^
```
-**А такое правило не будет оптимизировано только для AdGuard для Android:**
+**And this rule will not be optimized only for AdGuard for Android:**
```adblock
!+ NOT_OPTIMIZED PLATFORM(android)
@@ -4841,7 +4854,7 @@ Hint (подсказка) — это специальный комментари
#### Подсказки `PLATFORM` и `NOT_PLATFORM`
-Записи этого типа позволяют указывать платформу, для которой применяется правило. Ниже представлен список используемых платформ и ссылки на Базовый фильтр для каждой из них:
+Used to specify the platforms to apply the rules. List of existing platforms and links to Base filter, for example, for each of them:
- `windows` — AdGuard для Windows — [https://filters.adtidy.org/windows/filters/2.txt](https://filters.adtidy.org/windows/filters/2.txt)
@@ -4871,14 +4884,14 @@ Hint (подсказка) — это специальный комментари
**Примеры**
-Это правило будет действовать только в AdGuard для Windows, Mac и Android:
+This rule will be available only in AdGuard for Windows, Mac, Android:
```adblock
!+ PLATFORM(windows,mac,android)
||example.org^
```
-За исключением AdGuard для Safari, AdGuard Content Blocker и AdGuard для iOS, это правило доступно на всех платформах:
+Except for AdGuard for Safari, AdGuard Content Blocker, and AdGuard for iOS, this rule is available on all platforms:
```adblock
!+ NOT_PLATFORM(ext_safari, ext_android_cb, ios)
@@ -4887,9 +4900,9 @@ Hint (подсказка) — это специальный комментари
#### `NOT_VALIDATE`
-Эта подсказка используется для пропуска проверки правила. Она актуальна для правил, поддержка которых ещё не добавлена в компилятор фильтров, или для правил, которые были ошибочно отклонены.
+This hint is used to skip validation of the rule. It is useful for rules for which support has not yet been added to the filters compiler, or for rules that are incorrectly discarded.
-**Если вы хотите добавить правило, которое не нужно проверять, используйте подсказку `NOT_VALIDATE`:**
+**If you want to add a rule that should not be validated, use the `NOT_VALIDATE` hint:**
```adblock
!+ NOT_VALIDATE
@@ -4898,13 +4911,13 @@ Hint (подсказка) — это специальный комментари
## Отладка правил фильтрации
-Хоть самые простые правила фильтрации и возможно придумать «в уме», для чего-то чуть более сложного вам потребуются дополнительная помощь в их отладке и повторении. Есть инструменты, которые помогут вам в этом. Вы можете использовать «Инструменты разработчика» в Chrome и их аналоги в других браузерах, но большинство продуктов AdGuard предоставляют и другой инструмент — Журнал фильтрации.
+It may be possible to create simple filtering rules "in your head" but for anything even slightly more complicated you will need additional tools to debug and iterate them. There are tools to assist you with that. You can use DevTools in Chrome and its analogs in other browsers but most AdGuard products provide another one — Filtering log.
### Журнал фильтрации
-Журнал фильтрации — продвинутый инструмент, который полезен в основном разработчикам фильтров. В нём отображаются все веб-запросы, проходящие через AdGuard, даётся исчерпывающая информация по каждому из них, предлагаются различные опции сортировки и другие полезные возможности.
+Filtering log is an advanced tool that will be helpful mostly to filter developers. It lists all web requests that pass through AdGuard, gives you exhaustive information on each of them, offers multiple sorting options, and has other useful features.
-В зависимости от того, какой продукт AdGuard вы используете, журнал фильтрации может находиться в разных местах.
+Depending on which AdGuard product you are using, Filtering log can be located in different places.
- В **AdGuard для Windows** вы найдёте его во вкладке настроек *Блокировка рекламы* или через меню трея
- В **AdGuard для Mac** он располагается в разделе *Настройки → Дополнительно → Журнал фильтрации*
@@ -4913,17 +4926,17 @@ Hint (подсказка) — это специальный комментари
:::note
-В **AdGuard для iOS** и в **AdGuard для Safari** Журнал фильтрации отсутствует из-за особенностей реализации блокировщиков контента в Safari. AdGuard сам не видит веб-запросы и поэтому не может отображать их.
+In **AdGuard for iOS** and **AdGuard for Safari**, Filtering log does not exist because of the way content blockers are implemented in Safari. AdGuard does not see the web requests and therefore cannot display them.
:::
### Режим отладки селекторов {#selectors-debug-mode}
-Иногда может понадобиться проверить производительность того или иного селектора или таблицы стилей. Чтобы сделать это без непосредственного взаимодействия с JavaScript, вы можете использовать свойство стиля `debug`. Когда `ExtendedCss` встречает это свойство, он включает режим отладки для конкретного селектора или для всех селекторов, в зависимости от значения `debug`.
+Sometimes, you might need to check the performance of a given selector or a stylesheet. In order to do it without interacting with JavaScript directly, you can use a special `debug` style property. When `ExtendedCss` meets this property, it enables the debugging mode either for a single selector or for all selectors, depending on the `debug` value.
-Откройте консоль браузера, находясь на веб-странице, чтобы посмотреть статистику по времени, затраченному на применение селектора(-ов). В режиме отладки следующая статистика отображается в виде объекта, где каждый из отлаживаемых селекторов является ключом, а значение — объектом с такими свойствами:
+Open the browser console while on a web page to see the timing statistics for selector(s) that were applied there. Debugging mode displays the following stats as object where each of the debugged selectors are keys, and value is an object with such properties:
-**Всегда выводится:**
+**Always printed:**
- `selectorParsed` — текст разобранного селектора, может отличаться от входного
- `timings` — список узлов DOM, соответствующих селектору
@@ -4933,44 +4946,44 @@ Hint (подсказка) — это специальный комментари
- `standardDeviation` — стандартное отклонение
- `timingsSum` — общее время, ушедшее на все применения селектора на текущей странице
-**Выводится только для удаления псевдонимов:**
+**Printed only for remove pseudos:**
- `removed` — флаг, сигнализирующий об удалении элементов
-**Выводится, если элементы не удалены:**
+**Printed if elements are not removed:**
- `matchedElements` — список узлов DOM, соответствующих селектору
- `styleApplied` — объявление обработанного стиля правила, связанного с селектором
**Примеры**
-**Отладка конкретного селектора:**
+**Debugging a single selector:**
-Когда значение свойства `debug` равно `true`, информация только по этому селектору будет отображена в консоли браузера.
+When the value of the `debug` property is `true`, only information about this selector will be shown in the browser console.
```adblock
#$?#.banner { display: none; debug: true; }
```
-**Включение глобальной отладки:**
+**Enabling global debug:**
-Когда значение свойства `debug` равно `global`, в консоли будет отображаться информация по всем CSS-селекторам, которые были применены на данной странице, для всех правил из любого из включённых фильтров.
+When the value of the `debug` property is `global`, the console will display information about all extended CSS selectors that have matches on the current page, for all the rules from any of the enabled filters.
```adblock
#$?#.banner { display: none; debug: global; }
```
-**Тестирование расширенных селекторов без AdGuard**
+**Testing extended selectors without AdGuard**
-ExtendedCss может быть выполнен на любой странице без использования какого-либо продукта AdGuard. Для этого скопируйте и запустите следующий код в консоли браузера:
+ExtendedCss can be executed on any page without using any AdGuard product. In order to do that you should copy and execute the following code in a browser console:
```js
!function(e,t,d){C=e.createElement(t),C.src=d,C.onload=function(){alert("ExtendedCss loaded successfully")},s=e.getElementsByTagName(t)[0],s?s.parentNode.insertBefore(C,s):(h=e.getElementsByTagName("head")[0],h.appendChild(C))}(document,"script","https://AdguardTeam.github.io/ExtendedCss/extended-css.min.js");
```
-Или установите пользовательский скрипт [ExtendedCssDebugger](https://github.com/AdguardTeam/Userscripts/blob/master/extendedCssDebugger/extended-css.debugger.user.js).
+Alternatively, install the [ExtendedCssDebugger userscript](https://github.com/AdguardTeam/Userscripts/blob/master/extendedCssDebugger/extended-css.debugger.user.js).
-Теперь вы можете использовать `ExtendedCss` глобально и запустить его метод [`query()`](https://github.com/AdguardTeam/ExtendedCss#extended-css-query) как `Document.querySelectorAll()`.
+Now you can now use the `ExtendedCss` from global scope, and run its method [`query()`](https://github.com/AdguardTeam/ExtendedCss#extended-css-query) as `Document.querySelectorAll()`.
**Примеры**
@@ -4983,9 +4996,9 @@ ExtendedCss.query(selector);
### Отладка скриптлетов {#debug-scriptlets}
-Если вы используете Браузерное расширение AdGuard и хотите отладить правило [скриптлета](#scriptlets) или [доверенного скриптлета](#trusted-scriptlets), то можете получить дополнительную информацию, открыв журнал фильтрации. В этом случае скриптлеты перейдут в режим отладки и будут записывать больше информации в браузерную консоль.
+If you are using AdGuard Browser Extension and want to debug a [scriptlet](#scriptlets) or a [trusted scriptlet](#trusted-scriptlets) rule, you can get additional information by opening the Filtering log. In that case, scriptlets will switch to debug mode and there will be more information in the browser console.
-Следующие скриптлеты разработаны специально для отладки:
+The following scriptlets are especially developed for debug purposes:
- [`debug-current-inline-script`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#debug-current-inline-script)
- [`debug-on-property-read`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#debug-on-property-read)
@@ -4995,7 +5008,7 @@ ExtendedCss.query(selector);
- [`log-eval`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#log-eval)
- [`log`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#log)
-Следующие скриптлеты тоже могут быть использованы для отладки:
+The following scriptlets also may be used for debug purposes:
- [`json-prune`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#json-prune)
- [`prevent-fetch`](https://github.com/AdguardTeam/Scriptlets/blob/master/wiki/about-scriptlets.md#prevent-fetch)
@@ -5011,13 +5024,13 @@ ExtendedCss.query(selector);
### Краткие обозначения продуктов {#what-product}
-1. `CoreLibs apps` — [AdGuard для Windows](/adguard-for-windows/features/home-screen), [AdGuard для Mac](/adguard-for-mac/features/main) и [AdGuard для Android](/adguard-for-android/features/protection/ad-blocking) и [AdGuard для Linux](/adguard-for-linux)
-1. `AdGuard для Chromium` — [Браузерное расширение AdGuard](/adguard-browser-extension/availability) для Chrome и других браузеров на основе Chromium, таких как Microsoft Edge и Opera
-1. `AdGuard для Chrome MV3` — [Браузерное расширение AdGuard для Chrome MV3](/adguard-browser-extension/mv3-version)
-1. `AdGuard для Firefox` — [Браузерное расширение AdGuard](/adguard-browser-extension/availability) для Firefox
-1. `AdGuard для iOS` — [AdGuard для iOS](/adguard-for-ios/features/safari-protection) и AdGuard Pro для iOS (для мобильного браузера Safari)
-1. `AdGuard для Safari` — [AdGuard для десктопного браузера Safari](/adguard-for-safari/features/general)
-1. `AdGuard Content Blocker` — [Блокировщик контента](/adguard-content-blocker/overview) для мобильных браузеров Android: Samsung Internet и Яндекс Браузера
+1. `CoreLibs apps` — [AdGuard for Windows](/adguard-for-windows/features/home-screen), [AdGuard for Mac](/adguard-for-mac/features/main), [AdGuard for Android](/adguard-for-android/features/protection/ad-blocking), and [AdGuard for Linux](/adguard-for-linux)
+1. `AdGuard for Chromium` — [AdGuard Browser Extension](/adguard-browser-extension/availability) for Chrome and other Chromium-based browsers such as Microsoft Edge and Opera
+1. `AdGuard for Chrome MV3` — [AdGuard Browser Extension for Chrome MV3](/adguard-browser-extension/mv3-version)
+1. `AdGuard for Firefox` — [AdGuard Browser Extension](/adguard-browser-extension/availability) for Firefox
+1. `AdGuard for iOS` — [AdGuard for iOS](/adguard-for-ios/features/safari-protection) and AdGuard Pro for iOS (for mobile Safari browser)
+1. `AdGuard for Safari` — [AdGuard for desktop Safari browser](/adguard-for-safari/features/general)
+1. `AdGuard Content Blocker` — [Content Blocker](/adguard-content-blocker/overview) for Android mobile browsers: Samsung Internet and Yandex Browser
### Краткие обозначения совместимости {#what-compatibility}
@@ -5035,7 +5048,7 @@ ExtendedCss.query(selector);
[popup-in-mv3]: https://github.com/AdguardTeam/tsurlfilter/tree/master/packages/tsurlfilter/src/rules/declarative-converter#popup
-[по заголовку Sec-Fetch-Dest]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Sec-Fetch-Dest
+[Sec-Fetch-Dest header]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Sec-Fetch-Dest
[jsinject-in-mv3]: https://github.com/AdguardTeam/tsurlfilter/tree/master/packages/tsurlfilter/src/rules/declarative-converter#jsinject
@@ -5055,19 +5068,19 @@ ExtendedCss.query(selector);
[ext-ff]: #what-product "Браузерное расширение AdGuard для Firefox"
[ios-app]: #what-product "AdGuard для iOS и AdGuard Pro для iOS"
[ios-app]: #what-product "AdGuard for iOS and AdGuard Pro for iOS"
+[ios-app]: #what-product "AdGuard for iOS and AdGuard Pro for iOS"
[ext-saf]: #what-product "AdGuard для Safari"
[ext-saf]: #what-product "AdGuard for Safari"
+[ext-saf]: #what-product "AdGuard for Safari"
[and-cb]: #what-product "AdGuard Content Blocker для браузеров Samsung Internet and Яндекс на Android"
[and-cb]: #what-product "AdGuard Content Blocker for Samsung Internet and Yandex Browser on Android"
[gh-filters-downloader]: https://github.com/AdguardTeam/FiltersDownloader
[FiltersRegistry]: https://github.com/AdguardTeam/FiltersRegistry
[c CoreLibs]: https://adguard.com/en/blog/introducing-corelibs.html
-[с CoreLibs]: https://adguard.com/en/blog/introducing-corelibs.html
[CoreLibs]: https://adguard.com/en/blog/introducing-corelibs.html
-[с CoreLibs]: https://adguard.com/ru/blog/introducing-corelibs.html
-[CoreLibs]: https://adguard.com/ru/blog/introducing-corelibs.html
-[с TSUrlFilter]: https://github.com/AdguardTeam/tsurlfilter/tree/master/packages/tsurlfilter#tsurlfilter
+[с CoreLibs]: https://adguard.com/en/blog/introducing-corelibs.html
[TSUrlFilter]: https://github.com/AdguardTeam/tsurlfilter/tree/master/packages/tsurlfilter#tsurlfilter
+[с TSUrlFilter]: https://github.com/AdguardTeam/tsurlfilter/tree/master/packages/tsurlfilter#tsurlfilter
[в TSUrlFilter]: https://github.com/AdguardTeam/tsurlfilter/tree/master/packages/tsurlfilter#tsurlfilter
[TSWebExtension]: https://github.com/AdguardTeam/tsurlfilter/tree/master/packages/tswebextension#tswebextension
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index b3644a63ce9..2484d799073 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ sidebar_position: 6
- Базовый фильтр AdGuard
- Фильтр мобильной рекламы AdGuard
- Региональные фильтры, разделённые по языковому принципу — китайский, голландский, французский, немецкий, японский, русский, испанский/португальский, турецкий и украинский
-- Фильтр быстрых исправлений
### Назначение этих фильтров
- **Базовый фильтр** предназначен для блокировки рекламы на англоязычных сайтах и тех сайтах, для которых нет отдельного фильтра. Он также содержит общие правила фильтрации, которые применяются ко всем сайтам независимо от языка
- **Фильтр мобильной рекламы** блокирует рекламу на мобильных версиях сайтов и в мобильных приложениях. Разделения по языкам нет
- **Региональные фильтры** следуют той же политике, что и **Базовый фильтр**, но ограничены сайтами на определённых языках
-- **Фильтр быстрых исправлений** используется для быстрого устранения критических проблем фильтрации контента на популярных сайтах без обновления MV3-расширения.
Цель этих фильтров — блокировать все виды рекламы на сайтах, в приложениях и на некоторых устройствах, которые могут загружать рекламу из интернета:
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 68db37af985..ae7977af510 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 68db37af985..ae7977af510 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index d10f3e8722a..e8bf65a8bb2 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -21,19 +21,19 @@ The old beta extension will be renamed to [**AdGuard Ad Blocker MV2**](https://c
- **Filtering log**
- 
+ 
- Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
+ Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
- _Tracking protection_ (formerly known as _Stealth mode_)
- 
+ 
- There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
+ There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
- _Phishing & malware protection_ is no longer available in the general settings. To protect yourself from malicious websites and scams, enable the appropriate _Security_ filters in the _Filters_ tab.
- 
+ 
## Limitations
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index b1adcc3ff6a..ae7977af510 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/sv/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 68db37af985..ae7977af510 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/ta/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 2238c7a1e39..de926687aed 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-Bu limit aşılırsa, yalnızca **5,000 dönüştürülmüş kural** aşağıdaki sırayla uygulanacaktır: önce İzin listesi, ardından Kullanıcı kuralları, Özel filtreler ve nihayet — Hızlı Çözümler filtresi.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index 7dc7a6cfcfb..abbb1c489e3 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**HTTP/3 Hakkında**: Bu, QUIC tabanlı HTTP protokolünün en son sürümüdür.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Giden proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 01da63c7c12..a20fb64cb75 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- 14 günlük deneme sürenizi etkinleştirmek için kaydolun. Etkinleştirme kodu farklı cihazlarda ve platformlarda kullanılabilir
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Destek
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index e288b75ed4e..7ab6d971f9f 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ Done, AdGuard for Android TV is installed.
- In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- Wait for a message in the terminal indicating the successful installation of the app.
+
+## Android TV için AdGuard'ı atvTools aracılığıyla yükleme
+
+**Önemli:** Akıllı telefonunuz ve Android TV (TV kutusu) yüklü televizyonunuz aynı yerel ağda olmalıdır.
+
+1. Android akıllı telefonunuza [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) uygulamasını yükleyin
+
+2. **atvTools'u** **Android TV'ye** bağlayın
+
+ 1. Android TV cihazınızda geliştirici modunu etkinleştirin
+
+ `Ayarlar` → `Cihaz ayarları` → `Cihaz hakkında` → Geliştirici durumunu başarıyla aldığınızı onaylayan bir mesaj görene kadar `Android TV yapısı` öğesine dokunun
+
+ 2. Android TV cihazınızda USB hata ayıklamayı etkinleştirin
+
+ `Ayarlar` → `Cihaz ayarları` → `Geliştiriciler için` → `Hata ayıklama` öğesine gidin, `USB hata ayıklama` öğesine izin verin ve etkinleştirin
+
+3. Akıllı telefonunuzda **atvTools'u** başlatın
+
+4. Listeden istediğiniz **Android TV** cihazını bulun ve tıklayın
+
+5. TV'de bağlantıya izin verin
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index 5f66bb2a3d4..bca6af8f56a 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 1597f1de15d..74c749c9577 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ Bu makale, cihazınızı sistem düzeyinde koruyan çok işlevli bir reklam enge
Windows için AdGuard can sıkıcı afişleri, açılır pencereleri, video reklamları ve izleyicileri engelleyen, kullanımı kolay bir araçtır. Ancak hepsi bu kadar değil: veri tasarrufu yapmanıza, web sayfalarını daha hızlı yüklemenize, bilgisayarınızı istenmeyen ve potansiyel olarak kötü amaçlı sitelerden korumanıza yardımcı olur. AdGuard ayrıca sizi kimlik avı sitelerinden korur ve çocuklarınızı uygunsuz içerikten uzak tutar.
-
+
Windows için AdGuard'ı başlattığınızda, uygulamanın ana ekranını göreceksiniz. Its most noticeable detail is the _enable/disable protection_ button. Ayrıca bu ekranda engellenen reklamları, izleyicileri ve tehdit istatistiklerini izleyebilir, uygulamanın güncel sürümünü öğrenebilir veya güncelleyebilirsiniz. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Bunların her biri hakkında ayrı ayrı konuşmaya değer.
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index b70035f4baf..b607f53bed5 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ Bu makale, cihazınızı sistem düzeyinde koruyan çok işlevli bir reklam enge
_Ayarlar_ en fazla dikkat gerektiren bölümdür. Burası, uygulamayı gereksinimlerinizi tam olarak karşılayacak şekilde yapılandırabileceğiniz yerdir: yalnızca sizi rahatsız edenleri engeller, güvenilir sağlayıcının DNS sunucusunu kullanır, üçüncü taraf tanımlama bilgilerini kaldırır, vb.
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### Genel ayarlar
+
-Burada dili ve temayı (Koyu veya Açık) ayarlayabilir, AdGuard'ın sistem başlangıcında başlatılmasını ve sessiz otomatik güncellemeleri etkinleştirebilir, güncelleme kanalını ve filtre güncelleme denetimi aralığını seçebilirsiniz. Ayrıca Ayarlar, Windows için AdGuard düzgün çalışmıyorsa ve destek ekibi sizden [_Hata ayıklama günlüklerini_ toplamanızı](/adguard-for-windows/solving-problems/adguard-logs.md) istediyse gidilecek yerdir.
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-Ekranın en altında _Gelişmiş Ayarlar_ öğesini bulacaksınız. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Ad blocking
Bu, ziyaret ettiğiniz sitelerden ve cihazınızda yüklü uygulamalardan reklamları kaldıran Windows için AdGuard'ın ana modülüdür. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-Gizlilik Modun çalışmasını esnek bir şekilde ayarlayabilirsiniz: örneğin, sitenin internette bulmak için kullandığınız arama isteğini almasını yasaklayabilir, hem üçüncü taraf hem de sitenin kendi çerezlerini otomatik olarak silebilir ve tarayıcınızda nerede olduğunuzu izlemek için kullanılabilecek konum paylaşımını devre dışı bırakabilirsiniz.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Gezinti koruması
@@ -81,15 +81,15 @@ v7.20 sürümünden itibaren, önceden oluşturulmuş güvenilir filtreler liste

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Tarayıcı Asistanı
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 65e3dba0a17..aa79aea0075 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ AdGuard'ın filtre aboneliği URL'lerini (ör. `abp:subscribe` ve benzeri) otoma
Bu ayar etkinleştirilirse, AdGuard diğer istek türlerinin yanı sıra HTTP/3 üzerinden gönderilen istekleri de filtreler.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Yönlendirme sürücü modunu kullan
Bu seçenek etkinleştirilirse AdGuard tüm trafiği keser ve daha fazla filtreleme için yerel proxy sunucusuna yönlendirir.
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index bfee38b114e..9da13156293 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -40,8 +40,7 @@ Bu sayfada bu filtre hakkında daha fazla bilgi edinin. [Kuralları görüntüle
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Bilinen tüm mobil reklam ağlarını içerir. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
-- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Hızlı Çözümler filtresi** — MV3 uzantısını güncellemeden popüler sitelerdeki kritik içerik filtreleme sorunlarını hızlı bir şekilde çözmek için kullanılır. [Kuralları görüntüle](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
+- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 220aca502ae..1be5d6a4454 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Örnekler**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::dikkat Kısıtlamalar
-Değiştirici değerindeki uygulamaların joker karakteri olamaz, örneğin `$app=com.*.music`. Bu tür değiştiriciye sahip kurallar geçersiz kabul edilir.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Değiştirici değerindeki uygulamaların joker karakteri olamaz, örneğin `$ap
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 VE ((2 VE 3) VEYA 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Örnekler**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -568,7 +581,7 @@ In the following examples it is implied that requests are sent from `http://exam
In [AdGuard for Chrome MV3][ext-mv3], `regexp` and `any_tld_domain` entries are not supported.
-AdGuard for iOS and AdGuard for Safari support the `$domain` modifier but have some limitations. Daha fazla ayrıntı için [SafariConverterLib bölümüne](#safari-converter--basic--supported-with-limitations) bakın.
+AdGuard for iOS and AdGuard for Safari support the `$domain` modifier but have some limitations. For more details, see the [SafariConverterLib section](#safari-converter--basic--supported-with-limitations).
Rules with `regexp` in the `$domain` modifier are not supported by AdGuard for Safari and AdGuard for iOS.
@@ -640,9 +653,9 @@ Go to [rules priorities](#rule-priorities) for more details.
```
```adblock
-! istisna kuralı aynı zamanda `$important` değiştiricisi varsa, bu kural geçerli olur ve istekler engellenmeyecektir
+! if the exception rule also has `$important` modifier, it will prevail and requests won't be blocked
||example.org^$important
-@@|example.org^$important
+@@||example.org^$important
```
#### **`$match-case`** {#match-case-modifier}
@@ -699,7 +712,7 @@ AdGuard will try to close the browser tab with any address that matches a blocki
1. The `$popup` modifier works best in AdGuard Browser Extension for Chromium-based browsers and Firefox.
1. In [AdGuard for Chrome MV3][ext-mv3] rules with the [`$popup`][popup-in-mv3] modifier would not work, so we disable converting them to declarative rules. We will try to use them only in our [TSUrlFilter][] engine and close new tabs programmatically.
1. In AdGuard for iOS and AdGuard for Safari, `$popup` rules simply block the page right away.
-1. In AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux, the `$popup` modifier may not detect a popup in some cases and it will not be blocked. The `$popup` modifier applies the `document` content type with a special flag which is passed to a blocking page. Sayfanın kendisinin engellenmesi bazı kontroller yapabilir ve eğer gerçekten bir açılır pencere ise pencereyi kapatabilir. Aksi takdirde, sayfa yüklenmelidir. It can be combined with other request type modifiers, such as `$third-party`, `$strict-third-party`, `$strict-first-party`, and `$important`.
+1. In AdGuard for Windows, AdGuard for Mac, AdGuard for Android, and AdGuard for Linux, the `$popup` modifier may not detect a popup in some cases and it will not be blocked. The `$popup` modifier applies the `document` content type with a special flag which is passed to a blocking page. Blocking page itself can do some checks and close the window if it is really a popup. Otherwise, page should be loaded. It can be combined with other request type modifiers, such as `$third-party`, `$strict-third-party`, `$strict-first-party`, and `$important`.
:::
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
@@ -2240,8 +2253,8 @@ Firefox ignores the `Permissions-Policy` header. For more information, see [this
:::dikkat Kısıtlamalar
-1. `$permissions` değerinde yasak olan karakterler: `$`.
-2. `$permissions` sınırlı sayıda değiştiriciyle uyumludur: `$domain`, `$important`, `$subdocument` ve [içerik türü değiştiricileri](#content-type-modifiers).
+1. Characters forbidden in the `$permissions` value: `$`.
+2. `$permissions` is compatible with a limited set of modifiers: `$domain`, `$important`, `$subdocument`, and [content-type modifiers](#content-type-modifiers).
3. `$permissions` rules that do not have any [content-type modifiers](#content-type-modifiers) will match only requests where content type is `document`.
:::
@@ -3532,7 +3545,7 @@ the element `div#match` can be selected by any of these extended selectors:
! plain text
div:contains(banner)
-! düzenli ifade
+! regular expression
div:contains(/as .*banner/)
! regular expression with flags
@@ -4025,7 +4038,7 @@ In most cases, the basis and cosmetic rules are enough to filter ads. But someti
HTML filtering rules are supported by AdGuard for Windows, AdGuard for Mac, AdGuard for Android, AdGuard for Linux, and AdGuard Browser Extension for Firefox. Such rules do not work in extensions for other browsers because they are unable to modify content on network level.
-The syntax with an optional `value` in the attributes is supported by AdGuard for Windows, AdGuard for Mac, and AdGuard for Android with CoreLibs v1.18 or later. It is also supported by AdGuard Browser Extension v5.2 or later. For the other products and previous versions `value` must **always** be specified. Aksi takdirde, kural yanlış olarak değerlendirilir ve yok sayılır.
+The syntax with an optional `value` in the attributes is supported by AdGuard for Windows, AdGuard for Mac, and AdGuard for Android with CoreLibs v1.18 or later. It is also supported by AdGuard Browser Extension v5.2 or later. For the other products and previous versions `value` must **always** be specified. Otherwise, the rule will be treated as incorrect and ignored.
:::
@@ -4075,7 +4088,7 @@ If the value of the attribute is omitted in the rule, then the element will be r
example.org$$div[some_attribute]
```
-This rule removes all `div` elements with the attribute `some_attribute` on `example.org` and all its subdomains. Yani yukarıdaki örnekteki `div` elemanlarının ikisi de kaldırılacaktır.
+This rule removes all `div` elements with the attribute `some_attribute` on `example.org` and all its subdomains. So, the both `div` elements from the example above will be removed.
### Special attributes
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 46c418da849..77b00d20a51 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard reklam engelleme filtreleri şunları içerir:
- AdGuard Temel filtresi
- AdGuard Mobil Reklam filtresi
- Dil ilkesine göre ayrılmış bölgesel filtreler — Çince, Felemenkçe, Fransızca, Almanca, Japonca, Rusça, İspanyolca/Portekizce, Türkçe ve Ukraynaca
-- AdGuard Hızlı Çözümler filtresi
### Bu filtrelerin amacı
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. Ayrıca, dilden bağımsız olarak tüm siteler için geçerli olan genel filtreleme kuralları da içerir
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. Dile dayalı bir sınıflandırma yoktur
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Hızlı Çözümler filtresi**, MV3 uzantısını güncellemeden popüler sitelerdeki kritik içerik filtreleme sorunlarını hızlı bir şekilde çözmek için kullanılır.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index d10f3e8722a..e8bf65a8bb2 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -21,19 +21,19 @@ The old beta extension will be renamed to [**AdGuard Ad Blocker MV2**](https://c
- **Filtering log**
- 
+ 
- Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
+ Due to DNR restrictions, we can’t show exactly which rule worked, but we will provide an “assumed rule that was triggered” based on our engine. For precise information, you’ll need to install the “unpacked” form of the extension in your browser yourself. You’ll find detailed instructions on how to do this in a [separate article](/adguard-browser-extension/solving-problems/debug-rules/).
- _Tracking protection_ (formerly known as _Stealth mode_)
- 
+ 
- There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
+ There are no _Cookies_ section, along with _Self-destruction of first-party cookies_ and _Self-destruction of third-party cookies_ since we cannot set the TTL of cookies using declarative rules.
- _Phishing & malware protection_ is no longer available in the general settings. To protect yourself from malicious websites and scams, enable the appropriate _Security_ filters in the _Filters_ tab.
- 
+ 
## Limitations
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index b1adcc3ff6a..ae7977af510 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/uk/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 29883b220fb..1c54d6ea766 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## Support
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 68db37af985..ae7977af510 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet:
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 174f45bba6d..769988a50d5 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ Manifest V3 对每个扩展的静态规则和正则表达式规则施加限制
**动态规则**:严格限制 **5,000** 个规则,其中包括最多 1,000 个正则表达式规则。
-如果超出此限制,则仅会按以下顺序应用 **5,000 个转换后的规则**:首先是白名单,然后是用户规则,自定义过滤器,最后是快速修复的过滤器。
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **转换后的规则**是使用[声明性转换器][github-declarative-converter]转换为 \[DNR 格式]的规则。
> 在转换过程中,一些规则会覆盖其他规则(`$badfilter`),一些规则会合并(`$removeparam`),从而导致规则列表的顺序略有不同。
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index 69a1e7105e4..71c121d30e6 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -137,6 +137,12 @@ For AdGuard for Android v4.x we’ve completely redesigned the low-level setting
**关于 HTTP/3**:这是基于 QUIC 的 HTTP 协议的最新版本。
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### 出站代理
#### 显示「过滤 DNS 请求」设置
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index 21f176f3edd..6084ae94b06 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## 支持
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index 601304a7b1d..5a86e027653 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -58,3 +58,31 @@ sidebar_position: 15
- 在终端中,输入命令 `adb install Downloads/adguard_tv.apk`。 如有必要,请将 `Downloads/adguard_tv.apk` 替换为您的路径。
- 等待终端中出现指示应用程序安装成功的消息。
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index cfaeb27c08a..21cb20c43fc 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ sidebar_position: 9
如果设置为 `true`,允许 AdGuard 过滤通过 HTTP/3 发送的流量,HTTP/3 是基于 QUIC 的 HTTP 协议的最新版本。
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
设置为 `true` 即可启用本地网络过滤。
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 24ec066a90d..ace7495e416 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ sidebar_position: 1
Windows 版 AdGuard 是一款易于使用的可拦截烦人横幅,弹窗,视频广告和跟踪器的工具。 但这还不是全部:它可帮助用户节省流量、更快地加载网页,并保护计算机免受不良网站和潜在恶意网站的侵害。 AdGuard 还可以保护用户免受网络钓鱼网站的侵害,并让孩子远离不当内容。
-
+
启动 Windows 版 AdGuard 后可以看到主页。 主页上最引人注目的细节是「启用/禁用保护」按钮。 此外,用户可以在主页上看到关于拦截的广告,跟踪器和威胁的统计数据,查看程序版本或更新。 此外,右上角有四个标签,包括「设置」、「支持」、「许可证」和「关于」。 它们都值得单独讨论。
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 54770ea0ef0..55e84794c89 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ sidebar_position: 2
「设置」是最需要关注的部分。 用户可以在此处配置本应用以完全符合您的需求:仅拦截困扰您的广告,使用受信任提供商的 DNS 服务器,移除第三方 Cookie 等等。
-
+### General settings
+
+Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-### 常规设置
+
-用户可以在此处设置语言和主题(暗色或亮色),开启 AdGuard 随系统启动运行,静寂自动更新,选择更新通道和过滤器更新检查时间间隔。 如果 Windows 版 AdGuard 无法正常工作,而支持团队要求用户[收集「调试日志」](/adguard-for-windows/solving-problems/adguard-logs.md),那么「设置」也是要查看的地方。
+At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).

-在屏幕的最底部,可以找到「高级设置」。 Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
-
### Ad blocking
此为 Windows 版 AdGuard 的主模块,可从用户访问的网站上和设备上安装的应用内移除广告。 要过来广告和威胁隐私的内容,如横幅,弹窗或跟踪器,AdGuard 使用不同的过滤器:用[特定语法](/general/ad-filtering/create-own-filters)编写的有类似用途的规则组。 要了解什么是过滤器及其工作原理,请阅读[本文](/general/ad-filtering/how-ad-blocking-works)。
@@ -46,9 +46,9 @@ In the Ad blocking module you can:

-用户可以灵活调整隐身模式的工作方式:例如,可以阻止网站接收您在因特网查找它时所用的搜索请求,自动删除第三方和网站自身的 Cookie,禁用可用于跟踪用户行踪的位置共享。
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-要了解关于隐身模式及其选项的更多信息,请阅读[此文章](/general/stealth-mode)。
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### 浏览安全
@@ -81,15 +81,15 @@ In the Ad blocking module you can:

-### 家长控制
+### Parental control
-有一些网站不适合儿童访问,建议在儿童使用的电脑上对其进行访问限制。 This task is accomplished by _Parental Control_.
+有一些网站不适合儿童访问,建议在儿童使用的电脑上对其进行访问限制。 This task is accomplished by _Parental control_.
-
+
-此模块检查浏览器打开的网页内容,过滤儿童不宜的内容:成人图像和文字、粗俗语言、暴力、毒品宣传等。 家长控制设置受密码保护,孩子无法绕过限制。 此模块不仅拦截对不良网站的指向,也可从搜索结果中移除儿童不宜的链接。
+此模块检查浏览器打开的网页内容,过滤儿童不宜的内容:成人图像和文字、粗俗语言、暴力、毒品宣传等。 Parental control settings are password-protected so that the child is not able to go round the restrictions. 此模块不仅拦截对不良网站的指向,也可从搜索结果中移除儿童不宜的链接。
-在「家长控制」模块,用户可以开启「安全搜索」,管理「黑名单」和「白名单」以自定义此选项的工作方式。 用户也可以选中「阻止下载可执行文件」以防止儿童在计算机上下载和安装软件。 「家长控制」模块有多个选项:用户可以选择「家长控制」保护特定的 Windows 用户,设置密码保护 AdGuard 设置以防更改。
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. 用户也可以选中「阻止下载可执行文件」以防止儿童在计算机上下载和安装软件。 There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### 浏览器助手
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 9da3cbd7202..4f5b5aa74ab 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ sidebar_position: 7
如果启用此设置,AdGuard 除过滤其他请求类型外,还会过滤通过 HTTP/3 发送的请求。
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### 使用重定向驱动模式
如果启用该选项,AdGuard 将拦截所有流量,并将其重定向到本地代理服务器进行进一步过滤。
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 5402281f883..9ba6511e9f7 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ sidebar_position: 2
- **实验性过滤器**,此过滤器设计用于在将某些有风险的过滤规则添加到基本过滤器之前对其进行测试。 如果这些规则执行没有任何问题,它们会被添加到主过滤器中。 [查看规则](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **移动广告过滤器**拦截移动设备上的广告。 包含所有已知的移动广告网络。 [查看规则](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS 过滤器** — 此过滤器由其他几个过滤器 (AdGuard 基础过滤器、社交媒体过滤器、防跟踪保护过滤器、移动广告过滤器、EasyList 和 EasyPrivacy) 组成,并经过简化,以便更好地与 DNS 级别的广告拦截兼容。 [AdGuard DNS](https://adguard-dns.io/kb) 服务器使用此过滤器来拦截广告和跟踪器。 [查看规则](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **快速修复的 AdGuard 过滤器**,无需更新 MV3 扩展即可快速解决网站过滤问题。 [查看规则](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard 过滤器政策
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index fc2c0e440ce..ba6883d002c 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8a55d5808c5..b8c9fc1881e 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard 广告拦截的过滤器包含以下过滤器:
- AdGuard 基础过滤器
- AdGuard 移动广告过滤器
- 按语言原则划分的地区过滤器,包括中文、荷兰语、法语、德语、日语、俄语、西班牙语/葡萄牙语、土耳其语和乌克兰语
-- 快速修复的 AdGuard 过滤器
### 过滤器的用途
- **基础过滤器**旨在拦截英语网站和没有单独过滤器的网站上的广告。 它还包含适用于所有网站(无论网站的语言)的一般过滤规则。
- **移动广告过滤器**拦截移动版网站和移动应用程序中的广告。 没有基于语言的细分。
- **地区过滤器**遵循与**基础过滤器**相同的政策,但仅限于特定语言的网站。
-- **快速修复的 AdGuard 过滤器**,无需更新 MV3 扩展即可快速解决网站过滤问题。
广告拦截过滤器的主要目标在于拦截网站、应用程序和某些可以从互联网上加载广告的设备上的所有类型广告。广告类型如下:
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
index 1c49edaf3a6..e8bf65a8bb2 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-browser-extension/mv3-version.md
@@ -55,7 +55,7 @@ The maximum number of simultaneously enabled filters is **50**.
**Dynamic rules:** a strict cap of **5,000** rules is imposed, which includes a maximum of 1,000 regex rules.
-If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules, Custom filters, and finally — Quick Fixes filter.
+If this limit is exceeded, only **5,000 converted rules** will be applied in the following order: first Allowlist, then User rules and finally Custom filters.
> **Converted rules** are rules that have been transformed
> to [DNR format] using the [declarative converter][github-declarative-converter].
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
index b2b239a214d..b658f10df14 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/features/low-level-settings.md
@@ -138,6 +138,12 @@ If this setting is enabled, AdGuard will filter requests sent over HTTP/3 in add
**About HTTP/3**: This is the latest version of the HTTP protocol, based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Outbound proxy
#### Show the Filter DNS requests setting
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
index e339b666856..b08a8421cf6 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/features/settings.md
@@ -145,13 +145,13 @@ Please note that DNS filtering will still be active in _Automatic proxy_ routing
In this section, you can find information about your license and manage it:
- Buy an AdGuard license to activate [the full version's features](/adguard-for-android/features/free-vs-full)
-- Log in to your AdGuard account or enter the license key to activate your license
-- Sign up to activate your 7-day trial period if you haven't used it yet
+- Log in to your AdGuard account or enter the activation code to activate your license
+- Sign up to activate your 14-day trial period. The activation code can be used on different devices and platforms
- Refresh the license status from the three-dots menu (⋮)
- Open the AdGuard account to manage your license there
- Reset your license — for example, if you've reached device limit for this license and want to apply another one
-
+
## 支援
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
index b5525cd735c..3df7d66e56c 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-android/solving-problems/adguard-for-android-tv.md
@@ -43,18 +43,46 @@ Done, AdGuard for Android TV is installed.
4. Write down the IP address of your Android TV:
- - On your Android TV, navigate to Settings.
- - Select _System_ → _About_.
- - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
- - Go to the network section and find _IP address_. Note down this IP address.
+ - On your Android TV, navigate to Settings.
+ - Select _System_ → _About_.
+ - Find _Network_ and select _Wi-Fi_ or _Ethernet_, depending on your connection type.
+ - Go to the network section and find _IP address_. Note down this IP address.
5. Connect to Android TV via ADB:
- - Open the terminal or command prompt on your computer.
- - Enter the command `adb connect` and paste the IP address of your TV.
- - The connection will be established.
+ - Open the terminal or command prompt on your computer.
+ - Enter the command `adb connect` and paste the IP address of your TV.
+ - The connection will be established.
6. Install AdGuard for Android TV via ADB:
- - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
- - Wait for a message in the terminal indicating the successful installation of the app.
+ - In the terminal, enter the command `adb install Downloads/adguard_tv.apk`. If necessary, replace `Downloads/adguard_tv.apk` with your path.
+ - Wait for a message in the terminal indicating the successful installation of the app.
+
+## Installing AdGuard for Android TV via atvTools
+
+**Important:** Your smartphone and TV with Android TV (TV box) must be on the same local network.
+
+1. Install the [atvTools](https://play.google.com/store/apps/details?id=dev.vodik7.atvtools) app on your Android smartphone
+
+2. Connect **atvTools** to **Android TV**
+
+ 1. Enable developer mode on your Android TV device
+
+ `Settings` → `Device settings` → `About device` → Tap `Android TV build` until you see a message confirming that you have successfully obtained developer status
+
+ 2. Enable USB debugging on your Android TV device
+
+ Go to `Settings` → `Device settings` → `For developers` → `Debugging`, allow and enable `USB debugging`
+
+3. Launch **atvTools** on your smartphone
+
+4. Find the desired **Android TV** device in the list and click it
+
+5. Allow the connection on the TV
+
+6. Download the [AdGuard for Android TV](https://agrd.io/tvapk) installer to your smartphone as an **APK** file
+
+7. In **atvTools**, click **Install** on the main screen and wait (less than a minute) until the **AdGuard for Android TV** icon appears in the list of applications
+
+
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
index dab74463df3..bf1d4170ce3 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-mac/solving-problems/advanced-settings.md
@@ -81,6 +81,12 @@ Verifies the authenticity of all certificates for the domain based on Chrome Cer
By setting `true`, you allow AdGuard to filter traffic sent over HTTP/3, the latest version of the HTTP protocol based on QUIC.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
#### `network.filtering.localnetwork`
By setting `true`, you enable local network filtering.
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
index 68db37af985..ae7977af510 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/features/home-screen.md
@@ -11,6 +11,6 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
AdGuard for Windows is an easy-to-use tool that blocks annoying banners, popups, video ads, and trackers. But that's not all: it helps you save traffic, load web pages faster, and protect your computer from undesirable and potentially malicious websites. AdGuard also protects you from phishing websites and keeps your kids away from inappropriate content.
-
+
Once you start AdGuard for Windows, you will see the main screen of the app. Its most noticeable detail is the _enable/disable protection_ button. Also, on this screen you can monitor blocked ads, trackers and threats statistics, find out the current version of the app or update it. Furthermore, there are four tabs in the upper right corner: _Settings_, _Support_, _License_, and _About_. Each of these is worth talking about separately.
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
index 06699bfae4a..7fb00d05272 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/features/settings.md
@@ -11,16 +11,16 @@ This article covers AdGuard for Windows, a multifunctional ad blocker that prote
_Settings_ is the section that requires the most attention. This is where you can configure the app so that it fully meets your requirements: blocks only what bothers you, uses the DNS server of the trusted provider, removes third-party cookies, and so on.
-
-
### General settings
Here you can set the language and theme (Dark or Light), enable AdGuard launching at system start-up and silent automatic updates, choose the update channel and filter update check interval. Also Settings is the place to go if AdGuard for Windows is not working properly and the support team asked you to [collect _Debug logs_](/adguard-for-windows/solving-problems/adguard-logs.md).
-
+
At the very bottom of the screen you will find _Advanced Settings_. Changing some of them mindlessly may potentially cause problems with AdGuard’s performance, break the Internet connection or compromise your security and privacy. That’s why we suggest you open this section only if you are sure of what you are doing or our support team has asked you about it. If you want to know what can be set up in _Advanced Settings_, read the [dedicated article](/adguard-for-windows/solving-problems/low-level-settings.md).
+
+
### Ad blocking
This is the main module of AdGuard for Windows that removes ads from the websites you visit and from the apps installed on your device. To filter out advertising and privacy-threatening content such as banners, popups, or trackers AdGuard uses different filters — groups of rules with a similar purpose written with a [special syntax](/general/ad-filtering/create-own-filters). To understand what filters are and how they work read [this article](/general/ad-filtering/how-ad-blocking-works).
@@ -46,9 +46,9 @@ Many websites gather information about their visitors, such as their IP addresse

-You can flexibly adjust the work of Stealth Mode: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
+You can flexibly adjust the work of _Tracking protection_: for instance, you can prohibit the website to receive the search request you used to find it on the Internet, automatically delete both third-party and website’s own cookies, and disable location sharing in your browser that can be used to track your whereabouts.
-To learn everything about Stealth Mode and its many options, [read this article](/general/stealth-mode).
+To learn everything about _Tracking protection_ and its many options, [read this article](/general/stealth-mode).
### Browsing security
@@ -81,15 +81,15 @@ Starting with v7.20, you can also add filters by simply selecting them from a li

-### Parental Control
+### Parental control
-There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental Control_.
+There are several websites to which access should be restricted from a PC used by children. This task is accomplished by _Parental control_.
-
+
-The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental Control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
+The module checks the contents of web pages opened in the browser and filters those with content undesirable for children: images and texts for adults, crude language, violence, drug propaganda, etc. Parental control settings are password-protected so that the child is not able to go round the restrictions. This module not only blocks directions to undesirable sites but can also delete the links that are inappropriate for children from the search results.
-In the _Parental Control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental Control_ module: you can select a specific Windows user to be protected by _Parental Control_ and set a password to protect AdGuard settings from change.
+In the _Parental control_ module you can enable the _Safe search_ and manage the _blocklist_ and the _allowlist_ to customize how this option works. You can also check the _Block executable files download_ box to prevent your child from downloading and installing software on the computer. There are two more options in the _Parental control_ module: you can select a specific Windows user to be protected by _Parental control_ and set a password to protect AdGuard settings from change.
### Browser Assistant
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
index 1641d89befe..2d9c4320c1a 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-for-windows/solving-problems/low-level-settings.md
@@ -65,6 +65,12 @@ Enable this feature if you want AdGuard to automatically intercept filter subscr
If this option is enabled, AdGuard will filter requests sent over HTTP/3 in addition to other request types.
+**Limitations**:
+
+- Chrome-based browsers do not accept user certificates, so HTTP/3 filtering is not supported in them.
+- Firefox-based browsers behave similarly by default, but you can set the `network.http.http3.disable_when_third_party_roots_found` option in `about:config` to `false` to allow user certificates for HTTP/3.
+- Safari supports HTTP/3 filtering without additional configuration.
+
### Use redirect driver mode
If this option is enabled, AdGuard intercepts all the traffic and redirects it to the local proxy server for further filtering.
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
index 22553b8a979..56d3fb5eed8 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/adguard-filters.md
@@ -38,7 +38,6 @@ This article is about the filters we create to use in AdGuard and other ad-block
- **Experimental filter** serves to test some new filtering rules that can potentially cause conflicts and mess with websites' work. In case these rules perform without any issues, they get added to main filters. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_5_Experimental/filter.txt)
- **Mobile ads filter** blocks ads on mobile devices. Contains all known mobile ad networks. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_11_Mobile/filter.txt)
- **DNS filter** — composed of several other filters (AdGuard Base filter, Social media filter, Spyware filter, Mobile ads filter, EasyList and EasyPrivacy) and simplified specifically to be better compatible with DNS-level ad blocking. This filter is used by [AdGuard DNS](https://adguard-dns.io/kb) servers to block ads and tracking. [View rules](https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_15_DnsFilter/filter.txt)
-- **Quick Fixes filter** — used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension. [View rules](https://filters.adtidy.org/extension/chromium-mv3/filters/24.txt)
## AdGuard Filters Policy
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
index 641e9df9360..f571dc8cdb6 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/create-own-filters.md
@@ -419,6 +419,19 @@ This modifier lets you narrow the rule coverage down to a specific application (
For Mac, you can find out the bundle ID or the process name of the app by viewing the respective request details in the Filtering log.
+**Syntax**
+
+The modifier is a list of one or more expressions, each of which is matched against an application in a particular way depending on its type. These expressions are separated by the `|` symbol.
+
+```text
+applications = ["~"] entry_0 ["|" ["~"] entry_1 ["|" ["~"]entry_2 ["|" ... ["|" ["~"]entry_N]]]]
+entry_i = ( regular_app / wildcard_app / regexp )
+```
+
+- **`regular_app`** — a regular application name (`example.app`). It corresponds to the specified application and is matched lexicographically.
+- **`wildcard_app`** — an application name ending with a wildcard character `*`, such as `org.example.*` or `com.ad*`. It matches all applications whose names start with the specified prefix. Matching is done lexicographically.
+- **`regexp`** — a regular expression that starts and ends with `/`. It works the same way as the basic URL rules, but the characters `/`, `$`, `,`, and `|` must be escaped with `\`.
+
**Examples**
- `||baddomain.com^$app=org.example.app` — a rule to block requests that match the specified mask and are sent from the `org.example.app` Android app.
@@ -429,9 +442,23 @@ If you want the rule not to be applied to certain apps, start the app name with
- `||baddomain.com^$app=~org.example.app` — a rule to block requests that match the specified mask and are sent from any app except for the `org.example.app`.
- `||baddomain.com^$app=~org.example.app1|~org.example.app2` — same as above, but now two apps are excluded: `org.example.app1` and `org.example.app2`.
+You can use wildcards in the `$app` modifier:
+
+- `||baddomain.com^$app=org.example.*` — applies to all apps whose package names start with `org.example.`
+
+You can use regular expressions in the `$app` modifier by enclosing them in forward slashes `/.../`. This allows for more flexible matching — for example, targeting a group of apps from the same publisher or matching complex patterns.
+
+- `||baddomain.com^$app=/org\.example\.[a-z0-9_]+/` — applies to all apps whose package name starts with `org.example` (e.g. `org.example.app1`, `org.example.utility`, etc.).
+- `||baddomain.com^$app=/^org\.example\.app\$\|^org\.example\.[ab].*/` — applies to `org.example.app` and to any app whose package starts with `org.example.a` or `org.example.b`.
+
+The `$app` modifier supports combining all three types of entries — plain names, wildcards, and regular expressions — within the same rule, but it does not allow combining negated and non-negated expressions together.
+
+- `||example.com^$app=org.example.app|org.example.*|/org\.example\.[a-z]+/` — applies to `org.example.app`, all matching `org.example.*` and `org.example.[a-z]+` apps.
+
:::caution Restrictions
-Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rules with such modifier are considered invalid.
+- Apps in the modifier value cannot include a wildcard inside the string , e.g. `$app=com.*.music`. Use a regular expression instead: `$app=/com\..*\.music/`.
+- You cannot combine negated (`~`) and non-negated expressions in the same `$app` modifier — this would be ambiguous.
:::
@@ -439,6 +466,7 @@ Apps in the modifier value cannot have a wildcard, e.g. `$app=com.*.music`. Rule
- Only AdGuard for Windows, Mac, Android are technically capable of using rules with `$app` modifier.
- On Windows the process name is case-insensitive starting with AdGuard for Windows with [CoreLibs][] v1.12 or later.
+- Support for regular expressions and for combining different types of entries (plain names, wildcards, and regular expressions) in the `$app` modifier is available starting from CoreLibs v1.19 or later.
:::
@@ -529,38 +557,23 @@ If you want the rule not to be applied to certain domains, start a domain name w
**`$domain` modifier matching target domain:**
-In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain. This happens when all the following conditions are met:
-
-1. The request has the `document` content type
-1. The rule pattern does not match any particular domains
-1. The rule pattern does not contain regular expressions
-1. The `$domain` modifier contains only excluded domains, e.g. `$domain=~example.org|~example.com`
-
-The following predicate should be satisfied to perform a target domain matching:
-
-```text
-1 AND ((2 AND 3) OR 4)
-```
-
-That is, if the modifier `$domain` contains only excluded domains, then the rule does not need to meet the second and third conditions to match the target domain against the modifier `$domain`.
+In some cases the `$domain` modifier can match not only the referrer domain, but also the target domain.
-If some of the conditions above are not met but the rule contains [`$cookie`](#cookie-modifier) or [`$csp`](#csp-modifier) modifier, the target domain will still be matched.
+This happens when the rule has one of the following modifiers: [`$cookie`](#cookie-modifier), [`$csp`](#csp-modifier), [`$permissions`](#permissions-modifier), [`$removeparam`](#removeparam-modifier).
-If the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, then the rule will not be applied even if the target domain also matches the rule. This affects rules with [`$cookie`](#cookie-modifier) and [`$csp`](#csp-modifier) modifiers, too.
+These modifiers will not be applied if the referrer matches a rule with `$domain` that explicitly excludes the referrer domain, even if the target domain also matches the rule.
**Examples**
- `*$cookie,domain=example.org|example.com` will block cookies for all requests to and from `example.org` and `example.com`.
-- `*$document,domain=example.org|example.com` will block all requests to and from `example.org` and `example.com`.
+- `*$document,domain=example.org|example.com` will block requests only from `example.org` and `example.com`, but not to them.
In the following examples it is implied that requests are sent from `http://example.org/page` (the referrer) and the target URL is `http://targetdomain.com/page`.
- `page$domain=example.org` will be matched, as it matches the referrer domain.
-- `page$domain=targetdomain.com` will be matched, as it matches the target domain and satisfies all requirements mentioned above.
-- `||*page$domain=targetdomain.com` will not be matched, as the pattern `||*page` may match specific domains, e.g. `example.page`.
+- `page$domain=targetdomain.com` will not be matched because it does not match the referrer domain.
- `||*page$domain=targetdomain.com,cookie` will be matched because the rule contains `$cookie` modifier despite the pattern `||*page` may match specific domains.
-- `/banner\d+/$domain=targetdomain.com` will not be matched as it contains a regular expression.
-- `page$domain=targetdomain.com|~example.org` will not be matched because the referrer domain is explicitly excluded.
+- `page$domain=targetdomain.com|~example.org,cookie` will not be matched because the referrer domain is explicitly excluded.
##### `$domain` modifier limitations {#domain-modifier-limitations}
@@ -1877,7 +1890,7 @@ In AdGuard for Windows, Mac and Android with [CoreLibs][] v1.11 or later, JSONPa
{
"elems": [
{
- "a": {"b": {"c": 123}},
+ "a": {"b": {"c": 123}}
},
{
"a": {"b": {"c": "abc"}}
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
index 8c0d0047761..3d16498e77e 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/general/ad-filtering/filter-policy.md
@@ -41,14 +41,12 @@ AdGuard ad-blocking filters include:
- AdGuard Base filter
- AdGuard Mobile Ads filter
- Regional filters divided by language principle — Chinese, Dutch, French, German, Japanese, Russian, Spanish/Portuguese, Turkish, and Ukrainian
-- AdGuard Quick Fixes filter
### The purpose of these filters
- **Base filter** is designed to block ads on English-language websites and those for which there is no separate filter. It also contains general filtering rules that apply to all sites regardless of language
- **Mobile Ads filter** blocks advertisements on mobile versions of websites and within mobile apps. There is no segmentation based on language
- **Regional filters** follow the same policy as the **Base filter**, but limited to websites in certain languages
-- **Quick Fixes filter** used to quickly resolve critical content filtering issues on popular websites without updating the MV3 extension.
The goal of ad-blocking filters is to block all types of advertising on websites, applications, and certain devices that can load ads from the Internet: